Kubernetes UI(dashboard)部署
1.下载地址
https://github.com/kubernetes/kubernetes/tree/master/cluster/addons/dashboard
2.上传文件
将下载的dashboard的yaml文件上传到master01节点
为dashborad创建一个文件目录
[root@dn01 ~]# mkdir /root/k8s/dashboard/ -p && cd /root/k8s/dashboard/
[root@dn01 dashboard]# ls *.yaml
dashboard-configmap.yaml dashboard-controller.yaml dashboard-rbac.yaml dashboard-secret.yaml dashboard-service.yaml
3.创建Dashboard 图形访问界面
[root@dn01 dashboard]# kubectl create -f dashboard-rbac.yaml
[root@dn01 dashboard]# kubectl create -f dashboard-secret.yaml
[root@dn01 dashboard]# kubectl create -f dashboard-configmap.yaml
[root@dn01 dashboard]# kubectl create -f dashboard-controller.yaml
[root@dn01 dashboard]# kubectl create -f dashboard-service.yaml
查看在kube-system命名空间生成的pods
[root@dn01 dashboard]# kubectl get pods,svc -n kube-system
NAME READY STATUS RESTARTS AGE
pod/kubernetes-dashboard-7dffbccd68-64xpk 1/1 Running 1 17h
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes-dashboard NodePort 10.0.0.11 <none> 443:30001/TCP 18h
创建UI登陆用户,执行yaml文件内容:

[root@dn01 dashboard]# cat k8s-admin.yaml apiVersion: v1 kind: ServiceAccount metadata: name: dashboard-admin namespace: kube-system --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: dashboard-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kube-system roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io [root@dn01 dashboard]#
[root@dn01 dashboard]# kubectl create -f k8s-admin.yaml
查看生成机密文件

[root@dn01 dashboard]# kubectl get secret -n kube-system NAME TYPE DATA AGE dashboard-admin-token-mmchp kubernetes.io/service-account-token 3 18h default-token-s966n kubernetes.io/service-account-token 3 9d kubernetes-dashboard-certs Opaque 11 17h kubernetes-dashboard-key-holder Opaque 2 19h kubernetes-dashboard-token-tprtg kubernetes.io/service-account-token 3 19h
查看令牌token 的内容

[root@dn01 dashboard]# kubectl describe secret dashboard-admin-token-mmchp -n kube-system Name: dashboard-admin-token-mmchp Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: dashboard-admin kubernetes.io/service-account.uid: 89b83aae-dee0-11e9-a916-000c299e3706 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1359 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbW1jaHAiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiODliODNhYWUtZGVlMC0xMWU5LWE5MTYtMDAwYzI5OWUzNzA2Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.AbSY3H0y91l9WtIxgN3c-ZtVewm-9Q0IPmNL7ANEGc3Tx_HR2B2THlm3Xc_4YsiwW3D64Bb8J11OCWdqgbgPEZYWu11xHQZTDUePiQnpnI-mFHHwYoav-BHWHb3PqmRDVp_XVUhzlIjnz4e6N6JchMf5hU0_9DSiP0NRrzlyl5hsCUmoa1VSI5ZNAgzJG895PidFrhtOhOLBuFBPaKImAo-JmZAW83R6-FwOzK4uKys4UPilr31w0YXhiiVc6YZrD6K4PfZo3WOG3pZpZHeLocMukqkcnKLdGZOFcffP23MGgz9D4bgJAPlKn_SP-vjf8H_mZDZXg8uBBSd-uJn8VA [root@dn01 dashboard]#
记录token的字符串内容:

eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbW1jaHAiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiODliODNhYWUtZGVlMC0xMWU5LWE5MTYtMDAwYzI5OWUzNzA2Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.AbSY3H0y91l9WtIxgN3c-ZtVewm-9Q0IPmNL7ANEGc3Tx_HR2B2THlm3Xc_4YsiwW3D64Bb8J11OCWdqgbgPEZYWu11xHQZTDUePiQnpnI-mFHHwYoav-BHWHb3PqmRDVp_XVUhzlIjnz4e6N6JchMf5hU0_9DSiP0NRrzlyl5hsCUmoa1VSI5ZNAgzJG895PidFrhtOhOLBuFBPaKImAo-JmZAW83R6-FwOzK4uKys4UPilr31w0YXhiiVc6YZrD6K4PfZo3WOG3pZpZHeLocMukqkcnKLdGZOFcffP23MGgz9D4bgJAPlKn_SP-vjf8H_mZDZXg8uBBSd-uJn8VA
此时通过火狐浏览器访问节点的30001端口,将上述token字符串内容输入到令牌口令中,确认登陆
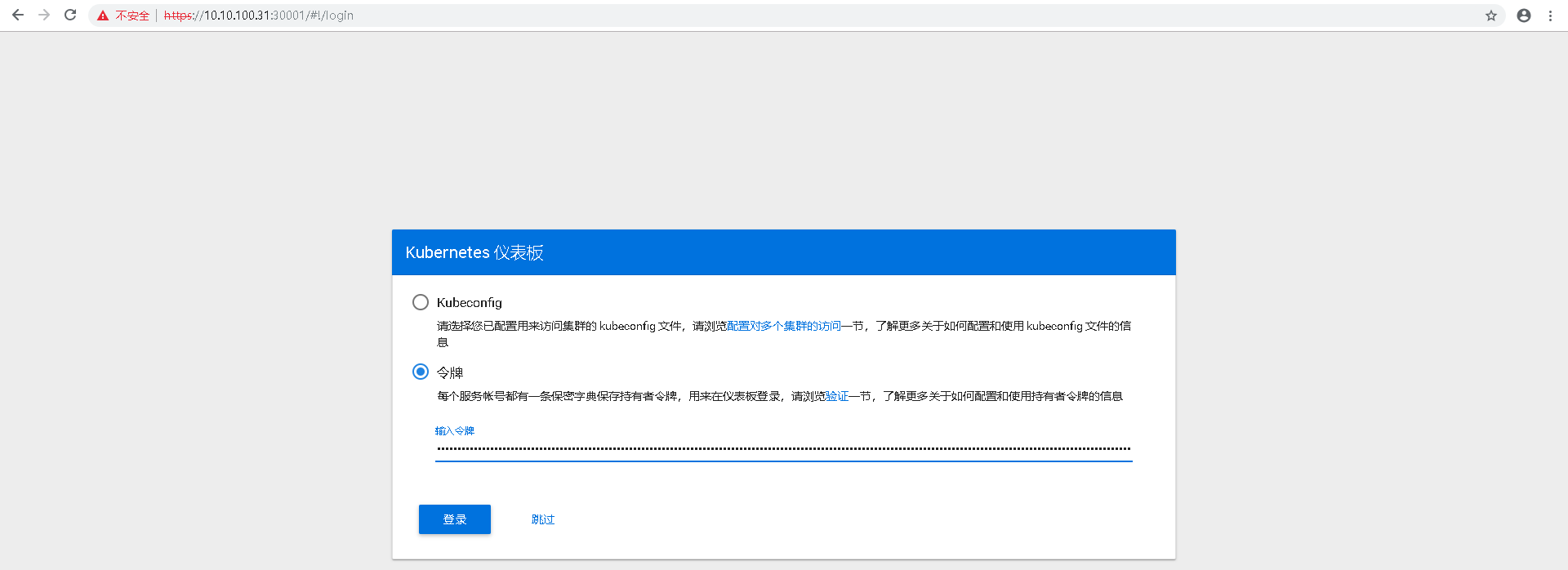
以上过程配置完成后仅限于特定的浏览器(一般是火狐浏览器,其他特殊浏览器没有测试),如果通过谷歌浏览器登陆,会因为证书不信任而无法继续浏览。
3.解决谷歌浏览器无法继续浏览无法显示登陆的问题(以下图片来自网络,除地址不同外,说明的问题相同)
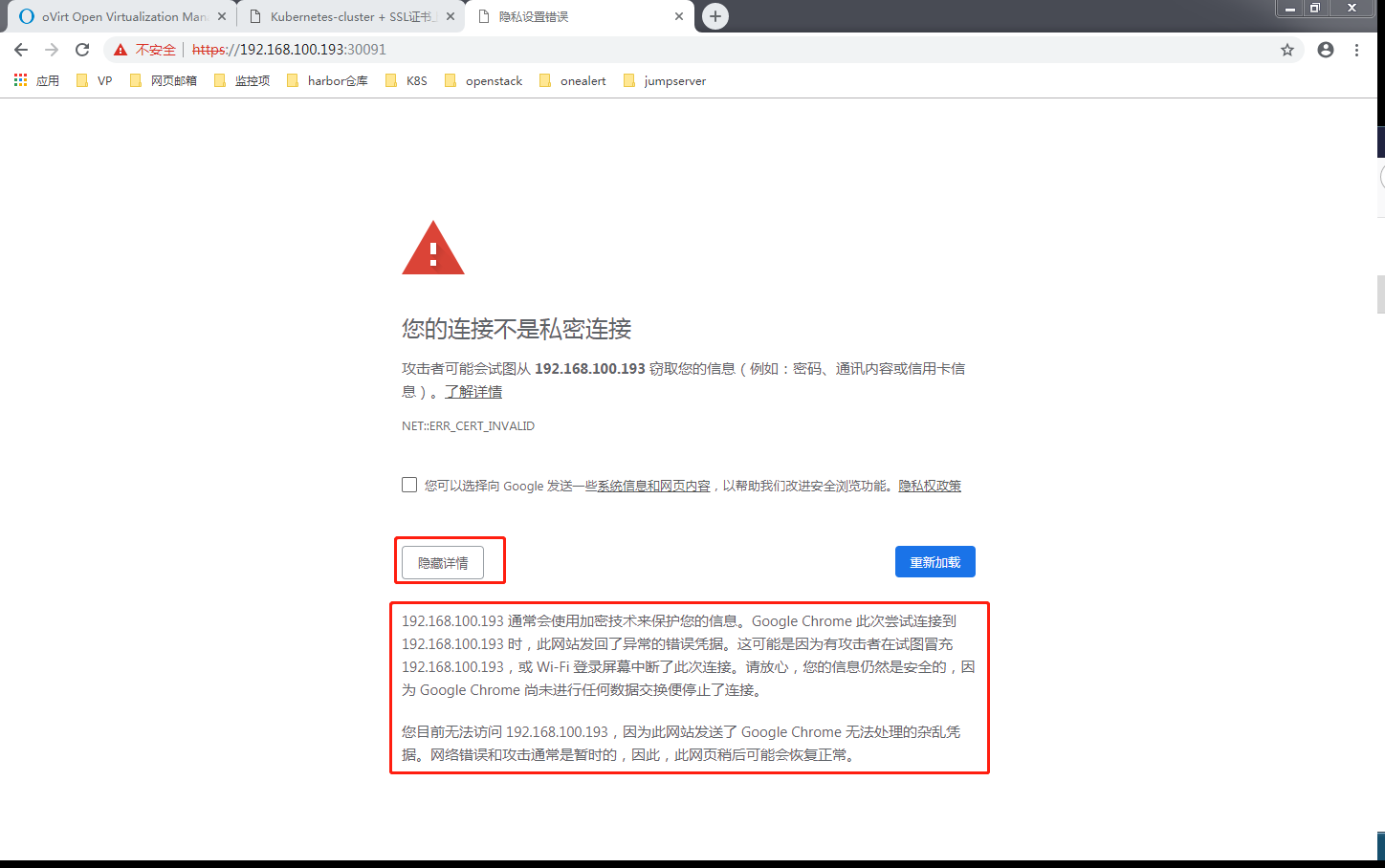
解决方法:
为dashboard 生成自签证书
证书的信息:

cat > dashboard-csr.json <<EOF { "CN": "Dashboard", "hosts":[], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ] } EOF
颁发证书:

cfssl gencert -ca=/root/k8s/k8s-cert/ca.pem -ca-key=/root/k8s/k8s-cert/ca-key.pem -config=/root/k8s/k8s-cert/ca-config.json -profile=kubernetes dashboard-csr.json | cfssljson -bare dashboard
删除dashboard默认的机密文件
kubectl delete secret kubernetes-dashboard-certs -n kube-system
重新生成dashboard 的机密文件
[root@dn01 dashboard]# pwd
/root/k8s/dashboard
[root@dn01 dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file=./ -n kube-system
修改dashboard-controller.yaml的文件内容,
在文件内容# PLATFORM-SPECIFIC ARGS HERE后面增加内容

# dashboard-controller.yaml # args: # # PLATFORM-SPECIFIC ARGS HERE # - --auto-generate-certificates 后面增加证书配置 # - --tls-key-file=dashboard-key.pem # - --tls-cert-file=dashboard.pem
dashboard-controller.yaml完整内容

root@dn01 dashboard]# cat dashboard-controller.yaml apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard addonmanager.kubernetes.io/mode: Reconcile name: kubernetes-dashboard namespace: kube-system --- apiVersion: apps/v1 kind: Deployment metadata: name: kubernetes-dashboard namespace: kube-system labels: k8s-app: kubernetes-dashboard kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile spec: selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard annotations: scheduler.alpha.kubernetes.io/critical-pod: '' seccomp.security.alpha.kubernetes.io/pod: 'docker/default' spec: priorityClassName: system-cluster-critical containers: - name: kubernetes-dashboard image: siriuszg/kubernetes-dashboard-amd64:v1.8.3 resources: limits: cpu: 100m memory: 300Mi requests: cpu: 50m memory: 100Mi ports: - containerPort: 8443 protocol: TCP args: # PLATFORM-SPECIFIC ARGS HERE - --auto-generate-certificates - --tls-key-file=dashboard-key.pem - --tls-cert-file=dashboard.pem volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs - name: tmp-volume mountPath: /tmp livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard tolerations: - key: "CriticalAddonsOnly" operator: "Exists" [root@dn01 dashboard]#
更新dashboard-controller
[root@dn01 dashboard]# kubectl apply -f dashboard-controller.yaml
尝试通过谷歌浏览器登陆
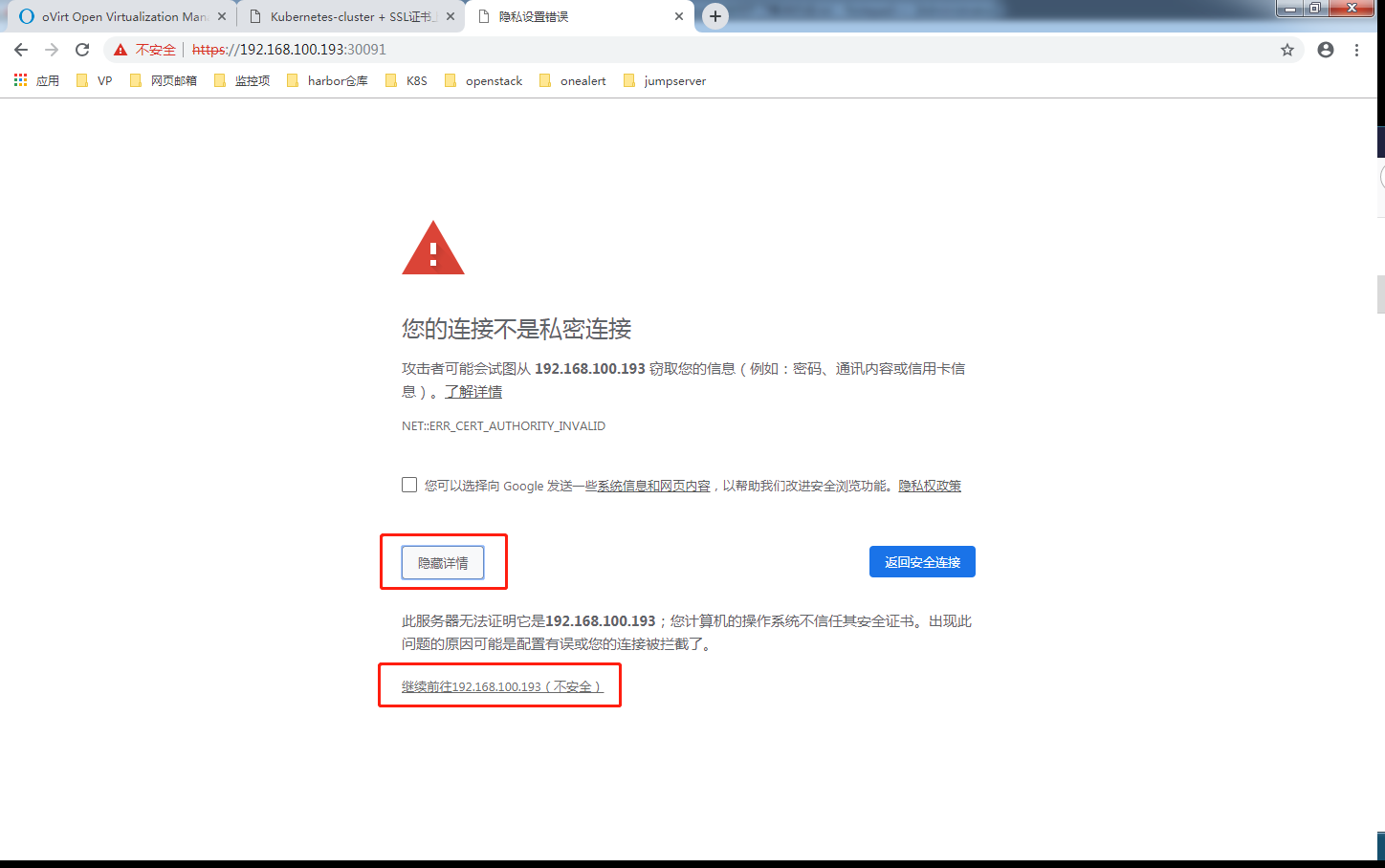
此时可以通过谷歌浏览器继续继续访问登陆。





