安装 Elasticsearch
安装 Elasticsearch
#中间件ElasticSearch#
一、Docker容器
-
创建所需目录和文件
配置:
./config-
elasticsearch.yml
cluster.name: "docker-cluster" http.host: 0.0.0.0 ----------------------- BEGIN SECURITY AUTO CONFIGURATION ----------------------- The following settings, TLS certificates, and keys have been automatically generated to configure Elasticsearch security features on 10-10-2023 02:45:44 直接docker创建时,xpack是开的,需要用命令行设置密码后才能访问,在下面我们直接关掉 https://www.elastic.co/guide/en/x-pack/current/security-getting-started.html -------------------------------------------------------------------------------- Enable security features xpack.security.enabled: false xpack.security.enrollment.enabled: false Enable encryption for HTTP API client connections, such as Kibana, Logstash, and Agents xpack.security.http.ssl: enabled: false keystore.path: certs/http.p12 Enable encryption and mutual authentication between cluster nodes xpack.security.transport.ssl: enabled: false verification_mode: certificate keystore.path: certs/transport.p12 truststore.path: certs/transport.p12 ----------------------- END SECURITY AUTO CONFIGURATION ------------------------- -
jvm.options
################################################################ ## ## JVM configuration ## ################################################################ ## ## WARNING: DO NOT EDIT THIS FILE. If you want to override the ## JVM options in this file, or set any additional options, you ## should create one or more files in the jvm.options.d ## directory containing your adjustments. ## ## See https://www.elastic.co/guide/en/elasticsearch/reference/8.10/jvm-options.html ## for more information. ## ################################################################ ################################################################ IMPORTANT: JVM heap size ################################################################ The heap size is automatically configured by Elasticsearch based on the available memory in your system and the roles each node is configured to fulfill. If specifying heap is required, it should be done through a file in jvm.options.d, which should be named with .options suffix, and the min and max should be set to the same value. For example, to set the heap to 4 GB, create a new file in the jvm.options.d directory containing these lines: -Xms4g -Xmx4g See https://www.elastic.co/guide/en/elasticsearch/reference/8.10/heap-size.html for more information ################################################################ ################################################################ Expert settings ################################################################ All settings below here are considered expert settings. Do not adjust them unless you understand what you are doing. Do not edit them in this file; instead, create a new file in the jvm.options.d directory containing your adjustments. ################################################################ -XX:+UseG1GC JVM temporary directory -Djava.io.tmpdir=${ES_TMPDIR} Leverages accelerated vector hardware instructions; removing this may result in less optimal vector performance 20:--add-modules=jdk.incubator.vector heap dumps generate a heap dump when an allocation from the Java heap fails; heap dumps are created in the working directory of the JVM unless an alternative path is specified -XX:+HeapDumpOnOutOfMemoryError exit right after heap dump on out of memory error -XX:+ExitOnOutOfMemoryError specify an alternative path for heap dumps; ensure the directory exists and has sufficient space -XX:HeapDumpPath=data specify an alternative path for JVM fatal error logs -XX:ErrorFile=logs/hs_err_pid%p.log GC logging -Xlog:gc*,gc+age=trace,safepoint:file=logs/gc.log:utctime,level,pid,tags:filecount=32,filesize=64m -
log4j2.properties
status = error ######## Server JSON ############################ appender.rolling.type = Console appender.rolling.name = rolling appender.rolling.layout.type = ECSJsonLayout appender.rolling.layout.dataset = elasticsearch.server ################################################ ################################################ rootLogger.level = info rootLogger.appenderRef.rolling.ref = rolling ######## Deprecation JSON ####################### appender.deprecation_rolling.type = Console appender.deprecation_rolling.name = deprecation_rolling appender.deprecation_rolling.layout.type = ECSJsonLayout Intentionally follows a different pattern to above appender.deprecation_rolling.layout.dataset = deprecation.elasticsearch appender.deprecation_rolling.filter.rate_limit.type = RateLimitingFilter appender.header_warning.type = HeaderWarningAppender appender.header_warning.name = header_warning ################################################# logger.deprecation.name = org.elasticsearch.deprecation logger.deprecation.level = WARN logger.deprecation.appenderRef.deprecation_rolling.ref = deprecation_rolling logger.deprecation.appenderRef.header_warning.ref = header_warning logger.deprecation.additivity = false ######## Search slowlog JSON #################### appender.index_search_slowlog_rolling.type = Console appender.index_search_slowlog_rolling.name = index_search_slowlog_rolling appender.index_search_slowlog_rolling.layout.type = ECSJsonLayout appender.index_search_slowlog_rolling.layout.dataset = elasticsearch.index_search_slowlog ################################################# ################################################# logger.index_search_slowlog_rolling.name = index.search.slowlog logger.index_search_slowlog_rolling.level = trace logger.index_search_slowlog_rolling.appenderRef.index_search_slowlog_rolling.ref = index_search_slowlog_rolling logger.index_search_slowlog_rolling.additivity = false ######## Indexing slowlog JSON ################## appender.index_indexing_slowlog_rolling.type = Console appender.index_indexing_slowlog_rolling.name = index_indexing_slowlog_rolling appender.index_indexing_slowlog_rolling.layout.type = ECSJsonLayout appender.index_indexing_slowlog_rolling.layout.dataset = elasticsearch.index_indexing_slowlog ################################################# logger.index_indexing_slowlog.name = index.indexing.slowlog.index logger.index_indexing_slowlog.level = trace logger.index_indexing_slowlog.appenderRef.index_indexing_slowlog_rolling.ref = index_indexing_slowlog_rolling logger.index_indexing_slowlog.additivity = false logger.org_apache_pdfbox.name = org.apache.pdfbox logger.org_apache_pdfbox.level = off logger.org_apache_poi.name = org.apache.poi logger.org_apache_poi.level = off logger.org_apache_fontbox.name = org.apache.fontbox logger.org_apache_fontbox.level = off logger.org_apache_xmlbeans.name = org.apache.xmlbeans logger.org_apache_xmlbeans.level = off logger.com_amazonaws.name = com.amazonaws logger.com_amazonaws.level = warn logger.com_amazonaws_jmx_SdkMBeanRegistrySupport.name = com.amazonaws.jmx.SdkMBeanRegistrySupport logger.com_amazonaws_jmx_SdkMBeanRegistrySupport.level = error logger.com_amazonaws_metrics_AwsSdkMetrics.name = com.amazonaws.metrics.AwsSdkMetrics logger.com_amazonaws_metrics_AwsSdkMetrics.level = error logger.com_amazonaws_auth_profile_internal_BasicProfileConfigFileLoader.name = com.amazonaws.auth.profile.internal.BasicProfileConfigFileLoader logger.com_amazonaws_auth_profile_internal_BasicProfileConfigFileLoader.level = error logger.com_amazonaws_services_s3_internal_UseArnRegionResolver.name = com.amazonaws.services.s3.internal.UseArnRegionResolver logger.com_amazonaws_services_s3_internal_UseArnRegionResolver.level = error appender.audit_rolling.type = Console appender.audit_rolling.name = audit_rolling appender.audit_rolling.layout.type = PatternLayout appender.audit_rolling.layout.pattern = { "type":"audit", "timestamp":"%d{yyyy-MM-dd'T'HH:mm:ss,SSSZ}" %varsNotEmpty{, "cluster.name":"%enc{%map{cluster.name}}{JSON}"} %varsNotEmpty{, "cluster.uuid":"%enc{%map{cluster.uuid}}{JSON}"} %varsNotEmpty{, "node.name":"%enc{%map{node.name}}{JSON}"} %varsNotEmpty{, "node.id":"%enc{%map{node.id}}{JSON}"} %varsNotEmpty{, "host.name":"%enc{%map{host.name}}{JSON}"} %varsNotEmpty{, "host.ip":"%enc{%map{host.ip}}{JSON}"} %varsNotEmpty{, "event.type":"%enc{%map{event.type}}{JSON}"} %varsNotEmpty{, "event.action":"%enc{%map{event.action}}{JSON}"} %varsNotEmpty{, "authentication.type":"%enc{%map{authentication.type}}{JSON}"} %varsNotEmpty{, "user.name":"%enc{%map{user.name}}{JSON}"} %varsNotEmpty{, "user.run_by.name":"%enc{%map{user.run_by.name}}{JSON}"} %varsNotEmpty{, "user.run_as.name":"%enc{%map{user.run_as.name}}{JSON}"} %varsNotEmpty{, "user.realm":"%enc{%map{user.realm}}{JSON}"} %varsNotEmpty{, "user.realm_domain":"%enc{%map{user.realm_domain}}{JSON}"} %varsNotEmpty{, "user.run_by.realm":"%enc{%map{user.run_by.realm}}{JSON}"} %varsNotEmpty{, "user.run_by.realm_domain":"%enc{%map{user.run_by.realm_domain}}{JSON}"} %varsNotEmpty{, "user.run_as.realm":"%enc{%map{user.run_as.realm}}{JSON}"} %varsNotEmpty{, "user.run_as.realm_domain":"%enc{%map{user.run_as.realm_domain}}{JSON}"} %varsNotEmpty{, "user.roles":%map{user.roles}} %varsNotEmpty{, "apikey.id":"%enc{%map{apikey.id}}{JSON}"} %varsNotEmpty{, "apikey.name":"%enc{%map{apikey.name}}{JSON}"} %varsNotEmpty{, "authentication.token.name":"%enc{%map{authentication.token.name}}{JSON}"} %varsNotEmpty{, "authentication.token.type":"%enc{%map{authentication.token.type}}{JSON}"} %varsNotEmpty{, "cross_cluster_access":%map{cross_cluster_access}} %varsNotEmpty{, "origin.type":"%enc{%map{origin.type}}{JSON}"} %varsNotEmpty{, "origin.address":"%enc{%map{origin.address}}{JSON}"} %varsNotEmpty{, "realm":"%enc{%map{realm}}{JSON}"} %varsNotEmpty{, "realm_domain":"%enc{%map{realm_domain}}{JSON}"} %varsNotEmpty{, "url.path":"%enc{%map{url.path}}{JSON}"} %varsNotEmpty{, "url.query":"%enc{%map{url.query}}{JSON}"} %varsNotEmpty{, "request.method":"%enc{%map{request.method}}{JSON}"} %varsNotEmpty{, "request.body":"%enc{%map{request.body}}{JSON}"} %varsNotEmpty{, "request.id":"%enc{%map{request.id}}{JSON}"} %varsNotEmpty{, "action":"%enc{%map{action}}{JSON}"} %varsNotEmpty{, "request.name":"%enc{%map{request.name}}{JSON}"} %varsNotEmpty{, "indices":%map{indices}} %varsNotEmpty{, "opaque_id":"%enc{%map{opaque_id}}{JSON}"} %varsNotEmpty{, "trace.id":"%enc{%map{trace.id}}{JSON}"} %varsNotEmpty{, "x_forwarded_for":"%enc{%map{x_forwarded_for}}{JSON}"} %varsNotEmpty{, "transport.profile":"%enc{%map{transport.profile}}{JSON}"} %varsNotEmpty{, "rule":"%enc{%map{rule}}{JSON}"} %varsNotEmpty{, "put":%map{put}} %varsNotEmpty{, "delete":%map{delete}} %varsNotEmpty{, "change":%map{change}} %varsNotEmpty{, "create":%map{create}} %varsNotEmpty{, "invalidate":%map{invalidate}} }%n "node.name" node name from the elasticsearch.yml settings "node.id" node id which should not change between cluster restarts "host.name" unresolved hostname of the local node "host.ip" the local bound ip (i.e. the ip listening for connections) "origin.type" a received REST request is translated into one or more transport requests. This indicates which processing layer generated the event "rest" or "transport" (internal) "event.action" the name of the audited event, eg. "authentication_failed", "access_granted", "run_as_granted", etc. "authentication.type" one of "realm", "api_key", "token", "anonymous" or "internal" "user.name" the subject name as authenticated by a realm "user.run_by.name" the original authenticated subject name that is impersonating another one. "user.run_as.name" if this "event.action" is of a run_as type, this is the subject name to be impersonated as. "user.realm" the name of the realm that authenticated "user.name" "user.realm_domain" if "user.realm" is under a domain, this is the name of the domain "user.run_by.realm" the realm name of the impersonating subject ("user.run_by.name") "user.run_by.realm_domain" if "user.run_by.realm" is under a domain, this is the name of the domain "user.run_as.realm" if this "event.action" is of a run_as type, this is the realm name the impersonated user is looked up from "user.run_as.realm_domain" if "user.run_as.realm" is under a domain, this is the name of the domain "user.roles" the roles array of the user; these are the roles that are granting privileges "apikey.id" this field is present if and only if the "authentication.type" is "api_key" "apikey.name" this field is present if and only if the "authentication.type" is "api_key" "authentication.token.name" this field is present if and only if the authenticating credential is a service account token "authentication.token.type" this field is present if and only if the authenticating credential is a service account token "cross_cluster_access" this field is present if and only if the associated authentication occurred cross cluster "event.type" informs about what internal system generated the event; possible values are "rest", "transport", "ip_filter" and "security_config_change" "origin.address" the remote address and port of the first network hop, i.e. a REST proxy or another cluster node "realm" name of a realm that has generated an "authentication_failed" or an "authentication_successful"; the subject is not yet authenticated "realm_domain" if "realm" is under a domain, this is the name of the domain "url.path" the URI component between the port and the query string; it is percent (URL) encoded "url.query" the URI component after the path and before the fragment; it is percent (URL) encoded "request.method" the method of the HTTP request, i.e. one of GET, POST, PUT, DELETE, OPTIONS, HEAD, PATCH, TRACE, CONNECT "request.body" the content of the request body entity, JSON escaped "request.id" a synthetic identifier for the incoming request, this is unique per incoming request, and consistent across all audit events generated by that request "action" an action is the most granular operation that is authorized and this identifies it in a namespaced way (internal) "request.name" if the event is in connection to a transport message this is the name of the request class, similar to how rest requests are identified by the url path (internal) "indices" the array of indices that the "action" is acting upon "opaque_id" opaque value conveyed by the "X-Opaque-Id" request header "trace_id" an identifier conveyed by the part of "traceparent" request header "x_forwarded_for" the addresses from the "X-Forwarded-For" request header, as a verbatim string value (not an array) "transport.profile" name of the transport profile in case this is a "connection_granted" or "connection_denied" event "rule" name of the applied rule if the "origin.type" is "ip_filter" the "put", "delete", "change", "create", "invalidate" fields are only present when the "event.type" is "security_config_change" and contain the security config change (as an object) taking effect logger.xpack_security_audit_logfile.name = org.elasticsearch.xpack.security.audit.logfile.LoggingAuditTrail logger.xpack_security_audit_logfile.level = info logger.xpack_security_audit_logfile.appenderRef.audit_rolling.ref = audit_rolling logger.xpack_security_audit_logfile.additivity = false elasticsearch.yml logger.xmlsig.name = org.apache.xml.security.signature.XMLSignature logger.xmlsig.level = error logger.samlxml_decrypt.name = org.opensaml.xmlsec.encryption.support.Decrypter logger.samlxml_decrypt.level = fatal logger.saml2_decrypt.name = org.opensaml.saml.saml2.encryption.Decrypter logger.saml2_decrypt.level = fatal
数据:
./data插件:
./plugins日志:
./logs -
-
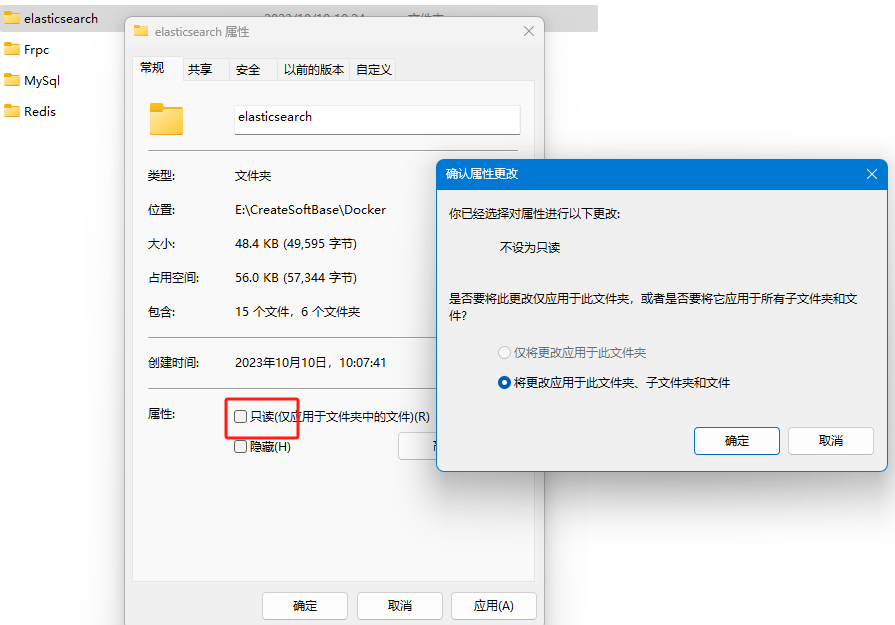
设置文件夹权限
linux:
chmod -R 777 config logs pluginswindows:
取消“只读”勾选
-
启动服务
docker run --name elasticsearch -p 9200:9200 -p 9300:9300 -e "discovery.type=single-node" -v E:\CreateSoftBase\Docker\elasticsearch\config:/usr/share/elasticsearch/config/ -v E:\CreateSoftBase\Docker\elasticsearch\data:/usr/share/elasticsearch/data -v E:\CreateSoftBase\Docker\elasticsearch\logs:/usr/share/elasticsearch/logs -v E:\CreateSoftBase\Docker\elasticsearch\plugins:/usr/share/elasticsearch/plugins -d elasticsearch:8.10.2 -
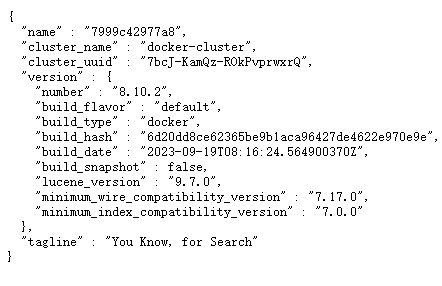
验证
访问http://localhost:9200/,出现以下结果代表成功



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构