Kubernetes 安全机制介绍
1.RBAC简介
2.RBC基本架构
3.示例
3.1创建测试命名空间

[root@m7-autocv-gpu01 ~]# kubectl create ns ctnrs namespace/ctnrs created [root@m7-autocv-gpu01 ~]# kubectl get ns NAME STATUS AGE ctnrs Active 4s default Active 164d kube-node-lease Active 164d kube-public Active 164d kube-system Active 164d
3.2在自定义的命名空间下运行测试pod

[root@m7-autocv-gpu01 ~]# kubectl run nginx --image=nginx -n ctnrs kubectl run --generator=deployment/apps.v1 is DEPRECATED and will be removed in a future version. Use kubectl run --generator=run-pod/v1 or kubectl create instead. deployment.apps/nginx created 扩展pod [root@m7-autocv-gpu01 ~]# kubectl scale deployment/nginx --replicas=2 -n ctnrs deployment.extensions/nginx scaled [root@m7-autocv-gpu01 ~]# kubectl get pods -n ctnrs NAME READY STATUS RESTARTS AGE nginx-7db9fccd9b-rqg55 1/1 Running 0 106s nginx-7db9fccd9b-ts8xt 1/1 Running 0 10s
3.3授权对pod 的权限

[root@m7-autocv-gpu01 demo]# cat rbac-role.yaml kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: namespace: ctnrs name: pod-reader rules: - apiGroups: [""] resources: ["pods"] verbs: ["get", "watch", "list"] 创建角色 [root@m7-autocv-gpu01 demo]# kubectl create -f rbac-role.yaml role.rbac.authorization.k8s.io/pod-reader created 查看创建结果 [root@m7-autocv-gpu01 demo]# kubectl get role -n ctnrs NAME AGE pod-reader 2m12s
3.4绑定角色

[root@m7-autocv-gpu01 demo]# cat rbac-rolebind.yaml kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: read-pods namespace: ctnrs subjects: - kind: User name: testuser ###绑定的用户名 apiGroup: rbac.authorization.k8s.io roleRef: kind: Role name: pod-reader ###绑定的对应角色,3.3创建的角色 apiGroup: rbac.authorization.k8s.io 创建角色绑定 [root@m7-autocv-gpu01 demo]# kubectl create -f rbac-rolebind.yaml rolebinding.rbac.authorization.k8s.io/read-pods created 查看角色及绑定 [root@m7-autocv-gpu01 demo]# kubectl get role,rolebinding -n ctnrs NAME AGE role.rbac.authorization.k8s.io/pod-reader 14m NAME AGE rolebinding.rbac.authorization.k8s.io/read-pods 2m35s
3.5基于证书识别用户身份
3.5.1 签发用户证书

cat > testuser-csr.json <<EOF { "CN": "testuser", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "BeiJing", "ST": "BeiJing" } ] } EOF 生成用户证书 [root@m7-autocv-gpu01 testuser]# cfssl gencert -ca=/opt/k8s/work/ca.pem -ca-key=/opt/k8s/work/ca-key.pem -config=/opt/k8s/work/ca-config.json -profile=kubernetes testuser-csr.json | cfssljson -bare testuser 2019/11/06 10:56:30 [INFO] generate received request 2019/11/06 10:56:30 [INFO] received CSR 2019/11/06 10:56:30 [INFO] generating key: rsa-2048 2019/11/06 10:56:30 [INFO] encoded CSR 2019/11/06 10:56:30 [INFO] signed certificate with serial number 382162107555901030770018868606500425334993601198 2019/11/06 10:56:30 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). [root@m7-autocv-gpu01 testuser]# ls rabc-user.sh testuser.csr testuser-csr.json testuser-key.pem testuser.pem
3.5.2创建用户配置文件

[root@m7-autocv-gpu01 testuser]# kubectl config set-cluster kubernetes \ > --certificate-authority=/opt/k8s/work/ca.pem \ > --embed-certs=true \ > --server=https://10.10.100.17:6443 \ > --kubeconfig=testuser-kubeconfig Cluster "kubernetes" set. [root@m7-autocv-gpu01 testuser]# ls rabc-user.sh testuser.csr testuser-csr.json testuser-key.pem testuser-kubeconfig testuser.pem [root@m7-autocv-gpu01 testuser]# kubectl config set-credentials testuser \ > --client-key=testuser-key.pem \ > --client-certificate=testuser.pem \ > --embed-certs=true \ > --kubeconfig=testuser-kubeconfig User "testuser" set. [root@m7-autocv-gpu01 testuser]# kubectl config set-context default \ > --cluster=kubernetes \ > --user=testuser \ > --kubeconfig=testuser-kubeconfig Context "default" created. [root@m7-autocv-gpu01 testuser]# kubectl config use-context default --kubeconfig=testuser-kubeconfig Switched to context "default".
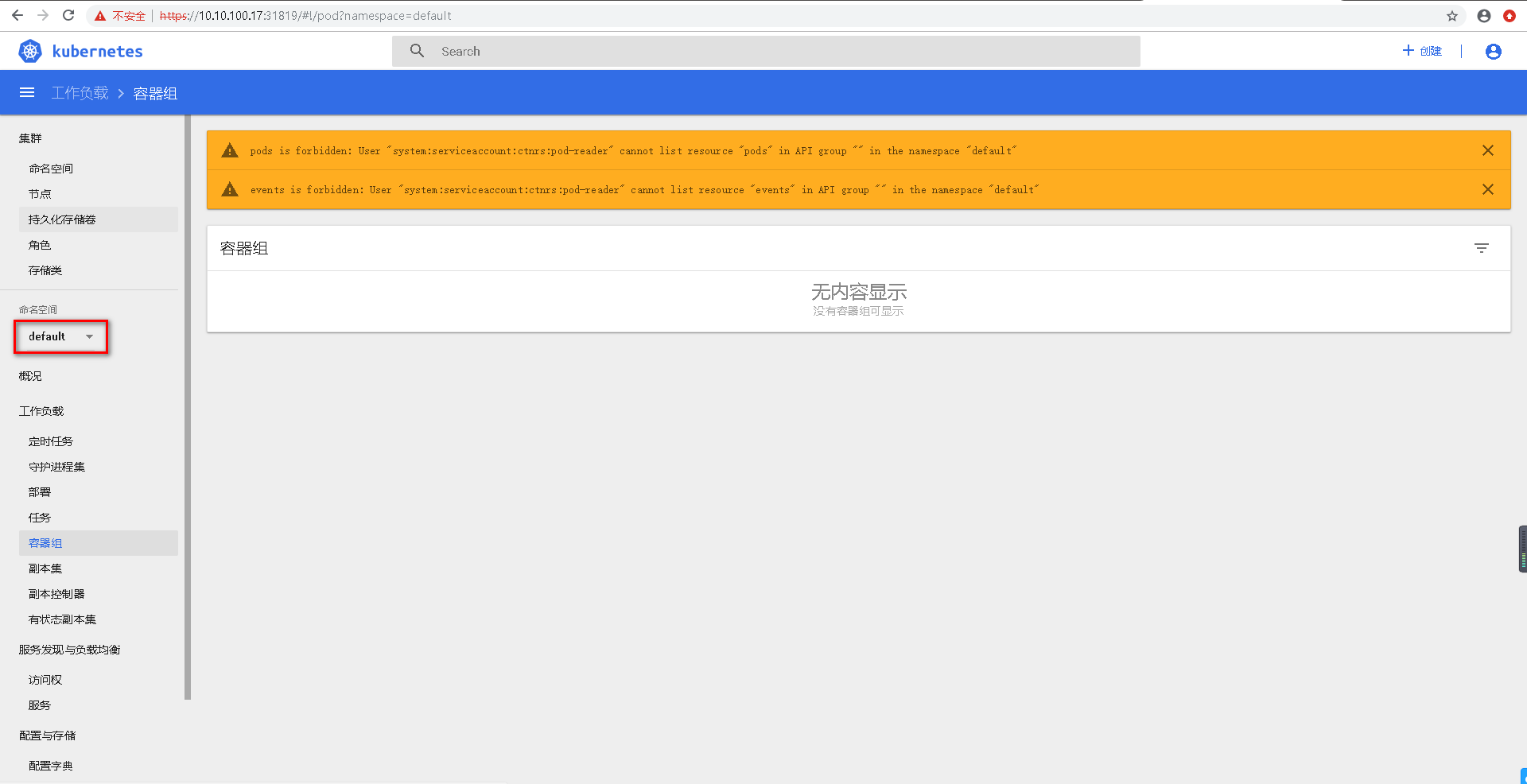
3.6验证结果

[root@m7-autocv-gpu01 testuser]# kubectl --kubeconfig=testuser-kubeconfig get pods -n ctnrs NAME READY STATUS RESTARTS AGE nginx-7db9fccd9b-rqg55 1/1 Running 0 94m nginx-7db9fccd9b-ts8xt 1/1 Running 0 92m testuser能够查看pod [root@m7-autocv-gpu01 testuser]# kubectl --kubeconfig=testuser-kubeconfig get svc -n ctnrs Error from server (Forbidden): services is forbidden: User "testuser" cannot list resource "services" in API group "" in the namespace "ctnrs" [root@m7-autocv-gpu01 testuser]# kubectl --kubeconfig=testuser-kubeconfig get svc Error from server (Forbidden): services is forbidden: User "testuser" cannot list resource "services" in API group "" in the namespace "default" testuser 不能查看service,包括默认命名空间中的色vice
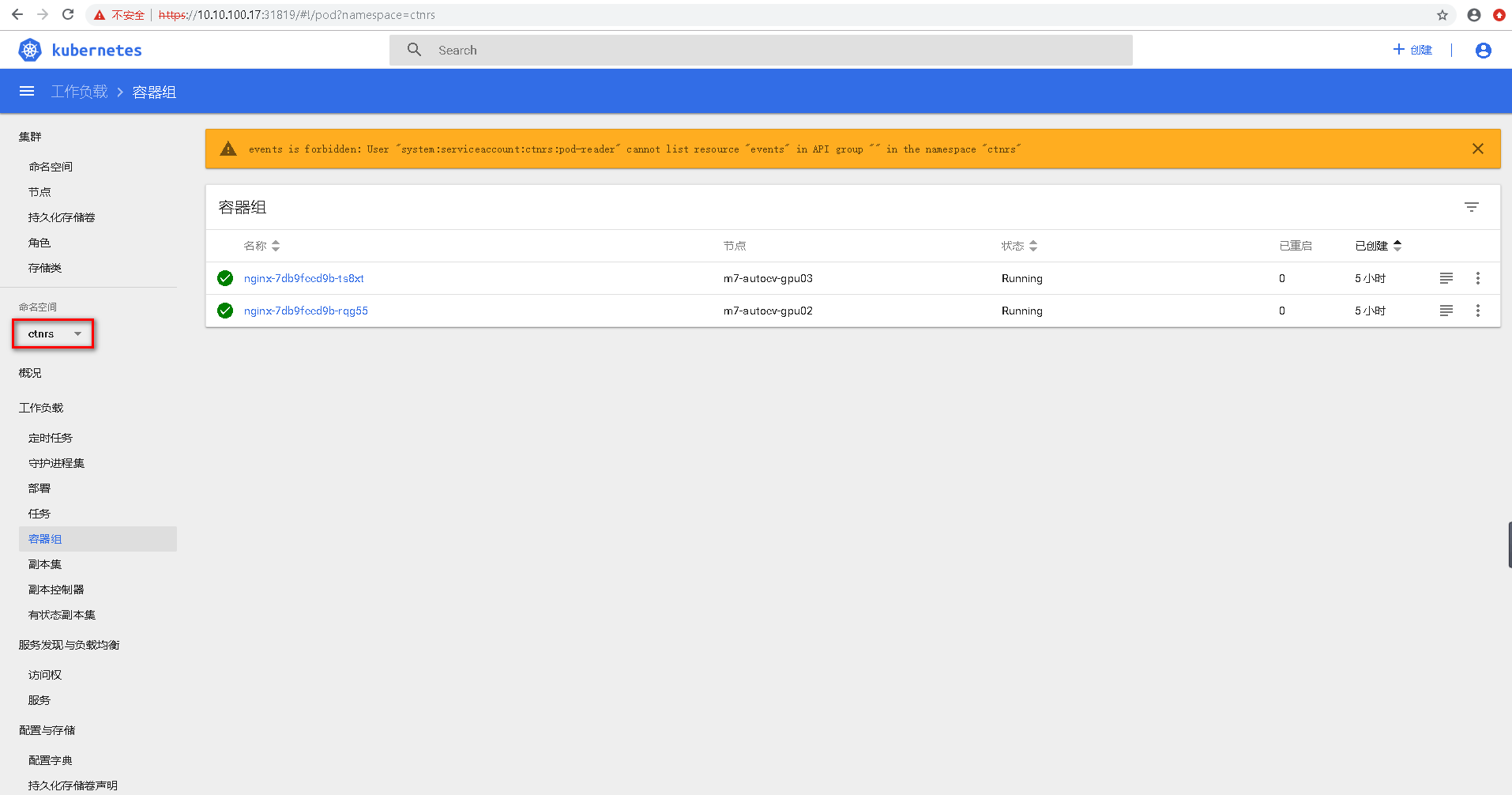
3.7UI界面验证
3.7.1 创建ServiceAccount

[root@m7-autocv-gpu01 demo]# cat sa.yaml apiVersion: v1 kind: ServiceAccount metadata: name: pod-reader namespace: ctnrs --- kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: sa-read-pods namespace: ctnrs subjects: - kind: ServiceAccount name: pod-reader roleRef: kind: Role name: pod-reader apiGroup: rbac.authorization.k8s.io [root@m7-autocv-gpu01 demo]# 创建ServiceAccount [root@m7-autocv-gpu01 demo]# kubectl apply -f sa.yaml serviceaccount/pod-reader created 查看 [root@m7-autocv-gpu01 demo]# kubectl get ServiceAccount -n ctnrs NAME SECRETS AGE default 1 5h46m pod-reader 1 6m55s
3.7.2 查看具体的token

查看在指定命名空间下生成的serviceaccount [root@m7-autocv-gpu01 demo]# kubectl get serviceaccount -n ctnrs NAME SECRETS AGE default 1 5h52m pod-reader 1 12m 查看详细的serviceaccount内容 [root@m7-autocv-gpu01 demo]# kubectl describe serviceaccount pod-reader -n ctnrs Name: pod-reader Namespace: ctnrs Labels: <none> Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"name":"pod-reader","namespace":"ctnrs"}} Image pull secrets: <none> Mountable secrets: pod-reader-token-sb258 Tokens: pod-reader-token-sb258 ###serviceaccount 对应的token名字 Events: <none> 查看serviceaccount对应的token内容 [root@m7-autocv-gpu01 demo]# kubectl describe secret pod-reader-token-sb258 -n ctnrs Name: pod-reader-token-sb258 Namespace: ctnrs Labels: <none> Annotations: kubernetes.io/service-account.name: pod-reader kubernetes.io/service-account.uid: fb2715d4-0067-11ea-88af-000c2909efb3 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1367 bytes namespace: 5 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJjdG5ycyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJwb2QtcmVhZGVyLXRva2VuLXNiMjU4Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6InBvZC1yZWFkZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmYjI3MTVkNC0wMDY3LTExZWEtODhhZi0wMDBjMjkwOWVmYjMiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6Y3RucnM6cG9kLXJlYWRlciJ9.MEhsxvdSMqil3yKrtfQ5XQiEwWZZNxFaFaHXj8lCOHQ4jTuSDnS-9FN40Jj8zkOSsIA80dlDucxrwfvhrW0U5uUBztTL0WChDHcsvXi_tuPMurpRmRM4Q4GKXVho67s3aTiKH_i6ZZy4OT66iNuyxgvRMz4AG9D82lQfiRpBryvPE4jFVZ4rHR_yzVoHfFS8aahR5ZgwBxLmBUQlNcHE9QCddE7bBydUJgJjxMUubgHFzKMMfbt7g2dbBnW8jkTBttM9LneNOm195b5ETiVz2U-v0a6gMHWG3pqaTmj3RArqXMNF17wNYPRy6qyeO3H58wD_MBEw8Q-apYBN3IRn_g
3.7.3登陆UI验证结果