Vulnhub NOOB: 1
0x00 配置
攻击机 IP: 10.177.245.240
靶机 IP: 10.177.245.248
这个镜像用 VirtualBox 启动一直获取不到 IP,进单用户改静态 IP 也不行,最后换 VMware 就好了~
0x01 攻击
使用 Nmap 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~/work]
└─# nmap -sV -p- -A -T3 10.177.245.248
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-14 10:09 CST
Nmap scan report for 10.177.245.248
Host is up (0.00055s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 21 Sep 21 2021 cred.txt
|_-rw-r--r-- 1 0 0 86 Jun 11 2021 welcome
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.177.245.240
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Login
|_http-server-header: Apache/2.4.29 (Ubuntu)
55077/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dce8ad803581c4297ecfe470f269d996 (RSA)
| 256 462020039c9735f62d5d624abe6c958e (ECDSA)
|_ 256 ae9088f6638ddc60fafffc7012e4f41f (ED25519)
MAC Address: 00:0C:29:A4:C6:9B (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.55 ms 10.177.245.248
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.42 seconds
发现了三个端口是开着的: 21 (FTP)、80 (HTTP)、55077 (SSH),其中 FTP 端口是允许匿名登录的,先把 FTP 里的文件拉下来
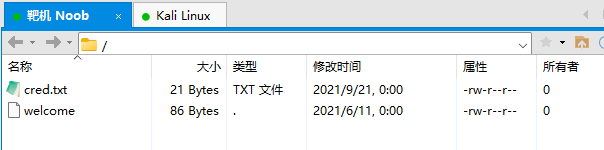
welcome 是个没有后缀的文本文件
🙏 WELCOME 🙏
We're glad to see you here.
💪 All The Best 👍
cred.txt 里面有一串 BASE64 编码,解码后得到一个用户名和密码
Y2hhbXA6cGFzc3dvcmQ=
// 解码
// champ:password
这个用户名和密码可能是 SSH 的,也可能是别的地方的,尝试登录 SSH 无果,继续看 80 端口的网页
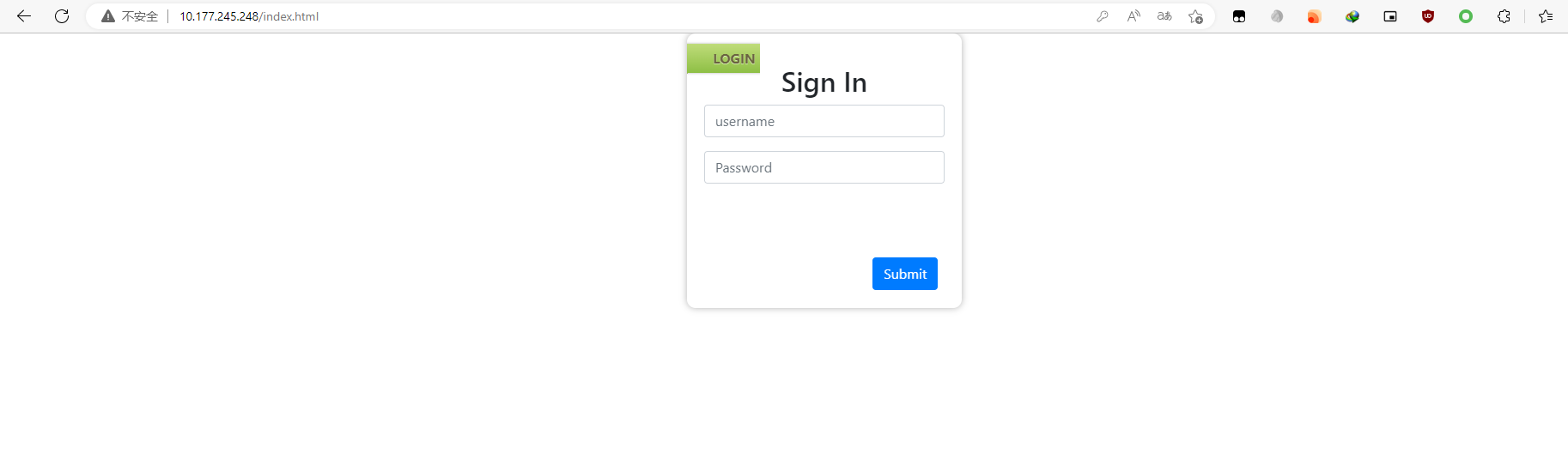
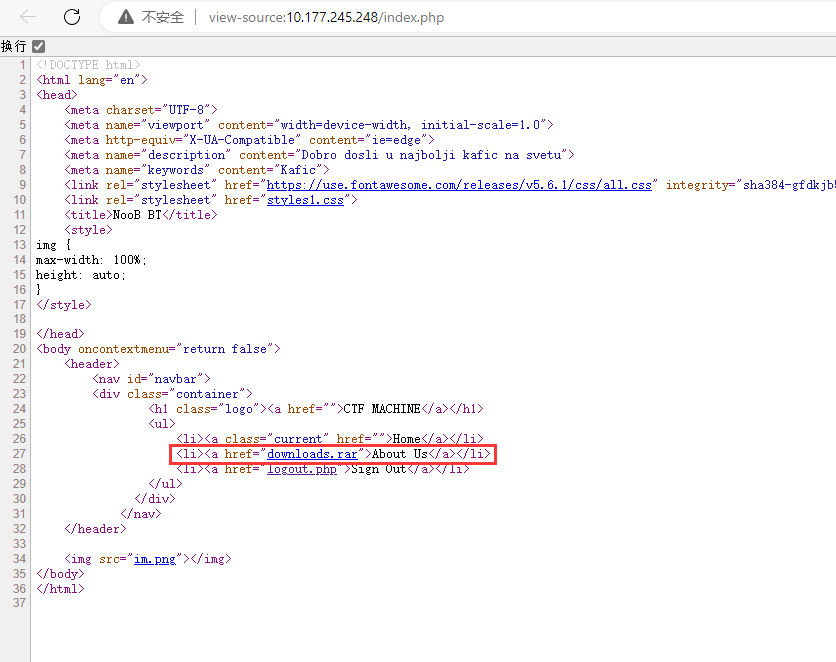
网页需要用户名和密码,用刚才获得的用户名 champ、密码 password 成功登录,主页什么都没有,Ctrl + U 查看源代码发现 About Us 按钮的事件,点击之后会下载一个 downloads.rar
解压 downloads.rar,发现两张图片和一个文件名是 sudo 的文本文件,猜测是图片隐写
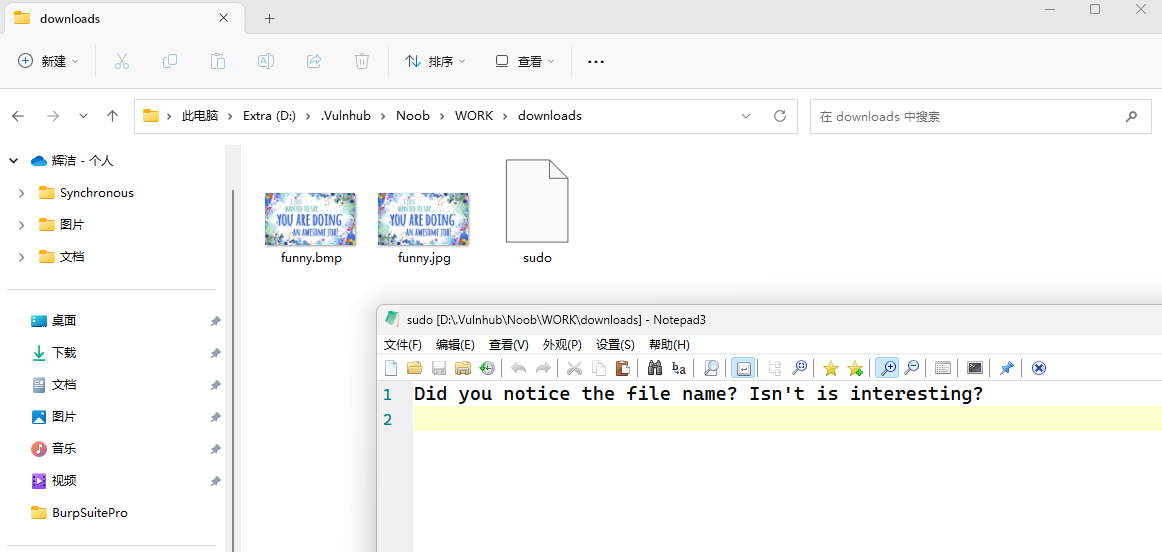
用 stgehide 工具解析文件,发现内部分别隐藏了一个 hint.py 和 user.txt。bmp 文件解析需要密码,用 "sudo" 成功解密
┌──(root㉿azwhikaru)-[~/work]
└─# steghide info funny.jpg
"funny.jpg":
format: jpeg
capacity: 2.5 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "hint.py":
size: 93.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
┌──(root㉿azwhikaru)-[~/work]
└─# steghide info funny.bmp
"funny.bmp":
format: jpeg
capacity: 2.5 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "user.txt":
size: 29.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
继续用 stgehide 解包
┌──(root㉿azwhikaru)-[~/work]
└─# steghide extract -sf funny.bmp
Enter passphrase:
wrote extracted data to "user.txt".
┌──(root㉿azwhikaru)-[~/work]
└─# steghide extract -sf funny.jpg
Enter passphrase:
wrote extracted data to "hint.py".
得到了 user.txt 和 hint.py,其中 hint.py 写着
This is_not a python file but you are revolving around.
well, try_ to rotate some words too.
user.txt
jgs:guvf bar vf n fvzcyr bar
hint.py 说这不是 python 文件,让我也试试翻转这些文字。用 ciphey 解密
┌──(root㉿azwhikaru)-[~/work]
└─# docker run -it --rm remnux/ciphey -t "jgs:guvf bar vf n fvzcyr bar"
Possible plaintext: 'wtf:this one is a simple one' (y/N): y
╭─────────────────────────────────────────────────────────────╮
│ Formats used: │
│ affine: │
│ Key: a=1, b=13Plaintext: "wtf:this one is a simple one" │
╰─────────────────────────────────────────────────────────────╯
解密得到了 wtf:this one is a simple one,和之前网页的用户名密码格式类似,这个应该就是 SSH 的用户名和密码了,尝试登录 SSH
[C:\~]$ ssh 10.177.245.248:55077
Connecting to 10.177.245.248:55077...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-156-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Feb 14 09:52:46 UTC 2023
System load: 0.0 Processes: 186
Usage of /: 49.3% of 8.79GB Users logged in: 0
Memory usage: 28% IP address for ens33: 10.177.245.248
Swap usage: 0%
77 packages can be updated.
1 update is a security update.
Last login: Tue Sep 21 19:59:59 2021 from 192.168.169.1
/usr/bin/xauth: file /home/wtf/.Xauthority does not exist
_________________________
< You now have Asian Flu. >
-------------------------
\
\
.--.
|o_o |
|:_/ |
// \ \
(| | )
/'\_ _/`\
\___)=(___/
wtf@wtf:~$
成功获取到 Shell,但并没有 Root 权限。现在当前用户的家目录中搜索有没有 flag 的线索
wtf@wtf:~$ find ./ -name "*flag*"
./Downloads/flag-1.txt
wtf@wtf:~$ cat ./Downloads/flag-1.txt
VGhlIGZsYWcgaXMgdGhlIGVuY29kZWQgc3RyaW5nIGl0c2VsZg
// The flag is the encoded string itself
获取到了一个 flag,继续尝试提权。用 id 命令发现 wtf 用户已经在 sudo 用户组里,直接提权
wtf@wtf:~$ id
uid=1000(wtf) gid=1000(wtf) groups=1000(wtf),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
wtf@wtf:~$ sudo -i
[sudo] password for wtf:
root@wtf:~# id
uid=0(root) gid=0(root) groups=0(root)
root@wtf:~#
切换到 /root 目录,发现第二个 flag
root@wtf:~# cd /root
root@wtf:~# ls
root.txt snap
root@wtf:~# cat root.txt
RW5kb3JzZSBtZSBvbiBsaW5rZWRpbiA9PiBodHRwczovL3d3dy5saW5rZWRpbi5jb20vaW4vZGVlcGFrLWFoZWVyCg==
// Endorse me on linkedin => https://www.linkedin.com/in/deepak-aheer
Follow me on Twitter https://www.twitter.com/Deepakhr9
TryHackMe --> https://www.tryhackme.com/p/Malwre99
Github --> https://www.github.com/Deepak-Aheer
(the flag is my LinkedIn username)
THANK YOU for PLAYING THIS CTF
But REMEMBER we're still N00bs ;)
0x02 总结
不难,只用到了端口扫描和一些简单的加解密。最后的提权看网上 WP,有几个用 nano 提权的,但实际上 wtf 用户本身就在 sudoers 里,直接 sudo -i 就可以提权


