Kubernetes Ingress介绍
1介绍:
实现全局的负债均衡,为集群中所有的应用提供统一的入口,授权每个应用达到具体pod的集合
2.pod与ingress关系
通过label-selector相关联
通过ingress controller实现pod的负载均衡(支持tcp/udp层和http 7层)
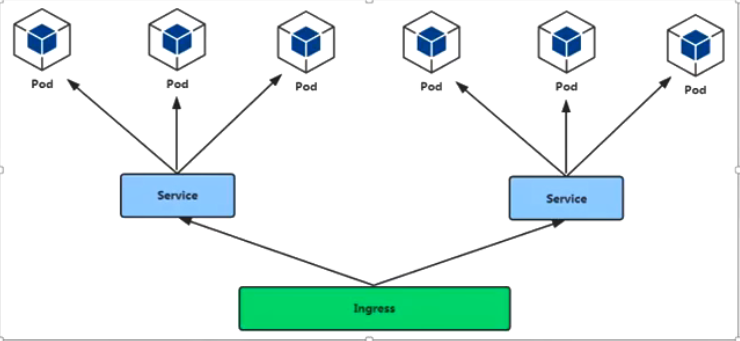
3.ingress controller
访问流程:用户->ingress controller (node) -> pod
3.1部署ingress controller
官方部署文档https://github.com/kubernetes?page=2
下载yaml文件

[root@m7-autocv-gpu01 demo]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/mandatory.yaml
创建ingress-nginx

[root@m7-autocv-gpu01 demo]# kubectl create -f mandatory.yaml namespace/ingress-nginx created configmap/nginx-configuration created configmap/tcp-services created configmap/udp-services created serviceaccount/nginx-ingress-serviceaccount created clusterrole.rbac.authorization.k8s.io/nginx-ingress-clusterrole created role.rbac.authorization.k8s.io/nginx-ingress-role created rolebinding.rbac.authorization.k8s.io/nginx-ingress-role-nisa-binding created clusterrolebinding.rbac.authorization.k8s.io/nginx-ingress-clusterrole-nisa-binding created deployment.apps/nginx-ingress-controller created 查看状态 [root@m7-autocv-gpu01 demo]# kubectl get pods -n ingress-nginx -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES nginx-ingress-controller-588f7dbb99-zx9pp 1/1 Running 0 15m 10.10.100.19 m7-autocv-gpu03 <none> <none> 查看监听的端口 [root@m7-autocv-gpu03 ~]# netstat -antp | grep 80 tcp 0 0 10.10.100.19:2380 0.0.0.0:* LISTEN 6793/etcd tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 53030/nginx: master ###监听的80端口 tcp 0 0 10.10.100.19:35654 10.10.100.18:2380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2380 10.10.100.18:47132 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2380 10.10.100.18:60912 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2380 10.10.100.17:37356 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2379 10.10.100.18:47380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2380 10.10.100.17:36606 ESTABLISHED 6793/etcd tcp 0 0 127.0.0.1:10246 127.0.0.1:60280 TIME_WAIT - tcp 0 0 10.10.100.19:2380 10.10.100.17:36260 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:50812 10.10.100.17:2380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:35354 10.10.100.18:2380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:50806 10.10.100.17:2380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:35574 10.10.100.18:2380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2380 10.10.100.17:36282 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2379 10.10.100.18:42580 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:51110 10.10.100.17:2380 ESTABLISHED 6793/etcd tcp 0 0 10.10.100.19:2380 10.10.100.18:60913 ESTABLISHED 6793/etcd [root@m7-autocv-gpu03 ~]#
注意,ingress-controller 会监听node节点上的80和443端口,因此尽量在使用端口时保留80和443给ingress-controller使用
3.2编写ingress规则
测试示例:
3.2.1测试http实现
用例service

[root@m7-autocv-gpu01 demo]# kubectl get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE my-service NodePort 10.254.213.182 <none> 80:31386/TCP 23h
默认访问
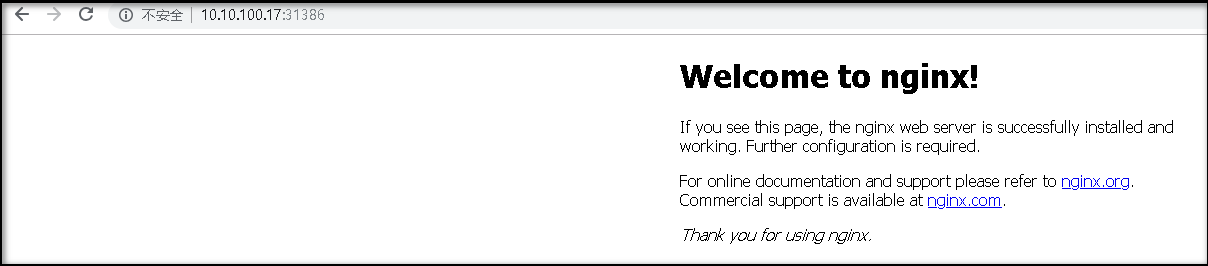
编写ingress配置yaml文件

[root@m7-autocv-gpu01 demo]# cat ingress.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: simple-fanout-example annotations: nginx.ingress.kubernetes.io/rewrite-target: / spec: rules: - host: foo.bar.com http: paths: - path: / backend: serviceName: my-service ###指定service的名字 servicePort: 80 ###对应集群端口 创建ingress [root@m7-autocv-gpu01 demo]# kubectl apply -f ingress.yaml ingress.extensions/simple-fanout-example created 查看刚创建的ingress [root@m7-autocv-gpu01 demo]# kubectl get ingress NAME HOSTS ADDRESS PORTS AGE simple-fanout-example foo.bar.com 80 114s
模拟访问
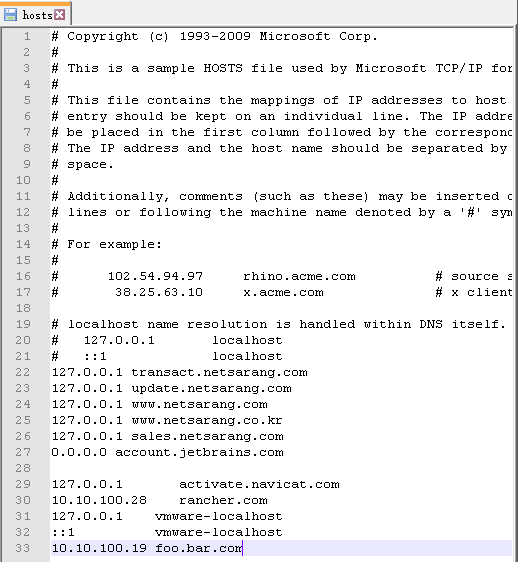
绑定host文件
修改windows 的host文件将node的ip 和解析域名添加进来
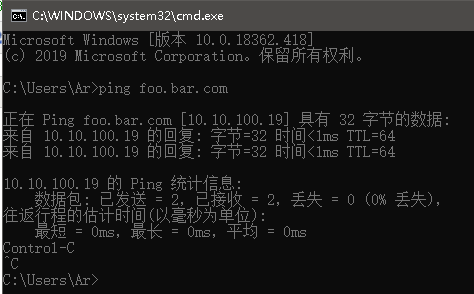
测试ping 域名是否可以通信
通过域名访问刚才的地址
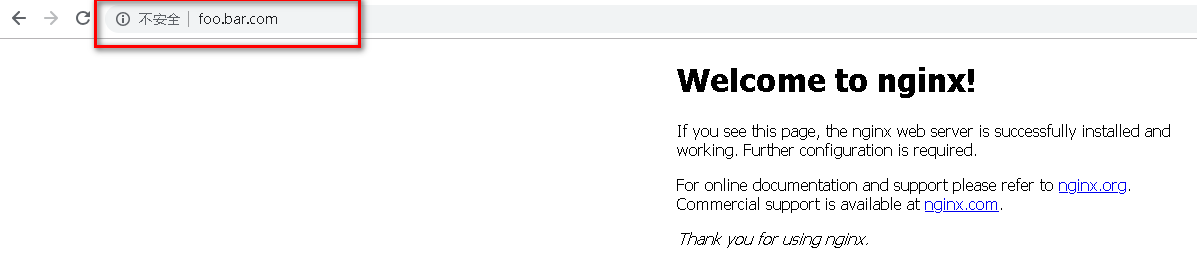
3.2.2测试https访问设置
自签发证书,在测试中使用该证书访问项目

[root@m7-autocv-gpu01 certs]# cat certs.sh cat > ca-config.json <<EOF { "signing": { "default": { "expiry": "87600h" }, "profiles": { "kubernetes": { "usages": [ "signing", "key encipherment", "server auth", "client auth" ], "expiry": "87600h" } } } } EOF cat > ca-csr.json <<EOF { "CN": "kubernetes", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "BeiJing", "L": "BeiJing", "O": "k8s" } ] } EOF cfssl gencert -initca ca-csr.json | cfssljson -bare ca - cat > sslexample.foo.com-csr.json <<EOF { "CN": "sslexample.foo.com", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "BeiJing", "L": "BeiJing" } ] } EOF cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes sslexample.foo.com-csr.json | cfssljson -bare sslexample.foo.com 将以上命令写入脚本执行 执行结果 [root@m7-autocv-gpu01 certs]# bash certs.sh 2019/11/10 13:49:41 [INFO] generating a new CA key and certificate from CSR 2019/11/10 13:49:41 [INFO] generate received request 2019/11/10 13:49:41 [INFO] received CSR 2019/11/10 13:49:41 [INFO] generating key: rsa-2048 2019/11/10 13:49:41 [INFO] encoded CSR 2019/11/10 13:49:41 [INFO] signed certificate with serial number 638697262036687898124676478943833799234359853509 2019/11/10 13:49:41 [INFO] generate received request 2019/11/10 13:49:41 [INFO] received CSR 2019/11/10 13:49:41 [INFO] generating key: rsa-2048 2019/11/10 13:49:41 [INFO] encoded CSR 2019/11/10 13:49:41 [INFO] signed certificate with serial number 239083797930979847717360877652088917484406734010 2019/11/10 13:49:41 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). [root@m7-autocv-gpu01 certs]# ls ca-config.json ca-csr.json ca.pem sslexample.foo.com.csr sslexample.foo.com-key.pem ca.csr ca-key.pem certs.sh sslexample.foo.com-csr.json sslexample.foo.com.pem
通过cubectl 创建保存到secret中

[root@m7-autocv-gpu01 certs]# kubectl create secret tls sslexample-foo-com --cert=sslexample.foo.com.pem --key=sslexample.foo.com-key.pem 查看创建的secret secret/sslexample-foo-com created [root@m7-autocv-gpu01 certs]# kubectl get secret NAME TYPE DATA AGE sslexample-foo-com kubernetes.io/tls 2 8s [root@m7-autocv-gpu01 certs]#
创建ingress并指定证书

[root@m7-autocv-gpu01 demo]# cat ingress-https.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: tls-example-ingress spec: tls: - hosts: - sslexample.foo.com secretName: sslexample-foo-com ###对应创建的证书secret的名字 rules: - host: sslexample.foo.com http: paths: - path: / backend: serviceName: my-service ###绑定的service的名字 servicePort: 80 [root@m7-autocv-gpu01 demo]# kubectl apply -f ingress-https.yaml ingress.extensions/tls-example-ingress created
创建完成测试通过https 访问demo
绑定hosts文件
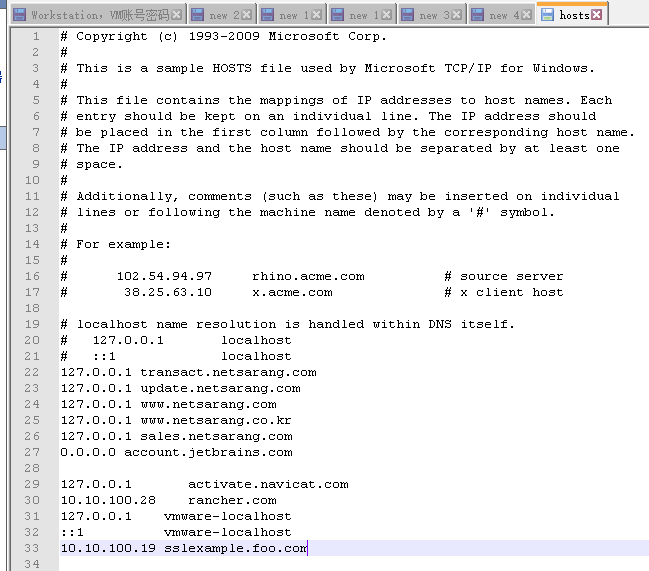
浏览器访问
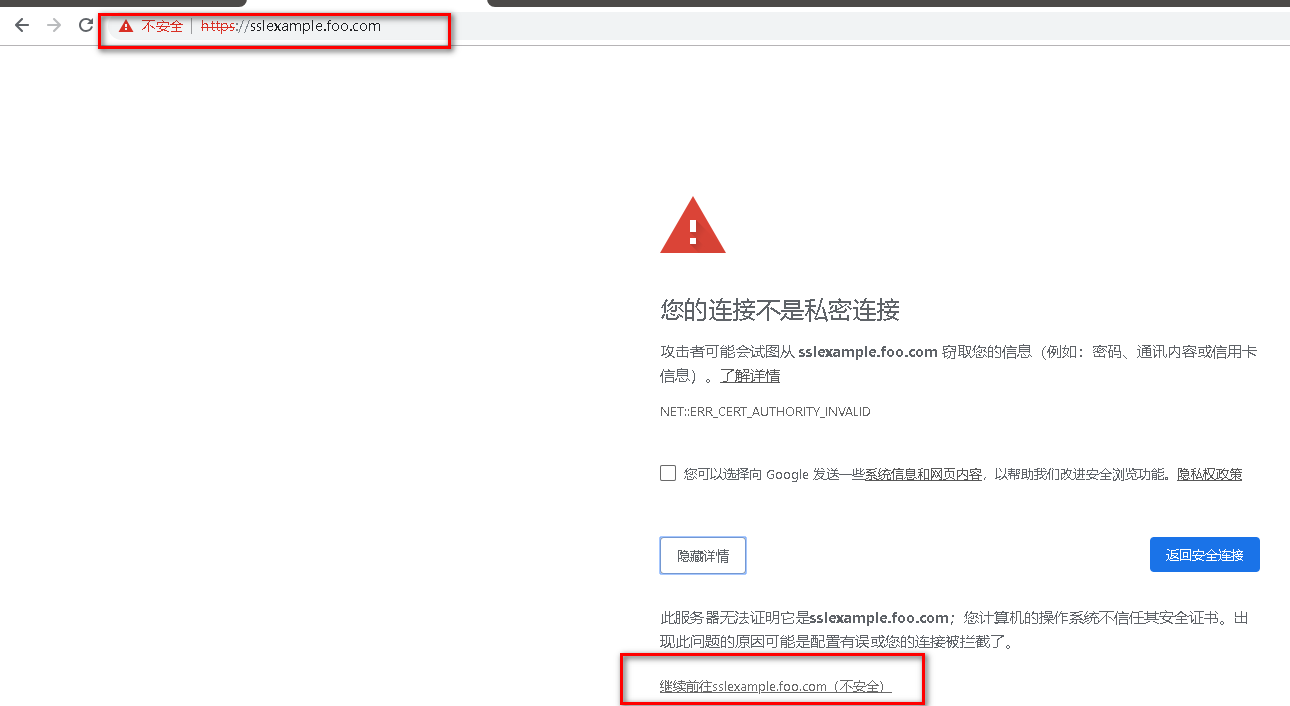
查看当前访问的证书
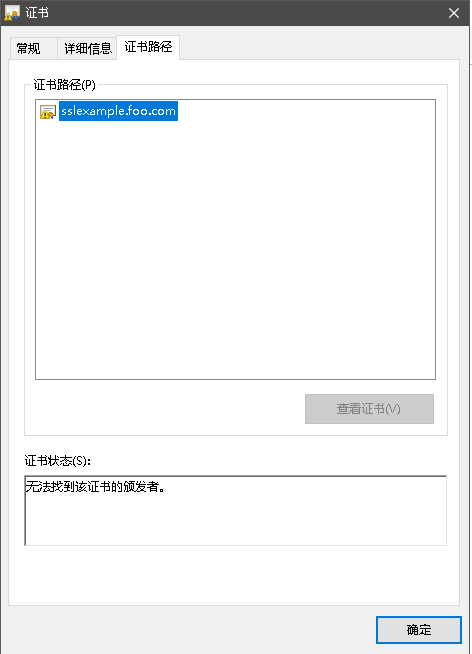
4.小结
四层、七层负载均衡转发
支持自定义service访问策略
只支持基于域名的网站访问
支持TLS





