sqli-labs:less-11/12 简单SQL注入和身份验证漏洞综合
这两个靶场是一样的题,我就拿less-12说事了吧
首先,尝试胡乱输入密码进行测试:
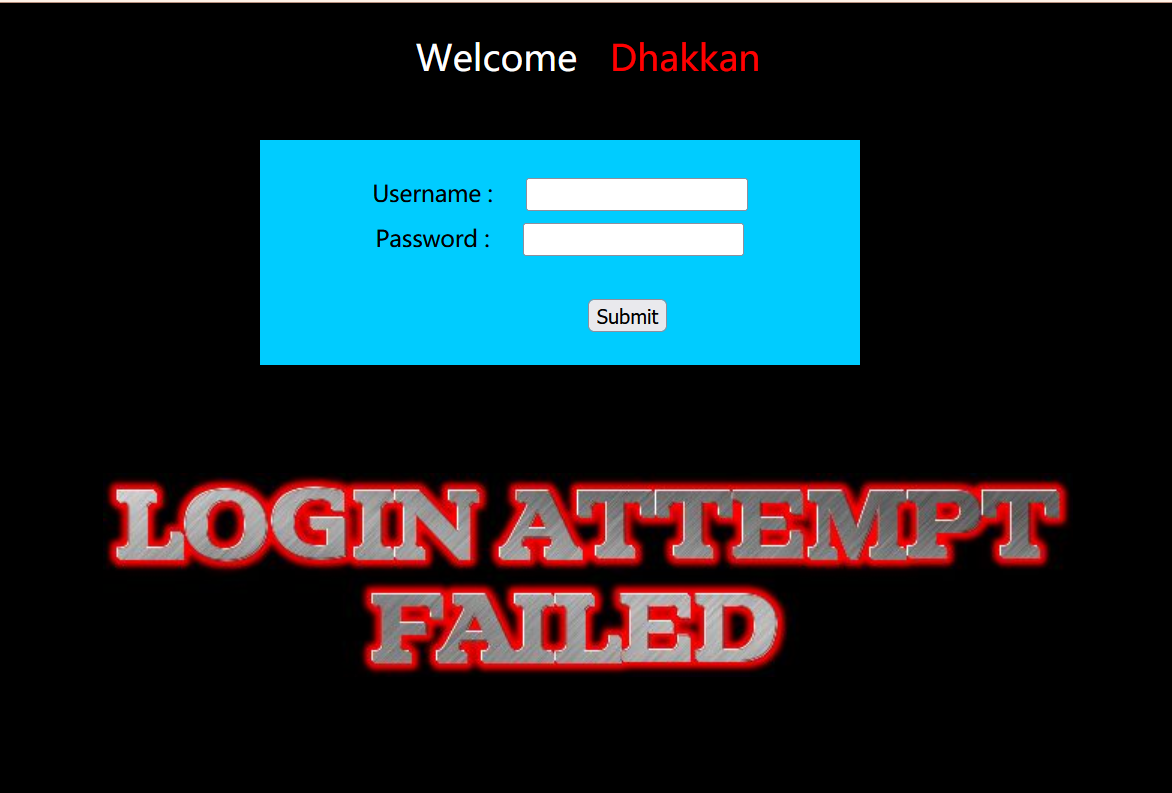
发现存在报错,这时用admin和admin这个正确的账号密码进行测试(1~10前面的题目告诉了)
发现有着正确的提示:

但是还不够,我们尝试在username后面加上单引号:
发现正常报错
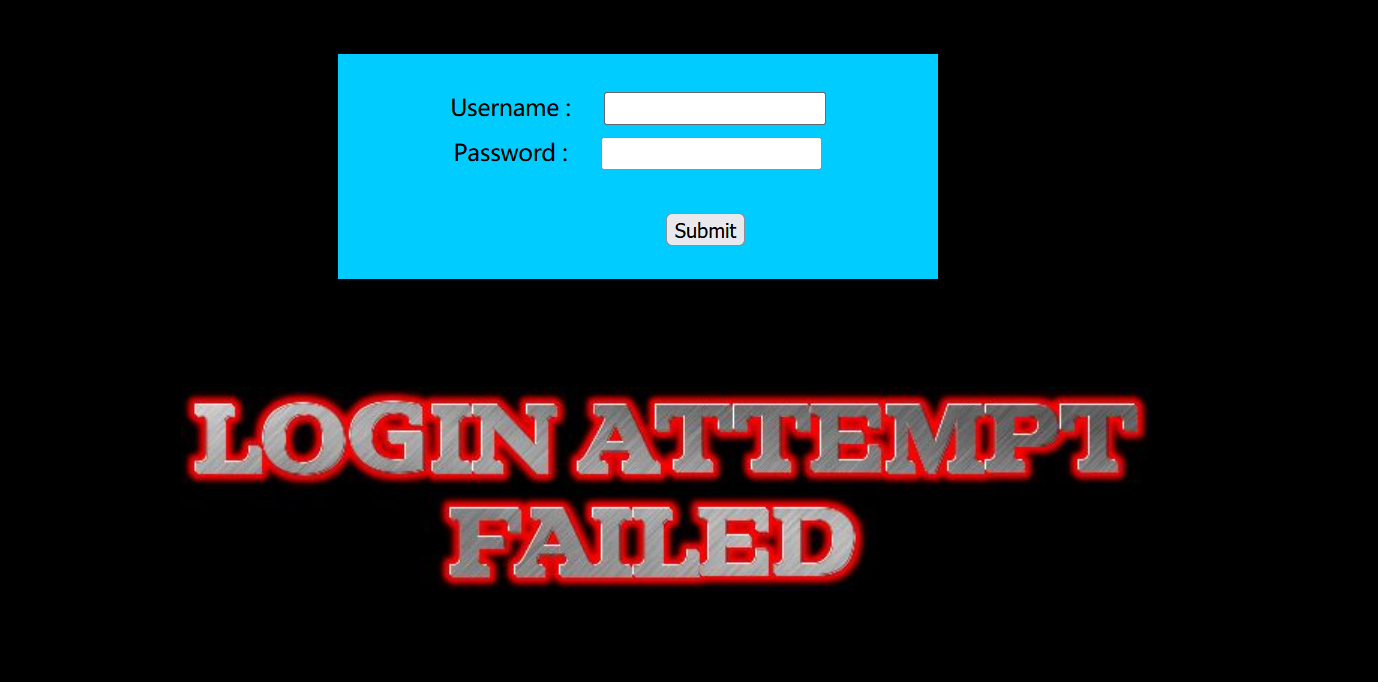
加上双引号尝试(没输入密码)

存在报错,这个就是SQL注入点:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '") and password=("") LIMIT 0,1' at line 1
构造SQL语句:
admin") and 1=1 %23
输入到其中去:

漏洞分析
首先进行代码审计:
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname."\n");
fwrite($fp,'Password:'.$passwd."\n");
fclose($fp);
// connectivity
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
//echo '<font color= "#0000ff">';
echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />';
echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
?>
- 首先,在判断语句
if(isset($_POST['uname']) && isset($_POST['passwd']))中只判断passwd是否存在,而并没有直接去查询数据库进行if判断,这样,会导致攻击者不需要用户名就可以进入if条件判断。 - 其次,在语句
在这里,就给SQL注入闭合双引号提供了可能,可以直接把passwd注释掉// connectivity $uname='"'.$uname.'"'; $passwd='"'.$passwd.'"'; @$sql="SELECT username, password FROM users WHERE username=($uname) and password=(\$passwd) LIMIT 0,1"; - 最后,报错:
print_r(mysql_error());,报错给注入者提供了便利。
综上所述,这些都是解决靶场的代码关键
本文来自博客园,作者:{Zeker62},转载请注明原文链接:https://www.cnblogs.com/Zeker62/p/15212119.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号