Kubernetes集群(二)——nfs的存储类(storageclass)
1. 安装nfs-server
1.1. 新建虚拟机用于nfs服务开启
作为存储服务器,存储空间配置高一些。
安装nfs服务
yum install -y nfs-utils rpcbind创建共享目录
mkdir /root/test-pv配置nfs服务信息
vi /etc/exports添加如下内容
/root/test-pv *(rw,async,no_root_squash,no_subtree_check)
启动nfs和rpcbind服务,并设置开机自启动
service nfs start && service rpcbind start
systemctl enable nfs && systemctl enable rpcbindnfs配置生效
exportfs -a1.2. 关闭防火墙
关闭
systemctl stop firewalld取消开机自启动
systemctl disable firewalld2. 工作节点上安装nfs客户端
2.1. 安装
yum install -y nfs-utils rpcbind2.2. 启动nfs和rpcbind服务,并设置开机自启动
service nfs start && service rpcbind start
systemctl enable nfs && systemctl enable rpcbind3. Kubernetes集群安装基于nfs的storage-class
在主结点进行操作。
storage-class简称为sc。
3.1. 创建命名空间
用于存放自定义sc的内容。
kubectl create namespace custom-sc3.2. nfs的RBAC文件
准备工作目录:mkdir -p /root/custom-sc/nfs && cd /root/custom-sc/nfs && vim rbac.yaml
添加如下内容,注意namespace的名称要与创建的命名空间名称相同
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: nfs-provisioner-runner
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "create", "delete"]
- apiGroups: [""]
resources: ["persistentvolumeclaims"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["events"]
verbs: ["create", "update", "patch"]
- apiGroups: [""]
resources: ["services", "endpoints"]
verbs: ["get"]
- apiGroups: ["extensions"]
resources: ["podsecuritypolicies"]
resourceNames: ["nfs-provisioner"]
verbs: ["use"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: run-nfs-provisioner
subjects:
- kind: ServiceAccount
name: nfs-provisioner
# replace with namespace where provisioner is deployed
namespace: custom-sc
roleRef:
kind: ClusterRole
name: nfs-provisioner-runner
apiGroup: rbac.authorization.k8s.io
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: leader-locking-nfs-provisioner
rules:
- apiGroups: [""]
resources: ["endpoints"]
verbs: ["get", "list", "watch", "create", "update", "patch"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: leader-locking-nfs-provisioner
subjects:
- kind: ServiceAccount
name: nfs-provisioner
# replace with namespace where provisioner is deployed
namespace: custom-sc
roleRef:
kind: Role
name: leader-locking-nfs-provisioner
apiGroup: rbac.authorization.k8s.io应用rbac文件:kubectl apply -f rbac.yaml -n custom-sc
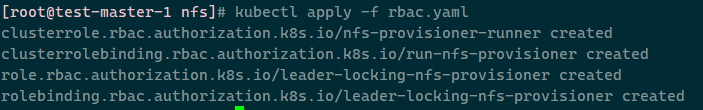
3.3. nfs的class文件
工作目录不变,保持 /root/custom-sc/nfs/
编辑class文件:vim class.yaml
kind: StorageClass
apiVersion: storage.k8s.io/v1
metadata:
name: nfs
provisioner: my/nfs
parameters:
archiveOnDelete: "true"
mountOptions:
- vers=4.1 应用class文件:kubectl apply -f class.yaml -n custom-sc

3.4. nfs的sa文件
工作目录不变,保持 /root/custom-sc/nfs/
编辑class文件:vim sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: nfs-provisioner
namespace: custom-sc应用class文件:kubectl apply -f sa.yaml -n custom-sc
3.5. nfs的deploymenbt文件
工作目录不变,保持 /root/custom-sc/nfs/
编辑class文件:vim deployment.yaml
apiVersion: apps/v1
kind: DaemonSet
metadata:
name: nfs
labels:
app: nfs
namespace: custom-sc
spec:
selector:
matchLabels:
app: nfs
template:
metadata:
labels:
app: nfs
spec:
serviceAccountName: nfs-provisioner
containers:
- name: nfs-client
image: registry.cn-shenzhen.aliyuncs.com/shuhui/nfs-subdir-external-provisioner:v4.0.2
volumeMounts:
- name: nfs-client-root
mountPath: /persistentvolumes
env:
- name: PROVISIONER_NAME
value: my/nfs
- name: NFS_SERVER
value: <nfs服务器IP>
- name: NFS_PATH
value: /root/test-pv
volumes:
- name: nfs-client-root
nfs:
server: <nfs服务器IP>
path: /root/test-pv应用class文件:kubectl apply -f deployment.yaml -n custom-sc
3.6. 设置为默认sc
查看sc:kubectl get sc
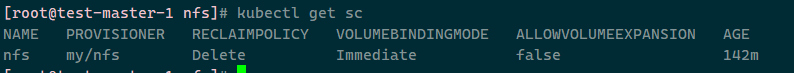
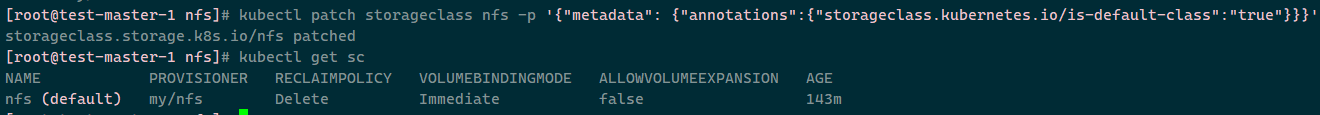
设置为默认:kubectl patch storageclass nfs -p '{"metadata": {"annotations":{"storageclass.kubernetes.io/is-default-class":"true"}}}'
3.7. 测试pvc与pv创建情况
编写测试文件:vim pvc-test.yaml
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: nfs-test
namespace: custom-sc
spec:
accessModes:
- ReadWriteMany
resources:
requests:
storage: 1Mi应用测试文件:kubectl apply -f pvc-test.yaml
查看pvc状态:kubectl get pvc -n custom-sc
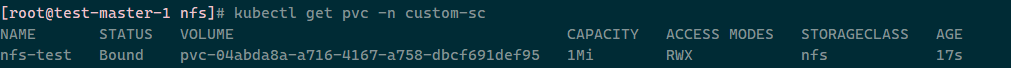
STATUS一栏为Bound说明nfs作为sc绑定数据卷成功!


