addslashes()函数绕过
前言
该文章主要描述了addslashes()函数常见的编码绕过的情况
2020-01-07
天象独行
函数addslashes()作用是返回在预定义字符之前添加反斜杠的字符串。预定义字符是单引号(')双引号(")反斜杠(\)NULL。比如下图,这样就造成了得结果是我们无法在注入的过程当中使用单引号(’)。在字符行注入的时候是比较头疼的一件事情。下面我们讨论一下一些情况可以绕过addslashes()函数。
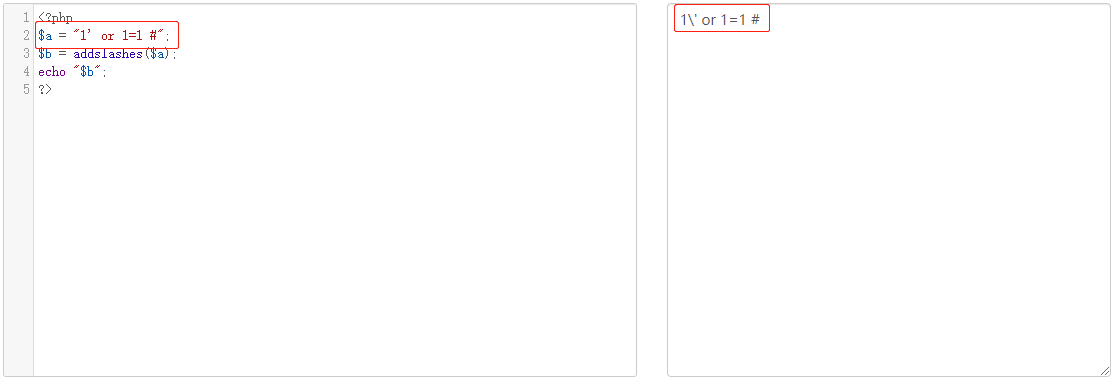
测试代码如下:
1 <!DOCTYPE html> 2 <HTML> 3 <head> 4 <title>过滤函数和类---addslashes()函数</title> 5 6 </head> 7 <body> 8 <p>addslashes() 函数返回在预定义字符之前添加反斜杠的字符串。预定义字符是单引号(')双引号(")反斜杠(\)NULL</p><br/> 9 <form action="" method="POST"> 10 Username : <input type="test" name = "username"><br/> 11 Password : <input type="Password" name = "password"><br/> 12 <input type="submit" value="Nest"><br/> 13 </from> 14 <?php 15 function deep_addslashes($str) 16 { 17 if(is_array($str)) 18 { 19 foreach($str as $key=>$val) 20 { 21 $str[$key] = deep_addslashes($val); 22 } 23 } 24 else 25 { 26 $str = addslashes($str); 27 } 28 return $str; 29 } 30 $username = $_POST["username"]; 31 $password = $_POST["password"]; 32 if (empty("$username") or empty("$password")) 33 { 34 die("输入字符不能为空"); 35 } 36 echo '$_POST接收后的username值:'; 37 echo "$username"; 38 echo "<br/>"; 39 //echo $password; 40 $connect_sql = mysqli_connect("127.0.0.1",'root','Password@2019','taodb'); 41 if (mysqli_connect_errno($connect_sql)) 42 { 43 echo "连接数据库失败".mysqli_connect_errno; 44 } 45 //mysqli_query($connect_sql,"SET NAMES 'gbk';"); 46 //$username = deep_addslashes("$username"); 47 //$username = urldecode($username); 48 $password = md5($password); 49 $sql = "select user_name,pwd from taodb.blue_user where user_name = '$username' and pwd = '$password';"; 50 echo "查询语句:"; 51 echo "select user_name,pwd from taodb.blue_user where user_name = '$username' and pwd = '$password';"; 52 echo "<br/>"; 53 $result = mysqli_query($connect_sql,$sql); 54 echo "登陆输出结果:"; 55 if (mysqli_fetch_row($result)) 56 { 57 echo "成功登陆"; 58 }else 59 { 60 echo "账号或密码错误"; 61 } 62 mysqli_close($connect_sql); 63 ?> 64 </body> 65 </HTML>
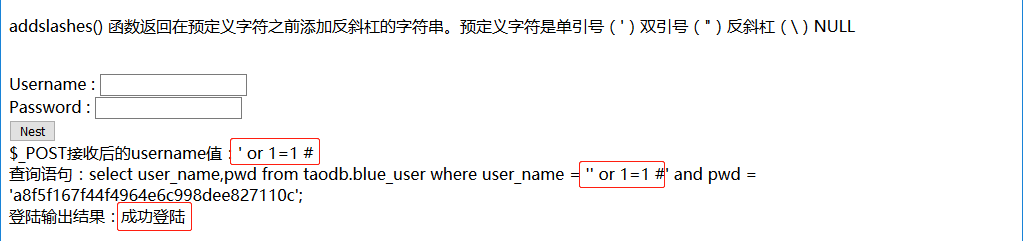
测试代码验证:
输入:‘ or 1=1 # 测试发现存在漏洞
0X01;编码绕过
很少一部分情况下,字符串在传入之后,带入数据库查询之前有个编码解码操作,然而在没有解码之后就没有对参数进行再一次的过滤。这个时候就存在了绕过addslashes()函数的可能性。
1;url解码导致addslashes()。下面我们调整一下代码,加入addslashes()函数以及urldecode()函数处理变量$username。
1 <!DOCTYPE html> 2 <HTML> 3 <head> 4 <title>过滤函数和类---addslashes()函数</title> 5 6 </head> 7 <body> 8 <p>addslashes() 函数返回在预定义字符之前添加反斜杠的字符串。预定义字符是单引号(')双引号(")反斜杠(\)NULL</p><br/> 9 <form action="" method="POST"> 10 Username : <input type="test" name = "username"><br/> 11 Password : <input type="Password" name = "password"><br/> 12 <input type="submit" value="Nest"><br/> 13 </from> 14 <?php 15 function deep_addslashes($str) 16 { 17 if(is_array($str)) 18 { 19 foreach($str as $key=>$val) 20 { 21 $str[$key] = deep_addslashes($val); 22 } 23 } 24 else 25 { 26 $str = addslashes($str); 27 } 28 return $str; 29 } 30 $username = $_POST["username"]; 31 $password = $_POST["password"]; 32 if (empty("$username") or empty("$password")) 33 { 34 die("输入字符不能为空"); 35 } 36 echo '$_POST接收后的username值:'; 37 echo "$username"; 38 echo "<br/>"; 39 //echo $password; 40 $connect_sql = mysqli_connect("127.0.0.1",'root','Password@2019','taodb'); 41 if (mysqli_connect_errno($connect_sql)) 42 { 43 echo "连接数据库失败".mysqli_connect_errno; 44 } 45 //mysqli_query($connect_sql,"SET NAMES 'gbk';"); 46 $username = deep_addslashes("$username"); 47 $username = urldecode($username); 48 $password = md5($password); 49 $sql = "select user_name,pwd from taodb.blue_user where user_name = '$username' and pwd = '$password';"; 50 echo "查询语句:"; 51 echo "select user_name,pwd from taodb.blue_user where user_name = '$username' and pwd = '$password';"; 52 echo "<br/>"; 53 $result = mysqli_query($connect_sql,$sql); 54 echo "登陆输出结果:"; 55 if (mysqli_fetch_row($result)) 56 { 57 echo "成功登陆"; 58 }else 59 { 60 echo "账号或密码错误"; 61 } 62 mysqli_close($connect_sql); 63 ?> 64 </body> 65 </HTML>
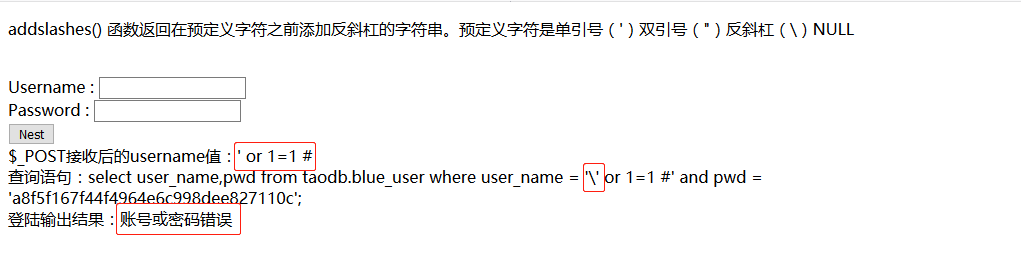
现在我们再次输入万能密码看看’ or 1=1 # 这个时候我们发现已经无法正常注入且单引号被转义。
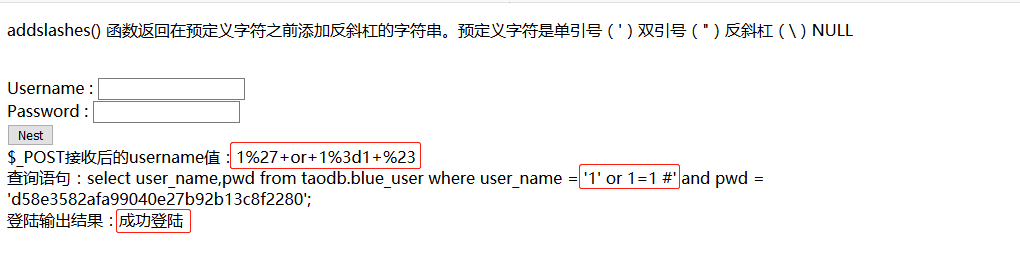
将万能密码进行url编码,再次注入:
2;base64解码绕过
测试代码当中插入“$username=base64_decode($username);”

编码万能密码:
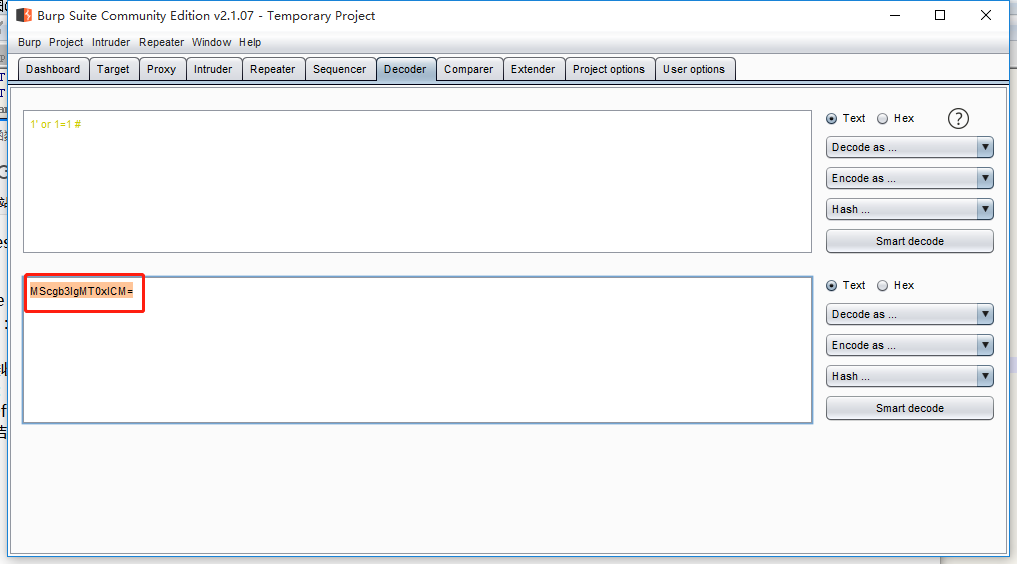
输入成功绕过:

2;宽字节注入
造成这种情况是因为数据库采用的是gbk编码。核心是一个字符串采用不同的编码方式,过滤函数认为是安全的,数据库的编码方式会造成影响。




