openssh由7.4编译升级到8.0之后出现一些问题
问题一 : /etc/ssh/ssh_config line 57: Unsupported option "gssapiauthentication"
ssh升级之后登陆远程服务器的时候出现如下报错
/etc/ssh/ssh_config line 57: Unsupported option "gssapiauthentication"
客户端:
找到/etc/ssh/ssh_config配置文件的第57行
GSSAPIAuthentication yes
把这一行注释掉就行了
服务端:
注释sshd_config的以下参数:
#GSSAPIAuthentication yes
#GSSAPICleanupCredentials yes
#UsePAM yes
服务端改配置需要重启sshd服务
问题二 : su命令不能用.
使用su命令不成功,无在目标机器上通过一个普通用户su切换为root执行相关命令
错误如下:
ansible Timeout (12s) waiting for privilege escalation prompt
我碰到的原因是因为ansible管理的客户端上面sshd配置文件设置有误,我直接从没问题的主机拷贝的sshd_config文件到问题主机上解决的,网上说的一种修改ansible.cfg的超时时间,不适合我当时碰到的情况
问题三 : 文件句柄数设置不成功
[root@cpoc-2 ssh]# cat /etc/security/limits.conf |grep -v ^#|grep -v ^$ * soft core 0 * hard core 0 * soft nproc 65535 * hard nproc 65535 * soft nofile 655350 * hard nofile 655350 * soft memlock 96 * hard memlock 96 [root@cpoc-2 ssh]# cat /etc/security/limits.d/20-nproc.conf |grep -v ^#|grep -v ^$ * soft nproc 4096 root soft nproc unlimited
然后普通用户ssh登陆之后查看 ulimit -a
[xuweiyuan@cpoc-2 ~]$ ulimit -n 1024 [xuweiyuan@cpoc-2 ~]$ ulimit -u 4096
ssh不支持pam,查找原因是编译openssh的时候没有支持pam,也就是 --with-pam
./configure --prefix=/usr --sysconfdir=/etc/ssh --with-md5-passwords --with-zlib --with-pam make -j4 && make instal
重新编译安装,调整sshd_config文件,重启服务之后,登陆服务器的时候,输入正确的密码,然后出现如下报错
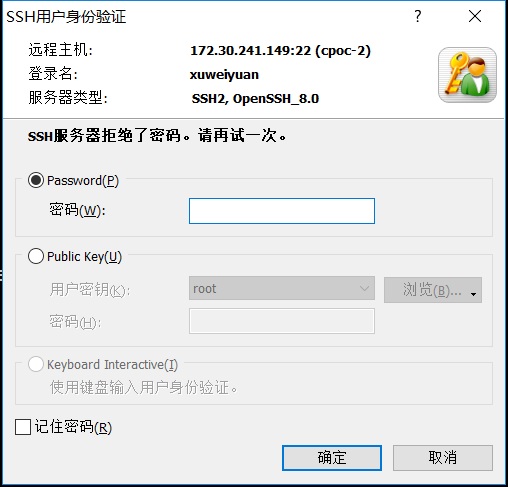
密码错误,是因为UsePAM yes
查看/etc/pam.d目录,没有发现sshd,所以重新写了一个文件
vim /etc/pam.d/sshd #%PAM-1.0 auth required pam_sepermit.so auth substack password-auth auth include postlogin # Used with polkit to reauthorize users in remote sessions -auth optional pam_reauthorize.so prepare account required pam_nologin.so account include password-auth password include password-auth # pam_selinux.so close should be the first session rule session required pam_selinux.so close session required pam_loginuid.so # pam_selinux.so open should only be followed by sessions to be executed in the user context session required pam_selinux.so open env_params session required pam_namespace.so session optional pam_keyinit.so force revoke session include password-auth session include postlogin # Used with polkit to reauthorize users in remote sessions -session optional pam_reauthorize.so prepare
重启sshd服务,再次登陆没有问题,而且查看 ulimit -a
[xuweiyuan@cpoc-2 ~]$ ulimit -n 655350 [xuweiyuan@cpoc-2 ~]$ ulimit -u 4096
已经和/etc/security/limits.conf文件配置的一样了
所以说卸载系统自带的openssh之前,最好是备份一下/etc/pam.d/sshd
cp /etc/pam.d/sshd{,.old}
编译完之后 ,查看/etc/pam.d如果没有sshd文件,就恢复备份
问题四 : [WARNING]: sftp transfer mechanism failed on [172.30.241.149]. Use ANSIBLE_DEBUG=1 to see detailed information
错误信息如下:
[root@cpoc-1 xuweiyuan]# ansible all -b --become-method=su -m shell -a "whoami" [WARNING]: sftp transfer mechanism failed on [172.30.241.149]. Use ANSIBLE_DEBUG=1 to see detailed information 172.30.241.150 | CHANGED | rc=0 >> root 172.30.241.149 | CHANGED | rc=0 >> root
查看sshd_config文件
cat sshd_config|grep sftp
Subsystem sftp /usr/libexec/openssh/sftp-server ll /usr/libexec/openssh/sftp-server
ls: cannot access /usr/libexec/openssh/sftp-server: No such file or directory
查找 sftp-server
ll /usr/libexec/sftp-server
-rwxr-xr-x 1 root root 112800 Jul 26 15:47 /usr/libexec/sftp-server
然后修改配置文件
Subsystem sftp /usr/libexec/openssh/sftp-server
改成
Subsystem sftp /usr/libexec/sftp-server
重启服务systemctl restart sshd ,重新执行命令,查看结果
[root@cpoc-1 xuweiyuan]# ansible all -b --become-method=su -m shell -a "whoami" 172.30.241.150 | CHANGED | rc=0 >> root 172.30.241.149 | CHANGED | rc=0 >> root
啦




 浙公网安备 33010602011771号
浙公网安备 33010602011771号