某高校-网络安全实战综合案例
本案例主要以安全为主,路由环境设计较为容易
主要内容包括
1.防火墙安全区域与安全策略
2.防火墙安全策略部署
3.防火墙NAT地址转换
4.防火墙DHCP与PPPoE服务部署
5.防火墙双机热备
6.防火墙URL过滤,反病毒,入侵防御使能
7.IPSEC虚拟私有网络建设
项目描述
本考试共包含如下项目内容:
1.防火墙安全区域与安全策略
2.防火墙安全策略部署
3.防火墙NAT地址转换
4.防火墙DHCP与PPPoE服务部署
5.防火墙双机热备
6.防火墙URL过滤,反病毒,入侵防御使能
7.IPSEC虚拟私有网络建设
----------------------------------------------------------------------------------------------------------------------------------------------
需求一:
1、总部防火墙做双机热备
fw1:
hrp interface GigabitEthernet1/0/2 remote 10.0.0.13
hrp enable
fw2:
hrp interface GigabitEthernet1/0/2 remote 10.0.0.12
hrp enable
2、pc1和pc2分别位于vlan10和vlan20中,主备网关在防火墙1和2上。
fw1:
interface Vlanif10
ip address 10.1.10.12 255.255.255.0
vrrp vrid 1 virtual-ip 10.1.10.254 active
interface Vlanif20
ip address 10.1.20.12 255.255.255.0
vrrp vrid 2 virtual-ip 10.1.20.254 standby
fw2:
interface Vlanif10
ip address 10.1.10.13 255.255.255.0
vrrp vrid 1 virtual-ip 10.1.10.254 standby
interface Vlanif20
ip address 10.1.20.13 255.255.255.0
vrrp vrid 2 virtual-ip 10.1.20.254 active
FW1:
firewall zone trust
add interface Vlanif10
add interface Vlanif20
firewall zone untrust
add interface GigabitEthernet1/0/0
firewall zone dmz
add interface GigabitEthernet1/0/2
3、R1为总部出口路由器,内部pc可以通过155.1.12.16-155.1.12.19来访问外网,pc1访问外网时走FW1,pc2访问外网时走FW2.
fw1:
ospf 1
silent-interface Vlanif10
silent-interface Vlanif20
area 0.0.0.0
network 10.1.121.12 0.0.0.0
area 0.0.0.1
network 10.1.10.12 0.0.0.0
network 10.1.20.12 0.0.0.0
security-policy
rule name locla_to_any
source-zone local
action permit
rule name trust_untrust
source-zone trust
destination-zone untrust
source-address 10.1.10.0 mask 255.255.255.0
source-address 10.1.20.0 mask 255.255.255.0
action permit
fw2:
ospf 1
silent-interface Vlanif10
silent-interface Vlanif20
area 0.0.0.0
network 10.1.131.13 0.0.0.0
area 0.0.0.1
network 10.1.10.13 0.0.0.0
network 10.1.20.13 0.0.0.0
R1:
ip route-static 0.0.0.0 0.0.0.0 155.1.12.2
acl number 3000
rule 5 deny ip source 10.1.0.0 0.0.255.255 destination 172.16.0.0 0.0.255.255 //后续做ipsec vpn不需要做nat
rule 10 permit ip source 10.1.0.0 0.0.255.255
ospf 1
default-route-advertise
area 0.0.0.0
network 10.1.121.1 0.0.0.0
network 10.1.131.1 0.0.0.0
nat address-group 1 155.1.12.16 155.1.12.19
interface GigabitEthernet0/0/0
ip address 155.1.12.1 255.255.255.0
nat outbound 3000 address-group 1
测试:
[R2]:
interface LoopBack0
ip address 155.2.2.2 255.255.255.255
pc1:
PC>tracert 155.2.2.2
traceroute to 155.2.2.2, 8 hops max
(ICMP), press Ctrl+C to stop
1 10.1.10.12 46 ms 32 ms 47 ms
2 * * *
3 155.2.2.2 93 ms 63 ms 47 ms
PC>
pc2:
PC>tracert 155.2.2.2
traceroute to 155.2.2.2, 8 hops max
(ICMP), press Ctrl+C to stop
1 *10.1.20.13 47 ms 31 ms
2 * * *
3 155.2.2.2 32 ms 47 ms 46 ms
PC>
需求二:
配置无线设备上线,直接转发,防火墙与交换机之间运行ospf协议,业务vlan 30,ap的管理vlan 254。
ap与无线设备的网关都在交换机上,防火墙作为ap与无线设备的dhcp服务器。
1、配置vlan与ip地址,接口之间放通相关vlan,开启dhcp功能。
SW2:
vlan batch 8 30 148 254
dhcp enable
interface Vlanif8
ip address 172.16.8.8 255.255.255.0
interface Vlanif30
ip address 172.16.30.8 255.255.255.0
interface Vlanif148
ip address 172.16.148.8 255.255.255.0
interface Vlanif254
ip address 172.16.254.8 255.255.255.0
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 254
port trunk allow-pass vlan all
interface GigabitEthernet0/0/10
port link-type trunk
port trunk allow-pass vlan all
interface GigabitEthernet0/0/24
port link-type access
port default vlan 148
AC:
vlan 8
capwap source interface vlanif8
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan all
FW3:
ip pool ap
gateway-list 172.16.254.8
network 172.16.254.0 mask 255.255.255.0
option 43 sub-option 2 ip-address 172.16.8.10
ip pool sta
gateway-list 172.16.30.8
network 172.16.30.0 mask 255.255.255.0
interface GigabitEthernet1/0/1
ip address 172.16.148.14 255.255.255.0
dhcp select global
interface GigabitEthernet1/0/2
ip address 172.16.0.14 255.255.255.0
firewall zone trust
add interface GigabitEthernet1/0/1
firewall zone dmz
add interface GigabitEthernet1/0/2
备注:G1/0/0接口不加入untrust区域,因为后面要做pppoe,将dialer接口加入untrust区域。
2、配置ospf使设备间互通
sw2:
interface Vlanif8
ospf enable 1 area 0.0.0.0
interface Vlanif30
ospf enable 1 area 0.0.0.0
interface Vlanif148
ospf enable 1 area 0.0.0.0
interface Vlanif254
ospf enable 1 area 0.0.0.0
AC:
ip route-static 0.0.0.0 0.0.0.0 172.16.8.8
fw3:
ospf 1
area 0.0.0.0
network 172.16.0.0 0.0.255.255
security-policy
rule name local_any
source-zone local
action permit
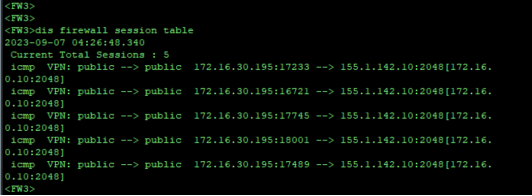
sta上线时防火墙的会话表项:
[FW3]dis firewall session table
2023-09-06 12:56:44.860
Current Total Sessions : 1
bootps VPN: public --> public 172.16.148.14:67 --> 10.1.30.8:67
3、安全部分,分布在sw2做snooping防御dhcp攻击
[SW2]dhcp snooping enable //防御饥饿攻击和欺骗攻击
[SW2-GigabitEthernet0/0/24]dhcp snooping trusted //指定信任接口,防御欺骗攻击
[SW2-vlan30]dhcp snooping enable
[SW2-vlan30]dhcp snooping check dhcp-chaddr enable
[SW2]dhcp snooping user-bind autosave flash:/dhcp1.tbl //将用户的上线信息表保存在文件中
无线用户上线后:
STA>ipconfig
Link local IPv6 address...........: ::
IPv6 address......................: :: / 128
IPv6 gateway......................: ::
IPv4 address......................: 172.16.30.195
Subnet mask.......................: 255.255.255.0
Gateway...........................: 172.16.30.8
Physical address..................: 54-89-98-BC-44-8C
DNS server........................:
[SW2]dis dhcp snooping user-bind all
DHCP Dynamic Bind-table:
Flags:O - outer vlan ,I - inner vlan ,P - map vlan
IP Address MAC Address VSI/VLAN(O/I/P) Interface Lease
--------------------------------------------------------------------------------
172.16.30.195 5489-98bc-448c 30 /-- /-- GE0/0/1 2023.09.08-10:25
--------------------------------------------------------------------------------
print count: 1 total count: 1
[SW2]
4、总部预防用户私接交换机、修改mac地址,防止mac地址欺骗、泛洪攻击等,需配置端口安全。
[SW1]port-group group-member GigabitEthernet 0/0/1 to GigabitEthernet 0/0/2
[SW1-port-group]port-security enable
[SW1-GigabitEthernet0/0/1]port-security enable
[SW1-GigabitEthernet0/0/2]port-security enable
[SW1-port-group]port-security mac-address sticky
[SW1-GigabitEthernet0/0/1]port-security mac-address sticky
[SW1-GigabitEthernet0/0/2]port-security mac-address sticky
[SW1-port-group]port-security protect-action shutdown
[SW1-GigabitEthernet0/0/1]port-security protect-action shutdown
[SW1-GigabitEthernet0/0/2]port-security protect-action shutdown
[SW1-port-group]port-security max-mac-num 2
[SW1-GigabitEthernet0/0/1]port-security max-mac-num 2
[SW1-GigabitEthernet0/0/2]port-security max-mac-num 2
三、广域网部分
1、分部防火墙作为出口设备,使用pppoe进行拨号上网
FW3:
[FW3]int Dialer 1
[FW3-Dialer1]ip address ppp-negotiate
[FW3-Dialer1]ppp chap user huawei
[FW3-Dialer1]ppp chap password cipher Huawei@123
[FW3-Dialer1]dialer user test
[FW3-Dialer1]mtu 1492
[FW3-Dialer1]dialer bundle 1
[FW3-GigabitEthernet1/0/0]pppoe-client dial-bundle-number 1
[FW3-zone-untrust]add interface Dialer 1
R2:
[R2-aaa]local-user huawei password cipher Huawei@123
[R2-aaa]local-user huawei service-type ppp
[R2]INT Virtual-Template 1
[R2-Virtual-Template1]ip address unnumbered interface Ethernet 1/0/0
[R2-Virtual-Template1]ppp authentication-mode chap
[R2-Virtual-Template1]remote address 155.1.142.14
[R2-Ethernet1/0/0]pppoe-server bind virtual-template 1
检查fw3的dialer 1接口ip地址获取情况:
[FW2]dis pppoe-client session summary
2023-09-09 02:21:49.360
PPPoE Client Session:
ID Bundle Dialer Intf Client-MAC Server-MAC State
1 1 1 GE1/0/0 00e0fc9e0d36 00e0fcf847bc PPPUP
[FW3]dis ip int b
2023-09-06 13:38:58.250
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
(d): Dampening Suppressed
(E): E-Trunk down
The number of interface that is UP in Physical is 6
The number of interface that is DOWN in Physical is 5
The number of interface that is UP in Protocol is 5
The number of interface that is DOWN in Protocol is 6
Interface IP Address/Mask Physical Protocol
Dialer1 155.1.142.14/32 up up(s)
为了分支可以访问外网,在防火墙上添加默认路由:
[FW3]ip route-static 0.0.0.0 0 Dialer 1
[FW3]ping -c 1 155.2.2.2
PING 155.2.2.2: 56 data bytes, press CTRL_C to break
Reply from 155.2.2.2: bytes=56 Sequence=1 ttl=255 time=15 ms
--- 155.2.2.2 ping statistics ---
1 packet(s) transmitted
1 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/15/15 ms
分支pc通过NAT访问外网,分支与总部之间需要建立ipsec vpn实现安全访问。
FW3:
nat-policy
rule name no_nat //分支与总部之间不需要做nat转换,需要做ipsec vpn
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.0.0
destination-address 10.1.0.0 mask 255.255.0.0
action no-nat
rule name in_out //访问外网则使用easy-ip
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.0.0
action source-nat easy-ip
rule name in_out
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.0.0
action permit
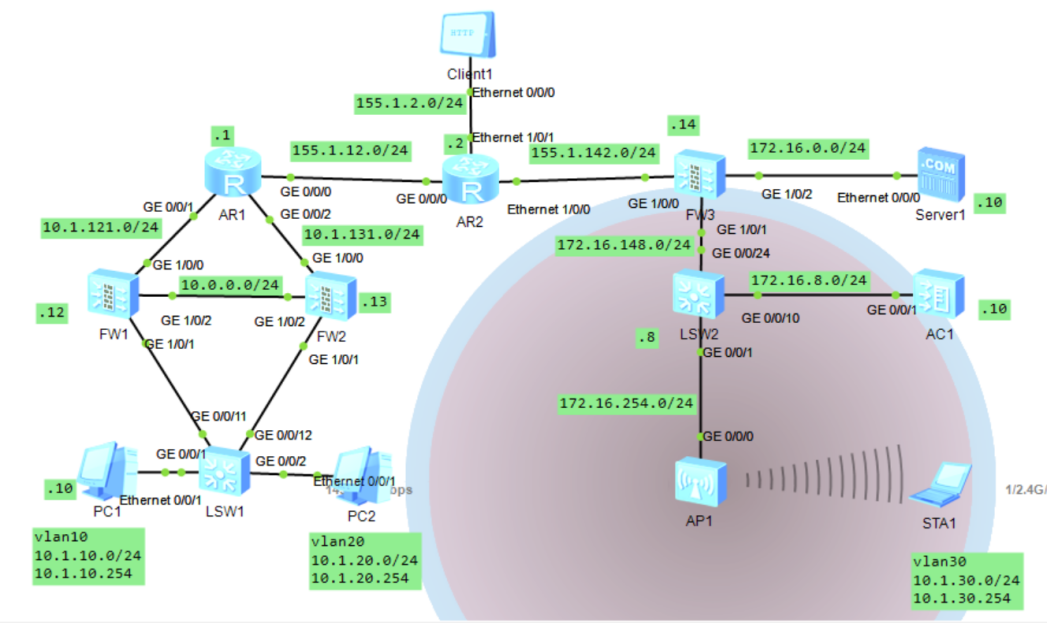
四、外网client可以公网地址155.1.142.10访问分支服务器的www和ftp服务。
R2:
ip route-static 155.1.142.10 32 Virtual-Template 1 //配置访问nat公网地址的路由,从虚口出
FW3:
nat server 0 protocol tcp global 155.1.142.10 www inside 172.16.0.10 www no-rev
erse unr-route
nat server 1 protocol tcp global 155.1.142.10 ftp inside 172.16.0.10 ftp no-rev
erse unr-route
rule name out_dmz
source-zone untrust
destination-zone dmz
destination-address 172.16.0.10 mask 255.255.255.255
service protocol tcp destination-port 21
service protocol tcp destination-port 80
action permit
[FW3]undo firewall detect ftp //关闭ASPF检测,以另一种方式配置如下:
[FW3]firewall interzone dmz untrust
[FW3-interzone-dmz-untrust]detect ftp
测试:
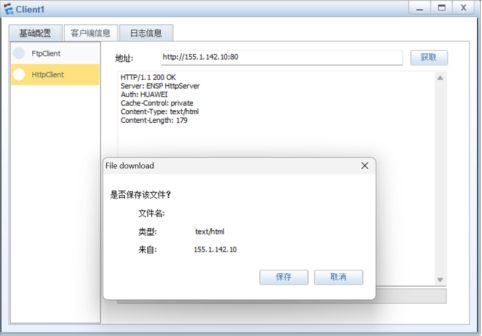
五、分支的内部用户可以通过公网访问服务的服务。
FW3:
nat-policy
rule name d_nat //做目的NAT
source-zone trust
source-address 172.16.30.0 mask 255.255.255.0
destination-address 155.1.142.10 mask 255.255.255.255
action destination-nat address 172.16.0.10
security-policy
rule name in_dmz
source-zone trust
destination-zone dmz
source-address 172.16.30.0 mask 255.255.255.0
destination-address 172.16.0.10 mask 255.255.255.255
action permit
测试:
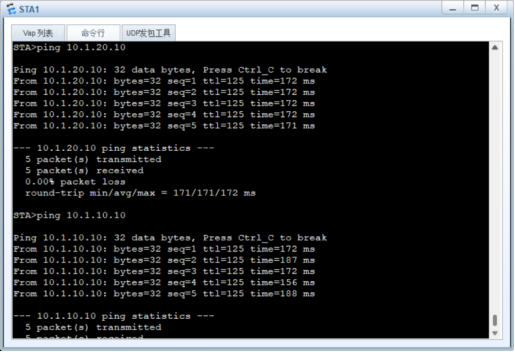
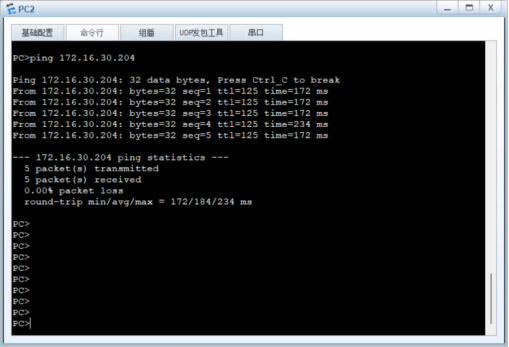
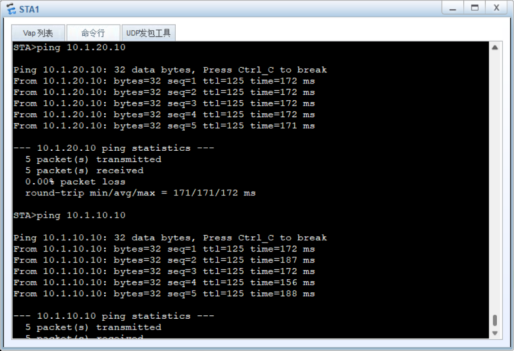
六、总部vlan 10和vlan20的用户都通过防火墙的ipsec vpn来访问分支vlan 30的用户
1、在fw3配置ipsec vpn
FW3:
ike proposal 10
encryption-algorithm 3des
dh group2
authentication-algorithm sha1
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer fw-1 //与vlan 10用户
pre-shared-key Huawei@123 ike-proposal 10
ike-proposal 10
remote-address 155.1.12.12
ike peer fw-2 //与vlan 20用户
pre-shared-key Huawei@123 ike-proposal 10
ike-proposal 10
remote-address 155.1.12.13
acl number 3001
rule 5 permit ip source 172.16.0.0 0.0.255.255 destination 10.1.10.0 0.0.0.255
acl number 3002
rule 5 permit ip source 172.16.0.0 0.0.255.255 destination 10.1.20.0 0.0.0.255
ipsec proposal lan_set
esp authentication-algorithm sha1
esp encryption-algorithm 3des
ipsec policy lan_map1 10 isakmp
security acl 3001
ike-peer fw-1
proposal lan_set
sa trigger-mode auto //(隧道自动触发协商,缺省情况下,IPSec隧道建立的触发方式为流量触发)
route inject dynamic
ipsec policy lan_map2 10 isakmp
security acl 3002
ike-peer fw-2
proposal lan_set
sa trigger-mode auto //(隧道自动触发协商,缺省情况下,IPSec隧道建立的触发方式为流量触发)
route inject dynamic
interface Tunnel1 //建立两条隧道与总部两台防火墙建立ipsec
ip address unnumbered interface Dialer1
tunnel-protocol ipsec
ipsec policy lan_map1
interface Tunnel2
ip address unnumbered interface Dialer1
tunnel-protocol ipsec
ipsec policy lan_map2
[FW3-zone-dmz]add interface Tunnel 1
[FW3-zone-dmz]add interface Tunnel 2
security-policy
rule name out_local //开放esp与ipsec的策略
source-zone untrust
destination-zone local
service protocol udp destination-port 4500 // 是UDP-encapsulated ESP and IKE端口号
service protocol udp destination-port 500 // 是ISAKMP端口
action permit
rule name dmz_in
source-zone dmz
destination-zone trust
source-address 10.1.0.0 mask 255.255.0.0
destination-address 172.16.0.0 mask 255.255.0.0
action permit
#
2、在总部防火墙上配置ipsec
HRP_M[FW-1-ike-proposal-10]d th
ike proposal 10
encryption-algorithm 3des
dh group2
authentication-algorithm sha1
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ipsec proposal lan_set
esp authentication-algorithm sha1
esp encryption-algorithm 3des
acl number 300
rule 5 permit ip source 10.1.0.0 0.0.255.255 destination 172.16.0.0 0.0.255.255
ike peer all //由于穿越NAT,不能配置remote address
pre-shared-key Huawei@123
ike-proposal 10
ipsec policy-template dy_map 10 //配置模板
security acl 3000
ike-peer all
proposal lan_set
HRP_M[FW-1]ipsec policy lan_map 10 isakmp template dy_map (+B
HRP_M[FW-1-GigabitEthernet1/0/0]ipsec policy lan_map alone
HRP_S[FW-2-GigabitEthernet1/0/0]ipsec policy lan_map alone
security-policy
rule name out_local
source-zone untrust
destination-zone local
service protocol udp destination-port 4500
service protocol udp destination-port 500
action permit
rule name out_in
source-zone untrust
destination-zone trust
source-address 172.16.0.0 mask 255.255.0.0
destination-address 10.1.0.0 mask 255.255.0.0
action permit
R1:
interface GigabitEthernet0/0/0
ip address 155.1.12.1 255.255.255.0
nat server protocol udp global 155.1.12.12 500 inside 10.1.121.12 500
nat server protocol udp global 155.1.12.12 4500 inside 10.1.121.12 4500
nat server protocol udp global 155.1.12.13 500 inside 10.1.131.13 500
nat server protocol udp global 155.1.12.13 4500 inside 10.1.131.13 4500
验证ipsec vpn隧道建立情况:
[FW3]dis ike sa
2023-09-07 12:33:27.800
IKE SA information :
Conn-ID Peer VPN Flag(
s) Phase RemoteType RemoteID
--------------------------------------------------------------------------------
----------------------------------------------------
33 155.1.12.13:4500 RD|ST
|A v2:2 IP 10.1.131.13
32 155.1.12.13:4500 RD|ST
|A v2:1 IP 10.1.131.13
9 155.1.12.12:4500 RD|ST
|A v2:2 IP 10.1.121.12
7 155.1.12.12:4500 RD|ST
|A v2:1 IP 10.1.121.12
Number of IKE SA : 4
--------------------------------------------------------------------------------
----------------------------------------------------
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
验证访问:
排错:
1、
FW3上:
nat-policy
rule name no_nat
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.0.0
destination-address 10.1.0.0 mask 255.255.0.0
action no-nat
#
return
[FW3-policy-nat]undo rule name no_nat //删除不需要做转换的nat,总部与分支之间走ipsec隧道
security-policy
rule name in_dmz
source-zone trust
destination-zone dmz
source-address 172.16.30.0 mask 255.255.255.0
destination-address 10.1.10.0 mask 255.255.255.0 //添加
destination-address 10.1.20.0 mask 255.255.255.0 //添加
destination-address 172.16.0.10 mask 255.255.255.255
action permit
[FW3]dis ip rou pro unr //下面10.1.0.0/16的路由跟route inject dynamic相关
2023-09-07 13:08:03.840
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : Unr
Destinations : 4 Routes : 4
Unr routing table status : <Active>
Destinations : 4 Routes : 4
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.1.10.0/24 Unr 70 0 D 155.1.12.12 Tunnel1
10.1.20.0/24 Unr 70 0 D 155.1.12.13 Tunnel2
155.1.142.2/32 Unr 61 0 D 155.1.142.2 Dialer1
155.1.142.10/32 Unr 61 0 D 127.0.0.1 InLoopBack0
Unr routing table status : <Inactive>
Destinations : 0 Routes : 0
3、验证
七、安全可靠性
总部:ospf邻居之间使用区域md5认证
[R1-ospf-1-area-0.0.0.0]authentication-mode md5 1 plain Huawei@123
HRP_M[FW-1-ospf-1-area-0.0.0.0]authentication-mode md5 1 plain Huawei@123
HRP_S[FW-2-ospf-1-area-0.0.0.0]authentication-mode md5 1 plain Huawei@123
分支:
修改网管端口
[FW3]undo web-manager security enable
[FW3]web-manager security enable port 10443
创建web管理员账户:
[FW3-aaa-manager-user-huawei]d th
2023-09-07 13:21:48.370
#
manager-user huawei
password cipher Huawei@123
service-type web
[FW3-aaa]bind manager-user huawei role system-admin //为账户绑定管理员角色
[FW3-Dialer1]service-manage https permit //在接口使能web功能
反病毒:
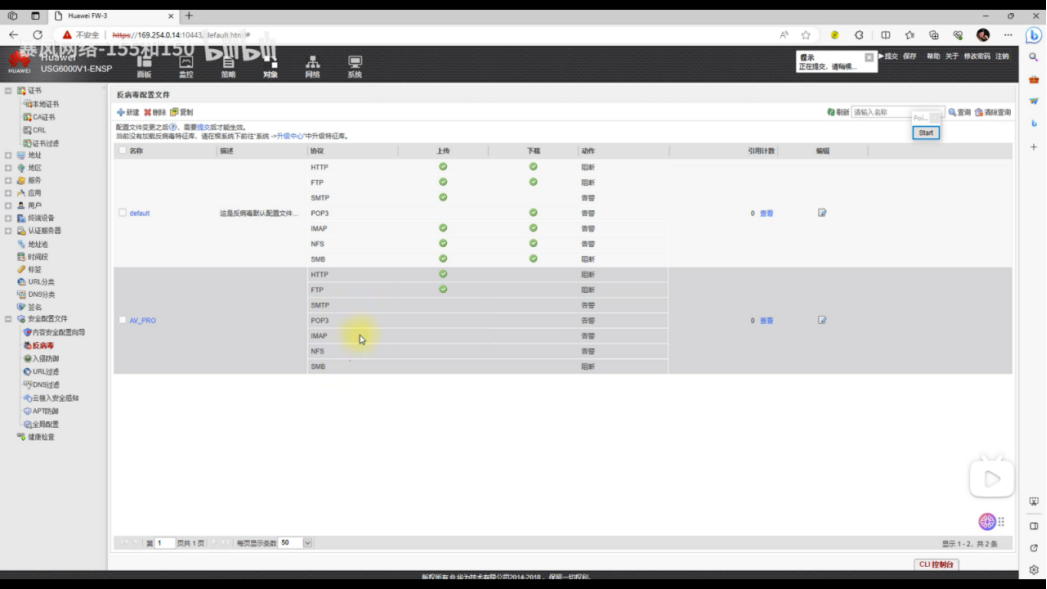
放行策略



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· 使用C#创建一个MCP客户端
· ollama系列1:轻松3步本地部署deepseek,普通电脑可用
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 按钮权限的设计及实现