赣CTF-Misc方向wp
checkin
下载附件,一张图片,拖进010,在文件尾看到隐藏文本,提取并用社会主义价值解密
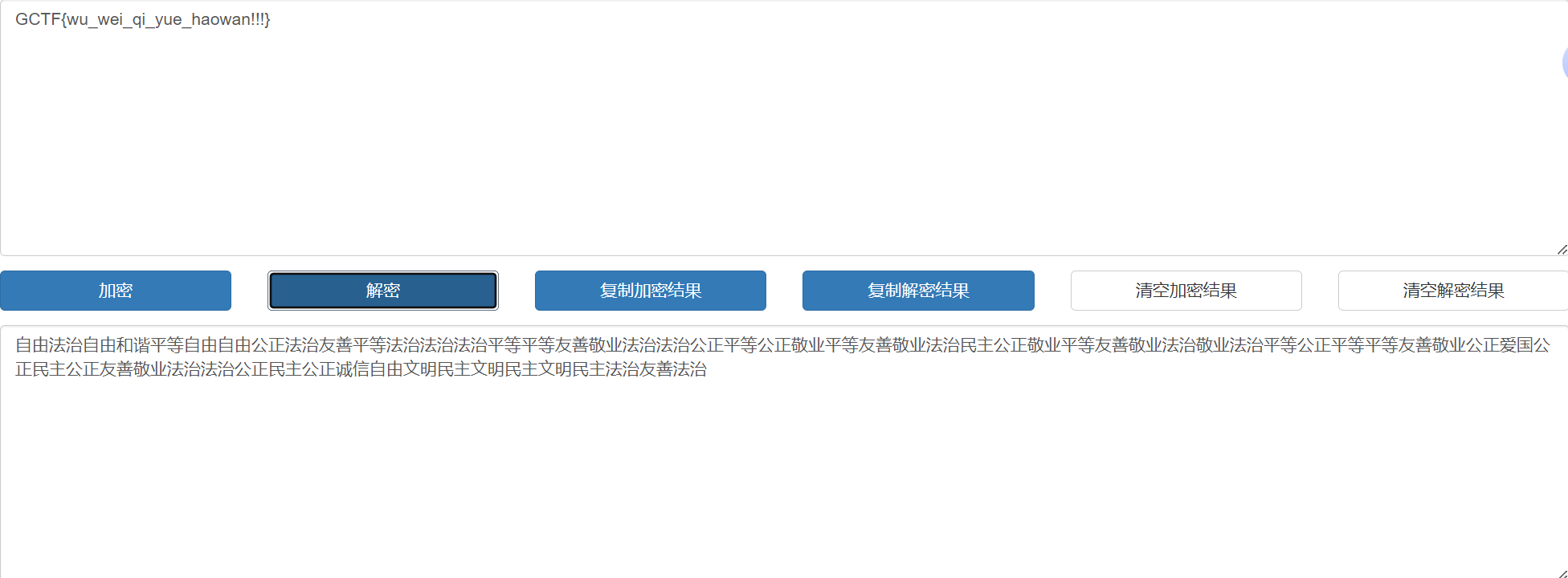
ez_forensics
提示为结合题目进行想象,我们会想到取证第一步vc挂载,但是需要密码,研究图片,lsb隐写,在row:G通道找到密钥
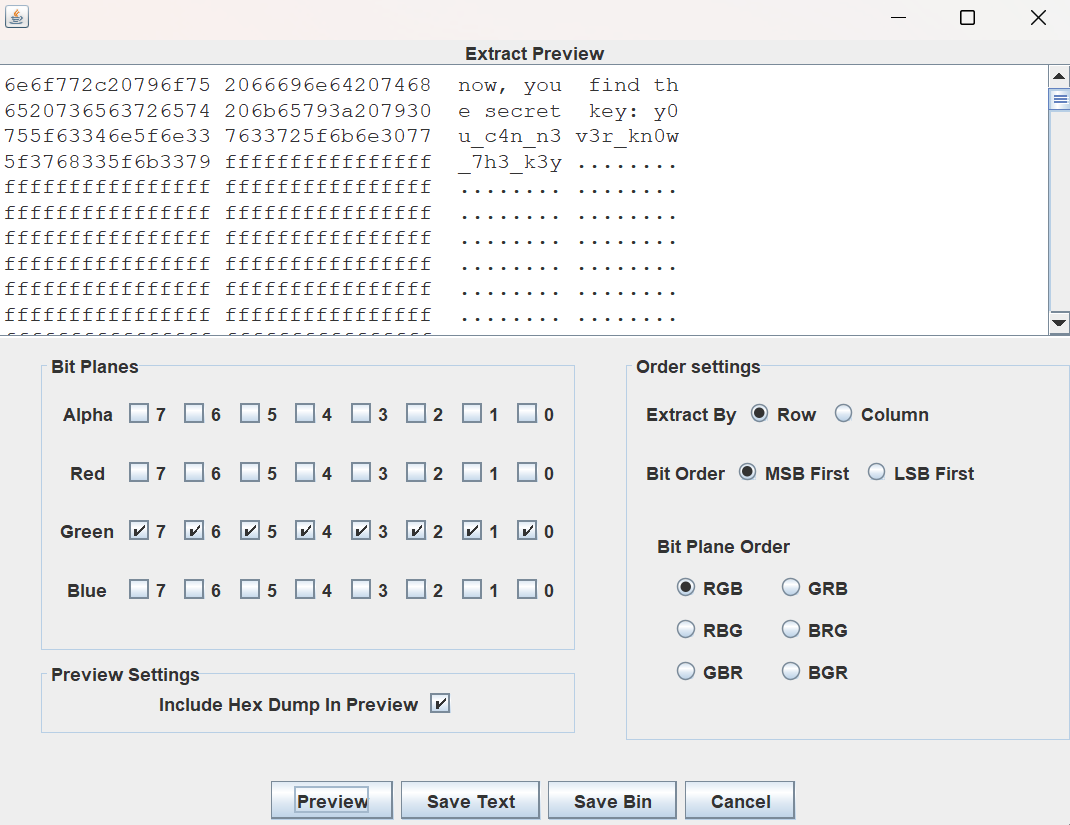
挂载,得到flag
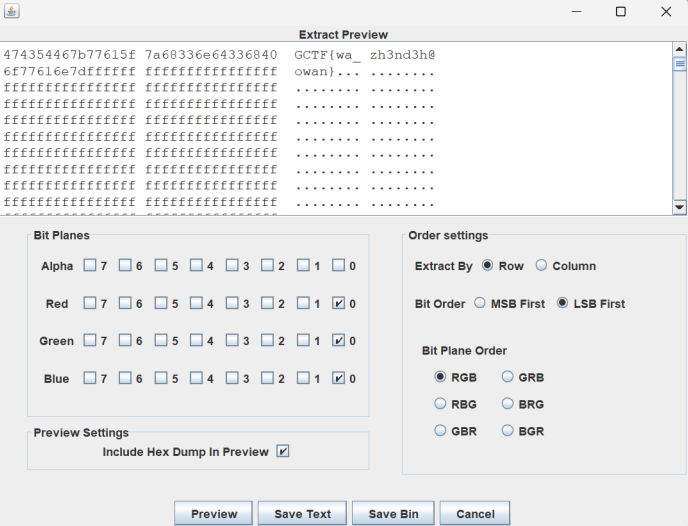
真的是base64哦
考点base64隐写
点击查看代码
import base64
path = input("请输入加密文件路径\n")
file = open(path)
a = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
aaa = ''
while True:
text = file.readline() # 只读取一行内容
# 判断是否读取到内容
text = text.replace("\n", "")
if not text:
break
if text.count('=') == 1:
aaa = aaa + \
str('{:02b}'.format((a.find(text[len(text)-2])) % 4))
if text.count('=') == 2:
aaa = aaa + \
str('{:04b}'.format((a.find(text[len(text)-3])) % 16))
file.close()
t = ""
ttt = len(aaa)
ttt = ttt//8*8
for i in range(0,ttt,8):
t = t + chr(int( aaa[i:i+8],2))
print(t)
GCTF{you_kn0w_base_sixsix_four}
嘿嘿,真的是无畏契约呢
base64转图片,得到一个二维码,(没想到是无畏契约官网吧)
lsb隐写
坚持不懈的压缩
password文本上赛博厨子,Megan35的base64表解密
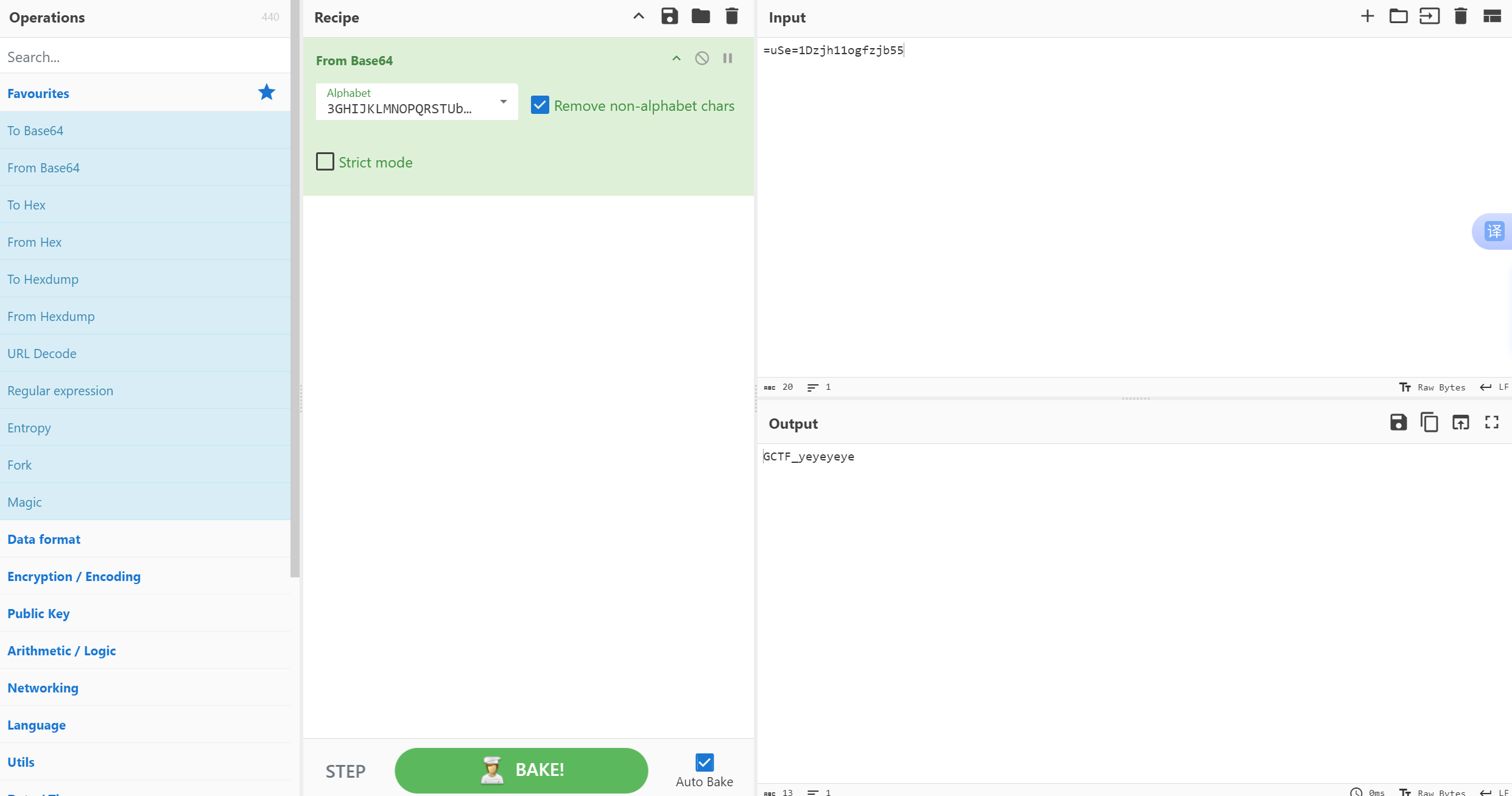
得到key,下面解决嵌套的压缩包,代码爆破
点击查看代码
import os
import zipfile
# 设置密码和初始压缩包名称
password = "GCTF_yeyeyeye"
initial_zip = r"final_zip.zip" # 最外层的压缩包
output_dir = "output" # 用于存储每层解压结果的临时文件夹
temp_file = "temp_extracted.zip" # 每次解压缩时的临时文件
# 创建输出目录
if not os.path.exists(output_dir):
os.makedirs(output_dir)
# 解压缩 1000 次
current_zip = initial_zip
for i in range(1000):
with zipfile.ZipFile(current_zip) as zf:
# 获取压缩包中的文件名
inner_file = zf.namelist()[0]
# 将文件解压到临时文件夹
zf.extract(inner_file, output_dir, pwd=bytes(password, 'utf-8'))
# 更新为下次需要解压的文件路径
current_zip = os.path.join(output_dir, inner_file)
# 重命名为临时文件以便处理下一层
if i < 999:
# 如果目标文件存在,先删除它
if os.path.exists(temp_file):
os.remove(temp_file)
os.rename(current_zip, temp_file)
current_zip = temp_file
print("解压缩完成!最终文件位于:", current_zip)
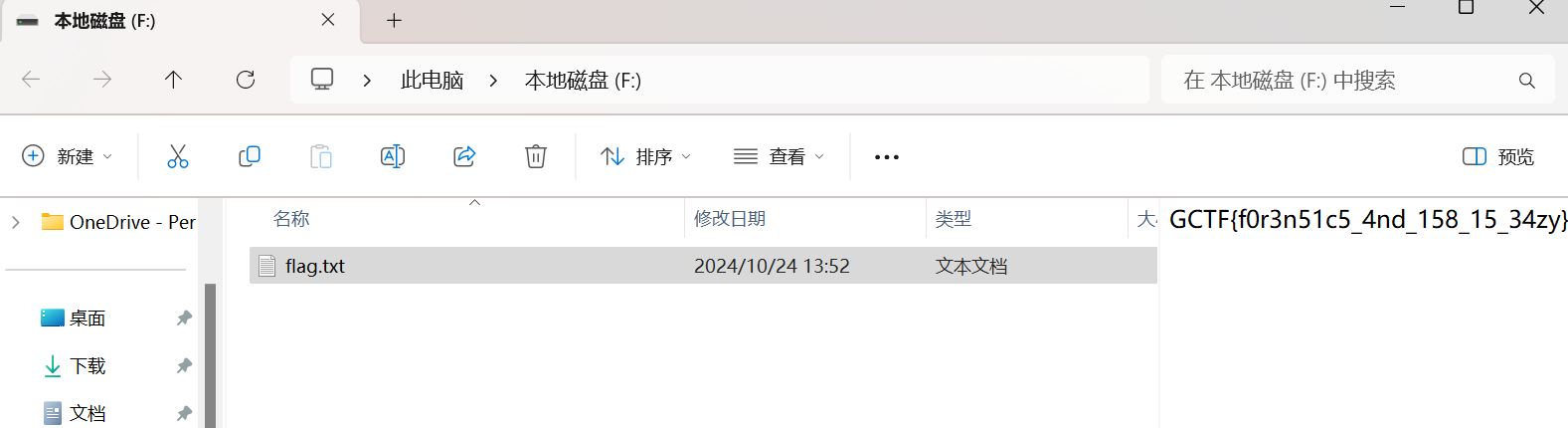
打开最后一层得到flag
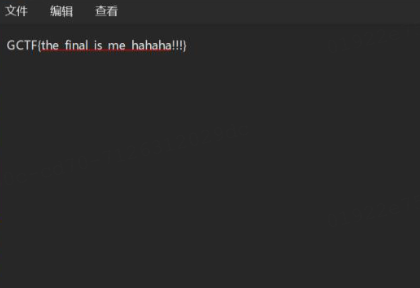
ez_word
word文档隐写,用系统自带word打开,设置显示隐藏文字,并改变字体颜色,可以得到2段flag
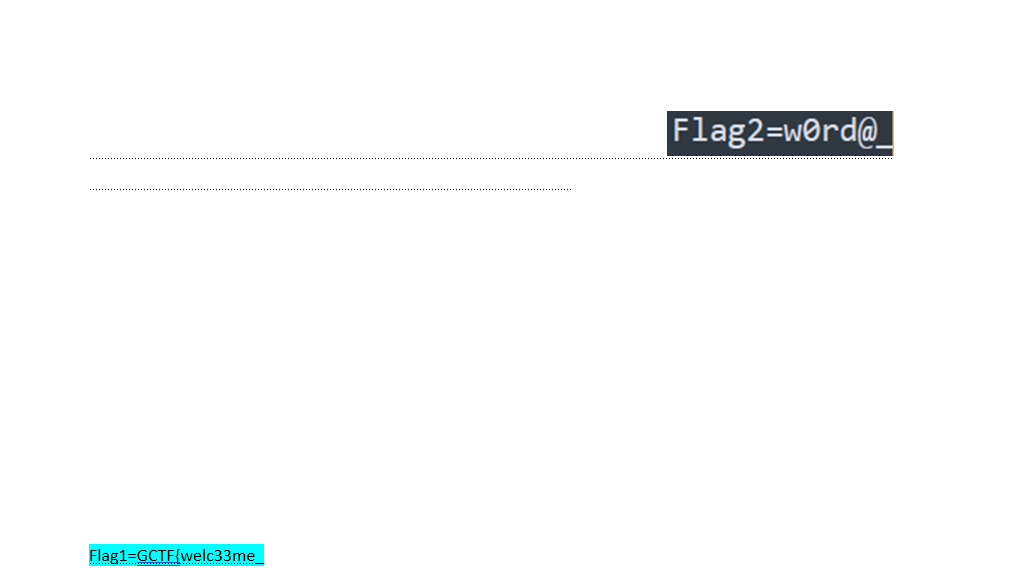
接着拖进010,发现内嵌压缩包,用foremost分离,出现加密文本base100(emoji解密)-Unicode-base64-base58得到最后一段:m1ssccc$$}
得到最后一段flag
最后拼接GCTF{welc33me_w0rd@_m1ssccc$$}
可惜雪飘进了双眼
题目即方法,空白文档隐写可以搜到snow隐写,但是没有密钥,里面有一个加密文件,拖进010,是个类png,16进制被交换过
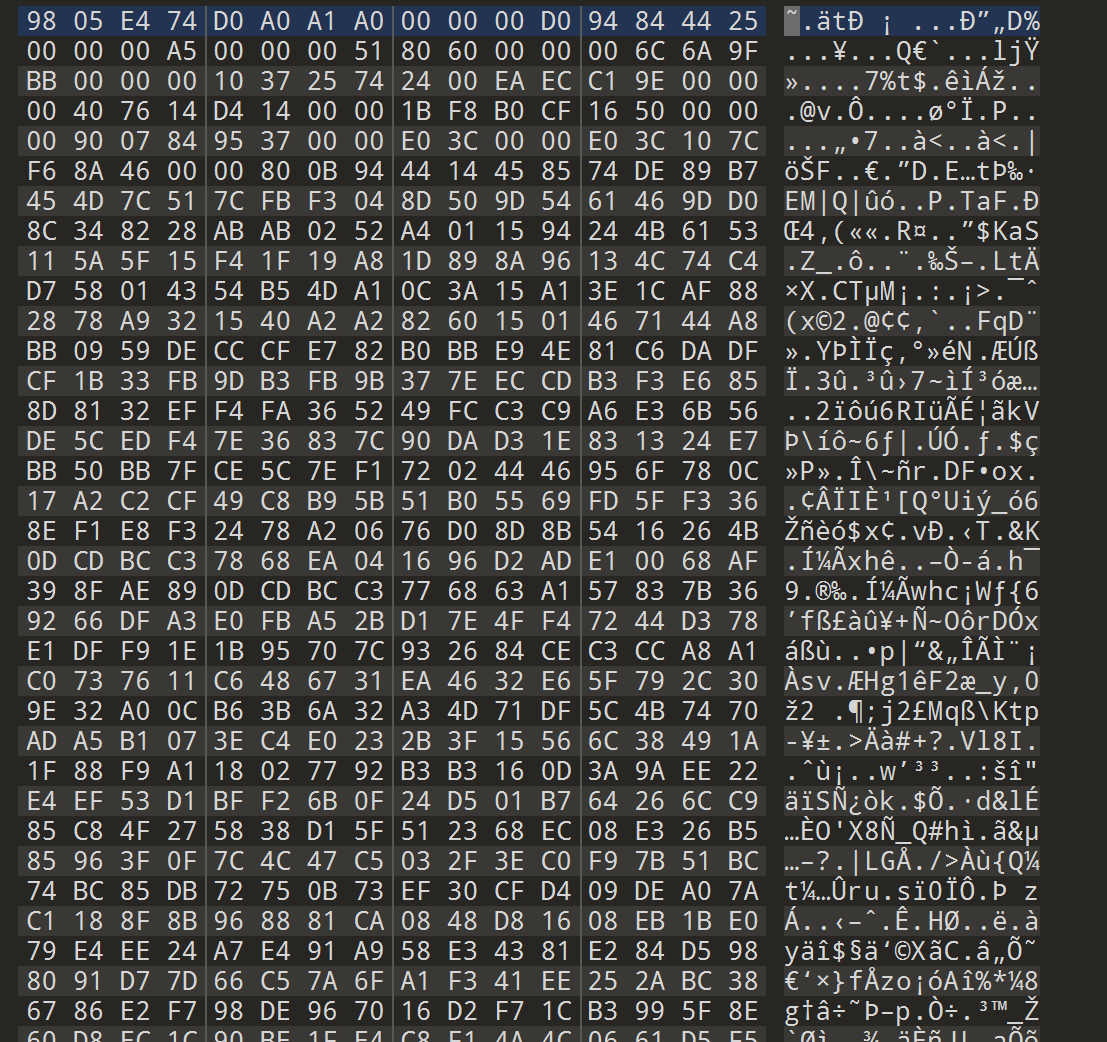
点击查看代码
def swap_pairs(s):
chars = list(s)
for i in range(0, len(chars) - 1, 2):
chars[i], chars[i + 1] = chars[i + 1], chars[i]
return ''.join(chars)
# 示例
input_string = ""
result = swap_pairs(input_string)
print(result)
https://blog.csdn.net/gitblog_09809/article/details/143005180
snow隐写解密,得到flag
爱玩原神?
拖进010,发现压缩包,手动分离,发现需要密码,根据提示water,我们想到盲水印解密
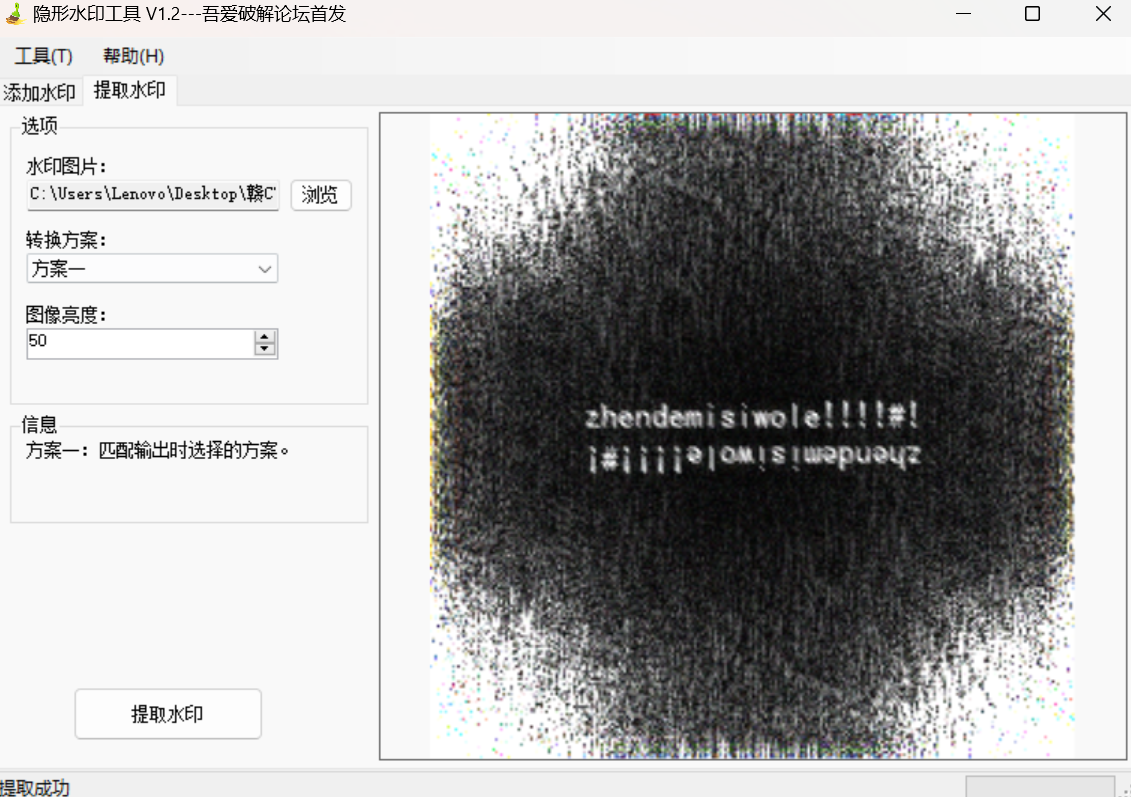
得到密钥,打开压缩包
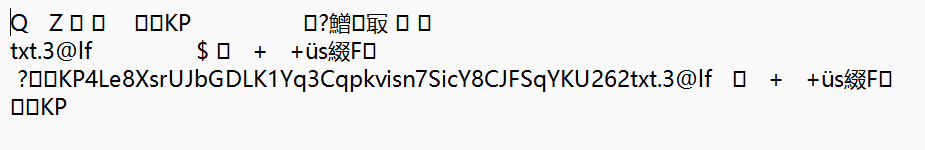
kp,是个倒过来的zip,倒转一下
点击查看代码
import re
str1 = ''
str1 = re.sub(r"(?<=\w)(?=(?:\w\w)+$)", " ", str1)
print(str1)
list1 = str1.split()
list1 = list(reversed(list1))
str1 = " ".join(list1)
print(str1)
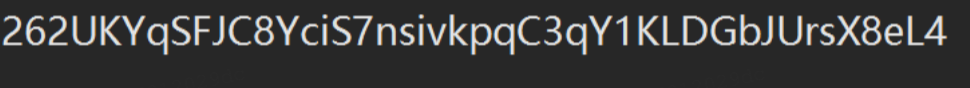
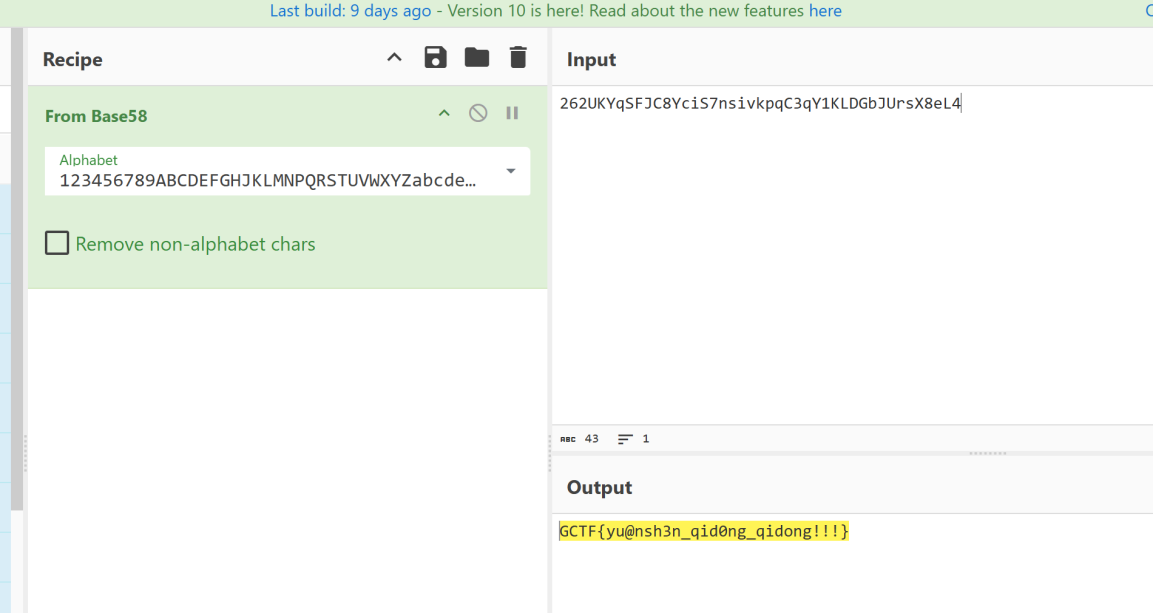
base58解密
ez_python?
一个无限循环,进行二分查找。在每次迭代中,检查当前范围的上下限之差是否为1。如果是,就获取 1[1]的值并打印然后终止循环
点击查看代码
import math
def battle(level):
HP = 4 * level + 100
ATK = max(3 * level - 90, 1)
M_ATK = max(3 ** 10 - level - 5, 1)
return True if math.ceil(3 ** 15 / ATK) < HP / M_ATK else False
geitaoshenketou = 3 ** 100 # 超大
l = [0, geitaoshenketou]
while True:
if l[1] - l[0] == 1:
res = l[1] # 直接使用l[1]的值
print('flag{' + str(res) + '}')
break
elif battle(sum(l) // 2):
l = [l[0], sum(l) // 2]
else:
l = [sum(l) // 2, l[1]]
点击查看代码
with open('http.txt','r') as f:
data = f.read()
re1 = r"from%20t\),(\d+),1\)\)=(\d+)--+"
pat = re.compile(re1)
a = data.split("\n")
b = {}
for i in a:
try:
rea = pat.search(i)
b[rea[1]] = rea[2]
except:
continue
flag = ""
for i in b:
flag+=chr(int(b[i]))
print(flag)
#flag{w1reshARK_ez_1sntit}
点击查看代码
p = 75622568597436029009683044560394575119431158827043458105864728211786000512791
a = 85026711271052943789730326470363572456786041535797705690318308421777954424637
b = 66098127120627409453551272472994257595002986659473620297996205313006369997437
k = 71968714696941641430925190199790590508283651626076908908651765926156451465871
e = elliptic curve defined by y^2 = x^3 + 9404142673616914780047281909968997337354882708754247584453580209991953911846*x + 66098127120627409453551272472994257595002986659473620297996205313006369997437 over finite field of size 75622568597436029009683044560394575119431158827043458105864728211786000512791
c1 = (66066117662242699468821517595725192879333073435277077882183775950349261792467 : 40228403532245213512933082571052263552637509365165217873276918743294218162507 : 1)
c2 = (55526569053402697811523099820610338430800152093428843463015712899070451620897 : 60523238843668948261533610341946158184574959321865109372495508584794806989724 : 1) cipher_left = 53849857630899617966127718792148796514724188262128669062866230792068679727635 cipher_right = 27732384893837974040803834222639325311271071577349345606901477238226516946069
看下snakeisme.js有一串很像base64的东西
把“-”全部替换成“+”
点击查看代码
input_file_path = 'input.txt'
output_file_path = 'output.txt'
with open(input_file_path, 'r', encoding='utf-8') as file:
content = file.read()
content = content.replace('-', '+')
with open(output_file_path, 'w', encoding='utf-8') as file:
file.write(content)
print("减号已成功替换为加号。")
拿去base64解密
再brainfuck解密
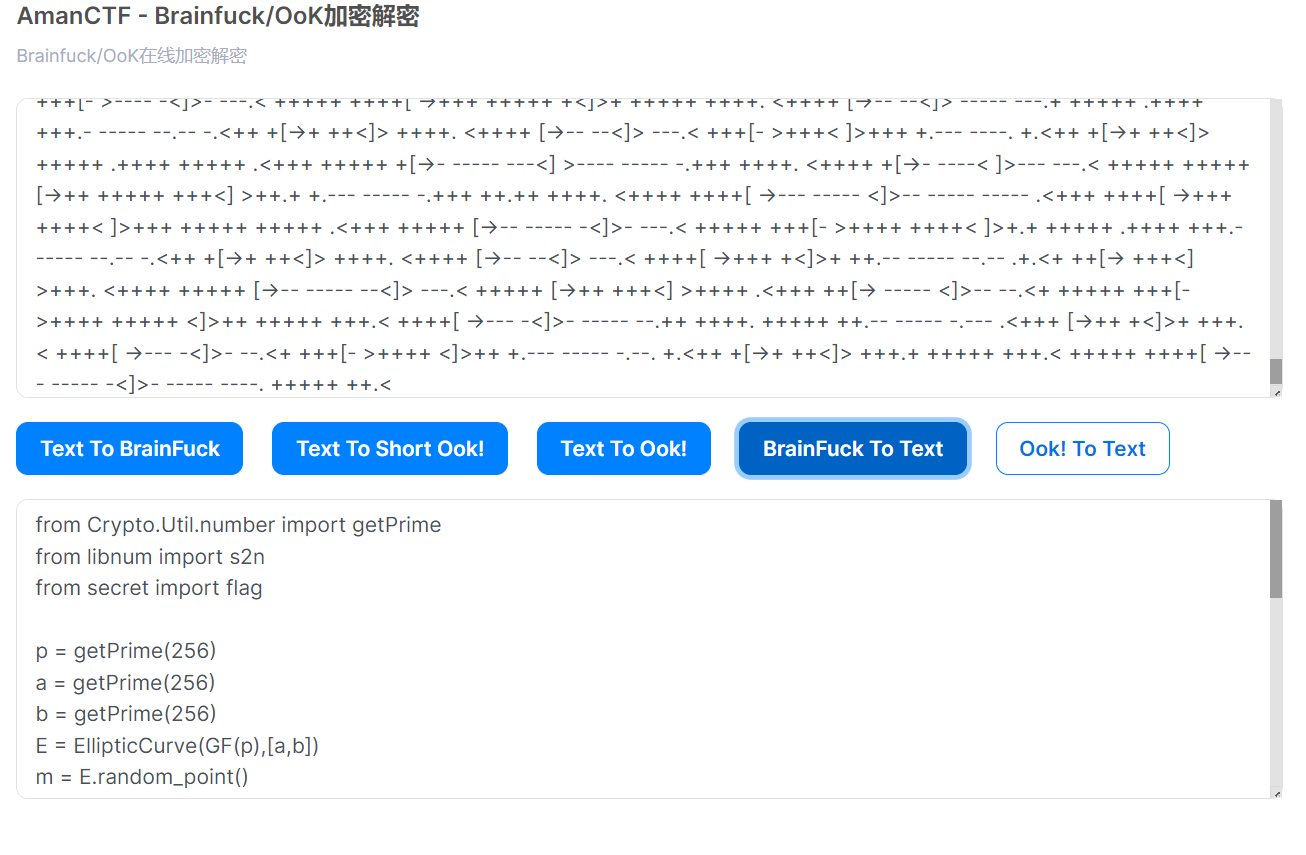
得到
点击查看代码
from Crypto.Util.number import getPrime
from libnum import s2n
from secret import flag
p = getPrime(256)
a = getPrime(256)
b = getPrime(256)
E = EllipticCurve(GF(p),[a,b])
m = E.random_point()
G = E.random_point()
k = getPrime(256)
K = k * G
r = getPrime(256)
c1 = m + r * K
c2 = r * G
cipher_left = s2n(flag[:len(flag)//2]) * m[0]
cipher_right = s2n(flag[len(flag)//2:]) * m[1]
print(f"p = {p}")
print(f"a = {a}")
print(f"b = {b}")
print(f"k = {k}")
print(f"E = {E}")
print(f"c1 = {c1}")
print(f"c2 = {c2}")
print(f"cipher_left = {cipher_left}")
print(f"cipher_right = {cipher_right}")
加密方式出来了,ecc曲线加密
K = k * G,c1 = m + r * K,c2 = r * G我们手算一下三个式子,最后化简得到m = c1 - k * c2
下面就是编写代码了
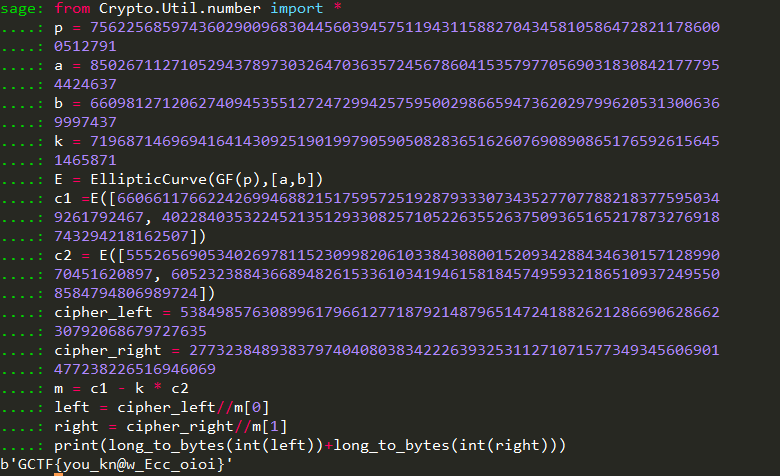
点击查看代码
#exp
from Crypto.Util.number import *
p = 75622568597436029009683044560394575119431158827043458105864728211786000512791
a = 85026711271052943789730326470363572456786041535797705690318308421777954424637
b = 66098127120627409453551272472994257595002986659473620297996205313006369997437
k = 71968714696941641430925190199790590508283651626076908908651765926156451465871
E = EllipticCurve(GF(p),[a,b])
c1 =E([66066117662242699468821517595725192879333073435277077882183775950349261792467, 40228403532245213512933082571052263552637509365165217873276918743294218162507])
c2 = E([55526569053402697811523099820610338430800152093428843463015712899070451620897, 60523238843668948261533610341946158184574959321865109372495508584794806989724])
cipher_left = 53849857630899617966127718792148796514724188262128669062866230792068679727635
cipher_right = 27732384893837974040803834222639325311271071577349345606901477238226516946069
m = c1 - k * c2
left = cipher_left//m[0]
right = cipher_right//m[1]
print(long_to_bytes(int(left))+long_to_bytes(int(right)))
本文来自博客园,作者:{Alexander17},转载请注明原文链接:{https://home.cnblogs.com/u/alexander17}



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 25岁的心里话
· 闲置电脑爆改个人服务器(超详细) #公网映射 #Vmware虚拟网络编辑器
· 零经验选手,Compose 一天开发一款小游戏!
· 通过 API 将Deepseek响应流式内容输出到前端
· AI Agent开发,如何调用三方的API Function,是通过提示词来发起调用的吗