安全加解密引擎基础(PKE RSA)
关键词:RSA、PKCS、openssl、PyCryptodome等。
1 基本概念
1.1 编码格式
1.2 密钥格式(PKCS#1、PKCS#8)
RSAPublicKey ::= SEQUENCE { modulus INTEGER, -- n publicExponent INTEGER -- e }
RSAPrivateKey ::= SEQUENCE { version Version, modulus INTEGER, -- n publicExponent INTEGER, -- e privateExponent INTEGER, -- d prime1 INTEGER, -- p prime2 INTEGER, -- q exponent1 INTEGER, -- d mod (p-1) exponent2 INTEGER, -- d mod (q-1) coefficient INTEGER -- (inverse of q) mod p }
PrivateKeyInfo ::= SEQUENCE {
version Version,
privateKeyAlgorithm AlgorithmIdentifier {{PrivateKeyAlgorithms}},
privateKey PrivateKey,
attributes [0] Attributes OPTIONAL
}
|
PKCS#1
|
PKCS#8
|
|
RSA公钥和私钥
|
RSA公钥和私钥
其他秘钥(比如ECC)
|
1.3 证书类型(X.509、PKCS#12、PKCS#7)
Certificate ::= SEQUENCE { tbsCertificate TBSCertificate, signatureAlgorithm AlgorithmIdentifier, signatureValue BIT STRING } TBSCertificate ::= SEQUENCE { version [0] EXPLICIT Version DEFAULT v1, serialNumber CertificateSerialNumber, signature AlgorithmIdentifier, issuer Name, validity Validity, subject Name, subjectPublicKeyInfo SubjectPublicKeyInfo, issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL, -- If present, version MUST be v2 or v3 subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL, -- If present, version MUST be v2 or v3 extensions [3] EXPLICIT Extensions OPTIONAL -- If present, version MUST be v3 } SubjectPublicKeyInfo ::= SEQUENCE { algorithm AlgorithmIdentifier, subjectPublicKey BIT STRING }
|
X.509
|
PKCS#12
|
PKCS#7
|
|
仅公钥
|
公钥和私钥
|
证书链
|
1.4 RSA
RSA算法原理
RSA算法描述
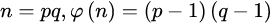 ;
; ,整数e用做加密钥(注意:e的选取是很容易的,例如,所有大于p和q的素数都可用);
,整数e用做加密钥(注意:e的选取是很容易的,例如,所有大于p和q的素数都可用);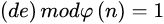 ,即
,即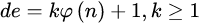 是一个任意的整数;所以,若知道e和
是一个任意的整数;所以,若知道e和 ,则很容易计算出d;
,则很容易计算出d;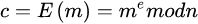

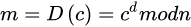

安全性
运算速度
2 openssl关于RSA的使用
2.1 密钥生成(PKCS#1)
通过openssl genpkey生成RSA私钥:
openssl genpkey -algorithm rsa -pkeyopt rsa_keygen_bits:2048 -out private_pkcs1.pem
openssl genpkey成成RSA秘钥可配置选项还包括:
rsa_keygen_bits:numbits The number of bits in the generated key. If not specified 2048 is used. rsa_keygen_primes:numprimes The number of primes in the generated key. If not specified 2 is used. rsa_keygen_pubexp:value The RSA public exponent value. This can be a large decimal or hexadecimal value if preceded by 0x. Default value is 65537.
或者通过openssl genrsa生成RSA私钥:
openssl genrsa -out private_pkcs1.pem 2048
2.2 密钥提取
从私钥中提取公钥:
openssl genrsa -out private_pkcs1.pem 2048 openssl rsa -in private_pkcs1.pem -out private_pkcs1_to_public_pkcs8.pem -pubout openssl rsa -in private_pkcs1.pem -out private_pkcs1_to_public_pkcs1.pem -pubout -RSAPublicKey_out
从公钥中提取e/n:
openssl rsa -in private_pkcs1_to_public_pkcs8.pem -text -pubin -noout > private_pkcs1_to_public_pkcs8.txt
公钥结果如下:
RSA Public-Key: (2048 bit) Modulus:--去除开始00,剩余共256字节,即2048bit。出去开头00,剩余部分才是Modulus有效部分。 00:d6:77:bc:0b:a5:49:b7:c2:93:c9:10:30:38:84: 59:51:72:a0:24:b8:20:ec:9b:a0:d9:9e:20:de:dc: e2:0e:ba:98:7a:ec:fe:7a:79:ec:09:87:93:72:c9: a4:ec:83:14:9f:e2:da:e4:d5:bd:d4:38:08:ad:a0: e7:a2:30:8a:c1:cc:11:9a:93:ab:53:35:23:00:6f: 26:d9:ac:e9:dd:93:dd:ec:0d:16:51:3b:4c:a5:04: b9:6a:a4:a9:3b:17:4c:0a:46:4d:63:be:54:08:84: 4d:c2:d2:85:50:c0:23:d3:3d:c3:54:47:fc:28:30: 68:d6:1c:33:30:28:7f:dc:16:ca:bb:02:09:1c:a8: 4c:83:a8:a7:7d:a6:ad:a6:3c:c9:14:68:e9:81:29: c6:18:54:26:02:c6:cf:de:e6:0d:9b:97:ed:2f:41: b7:43:47:33:ec:24:ed:e3:2c:d6:b7:b2:b5:d0:39: 1f:98:c5:4f:17:15:93:6b:4d:40:1e:34:aa:33:2b: 60:67:dd:d6:6f:a2:3b:b2:c8:a9:01:2f:60:7b:1a: 52:86:77:e6:07:b2:f8:3d:3d:29:40:47:87:cc:09: e9:0e:9b:0e:66:8a:5d:24:5f:aa:1a:24:8e:84:33: 4b:1b:16:61:8d:93:d9:63:f1:d4:ea:3b:f6:fe:c2: 2e:5d Exponent: 65537 (0x10001)--Exponent默认值为17bit大小的0x10001。
ASN.1解析PKCS#1公钥:
openssl asn1parse -in private_pkcs1_to_public_pkcs1.pem
结果如下:
0:d=0 hl=4 l= 266 cons: SEQUENCE
4:d=1 hl=4 l= 257 prim: INTEGER :D677BC0BA549B7C293C910303884595172A024B820EC9BA0D99E20DEDCE20EBA987AECFE7A79EC09879372C9A4EC83149FE2DAE4D5BDD43808ADA0E7A2308AC1CC119A93AB533523006F26D9ACE9DD93DDEC0D16513B4CA504B96AA4A93B174C0A464D63BE5408844DC2D28550C023D33DC35447FC283068D61C3330287FDC16CABB02091CA84C83A8A77DA6ADA63CC91468E98129C618542602C6CFDEE60D9B97ED2F41B7434733EC24EDE32CD6B7B2B5D0391F98C54F1715936B4D401E34AA332B6067DDD66FA23BB2C8A9012F607B1A528677E607B2F83D3D29404787CC09E90E9B0E668A5D245FAA1A248E84334B1B16618D93D963F1D4EA3BF6FEC22E5D
265:d=1 hl=2 l= 3 prim: INTEGER :010001
openssl rsa -in private_pkcs1.pem -text -noout > private_pkcs1.txt
结果如下:
RSA Private-Key: (2048 bit, 2 primes) modulus:--去除开头00,剩余部分共2048bit为有效部分。对应RSA参数n。 00:d6:77:bc:0b:a5:49:b7:c2:93:c9:10:30:38:84: 59:51:72:a0:24:b8:20:ec:9b:a0:d9:9e:20:de:dc: e2:0e:ba:98:7a:ec:fe:7a:79:ec:09:87:93:72:c9: a4:ec:83:14:9f:e2:da:e4:d5:bd:d4:38:08:ad:a0: e7:a2:30:8a:c1:cc:11:9a:93:ab:53:35:23:00:6f: 26:d9:ac:e9:dd:93:dd:ec:0d:16:51:3b:4c:a5:04: b9:6a:a4:a9:3b:17:4c:0a:46:4d:63:be:54:08:84: 4d:c2:d2:85:50:c0:23:d3:3d:c3:54:47:fc:28:30: 68:d6:1c:33:30:28:7f:dc:16:ca:bb:02:09:1c:a8: 4c:83:a8:a7:7d:a6:ad:a6:3c:c9:14:68:e9:81:29: c6:18:54:26:02:c6:cf:de:e6:0d:9b:97:ed:2f:41: b7:43:47:33:ec:24:ed:e3:2c:d6:b7:b2:b5:d0:39: 1f:98:c5:4f:17:15:93:6b:4d:40:1e:34:aa:33:2b: 60:67:dd:d6:6f:a2:3b:b2:c8:a9:01:2f:60:7b:1a: 52:86:77:e6:07:b2:f8:3d:3d:29:40:47:87:cc:09: e9:0e:9b:0e:66:8a:5d:24:5f:aa:1a:24:8e:84:33: 4b:1b:16:61:8d:93:d9:63:f1:d4:ea:3b:f6:fe:c2: 2e:5d publicExponent: 65537 (0x10001)--对应RSA参数e。 privateExponent:--去除开头00,剩余部分共2048bit为有效部分。对应RSA参数d。 00:8c:52:cb:36:d3:6e:e8:4c:e7:65:26:b2:66:48: 32:28:98:57:2f:af:49:db:85:f8:38:6a:be:17:13: 6e:d5:34:41:90:2c:80:54:a2:71:4d:ca:e7:2e:b3: c0:b4:ff:0e:ff:8d:ee:aa:cb:2e:e9:2b:c0:81:da: 45:b4:59:0e:70:be:94:c6:0e:d8:8a:18:ba:4e:0e: 6b:dd:00:c6:03:b4:3b:ff:b6:90:63:95:e9:10:0f: 87:41:bf:7a:fa:ae:c3:91:f5:6d:ad:55:5a:a6:37: ea:a9:0e:15:2c:40:8b:30:2b:b9:21:eb:f7:90:54: 1c:43:fb:2f:82:d2:fc:d5:82:e1:7b:19:d2:10:a3: 3b:f2:ab:4a:3c:63:53:59:3d:0f:47:6c:b5:2d:4d: 75:b4:d1:55:84:ec:36:7c:c1:a9:7e:53:56:74:88: 68:10:a3:73:6e:d7:70:77:da:4b:ef:43:29:fa:a1: ec:5a:70:ae:93:90:a4:0f:8a:2d:37:01:5d:ec:b3: c3:5c:6f:49:b7:ec:3b:6b:3f:d2:41:ab:af:b4:aa: 76:42:aa:e6:82:85:fb:f5:de:6a:c2:3e:81:e8:a6: 5b:18:1b:56:67:d1:3a:bb:3d:97:a6:6c:98:c8:4c: ae:c5:64:4c:01:2e:24:19:13:5c:eb:da:9e:2e:18: 82:01 prime1:--去除开头00,剩余1024bit为有效部分。对应RSA参数p。 00:ed:9e:c0:62:9e:98:34:09:63:50:80:eb:42:4f: cc:d3:25:8c:78:17:1c:d9:64:12:48:fd:13:e5:eb: 1d:86:f9:b9:f9:c8:70:a7:1b:27:5c:fb:8e:d9:6b: 8b:1e:c9:46:6b:77:2f:82:3b:5f:17:13:b9:63:66: 40:38:df:e7:4b:8f:ef:87:c0:34:da:57:7b:52:83: 25:a1:35:00:29:a9:55:56:0d:5a:87:1c:b5:e7:d9: 9f:2a:8a:31:40:a4:35:be:fb:3d:0c:18:87:14:6b: e6:49:44:d2:a8:97:dc:ab:25:f8:11:fb:4b:cc:b0: 18:5d:8b:2f:6c:d4:fd:16:63 prime2:--去除开头0,剩余1024bit为有效部分。对应RSA参数q。 00:e7:0e:87:7e:80:6b:57:02:71:4c:6f:16:43:3d: 1f:19:0e:fb:07:cd:60:c6:7b:48:ad:e4:72:5e:3e: b8:3f:f2:1f:ed:9f:90:51:ba:03:8a:69:a4:cb:65: 9b:f6:eb:46:b1:e8:40:05:50:9d:f3:36:2e:c4:d7: b0:33:2d:36:51:c0:ee:60:95:04:75:5d:5e:c5:82: f5:f5:72:c9:aa:66:3e:ff:a4:79:97:32:2c:73:c1: d5:f7:a3:80:17:8a:ee:81:95:55:b5:1a:93:81:f5: a7:7f:91:48:59:c3:3b:2a:ee:20:7f:df:7f:9c:b5: 0b:f6:3a:cd:0d:8c:c9:64:3f exponent1:--共1024bit,对应RSA参数dmp1。 55:a0:1f:33:6a:72:ee:4d:73:bc:4e:b8:77:ec:c9: a2:4c:a5:91:a0:c2:84:93:cb:03:02:2f:69:6a:8f: f9:53:83:f0:be:89:d9:ad:af:41:92:64:a7:74:59: 6d:7e:9a:21:9f:91:3f:1c:a5:e7:6a:f4:23:1d:75: 87:09:28:0f:d2:8e:3e:1c:c4:ee:e9:17:47:64:7a: ea:dc:6e:72:94:d2:6b:6f:e4:6f:4b:a9:41:22:ea: 78:29:d4:15:b7:16:a6:fb:61:c4:3a:12:73:09:6e: b2:78:5a:70:e6:48:5e:64:10:40:6a:8d:a5:f4:ce: d2:e6:94:f0:62:cf:d0:81 exponent2:--共1024bit,对应RSA参数dmq1。 24:f0:08:af:2b:7e:7d:79:71:7d:63:a0:ee:7c:dd: f4:d6:95:41:09:0f:38:8b:ca:f1:a9:bc:b2:de:59: fc:37:0b:ed:a3:fd:a1:63:18:5f:cf:45:be:12:6f: 5d:88:fd:53:41:aa:c2:6e:c1:e1:78:be:ff:4e:ef: e7:2e:8a:29:85:ab:56:1b:5c:8c:1a:b2:24:e7:2b: c4:e2:65:e4:ec:d5:93:6e:ca:d5:65:fa:ff:42:74: 9f:53:2f:0e:14:72:ce:9a:7e:0a:26:c6:80:17:32: 80:cd:4c:00:b5:9a:46:e1:ac:a6:64:a7:74:f8:e8: 81:a3:a2:d6:50:b4:7d:67 coefficient:--共1024bit,对应RSA参数iqmp。 54:65:9b:aa:37:59:97:88:8d:1d:f0:88:db:de:2c: 10:78:7c:15:34:21:58:69:70:95:a2:92:be:a4:33: 6c:6a:5a:eb:71:59:71:7a:95:f1:0f:a8:26:4d:a8: 00:47:d0:f3:b8:b8:1e:ff:7a:1b:8e:ab:16:9b:ec: c7:5d:c9:dd:45:6b:11:55:bd:f7:cd:d5:a4:07:5b: 24:75:7c:ed:c6:86:3e:36:f1:63:d0:65:0f:40:e8: 23:dc:cc:1b:d4:7f:d5:e9:83:ee:08:14:1d:8f:e0: 29:56:c0:1b:02:c5:bb:0e:dc:59:3d:a0:44:2b:d5: 64:2e:52:01:d5:7a:25:2e
|
openssl rsa
|
Struct rsa_st
|
RSA_GetKey
|
RSA_GetCRTKey(CRT模式)
|
Size(in bit, RSA 2048 for example.)
|
说明
|
|
modulus
|
n
|
n
|
n
|
2048
|
RSA public module n
|
|
publicExponent
|
e
|
e
|
e
|
2048
|
RSA public key e(公开幂)
|
|
privateExponent
|
d
|
d
|
2048 |
RSA private key d(私有幂)
|
|
|
prime1
|
p
|
p
|
1024
|
p, prime number, one part of private key (p,q,dp,dq,u)(n的素数因子p)
|
|
|
prime2
|
q
|
q
|
1024
|
q, prime number, one part of private key (p,q,dp,dq,u)(n的素数因子q)
|
|
|
exponent1
|
dmp1
|
dp
|
1024
|
dp = e^(-1) mod (p-1), one part of private key (p,q,dp,dq,u)
|
|
|
exponent2
|
dmq1
|
dq
|
1024
|
dq = e^(-1) mod (q-1), one part of private key (p,q,dp,dq,u)
|
|
|
coefficient
|
iqmp
|
u
|
1024
|
u = q^(-1) mod p, one part of private key (p,q,dp,dq,u)
|
从私钥或者公钥中提取出各元素的目的是对接底层加解密引擎。
2.3 RSA签名验签
1. 生成RSA 2048密钥对:私钥和公钥。
openssl genrsa -out key.pem 2048 openssl rsa -in key.pem -pubout > key.pub
2. 输入数据,生成其哈希摘要;输入私钥和哈希摘要,生成哈希摘要的签名。
openssl dgst -binary -sha256 uImage > hash openssl pkeyutl -sign -in hash -inkey key.pem -pkeyopt digest:sha256 -keyform PEM -out uImage.sign
或者
openssl dgst -sign key.pem -keyform PEM -sha256 -out uImage.sign -binary uImage
3. 输入签名和公钥,对数据进行验签。
openssl dgst -verify key.pub -keyform PEM -sha256 -signature uImage.sign -binary uImage
4. 查看私钥公钥信息
openssl rsa -inform PEM -in key.pem -text openssl rsa -inform PEM -in key.pub -pubin -text
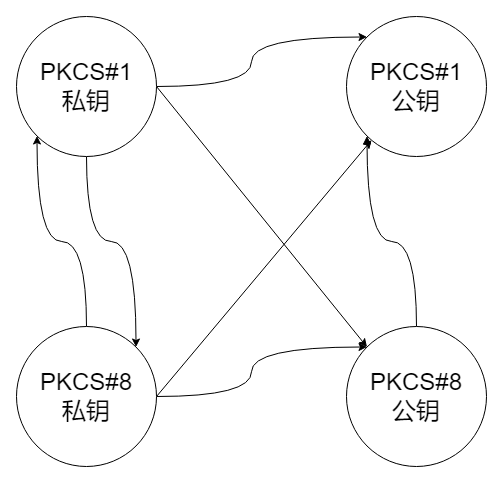
2.4 密钥格式转换(PKCS#1、PKCS#8)
openssl genrsa -out private_pkcs1.pem 2048 openssl rsa -in private_pkcs1.pem -out private_pkcs1_to_public_pkcs8.pem -pubout openssl rsa -in private_pkcs1.pem -out private_pkcs1_to_public_pkcs1.pem -pubout -RSAPublicKey_out
RSA私钥:PKCS#1 -> PKCS#8
openssl pkcs8 -in private_pkcs1.pem -out private_pkcs1_to_private_pkcs8.pem -topk8 -nocrypt
openssl rsa -in private_pkcs1_to_private_pkcs8.pem -out private_pkcs8_to_private_pkcs1.pem openssl rsa -in private_pkcs1_to_private_pkcs8.pem -out private_pkcs8_to_public_pkcs8.pem -pubout openssl rsa -in private_pkcs1_to_private_pkcs8.pem -out private_pkcs8_to_public_pkcs1.pem -pubout -RSAPublicKey_out
RSA公钥:PKCS#8 -> PKCS#1
openssl rsa -in private_pkcs8_to_public_pkcs8.pem -out public_pkcs8_public_pkcs1.pem -pubin -RSAPublicKey_out
openssl genrsa -out private_pkcs1.pem 2048 openssl rsa -in private_pkcs1.pem -out private_pkcs1_to_public_pkcs8.pem -pubout openssl rsa -in private_pkcs1.pem -out private_pkcs1_to_public_pkcs1.pem -pubout -RSAPublicKey_out openssl pkcs8 -in private_pkcs1.pem -out private_pkcs1_to_private_pkcs8.pem -topk8 -nocrypt openssl rsa -in private_pkcs1_to_private_pkcs8.pem -out private_pkcs8_to_private_pkcs1.pem openssl rsa -in private_pkcs1_to_private_pkcs8.pem -out private_pkcs8_to_public_pkcs8.pem -pubout openssl rsa -in private_pkcs1_to_private_pkcs8.pem -out private_pkcs8_to_public_pkcs1.pem -pubout -RSAPublicKey_out openssl rsa -in private_pkcs8_to_public_pkcs8.pem -out public_pkcs8_public_pkcs1.pem -pubin -RSAPublicKey_out
bdf4ca6a718690657cba0f468e7f5fe2 private_pkcs1.pem
72ae2b4a20ae9f250938f598c416b046 private_pkcs1_to_private_pkcs8.pem
25c8ce86dc4a385e3bd35c26d5c4d895 private_pkcs1_to_public_pkcs1.pem
b4c456ec560dfaac57c7a3f01041e4b7 private_pkcs1_to_public_pkcs8.pem
bdf4ca6a718690657cba0f468e7f5fe2 private_pkcs8_to_private_pkcs1.pem
25c8ce86dc4a385e3bd35c26d5c4d895 private_pkcs8_to_public_pkcs1.pem
b4c456ec560dfaac57c7a3f01041e4b7 private_pkcs8_to_public_pkcs8.pem
25c8ce86dc4a385e3bd35c26d5c4d895 public_pkcs8_public_pkcs1.pem
openssl rsa -in private_pkcs1.pem -text > private_pkcs1.txt openssl rsa -in private_pkcs1_to_private_pkcs8.pem -text > private_pkcs1_to_private_pkcs8.txt openssl rsa -in private_pkcs1_to_public_pkcs8.pem -text -pubin > private_pkcs1_to_public_pkcs8.txt
2.5 证书处理
x509证书处理
openssl genrsa -out private_pkcs1.pem 4096
openssl req -new -key private_pkcs1. pem -out certificate_csr.csr
openssl x509 -req -days 365 -in certificate_csr.csr -signkey private_pkcs1.pem -out certificate.pem openssl x509 -req -days 365 -in certificate_csr.csr -signkey private_pkcs1.pem -out certificate.der -outform DER
openssl x509 -in certificate.pem -text openssl x509 -in certificate.pem -text -noout (不输出文件本身内容) openssl x509 -in certificate.der -inform DER -text
PKCS#12证书处理
PKCS#7证书处理
3 Python加解密算法库PyCryptodome关于RSA的使用
PyCryptodome是python一个强大的加密算法库,可以实现常见的单向加密、对称加密、非对称加密和流加密算法。直接pip安装即可:
pip install pycryptodome
官网地址:https://pycryptodome.readthedocs.io/en/latest/index.html。
下面的代码进行了RSA密钥生成、加密解密、SHA256签名和验签:
# 参考文档:https://blog.csdn.net/weixin_43790276/article/details/100063132 # coding=utf-8 import os from Crypto import Random from Crypto.PublicKey import RSA from Crypto.Hash import SHA256 from Crypto.Cipher import PKCS1_v1_5 as PKCS1_cipher from Crypto.Signature import PKCS1_v1_5 as PKCS1_signature import base64 def hex_to_array(array, hex): print("unsigned char %s[] = {" % array, end='') for i in range(int(len(hex) / 2)): print("0x%c%c, " % (hex[i * 2], hex[i * 2 + 1]), end='') print("};") def key_int_to_array(array, key): print("unsigned int %s[128] = {" % array) hex_str = str(hex(key)).lstrip('0x') for i in reversed(range(int((len(hex_str)+7) / 8))): print("0x%s, " % (hex_str[i*8:(i+1)*8]), end='') if not (i)%8: print("") print("};") def rsa_gen_key(): random_generator = Random.new().read rsa = RSA.generate(2048, random_generator) print("RSA public key e = %08x" % rsa.e) print("RSA private key d = %0512x" % rsa.d) print("RSA public modulus n = %0512x" % rsa.n) print("RSA CRT private key p = %0256x" % rsa.p) print("RSA CRT private key q = %0256x" % rsa.q) print("RSA CRT private key u = %0256x" % rsa.u) # 生成私钥 # private_key = rsa.exportKey() # print(private_key.decode('utf-8')) # print("-" * 30 + "分割线" + "-" * 30) # 生成公钥 # public_key = rsa.publickey().exportKey() # print(public_key.decode('utf-8')) def rsa_encrypt_decrypt(): random_generator = Random.new().read rsa = RSA.generate(2048, random_generator) private_key = rsa.exportKey() with open("private_a.rsa", 'wb') as f: f.write(private_key) public_key = rsa.publickey().exportKey() with open("public_a.rsa", 'wb') as f: f.write(public_key) # 使用公钥对内容进行rsa加密 message = "This is a message." with open('public_a.rsa') as f: key = f.read() pub_key = RSA.importKey(str(key)) cipher = PKCS1_cipher.new(pub_key) rsa_text = base64.b64encode(cipher.encrypt(bytes(message.encode("utf8")))) print("RSA Encrypt:", rsa_text.decode('utf-8')) # 使用私钥对内容进行rsa解密 with open('private_a.rsa') as f: key = f.read() pri_key = RSA.importKey(key) cipher = PKCS1_cipher.new(pri_key) back_text = cipher.decrypt(base64.b64decode(rsa_text), 0) print("RSA Decrypt:", back_text.decode('utf-8')) def rsa_sign_verify(): message = "需要加密的信息" # 使用私钥生成签名 with open('private_a.rsa') as f: key = f.read() pri_key = RSA.importKey(key) signer = PKCS1_signature.new(pri_key) digest = SHA256.new() digest.update(message.encode("utf8")) sign = signer.sign(digest) signature = base64.b64encode(sign) print("Signature:", signature.decode('utf-8')) # 使用公钥验证签名 with open('public_a.rsa') as f: key = f.read() pub_key = RSA.importKey(key) verifier = PKCS1_signature.new(pub_key) digest = SHA256.new() digest.update(message.encode("utf8")) if verifier.verify(digest, base64.b64decode(signature)): print("Verification passed.") public_key_file = "key_pub.pem" private_key_file = "key.pem" def read_func(param): return b'0' def read_func2(param): return b'1' def rsa_osr_encrypt_decrypt_sign_verify(): if not (os.path.exists(public_key_file) and os.path.exists(private_key_file)): random_generator = Random.new().read rsa = RSA.generate(2048, random_generator) private_key = rsa.exportKey() with open(private_key_file, 'wb') as f: f.write(private_key) public_key = rsa.publickey().exportKey() with open(public_key_file, 'wb') as f: f.write(public_key) print("\n====================================HASH====================================") message = [] with open("pcs_enc.bin", 'rb') as f: message = f.read() # Generate SHA256 hash of message. digest = SHA256.new() digest.update(message) print("Hash:", digest.digest().hex()) print("\n====================================RSA Encrypt/Decrypt====================================") # 使用公钥对内容进行rsa加密 use_default_message = False if use_default_message: temp = [] for i in range(128): temp.append(0x01) message = bytes(temp) else: message = digest.digest() key_int_to_array('in', int.from_bytes(message, byteorder='little', signed=False)) with open(public_key_file) as f: key = f.read() pub_key = RSA.importKey(str(key)) cipher = PKCS1_cipher.new(pub_key, read_func) rsa_text = cipher.encrypt(message) # 使用私钥对内容进行rsa解密 with open(private_key_file) as f: key = f.read() pri_key = RSA.importKey(key) print("RSA public key e = %08x" % pri_key.e) print("RSA private key d = %0512x" % pri_key.d) print("RSA public module n = %0512x" % pri_key.n) #print("RSA CRT private key p = %0256x" % pri_key.p) #print("RSA CRT private key q = %0256x" % pri_key.q) #print("RSA CRT private key u = %0256x" % pri_key.u) key_int_to_array('e', pri_key.e) key_int_to_array('d', pri_key.d) key_int_to_array('n', pri_key.n) #key_int_to_array('p', pri_key.p) #key_int_to_array('q', pri_key.q) #key_int_to_array('u', pri_key.u) cipher = PKCS1_cipher.new(pri_key, read_func2) back_text = cipher.decrypt(rsa_text, 0) print("Input data:", message.hex()) print("RSA Encrypt:", rsa_text.hex()) print("RSA Decrypt:", back_text.hex()) # print("RSA Decrypt: %s"%(back_text)) print("\n====================================HASH Sigh/Verify====================================") print("Hash:", digest.digest().hex()) key_int_to_array('in', int.from_bytes(digest.digest(), byteorder='little', signed=False)) # 使用私钥生成签名 with open(private_key_file) as f: key = f.read() pri_key = RSA.importKey(key) signer = PKCS1_signature.new(pri_key) signature = signer.sign(digest) print("Signature:", signature.hex()) key_int_to_array('out', int(signature.hex(), 16)) # 使用公钥验证签名 with open(public_key_file) as f: key = f.read() pub_key = RSA.importKey(key) verifier = PKCS1_signature.new(pub_key) if verifier.verify(digest, signature): print("Verification passed.") else: print("Verification failed.") if __name__ == '__main__': print("Generate RSA key.") rsa_gen_key() print("\nRSA Encryption/Decryption.") rsa_encrypt_decrypt() print("\nRSA Sign/Verify.") rsa_sign_verify() print("\nRSA OSR Encryption/Decryption/Sign/Verify.") rsa_osr_encrypt_decrypt_sign_verify()
上面的代码为了和底层引擎对接调试,将中间参数输出。并将参数输出成数组形式。
输出结果如下:
/usr/bin/python3.8 /home/al/jupyter-notebook/edge10_scripted_code/rsa_test/main.py Generate RSA key. RSA public key e = 00010001 RSA private key d = 4cd0a498921b1c8ca3a9eb1547fa38fa38e69272abe4c672c471faf40e8601a67b40e6feeffe97b472ee2bb88ecbc96409794220212469261d824678d2ec767858f6ed338d497d463e1ca13bbd1e527e6b097ff9f676643f329fd583968fc3f783a4963a4909ea87f8f0b3d7fd03577260aa3c9e1741e77983b31b0287db92fea4325141ee229f12682c9b7662125a3b4e34fb4633d64438ce1b4e27efdd40fee1478b669d4b9cf1ddc17dbbb81300ea54a75967f97c2aae4179477cc798e6d69397dbe7ceb15b8133e66f8ef01a7677305f9c9a6528c84208da39f90962078ecfcafd103fa1651ed91192931e10c9e2251ac2e65319f988e38484327f139379 RSA public modulus n = c7f101db93cb9561ceb969041d034219054f74ec2c04ecac150ddb6d9fedc822940fc847ef2da757350b68cc3a4dabb343e55644f00ed3b8a1aa6bb6e919d05fbb04568cc09a004ffdab9d326892875889bf4641a2934835b68d0dc6aab1a912500756ecc7feb1b705edeb8f749e4fa8a48e36e076eafc8067eacc4a3b1aac36e4e6ca3ae39d92a207c0f6d16b7dbd26f226e78dea53fc6a61c87a8168e6aea63f171f81324fd1b5d82b993f7be098137244e0d98cc5e2f800942610f7d1d2113e1c7a3b6bec9e5e35466d26b7ffdc47765a5d867ee7fd72e1ba71b43c97fddbb599cbc448903ce893254ea85dbddf978a2dad67464bcf44efb88cd01cb2dbb3 RSA CRT private key p = e1be5b14e5efff5c75e6b7e4f7eef26614bcdbc721aad2bf1894bf0ff12cca86c2e31d670b6b01dbf15ff42cb95b5c26bef6bc42517a8bb02d1e998cfc2809bdb18e551a61e75b5c56463ae5f7b13d63255ac012ade31d2cd717a6f6e1c4cfc918be4068d6d950aa926e61dfaeffb2aa9e0755af0c04fc5c4176dabe602e04b9 RSA CRT private key q = e2bd56169bd629550ac210fa2c05c9c92eb5bb7b8dd7b94b09b736e3689323b418204bff4af0a4f334c7eb27b24d1995fcabe1765609c8f00c9acec7f0edff0d79da5c235b373cd47accb1988b8b5c2bfba5293559b14d040f1df8ca4defe363c008a4b271d862e364dfdccf1a14c447343cd539a752f8f7864a1df9cf4985cb RSA CRT private key u = 78c6041510c1fc51eb29f087016e71a4fa19e5d726cf51f629c29fbecd520a66fd36ba19dc9fbb8e5abd66f1a160ceb04f2fed6faeeb5aee683a26281ac310746760d48165a6c64a2db2c5cd0e11cb2d363daa1fde7e127042fdafe151a54cddee48a9c7789af8fe7b8a6b4d474ecf6d2d635391eed3d2e31ff0e9b0b4a6bfd3 RSA Encryption/Decryption. RSA Encrypt: eY96QGn4nOKC0tNPNqZpMF/lWfLegHTtfMezp+VZiJHL78x2p2l+sx30RX88Ao4GlkmtvA8ImCMNy0Hg2WdhSzMkyNnCWToeYGC3tV/e9jf/CLE6LfVKoBI1MOqpA7AYqeDG1EMT0G0MXiU4hpWseSwtts+ZxiJgV+ixIzLtYwNsqmIfsMtdKpRKwdSdPy+9cjudJg3VZt0LaRD+8Hvmu/QA5fMzZOvISjuFIvNlHSsOajZ8ojmKYdaps49C+NoUGFoAihNtXMefKWN0RIn2Jt9F26CYtGAdxEaqh48l3O4HcEN9zHi3Urm7QnUAG5K7TP4/8vFEu1LUjC4hQkEU0Q== RSA Decrypt: This is a message. RSA Sign/Verify. Signature: SVeVJ3b5vKqOpsI7w3w6JWGfMrSn8gswj91KPLqcUBeBoNFo/xiGf1XVgi61IjqsSbzAw7EQxMHk69OkhWJKxmPbIzajw1UuipUuPWfUgOaLy70GhMBEyYiQICCGZfjeSFBYnJgu2CFej/FzH2BEh44WIrSMRY4Km5NVq+V2JSmGKgQkdR2dPtvL9xp6+KgDFoKjNJj2zDlVafh60HVi5g90EMW2708zo8oG7kzIgNKxQbB5LPcULlwHY7u+Wwaw37FEeUigJs+yXSFpXuNwuZvEQOGrzoPMX+6PL0raZu3K/E7vPeUP2kVT7m9h9C9MXkvf7LzNCyJ9/U/RpGkMOA== Verification passed. RSA OSR Encryption/Decryption/Sign/Verify. ====================================HASH==================================== Hash: c17672af76117cfc9cfb4e5d59312f0e30a7df4e358141c019881afc39a4a09b ====================================RSA Encrypt/Decrypt==================================== unsigned int in[128] = { 0xaf7276c1, 0xfc7c1176, 0x5d4efb9c, 0x0e2f3159, 0x4edfa730, 0xc0418135, 0xfc1a8819, 0x9ba0a439, }; RSA public key e = 00010001 RSA private key d = 0643eb7d9041c954b9708106a30fd2686a328a3161dccf20b3097b32e127e4c36872942bca264fd37bcfcf5004a6b6a6df10868fddb202204c976d46962760120e1b078e9bd224fa466d5aff322f010d71a8cbc4f8f70bd9372429b3082c141e634788ca45b654943bf21a46499871f8294bc8549b384393df46e8c420b10654996e71dbc111634df6ebf89d03dd2c8bcdb4d090e95428e8a1c3c259ff56e0c465a44adf7a9f02acc3c2c16f571bdd3c28444a1d66fb3a57f30cb0173dd32b7a80dd9fc0336fe5db1d9f69a4244ac692b00ce9169a077a4d244e9497e6335b9b92003472819ff86f00b5892555db48a551a5e69761d123144d7fc4dc0aeea631 RSA public module n = c7e849f7fdecc13f69187c871d7894982145984b494f24550581a64ed03c8ffda88132e59e0cb5b12f85bfaabec853741fd4d46d36533bdcf1424a08e7117a1237f8baa86dc5c53981d2cf760d3c7a32b0c31b640c774097edb9cf8a93f491e1839ace1f38a8caba0546d1ef0891054f6cec82aa71c684a0e2aefe2294b558b33914ffc369d3cdab62b98527028914ce585cbae29c6d8db3427586dab5495773ab7e680c5f26c066e0d2c8fa8a3be3dccacd747d65f7e6fad2e34abf606ac075580f672ced4cf0a378067bfc0a0c1e9d9f3ac4b821731c7ff81136e3954ede058834f4d84e73e8ccd800876b48eef0485a89026d5fdb5a405817cdc9a18625bf unsigned int e[128] = { 0x10001, }; unsigned int d[128] = { 0xaeea631, 0xd7fc4dc0, 0x1d123144, 0x1a5e6976, 0x5db48a55, 0x0b589255, 0x19ff86f0, 0x20034728, 0x6335b9b9, 0x44e9497e, 0xa077a4d2, 0x00ce9169, 0x44ac692b, 0xd9f69a42, 0x36fe5db1, 0x0dd9fc03, 0xdd32b7a8, 0x30cb0173, 0x6fb3a57f, 0x8444a1d6, 0x71bdd3c2, 0x3c2c16f5, 0xa9f02acc, 0x5a44adf7, 0xf56e0c46, 0x1c3c259f, 0x95428e8a, 0xdb4d090e, 0x3dd2c8bc, 0x6ebf89d0, 0x111634df, 0x96e71dbc, 0x0b106549, 0xf46e8c42, 0xb384393d, 0x94bc8549, 0x99871f82, 0xbf21a464, 0x5b654943, 0x34788ca4, 0x82c141e6, 0x72429b30, 0x8f70bd93, 0x1a8cbc4f, 0x22f010d7, 0x66d5aff3, 0xbd224fa4, 0xe1b078e9, 0x62760120, 0xc976d469, 0xdb202204, 0xf10868fd, 0x4a6b6a6d, 0xbcfcf500, 0xa264fd37, 0x872942bc, 0x127e4c36, 0x3097b32e, 0x1dccf20b, 0xa328a316, 0x30fd2686, 0x9708106a, 0x041c954b, 0x643eb7d9, }; unsigned int n[128] = { 0xa18625bf, 0x5817cdc9, 0x5fdb5a40, 0x5a89026d, 0x48eef048, 0xd800876b, 0x4e73e8cc, 0x8834f4d8, 0x954ede05, 0xf81136e3, 0x21731c7f, 0x9f3ac4b8, 0x0a0c1e9d, 0x78067bfc, 0xed4cf0a3, 0x580f672c, 0x606ac075, 0xd2e34abf, 0x65f7e6fa, 0xcacd747d, 0x8a3be3dc, 0xe0d2c8fa, 0x5f26c066, 0xab7e680c, 0xb5495773, 0x427586da, 0x9c6d8db3, 0x585cbae2, 0x028914ce, 0x62b98527, 0x69d3cdab, 0x3914ffc3, 0x94b558b3, 0xe2aefe22, 0x71c684a0, 0x6cec82aa, 0x0891054f, 0x0546d1ef, 0x38a8caba, 0x839ace1f, 0x93f491e1, 0xedb9cf8a, 0x0c774097, 0xb0c31b64, 0x0d3c7a32, 0x81d2cf76, 0x6dc5c539, 0x37f8baa8, 0xe7117a12, 0xf1424a08, 0x36533bdc, 0x1fd4d46d, 0xbec85374, 0x2f85bfaa, 0x9e0cb5b1, 0xa88132e5, 0xd03c8ffd, 0x0581a64e, 0x494f2455, 0x2145984b, 0x1d789498, 0x69187c87, 0xfdecc13f, 0xc7e849f7, }; Input data: c17672af76117cfc9cfb4e5d59312f0e30a7df4e358141c019881afc39a4a09b RSA Encrypt: b762afd2b4c50f73a1c48dcbee0c426d29c994eb4a7c221d58114e8ec0be3590a8a4a38f2e4140f309813bed750cde403944c40e71797117f749fa9f9167de82fc3f629eb018c450474365c9a6b24290f775af3e31472fbd2502f57bd8f9c604b2f57c5957fdb048091aa19a158ff1005ab8033e7a0194fbb2a163028db2e1076a72f810ea3dfb7c181b0dd39d310a56c3298a5282fe3d84fd707e03b5ecf7de61fa073f14f0eccc32e5a1c48c1e35f17e23ba51a2a949b334af044faa3782516048289b46bfecbbe7e037dd4ec3465f86bc375eaa4c5c49f8153449d7f49f7ed461674e0cd9b0a3d654c87a704d802d463027f97e8c01497369a90f91e7e7fe RSA Decrypt: c17672af76117cfc9cfb4e5d59312f0e30a7df4e358141c019881afc39a4a09b ====================================HASH Sigh/Verify==================================== Hash: c17672af76117cfc9cfb4e5d59312f0e30a7df4e358141c019881afc39a4a09b unsigned int in[128] = { 0xaf7276c1, 0xfc7c1176, 0x5d4efb9c, 0x0e2f3159, 0x4edfa730, 0xc0418135, 0xfc1a8819, 0x9ba0a439, }; Signature: 9e28af8d9c7bcdc648baad6acbdcea1eb56d93bc827e2b10e7c2c8ef6a4eb7e5971d1e3e6d7c4711b448dd3fa2824b24f4485c541784e920bf9f78762db85ea220a2a5cc7c4a34fe3e0bc8b83dc85d2dbeb42e8aed2c70dc29128137bc34c5e39ce852bb031d344065766009f2f67a23999f5fc25afbbbdaccdc2ad0b6d9140425dbeedcedbe7c7c71c39b56883c2912e49ec55133fdfd018ae5f353a31a7cfbebd6696cf53ad6595dfab168d81a9512916b934078837fbe7d3cc7c8375f80b3071eb102282b88a1018f9b69d54c7fb03b58e699add47a7b1b383af891ba21500a4d97e1646d3d1c08a047a9434d36c591c726548bf75839414fe3fb989f6ea7 unsigned int out[128] = { 0x989f6ea7, 0x414fe3fb, 0x8bf75839, 0x91c72654, 0x434d36c5, 0x08a047a9, 0x646d3d1c, 0x0a4d97e1, 0x91ba2150, 0x1b383af8, 0xadd47a7b, 0x3b58e699, 0xd54c7fb0, 0x018f9b69, 0x282b88a1, 0x071eb102, 0x375f80b3, 0x7d3cc7c8, 0x78837fbe, 0x916b9340, 0xd81a9512, 0x5dfab168, 0xf53ad659, 0xebd6696c, 0xa31a7cfb, 0x8ae5f353, 0x33fdfd01, 0xe49ec551, 0x883c2912, 0x71c39b56, 0xedbe7c7c, 0x25dbeedc, 0xb6d91404, 0xccdc2ad0, 0x5afbbbda, 0x999f5fc2, 0xf2f67a23, 0x65766009, 0x031d3440, 0x9ce852bb, 0xbc34c5e3, 0x29128137, 0xed2c70dc, 0xbeb42e8a, 0x3dc85d2d, 0x3e0bc8b8, 0x7c4a34fe, 0x20a2a5cc, 0x2db85ea2, 0xbf9f7876, 0x1784e920, 0xf4485c54, 0xa2824b24, 0xb448dd3f, 0x6d7c4711, 0x971d1e3e, 0x6a4eb7e5, 0xe7c2c8ef, 0x827e2b10, 0xb56d93bc, 0xcbdcea1e, 0x48baad6a, 0x9c7bcdc6, 0x9e28af8d, }; Verification passed. Process finished with exit code 0
修改RSA.py中的class RsaKey,导出dp和dq:
@property def p(self): if not self.has_private(): raise AttributeError("No CRT component 'p' available for public keys") return int(self._p) @property def dp(self): if not self.has_private(): raise AttributeError("No CRT component 'dp' available for public keys") return int(self._dp) @property def q(self): if not self.has_private(): raise AttributeError("No CRT component 'q' available for public keys") return int(self._q) @property def dq(self): if not self.has_private(): raise AttributeError("No CRT component 'dq' available for public keys") return int(self._dq)
执行如下脚本,输出1024/2048精度的秘钥和明文/密文:

1 # 参考文档:https://blog.csdn.net/weixin_43790276/article/details/100063132 2 # coding=utf-8 3 import os, sys 4 from Crypto import Random 5 from Crypto.PublicKey import RSA 6 from Crypto.Hash import SHA256 7 from Crypto.Cipher import PKCS1_v1_5 as PKCS1_cipher 8 from Crypto.Signature import PKCS1_v1_5 as PKCS1_signature 9 import base64 10 11 rsa_data_c_file = "rsa_data.c" 12 def hex_to_array(array, hex): 13 print("unsigned char %s[] = {" % array, end='') 14 for i in range(int(len(hex) / 2)): 15 print("0x%c%c, " % (hex[i * 2], hex[i * 2 + 1]), end='') 16 print("};") 17 18 def key_int_to_array(array, key): 19 hex_str = str(hex(key)).lstrip('0x') 20 rsa_data_file.write("unsigned int %s[%d] = {\n" % (array, (len(hex_str)+7)/8)) 21 for i in reversed(range(int((len(hex_str)+7) / 8))): 22 rsa_data_file.write("0x%s, " % (hex_str[i*8:(i+1)*8])) 23 if not (i)%8: 24 rsa_data_file.write("\n") 25 rsa_data_file.write("};\n\n") 26 def read_func(param): 27 return b'0' 28 29 def read_func2(param): 30 return b'1' 31 32 def rsa_osr_encrypt_decrypt_sign_verify(width): 33 public_key_file = "public_key_%d.rsa" % (width) 34 private_key_file = "private_key_%d.rsa" % (width) 35 if not (os.path.exists(public_key_file) and os.path.exists(private_key_file)): 36 print("\n====================================Generate RSA key====================================") 37 38 random_generator = Random.new().read 39 rsa = RSA.generate(width, random_generator) 40 41 private_key = rsa.exportKey() 42 with open(private_key_file, 'wb') as f: 43 f.write(private_key) 44 45 public_key = rsa.publickey().exportKey() 46 with open(public_key_file, 'wb') as f: 47 f.write(public_key) 48 49 print("\n====================================Create message data====================================") 50 message = [] 51 for i in range(64): 52 message.append(i) 53 message = bytes(message) 54 55 print("\n====================================RSA Encrypt/Decrypt for OSR====================================") 56 # 使用公钥对内容进行rsa加密 57 with open(public_key_file) as f: 58 key = f.read() 59 pub_key = RSA.importKey(str(key)) 60 cipher = PKCS1_cipher.new(pub_key, read_func) 61 rsa_cipher = cipher.encrypt(message) 62 63 # 使用私钥对内容进行rsa解密 64 with open(private_key_file) as f: 65 key = f.read() 66 pri_key = RSA.importKey(key) 67 rsa_data_file.write("// RSA public key e(%d) = %x\n" % (len(hex(pri_key.e)) - 2, pri_key.e)) 68 key_int_to_array('rsa_%d_key_e' %(width), pri_key.e) 69 rsa_data_file.write("// RSA private key d(%d) = %x\n" % (len(hex(pri_key.d)) - 2, pri_key.d)) 70 key_int_to_array('rsa_%d_key_d' %(width), pri_key.d) 71 rsa_data_file.write("// RSA public module n(%d) = %x\n" % (len(hex(pri_key.n)) - 2, pri_key.n)) 72 key_int_to_array('rsa_%d_key_n' %(width), pri_key.n) 73 rsa_data_file.write("// RSA CRT private key p(%d) = %x\n" % (len(hex(pri_key.p)) - 2, pri_key.p)) 74 key_int_to_array('rsa_%d_key_p' %(width), pri_key.p) 75 rsa_data_file.write("// RSA CRT private key dp(%d) = %x\n" % (len(hex(pri_key.dp)) - 2, pri_key.dp)) 76 key_int_to_array('rsa_%d_key_dp' % (width), pri_key.dp) 77 rsa_data_file.write("// RSA CRT private key q(%d) = %x\n" % (len(hex(pri_key.q)) - 2, pri_key.q)) 78 key_int_to_array('rsa_%d_key_q' %(width), pri_key.q) 79 rsa_data_file.write("// RSA CRT private key dq(%d) = %x\n" % (len(hex(pri_key.dq)) - 2, pri_key.dq)) 80 key_int_to_array('rsa_%d_key_dq' %(width), pri_key.dq) 81 rsa_data_file.write("// RSA CRT private key u(%d) = %x\n" % (len(hex(pri_key.u)) - 2, pri_key.u)) 82 key_int_to_array('rsa_%d_key_u' %(width), pri_key.u) 83 84 cipher = PKCS1_cipher.new(pri_key, read_func2) 85 rsa_replain = cipher.decrypt(rsa_cipher, 0) 86 87 if message == rsa_replain: 88 print("Decryption passed.") 89 else: 90 print("Decryption failed.") 91 rsa_data_file.write("// Input data: %s\n" % message.hex()) 92 key_int_to_array('rsa_%d_plain' %(width), int.from_bytes(message, byteorder='little', signed=False)) 93 rsa_data_file.write("// RSA Encrypt: %s\n" % rsa_cipher.hex()) 94 key_int_to_array('rsa_%d_cipher' %(width), int.from_bytes(rsa_cipher, byteorder='little', signed=False)) 95 rsa_data_file.write("// RSA Decrypt: %s\n" % rsa_replain.hex()) 96 key_int_to_array('rsa_%d_replain' %(width), int.from_bytes(rsa_replain, byteorder='little', signed=False)) 97 98 print("\n====================================HASH Sigh/Verify for OSR====================================") 99 # Generate SHA256 hash of message. 100 digest = SHA256.new() 101 digest.update(message) 102 rsa_data_file.write("// Hash: %s\n" % digest.digest().hex()) 103 key_int_to_array('rsa_%d_sha256_digest' % (width), int.from_bytes(digest.digest(), byteorder='little', signed=False)) 104 105 # 使用私钥生成签名 106 with open(private_key_file) as f: 107 key = f.read() 108 pri_key = RSA.importKey(key) 109 signer = PKCS1_signature.new(pri_key) 110 signature = signer.sign(digest) 111 rsa_data_file.write("// Signature: %s\n" % signature.hex()) 112 key_int_to_array('rsa_%d_signature' % (width), int(signature.hex(), 16)) 113 114 # 使用公钥验证签名 115 with open(public_key_file) as f: 116 key = f.read() 117 pub_key = RSA.importKey(key) 118 verifier = PKCS1_signature.new(pub_key) 119 if verifier.verify(digest, signature): 120 print("Verification passed.") 121 else: 122 print("Verification failed.") 123 124 if __name__ == '__main__': 125 rsa_data_file = open(rsa_data_c_file, 'w') 126 127 print("\nPKA RSA 1024 Encryption/Decryption/Sign/Verify.") 128 rsa_osr_encrypt_decrypt_sign_verify(1024) 129 print("\nPKA RSA 2048 Encryption/Decryption/Sign/Verify.") 130 rsa_osr_encrypt_decrypt_sign_verify(2048) 131 132 rsa_data_file.close()
得到结果如下:

// RSA public key e(5) = 10001 unsigned int rsa_1024_key_e[1] = { 0x10001, }; // RSA private key d(256) = 3fcb66fa38a909e6d080a4eef90073796c13d96578366263cb93fcf760a0c3cd4a279be6f060f3b90760b01a55e5d237c2176c7bb1cb9f23d6593b980b96a2e1d87b034c776d9819832f00b7ed39a9da32d910b2fb20fa987f7a5110e94441b873d25c3a1c715e75194661f63d5e4a9a3478bcfea2e90d7b18c169ece09a5a79 unsigned int rsa_1024_key_d[32] = { 0xe09a5a79, 0x18c169ec, 0xa2e90d7b, 0x3478bcfe, 0x3d5e4a9a, 0x194661f6, 0x1c715e75, 0x73d25c3a, 0xe94441b8, 0x7f7a5110, 0xfb20fa98, 0x32d910b2, 0xed39a9da, 0x832f00b7, 0x776d9819, 0xd87b034c, 0x0b96a2e1, 0xd6593b98, 0xb1cb9f23, 0xc2176c7b, 0x55e5d237, 0x0760b01a, 0xf060f3b9, 0x4a279be6, 0x60a0c3cd, 0xcb93fcf7, 0x78366263, 0x6c13d965, 0xf9007379, 0xd080a4ee, 0x38a909e6, 0x3fcb66fa, }; // RSA public module n(256) = bb5de69865ea0c404634ca5f61f254817f6df291b8803f7215562a6540af2b3abd433aedfdc007a3fab2474d768f5138a7c424790a10ab41cd12e7fdb233557bb8bb66bc7b945c1d41ab0f15bc2fb37d3e6fa8eb7d956fc9ab7a223543ae36c03ced0c30509a59503b1bee4468bf92fadc434a183888170169c98e878483b895 unsigned int rsa_1024_key_n[32] = { 0x8483b895, 0x69c98e87, 0x38881701, 0xdc434a18, 0x68bf92fa, 0x3b1bee44, 0x509a5950, 0x3ced0c30, 0x43ae36c0, 0xab7a2235, 0x7d956fc9, 0x3e6fa8eb, 0xbc2fb37d, 0x41ab0f15, 0x7b945c1d, 0xb8bb66bc, 0xb233557b, 0xcd12e7fd, 0x0a10ab41, 0xa7c42479, 0x768f5138, 0xfab2474d, 0xfdc007a3, 0xbd433aed, 0x40af2b3a, 0x15562a65, 0xb8803f72, 0x7f6df291, 0x61f25481, 0x4634ca5f, 0x65ea0c40, 0xbb5de698, }; // RSA CRT private key p(128) = bd681ecb6006e76ea725e770f973ab44532c6378f95b11748ef055423b45b4d9c10f2d1890a68aa66462ed6310f419308c26e2ed4ba22b373f1478aad9a607f3 unsigned int rsa_1024_key_p[16] = { 0xd9a607f3, 0x3f1478aa, 0x4ba22b37, 0x8c26e2ed, 0x10f41930, 0x6462ed63, 0x90a68aa6, 0xc10f2d18, 0x3b45b4d9, 0x8ef05542, 0xf95b1174, 0x532c6378, 0xf973ab44, 0xa725e770, 0x6006e76e, 0xbd681ecb, }; // RSA CRT private key dp(127) = 2d8055e585ac22ecf23aa8defb0e4e969b648e8101665f4b210b9b6fcdcd7124debc46992026e22816f5ad119f81048c251f3264cf46a61b1f8c4b70bfd8a31 unsigned int rsa_1024_key_dp[16] = { 0xbfd8a31, 0x1f8c4b70, 0xcf46a61b, 0x251f3264, 0x9f81048c, 0x16f5ad11, 0x2026e228, 0xdebc4699, 0xcdcd7124, 0x210b9b6f, 0x01665f4b, 0x9b648e81, 0xfb0e4e96, 0xf23aa8de, 0x85ac22ec, 0x2d8055e5, }; // RSA CRT private key q(128) = fd3e2c873adf42cf31ad6cc4557f37025ec12d4ef41044632d128c468cb8529440dd7b178efe428df0bf9ed3ff1afb37fa954ebcf9100b44d4500cb9f7db2757 unsigned int rsa_1024_key_q[16] = { 0xf7db2757, 0xd4500cb9, 0xf9100b44, 0xfa954ebc, 0xff1afb37, 0xf0bf9ed3, 0x8efe428d, 0x40dd7b17, 0x8cb85294, 0x2d128c46, 0xf4104463, 0x5ec12d4e, 0x557f3702, 0x31ad6cc4, 0x3adf42cf, 0xfd3e2c87, }; // RSA CRT private key dq(128) = ca32a54d0805910b6be7c38b73945270b3055ccec87260982b39bf04e9809676c6dfd0537c19a93c39b855f180a3a3680bccc104837c7af2e6ee4f6b00ea5b9b unsigned int rsa_1024_key_dq[16] = { 0x00ea5b9b, 0xe6ee4f6b, 0x837c7af2, 0x0bccc104, 0x80a3a368, 0x39b855f1, 0x7c19a93c, 0xc6dfd053, 0xe9809676, 0x2b39bf04, 0xc8726098, 0xb3055cce, 0x73945270, 0x6be7c38b, 0x0805910b, 0xca32a54d, }; // RSA CRT private key u(128) = 2da62a0b95a138aefafd04ff0afbff9edbff1a4db8cbc005b653c368156cb78d3be74ee32f7e74e16fc11dd9d492c7a6613dcbffa23b27df630b8d2e93fc695c unsigned int rsa_1024_key_u[16] = { 0x93fc695c, 0x630b8d2e, 0xa23b27df, 0x613dcbff, 0xd492c7a6, 0x6fc11dd9, 0x2f7e74e1, 0x3be74ee3, 0x156cb78d, 0xb653c368, 0xb8cbc005, 0xdbff1a4d, 0x0afbff9e, 0xfafd04ff, 0x95a138ae, 0x2da62a0b, }; // Input data: 000102030405060708090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f202122232425262728292a2b2c2d2e2f303132333435363738393a3b3c3d3e3f unsigned int rsa_1024_plain[16] = { 0x03020100, 0x07060504, 0x0b0a0908, 0x0f0e0d0c, 0x13121110, 0x17161514, 0x1b1a1918, 0x1f1e1d1c, 0x23222120, 0x27262524, 0x2b2a2928, 0x2f2e2d2c, 0x33323130, 0x37363534, 0x3b3a3938, 0x3f3e3d3c, }; // RSA Encrypt: 7c71cd9e648da2b94beea422bc03c1193c63ae58e2aa057ff4d86da31c42e9edc2126aa612a3ee57f5f1bdfcc30d962aa80d5858d490cd6a3fe871342a5b6cd65817e3cb942a781c251268f77b726632741fcf5caa0cefa941b92ae1285ded095c9e92f83c874b05cf818033994aca954dd0a82a4a9a7b78dc4f84052415cb90 unsigned int rsa_1024_cipher[32] = { 0x9ecd717c, 0xb9a28d64, 0x22a4ee4b, 0x19c103bc, 0x58ae633c, 0x7f05aae2, 0xa36dd8f4, 0xede9421c, 0xa66a12c2, 0x57eea312, 0xfcbdf1f5, 0x2a960dc3, 0x58580da8, 0x6acd90d4, 0x3471e83f, 0xd66c5b2a, 0xcbe31758, 0x1c782a94, 0xf7681225, 0x3266727b, 0x5ccf1f74, 0xa9ef0caa, 0xe12ab941, 0x09ed5d28, 0xf8929e5c, 0x054b873c, 0x338081cf, 0x95ca4a99, 0x2aa8d04d, 0x787b9a4a, 0x05844fdc, 0x90cb1524, }; // RSA Decrypt: 000102030405060708090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f202122232425262728292a2b2c2d2e2f303132333435363738393a3b3c3d3e3f unsigned int rsa_1024_replain[16] = { 0x03020100, 0x07060504, 0x0b0a0908, 0x0f0e0d0c, 0x13121110, 0x17161514, 0x1b1a1918, 0x1f1e1d1c, 0x23222120, 0x27262524, 0x2b2a2928, 0x2f2e2d2c, 0x33323130, 0x37363534, 0x3b3a3938, 0x3f3e3d3c, }; // Hash: fdeab9acf3710362bd2658cdc9a29e8f9c757fcf9811603a8c447cd1d9151108 unsigned int rsa_1024_sha256_digest[8] = { 0xcb9eafd, 0x20371f3a, 0xd5826bd6, 0xf9ea2c9c, 0xf7f759c8, 0xa601198c, 0x17c448c3, 0x81115d9d, }; // Signature: 517db104fa62955739034d6c62b5c05b34f6b12257c90d0e45bd78205bc5440e54c47aaee07f6deb50c96ea9a32e4eb9584770d9dfc65135fb4cbac52fe87c838c57af29d7943d2c800d538ca09715ee1924c700a54c7806c4ded0cacd7b4b5e5c7bc55fb866b23e554c8e601331d2053b22dec6b3fcecd6233a5d550bb0327f unsigned int rsa_1024_signature[32] = { 0x0bb0327f, 0x233a5d55, 0xb3fcecd6, 0x3b22dec6, 0x1331d205, 0x554c8e60, 0xb866b23e, 0x5c7bc55f, 0xcd7b4b5e, 0xc4ded0ca, 0xa54c7806, 0x1924c700, 0xa09715ee, 0x800d538c, 0xd7943d2c, 0x8c57af29, 0x2fe87c83, 0xfb4cbac5, 0xdfc65135, 0x584770d9, 0xa32e4eb9, 0x50c96ea9, 0xe07f6deb, 0x54c47aae, 0x5bc5440e, 0x45bd7820, 0x57c90d0e, 0x34f6b122, 0x62b5c05b, 0x39034d6c, 0xfa629557, 0x517db104, }; // RSA public key e(5) = 10001 unsigned int rsa_2048_key_e[1] = { 0x10001, }; // RSA private key d(512) = 3613c8f666d1c5971b06ac845cdc5ba833043119a4e8d647c05b119cd9024033e0e691828a6a5f2ca2d0da5c9812598df979dfbf4d22a5b49962f856071ee19a13cb6a9f2c0c9f1239f05b437d5a550e24af796907f5c9edce31b5a3ad8903bc541efff7f1903904265fea957af7fe9911369f9bbf0b021ad66073a6ee0dbbeb4cc29b7d5bc6376fd5b93d6a1b58d211159bb4167da113b3250a52a32e65dc6f35c6b385c11c34d5518771657b4bf0ec576be751d2f32fabaa8c57ba75b13242618a74d13cef8e9241bbad6adf280c933a4a0115c355ede682dc0a727b1a07286ac41b63f84d5b7e1430732f7a439a7ca33c4864b5460f14f548f91fa6acc7a5 unsigned int rsa_2048_key_d[64] = { 0xa6acc7a5, 0xf548f91f, 0xb5460f14, 0xa33c4864, 0x7a439a7c, 0x1430732f, 0xf84d5b7e, 0x6ac41b63, 0x7b1a0728, 0x82dc0a72, 0xc355ede6, 0x3a4a0115, 0xdf280c93, 0x41bbad6a, 0x3cef8e92, 0x618a74d1, 0x75b13242, 0xaa8c57ba, 0xd2f32fab, 0x576be751, 0x7b4bf0ec, 0x51877165, 0xc11c34d5, 0x35c6b385, 0x2e65dc6f, 0x250a52a3, 0x7da113b3, 0x159bb416, 0x1b58d211, 0xd5b93d6a, 0x5bc6376f, 0x4cc29b7d, 0xee0dbbeb, 0xd66073a6, 0xbf0b021a, 0x11369f9b, 0x7af7fe99, 0x265fea95, 0xf1903904, 0x541efff7, 0xad8903bc, 0xce31b5a3, 0x07f5c9ed, 0x24af7969, 0x7d5a550e, 0x39f05b43, 0x2c0c9f12, 0x13cb6a9f, 0x071ee19a, 0x9962f856, 0x4d22a5b4, 0xf979dfbf, 0x9812598d, 0xa2d0da5c, 0x8a6a5f2c, 0xe0e69182, 0xd9024033, 0xc05b119c, 0xa4e8d647, 0x33043119, 0x5cdc5ba8, 0x1b06ac84, 0x66d1c597, 0x3613c8f6, }; // RSA public module n(512) = 96d8b41274aaca7e378ea19cc30707398b678532cae71c1a286115a228782d16f9c71802c9e21b7aef971ac2aa2cfc77bd023b0f2391ea0ecc499c8a2de4c741fc6e72b5da7b74737d13f82cc4a6ef08ce8593c088ab2d75b7d4538b8df7dfd961e673101ad997854d71fa998e08010396964cbee86f326e64f1fb7e3ec7b19bc2fb83ff63eee9805f76cb09888477bb4e8ebabe112ffa56a7f04404e0d5828b4e9a027a9ffc3cfcb1e79a0db867cb16fa77dadffdd33a3861f16800bae63cc152c948e7087d18d8386aa390596a2c6dd620cd34826d37365dbcfe44fe91364d207813e73713a0168e42213ac6a83fc9dc58054e45812b71f9ca2eda3db8a623 unsigned int rsa_2048_key_n[64] = { 0x3db8a623, 0xf9ca2eda, 0x45812b71, 0xdc58054e, 0xc6a83fc9, 0x8e42213a, 0x3713a016, 0x207813e7, 0xfe91364d, 0x5dbcfe44, 0x826d3736, 0xd620cd34, 0x596a2c6d, 0x386aa390, 0x087d18d8, 0x52c948e7, 0xbae63cc1, 0x61f16800, 0xfdd33a38, 0xfa77dadf, 0xb867cb16, 0xb1e79a0d, 0x9ffc3cfc, 0x4e9a027a, 0xe0d5828b, 0xa7f04404, 0x112ffa56, 0x4e8ebabe, 0x888477bb, 0x5f76cb09, 0x63eee980, 0xc2fb83ff, 0x3ec7b19b, 0x64f1fb7e, 0xe86f326e, 0x96964cbe, 0x8e080103, 0x4d71fa99, 0x1ad99785, 0x61e67310, 0x8df7dfd9, 0xb7d4538b, 0x88ab2d75, 0xce8593c0, 0xc4a6ef08, 0x7d13f82c, 0xda7b7473, 0xfc6e72b5, 0x2de4c741, 0xcc499c8a, 0x2391ea0e, 0xbd023b0f, 0xaa2cfc77, 0xef971ac2, 0xc9e21b7a, 0xf9c71802, 0x28782d16, 0x286115a2, 0xcae71c1a, 0x8b678532, 0xc3070739, 0x378ea19c, 0x74aaca7e, 0x96d8b412, }; // RSA CRT private key p(256) = c2448e6340d1cf4674ba610a80c1e68cc1a5ecfba59ce8fc291007f0652b9c6423272a64b96d00bdaa0ac24176ca7b1e75bada9ff8db43fe75fb6d28e4dbaf0ff93fad6e1f1b96b2a18a56fde7913409b36620db2826fc1ee7797a64d7a18f9a344b1f04f27c03e0bfed8f11720ea072673db16dcd75e902114595423b01fa8f unsigned int rsa_2048_key_p[32] = { 0x3b01fa8f, 0x11459542, 0xcd75e902, 0x673db16d, 0x720ea072, 0xbfed8f11, 0xf27c03e0, 0x344b1f04, 0xd7a18f9a, 0xe7797a64, 0x2826fc1e, 0xb36620db, 0xe7913409, 0xa18a56fd, 0x1f1b96b2, 0xf93fad6e, 0xe4dbaf0f, 0x75fb6d28, 0xf8db43fe, 0x75bada9f, 0x76ca7b1e, 0xaa0ac241, 0xb96d00bd, 0x23272a64, 0x652b9c64, 0x291007f0, 0xa59ce8fc, 0xc1a5ecfb, 0x80c1e68c, 0x74ba610a, 0x40d1cf46, 0xc2448e63, }; // RSA CRT private key dp(256) = af65bc754a99e41e05d81d33a16af02097da9aabde2c5c8307040d56f3d13b438225a3760ba0a9f1946c605540ceb1f89f6d14652907b74d30f2cfed032c81d3d743b1ef6230c390069fe3c91ce191ed4c476254dcdccdf78d20b5ec04703f3a880a67384d42c13193b805db47728354a77821113557470871d5b45c76f0636b unsigned int rsa_2048_key_dp[32] = { 0x76f0636b, 0x71d5b45c, 0x35574708, 0xa7782111, 0x47728354, 0x93b805db, 0x4d42c131, 0x880a6738, 0x04703f3a, 0x8d20b5ec, 0xdcdccdf7, 0x4c476254, 0x1ce191ed, 0x069fe3c9, 0x6230c390, 0xd743b1ef, 0x032c81d3, 0x30f2cfed, 0x2907b74d, 0x9f6d1465, 0x40ceb1f8, 0x946c6055, 0x0ba0a9f1, 0x8225a376, 0xf3d13b43, 0x07040d56, 0xde2c5c83, 0x97da9aab, 0xa16af020, 0x05d81d33, 0x4a99e41e, 0xaf65bc75, }; // RSA CRT private key q(256) = c6c7e0e15cf320cbcb06ff2ec90daa18d251fe42f9ed3daa71910ce0b5a44747d9b90e4468d2d8bf62349467e9517900ae723666cbc21700e7b779f724435b117e88234bde9cbd685cfae7e9a826427cce5a296c5873dc84de17bdecb864f90ab6bc2f5b78279f22f156e4a838eae0bb7b58e2f7245bc74016214c7af280352d unsigned int rsa_2048_key_q[32] = { 0xf280352d, 0x16214c7a, 0x245bc740, 0x7b58e2f7, 0x38eae0bb, 0xf156e4a8, 0x78279f22, 0xb6bc2f5b, 0xb864f90a, 0xde17bdec, 0x5873dc84, 0xce5a296c, 0xa826427c, 0x5cfae7e9, 0xde9cbd68, 0x7e88234b, 0x24435b11, 0xe7b779f7, 0xcbc21700, 0xae723666, 0xe9517900, 0x62349467, 0x68d2d8bf, 0xd9b90e44, 0xb5a44747, 0x71910ce0, 0xf9ed3daa, 0xd251fe42, 0xc90daa18, 0xcb06ff2e, 0x5cf320cb, 0xc6c7e0e1, }; // RSA CRT private key dq(256) = 4860427b0bd2e260115e4ccf8618d9940c101a99dc520b1fe215c43095326959b9e66d516f314605f905d7fb35b29a722b121ec8b2ebca6063fe24045e49c000d0a754e2acfd38e1a4e91e43af1baf1dae2c99e47f1840748840f0c01e2b7599f70af1db46167714cbf6ad6eaabaaa74d8e6764d3209d0b47eda44f487133349 unsigned int rsa_2048_key_dq[32] = { 0x87133349, 0x7eda44f4, 0x3209d0b4, 0xd8e6764d, 0xaabaaa74, 0xcbf6ad6e, 0x46167714, 0xf70af1db, 0x1e2b7599, 0x8840f0c0, 0x7f184074, 0xae2c99e4, 0xaf1baf1d, 0xa4e91e43, 0xacfd38e1, 0xd0a754e2, 0x5e49c000, 0x63fe2404, 0xb2ebca60, 0x2b121ec8, 0x35b29a72, 0xf905d7fb, 0x6f314605, 0xb9e66d51, 0x95326959, 0xe215c430, 0xdc520b1f, 0x0c101a99, 0x8618d994, 0x115e4ccf, 0x0bd2e260, 0x4860427b, }; // RSA CRT private key u(256) = 1a38a4e7579655b3babf5638feb504190fa60871b2350022f661653dc2711424d2d093966a73bcf52ea8839fe5198e97cde80e5b67521d66ac0580d7889efc516096784124048e715956d058a3a915d686fd8667c94a50f45f1ea0a4ca1ecc06319701751a7edabf84e5b387bb6610c496ce3c97b35606f60b8ec64f206be2cf unsigned int rsa_2048_key_u[32] = { 0x206be2cf, 0x0b8ec64f, 0xb35606f6, 0x96ce3c97, 0xbb6610c4, 0x84e5b387, 0x1a7edabf, 0x31970175, 0xca1ecc06, 0x5f1ea0a4, 0xc94a50f4, 0x86fd8667, 0xa3a915d6, 0x5956d058, 0x24048e71, 0x60967841, 0x889efc51, 0xac0580d7, 0x67521d66, 0xcde80e5b, 0xe5198e97, 0x2ea8839f, 0x6a73bcf5, 0xd2d09396, 0xc2711424, 0xf661653d, 0xb2350022, 0x0fa60871, 0xfeb50419, 0xbabf5638, 0x579655b3, 0x1a38a4e7, }; // Input data: 000102030405060708090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f202122232425262728292a2b2c2d2e2f303132333435363738393a3b3c3d3e3f unsigned int rsa_2048_plain[16] = { 0x03020100, 0x07060504, 0x0b0a0908, 0x0f0e0d0c, 0x13121110, 0x17161514, 0x1b1a1918, 0x1f1e1d1c, 0x23222120, 0x27262524, 0x2b2a2928, 0x2f2e2d2c, 0x33323130, 0x37363534, 0x3b3a3938, 0x3f3e3d3c, }; // RSA Encrypt: 4713047edb664d720a92cc7368b42ca8d17fff60715b75f91b27a06b3dcd8a336cf051d88f71f1d12cf1222f1d3a072b702c529faa356080f3f47cafd3a8fd58ca34b4ab209b23d38cd0d3e32b222fa9f6bcd27eafe89def8f4e14f1b2255caffa0c872f550ab66bf2e5bb280887e4db4eb8908d8d7d7850ef4e1e42c713b3a10557c331c5a5e5ed8bce770ed5c3a93d5089dbe375eedd9729b85005e8de958360ee832b8d1bcf1a6293d6241d88c633ee82dd9b4148d2ec8f4c4b698b0ac06b8b5225816b9fcee3468a05009e201d7070de7e4fbd1ebd7fec8d627eb12b8a652eeb46bd0e84316d2eeeb82591b7e71c7e8c3a0915e3f2af1b3ee4d47e9dc27a unsigned int rsa_2048_cipher[64] = { 0x7e041347, 0x724d66db, 0x73cc920a, 0xa82cb468, 0x60ff7fd1, 0xf9755b71, 0x6ba0271b, 0x338acd3d, 0xd851f06c, 0xd1f1718f, 0x2f22f12c, 0x2b073a1d, 0x9f522c70, 0x806035aa, 0xaf7cf4f3, 0x58fda8d3, 0xabb434ca, 0xd3239b20, 0xe3d3d08c, 0xa92f222b, 0x7ed2bcf6, 0xef9de8af, 0xf1144e8f, 0xaf5c25b2, 0x2f870cfa, 0x6bb60a55, 0x28bbe5f2, 0xdbe48708, 0x8d90b84e, 0x50787d8d, 0x421e4eef, 0xa1b313c7, 0x31c35705, 0xede5a5c5, 0x0e77ce8b, 0x3da9c3d5, 0xe3db8950, 0x97ddee75, 0x0550b829, 0x8395dee8, 0x2b83ee60, 0x1acf1b8d, 0x24d69362, 0x33c6881d, 0x9bdd82ee, 0xecd24841, 0x694b4c8f, 0x6bc00a8b, 0x8125528b, 0xe3ce9f6b, 0x00058a46, 0x701d209e, 0x4f7ede70, 0x7fbd1ebd, 0x7e628dec, 0x658a2bb1, 0xbd46eb2e, 0x6d31840e, 0x25b8ee2e, 0x1ce7b791, 0x093a8c7e, 0xaff2e315, 0xd4e43e1b, 0x7ac29d7e, }; // RSA Decrypt: 000102030405060708090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f202122232425262728292a2b2c2d2e2f303132333435363738393a3b3c3d3e3f unsigned int rsa_2048_replain[16] = { 0x03020100, 0x07060504, 0x0b0a0908, 0x0f0e0d0c, 0x13121110, 0x17161514, 0x1b1a1918, 0x1f1e1d1c, 0x23222120, 0x27262524, 0x2b2a2928, 0x2f2e2d2c, 0x33323130, 0x37363534, 0x3b3a3938, 0x3f3e3d3c, }; // Hash: fdeab9acf3710362bd2658cdc9a29e8f9c757fcf9811603a8c447cd1d9151108 unsigned int rsa_2048_sha256_digest[8] = { 0xcb9eafd, 0x20371f3a, 0xd5826bd6, 0xf9ea2c9c, 0xf7f759c8, 0xa601198c, 0x17c448c3, 0x81115d9d, }; // Signature: 425ae076ebb33a3a38cb0903a9ec7ecb8ce047d9a8c1bf129878986c37f298753e9add2fa0fe8c5a2aa7d1cef6b7da5a8df76a4ea1acff8cdfbf00a23cce6af2511f24c3607a87bb2d71d13ff068dbdec52db9abef95c0240ec907faa3a50cba210ec2027ab06d2933db3a363353915d7819d2d42cf469cc872075d937d22283f826aa5029c518d54ac8672a1bd226362282af392c5d145d601dd1fdcef6018e3ea1f10bb51ec2fc7f6eb49ba4153fceefabd3876d6e83f8036c65b108de610377c61472d7522c1133da9772b84ac2ed1db8e6a1344129b4d0119bc5480258c83703e66bae31e2a6a51ef5dd2f60a822d79384ba3c1d1accad78b8a7b4bba97f unsigned int rsa_2048_signature[64] = { 0xb4bba97f, 0xad78b8a7, 0x3c1d1acc, 0xd79384ba, 0x2f60a822, 0xa51ef5dd, 0xae31e2a6, 0x3703e66b, 0x480258c8, 0xd0119bc5, 0x344129b4, 0x1db8e6a1, 0xb84ac2ed, 0x33da9772, 0xd7522c11, 0x77c61472, 0x08de6103, 0x036c65b1, 0x6d6e83f8, 0xefabd387, 0xa4153fce, 0x7f6eb49b, 0xb51ec2fc, 0x3ea1f10b, 0xcef6018e, 0x601dd1fd, 0x2c5d145d, 0x2282af39, 0x1bd22636, 0x4ac8672a, 0x29c518d5, 0xf826aa50, 0x37d22283, 0x872075d9, 0x2cf469cc, 0x7819d2d4, 0x3353915d, 0x33db3a36, 0x7ab06d29, 0x210ec202, 0xa3a50cba, 0x0ec907fa, 0xef95c024, 0xc52db9ab, 0xf068dbde, 0x2d71d13f, 0x607a87bb, 0x511f24c3, 0x3cce6af2, 0xdfbf00a2, 0xa1acff8c, 0x8df76a4e, 0xf6b7da5a, 0x2aa7d1ce, 0xa0fe8c5a, 0x3e9add2f, 0x37f29875, 0x9878986c, 0xa8c1bf12, 0x8ce047d9, 0xa9ec7ecb, 0x38cb0903, 0xebb33a3a, 0x425ae076, };





 浙公网安备 33010602011771号
浙公网安备 33010602011771号