BUU
BUU
LSB
010看了一下没发现有什么问题
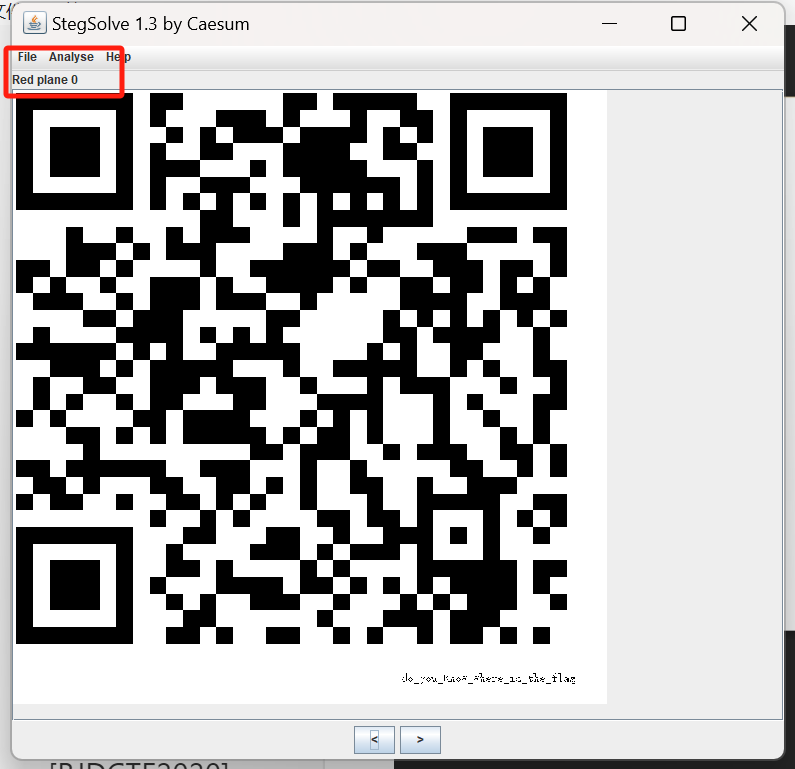
丢到stegsolve,rgb调到0的时候,是张二维码

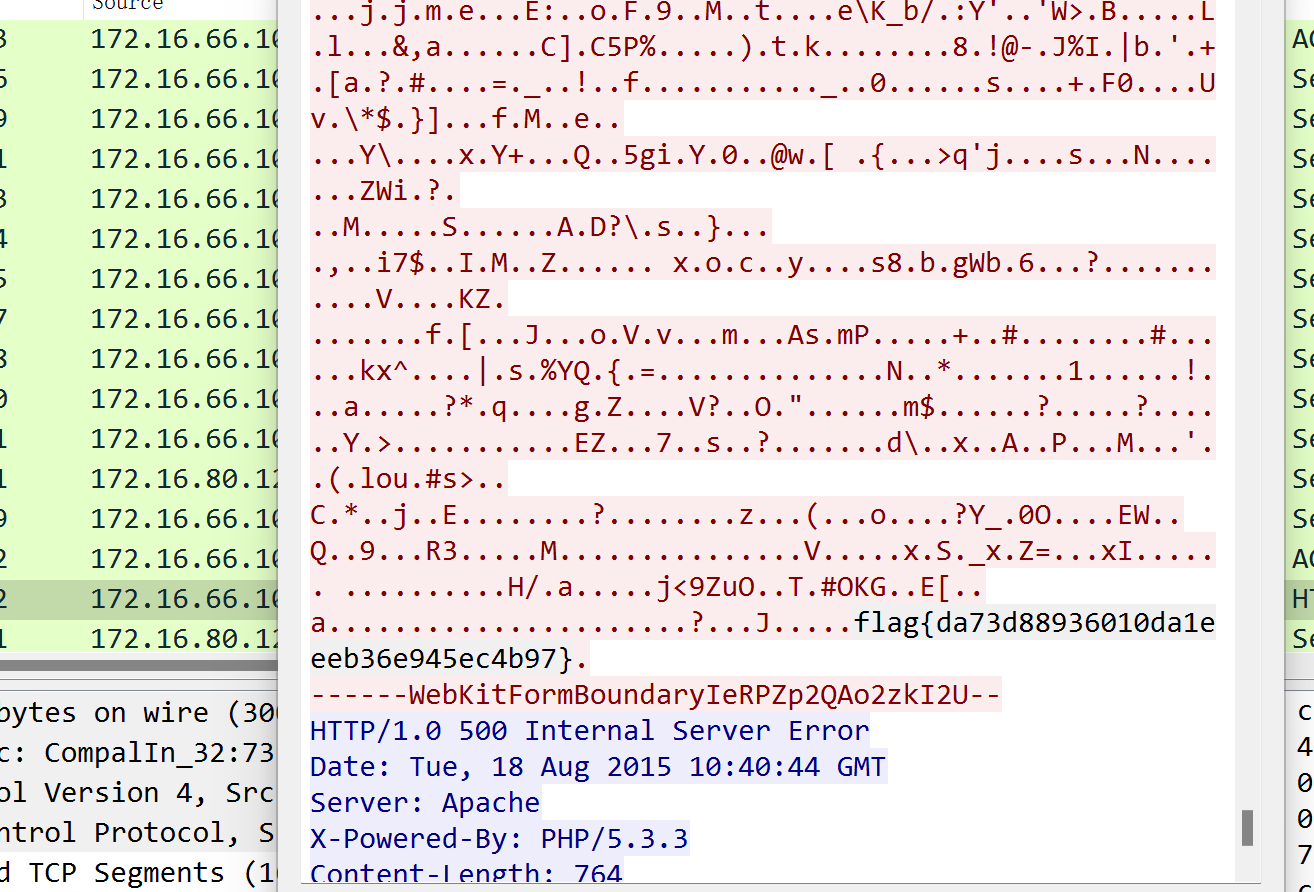
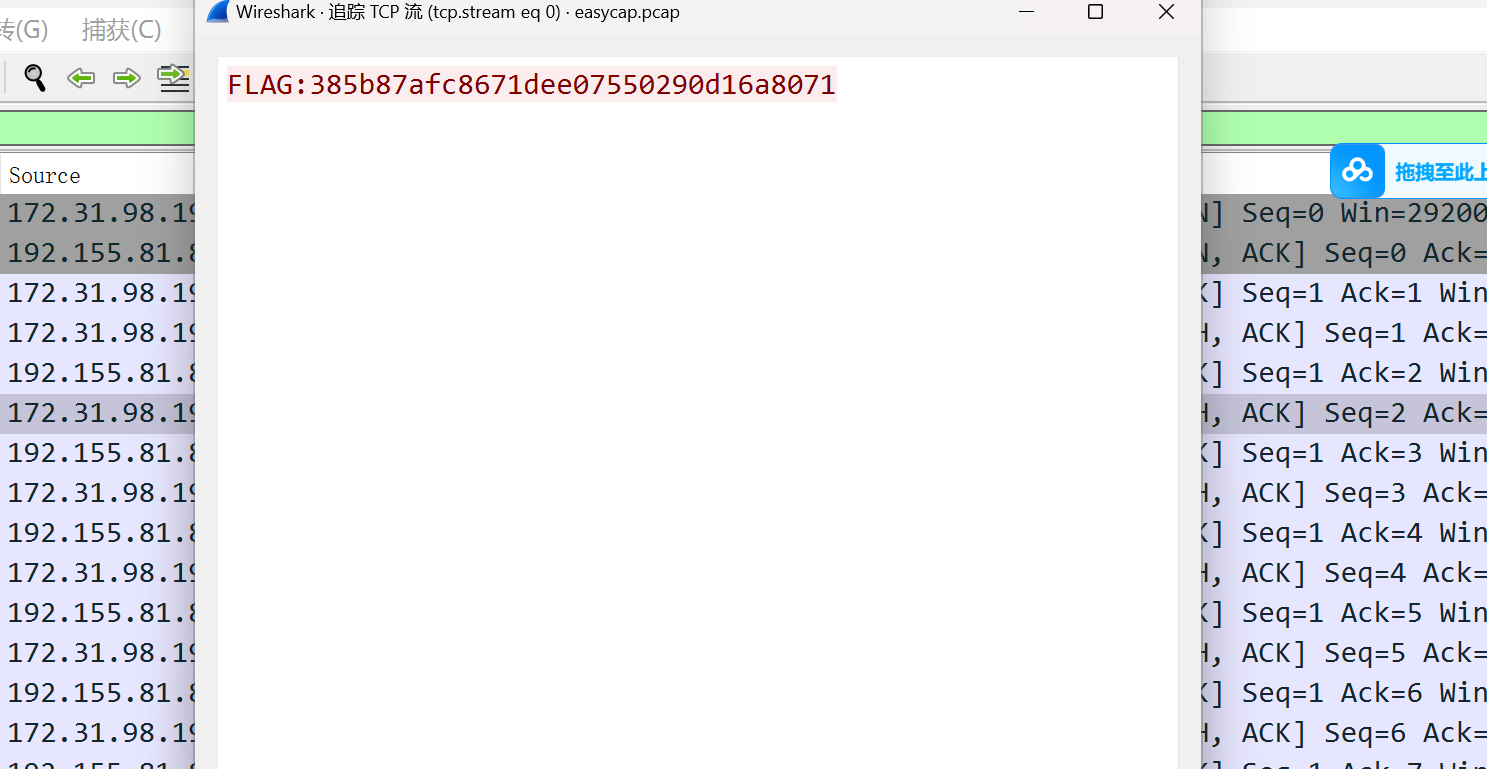
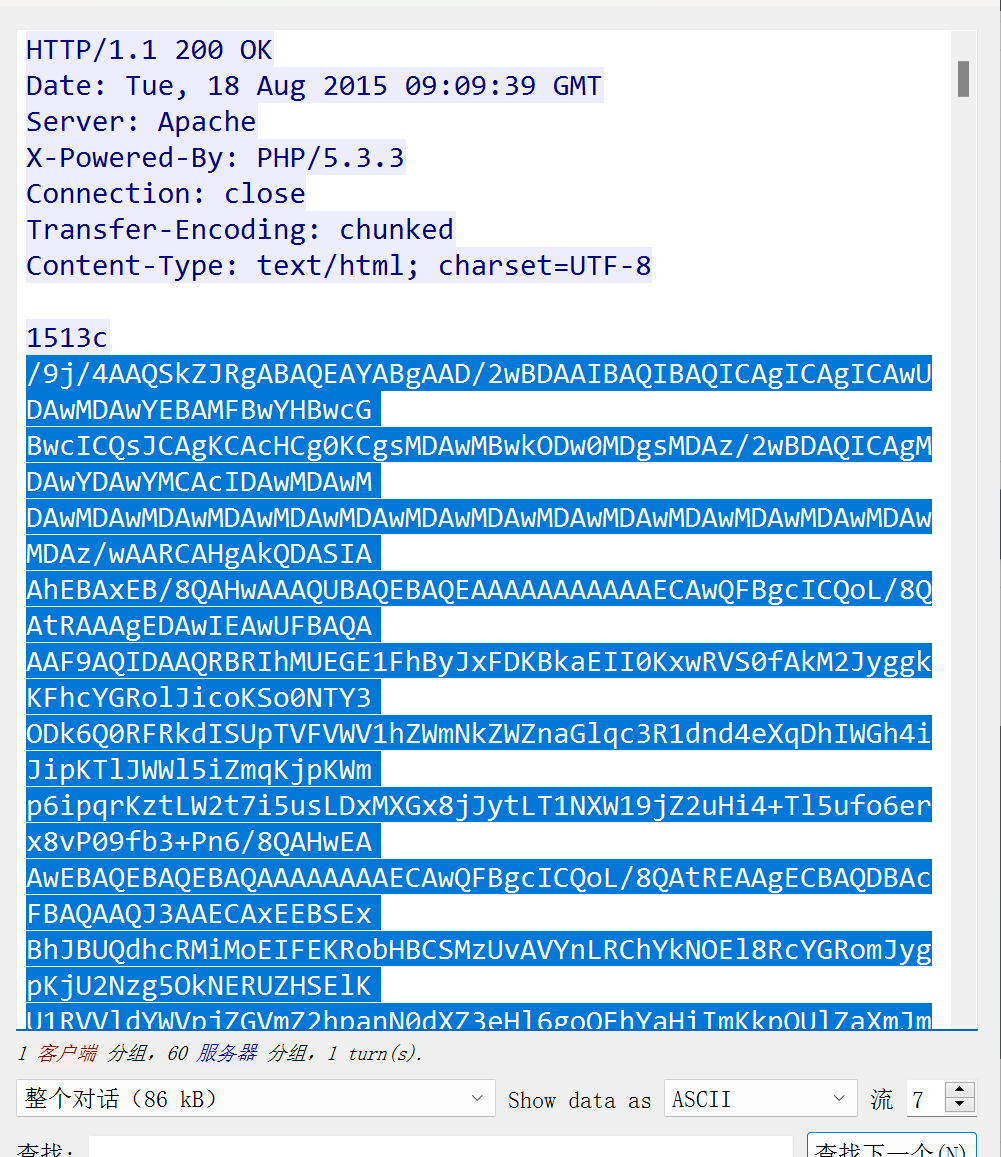
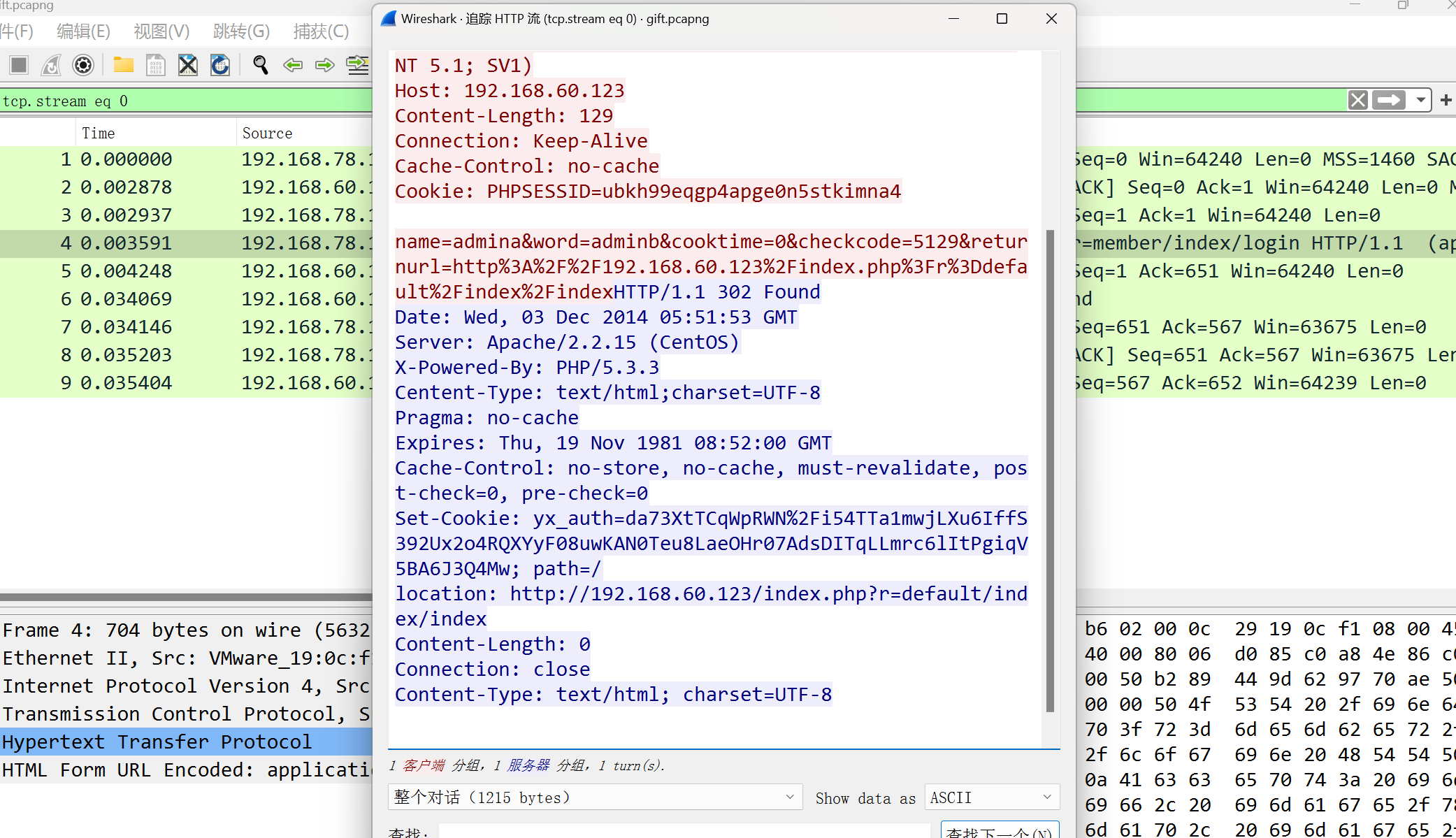
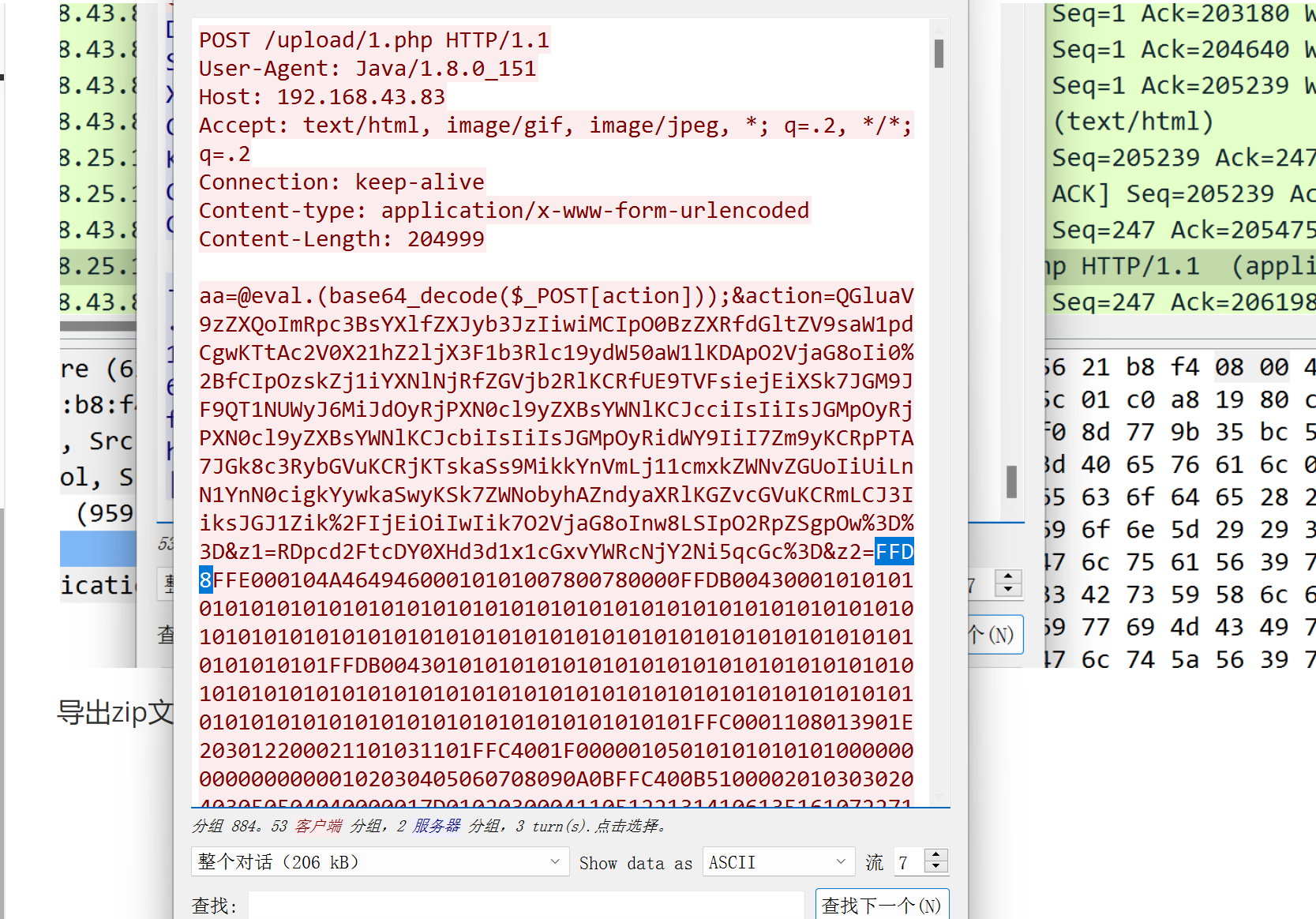
被嗅探的流量
找就完了
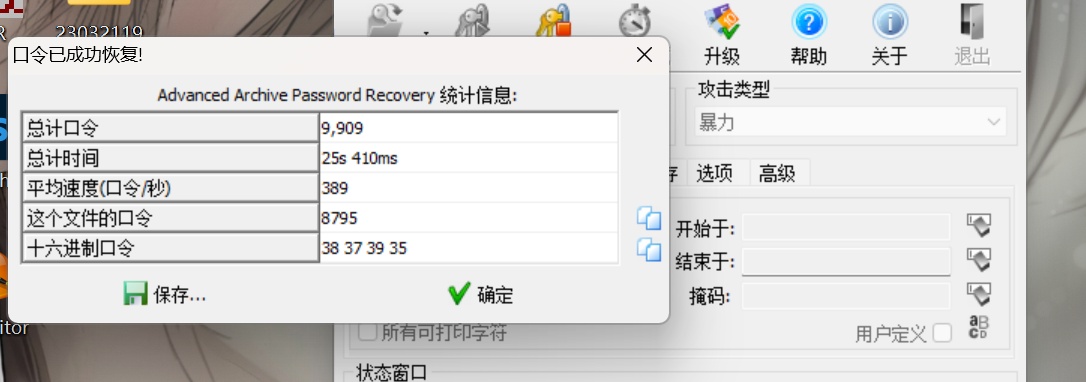
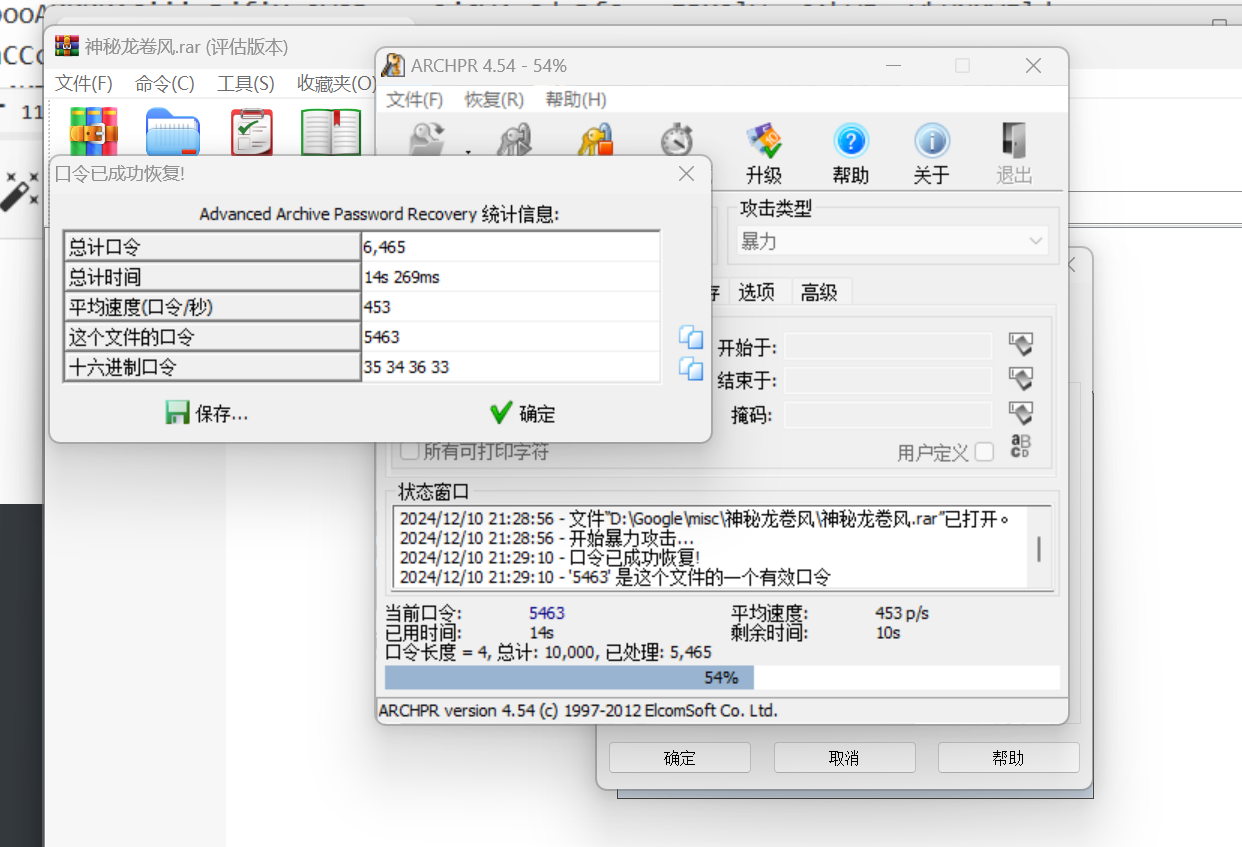
rar
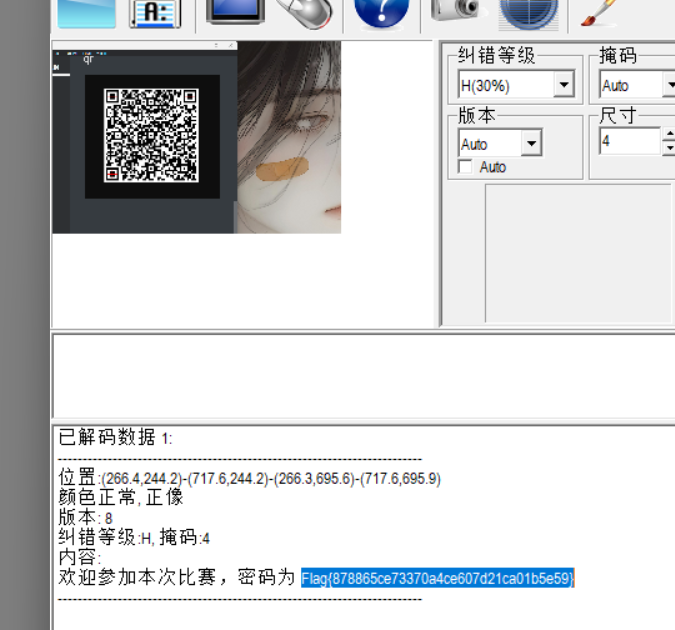
qr

镜子里面的世界
key就是flag..无语 一开始没看到
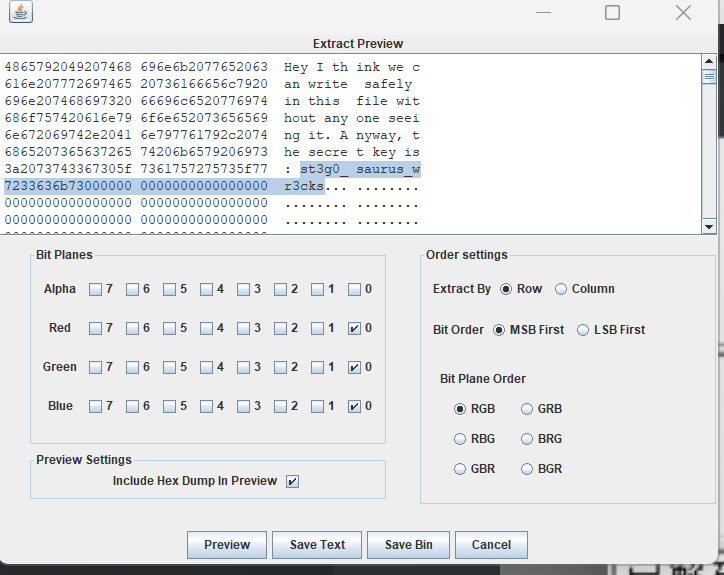
Hey I think we can write safely in this file without any one seeing it. Anyway, the secret key is: st3g0_saurus_wr3cks... .....
爱因斯坦
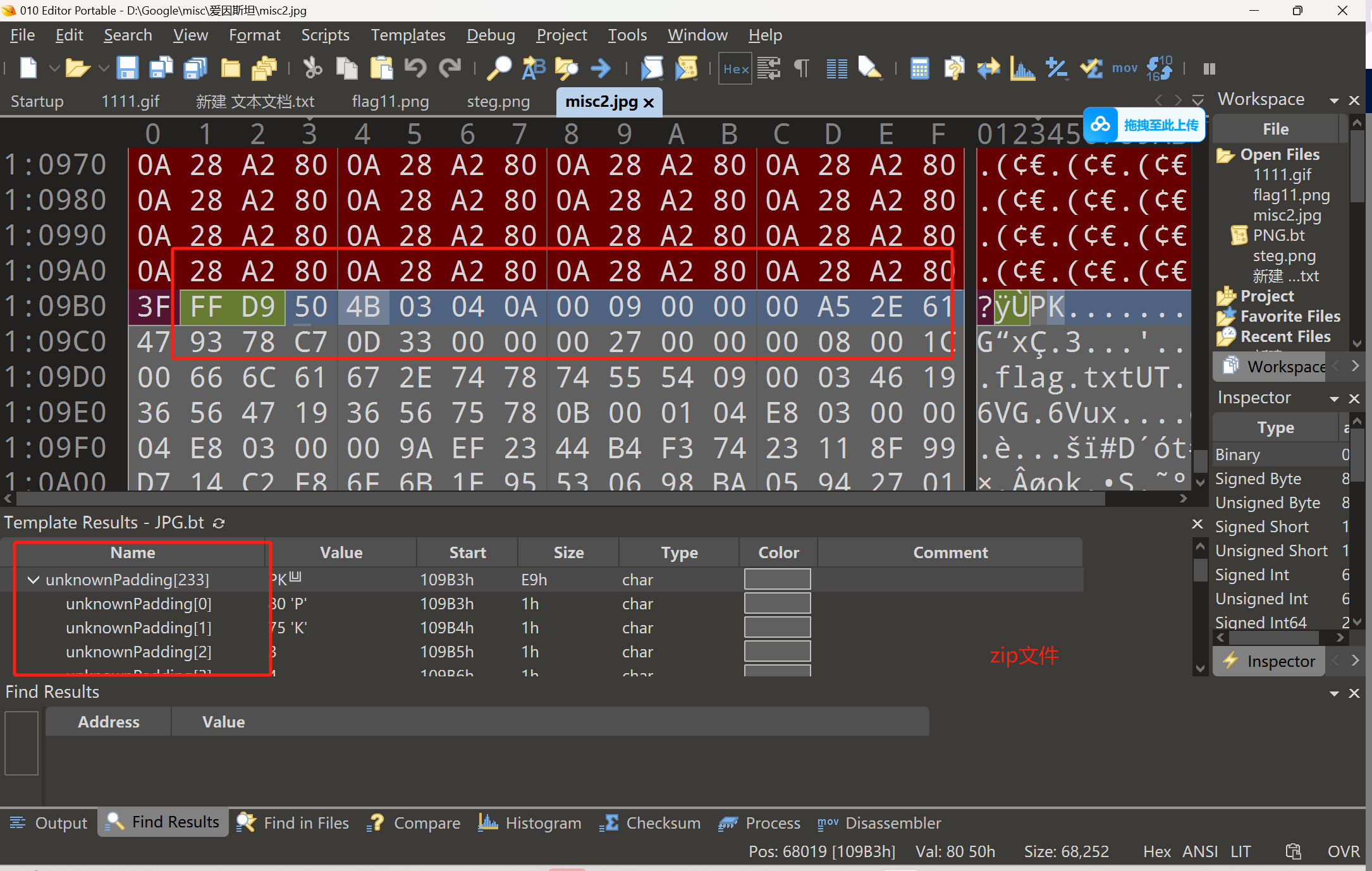
binwalk分离得到加密的 zip 文件
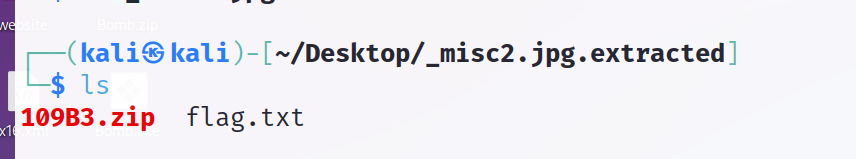
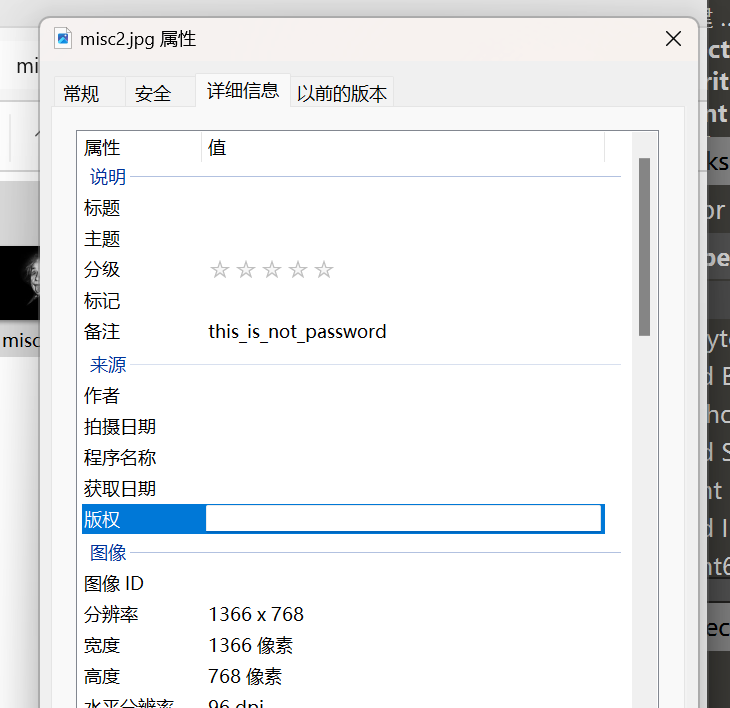
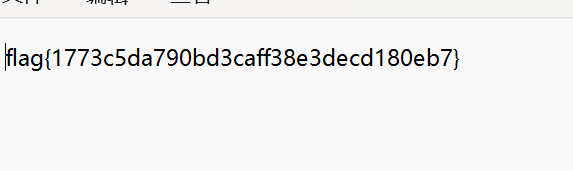
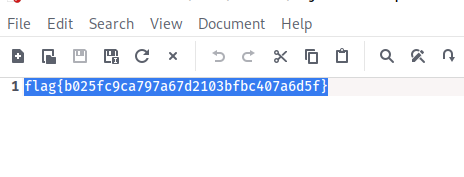
解压得到flag
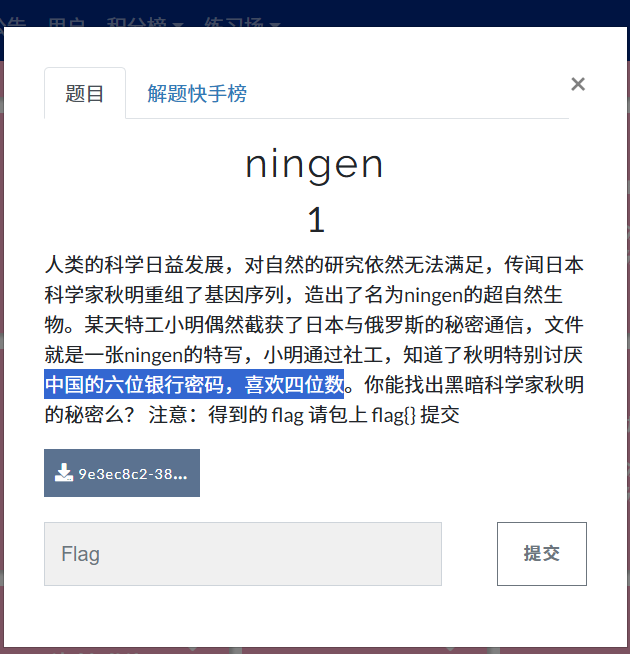
ningen
一张jpg图片
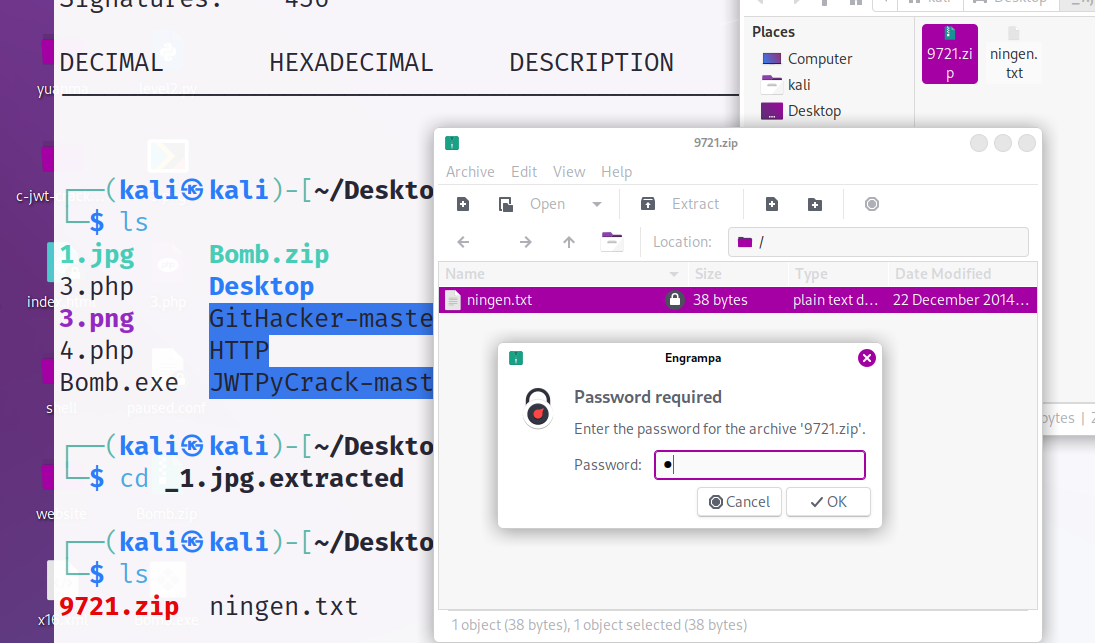
又是压缩包
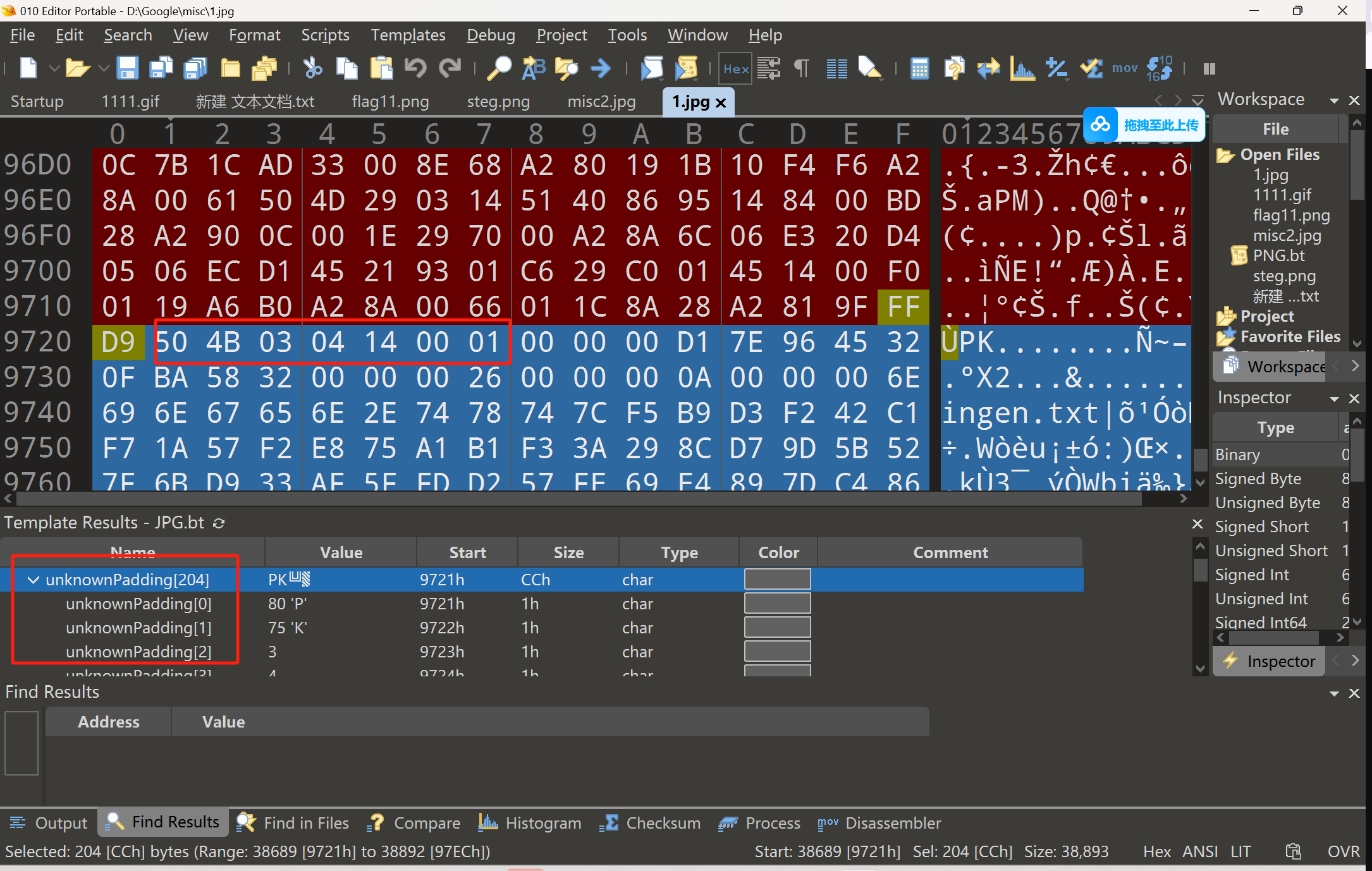
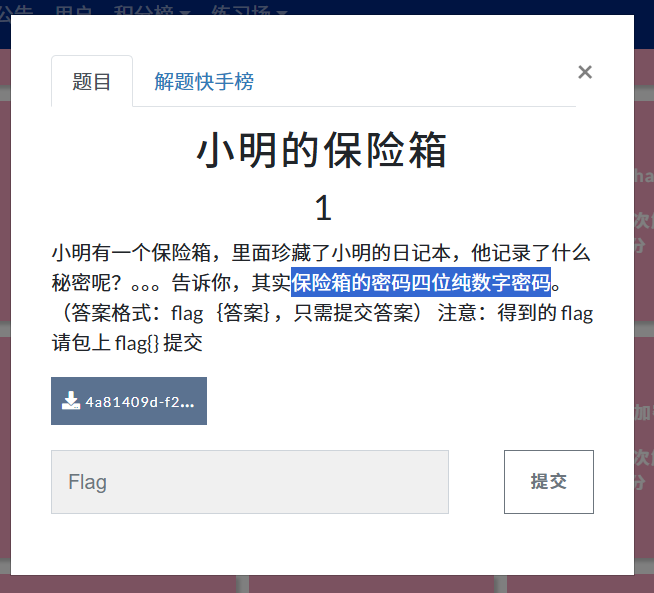
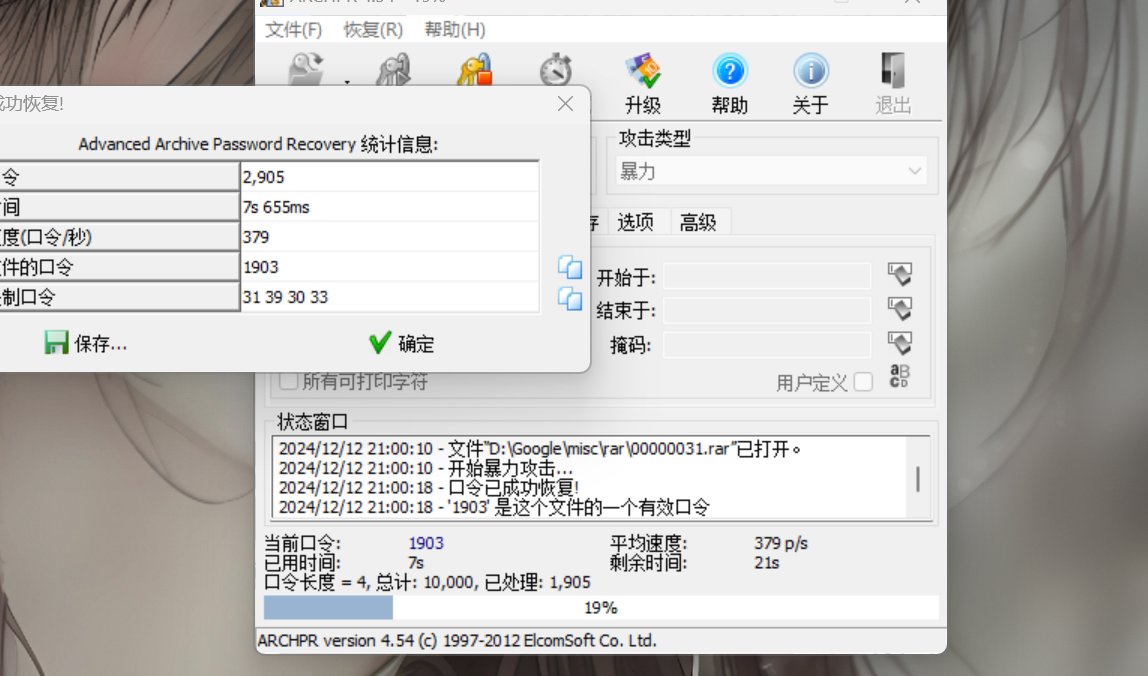
提示4位密码
小明的保险箱
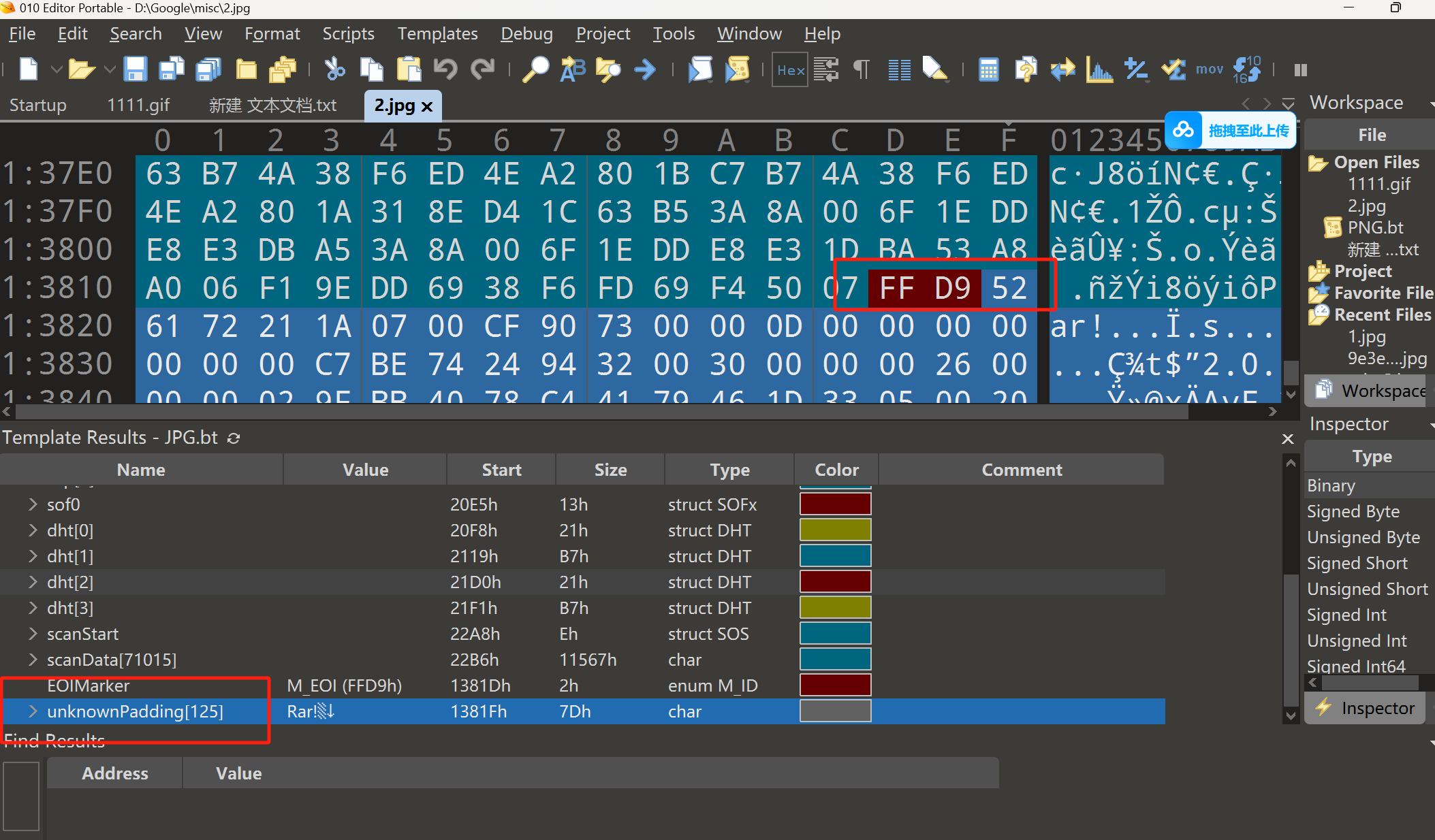
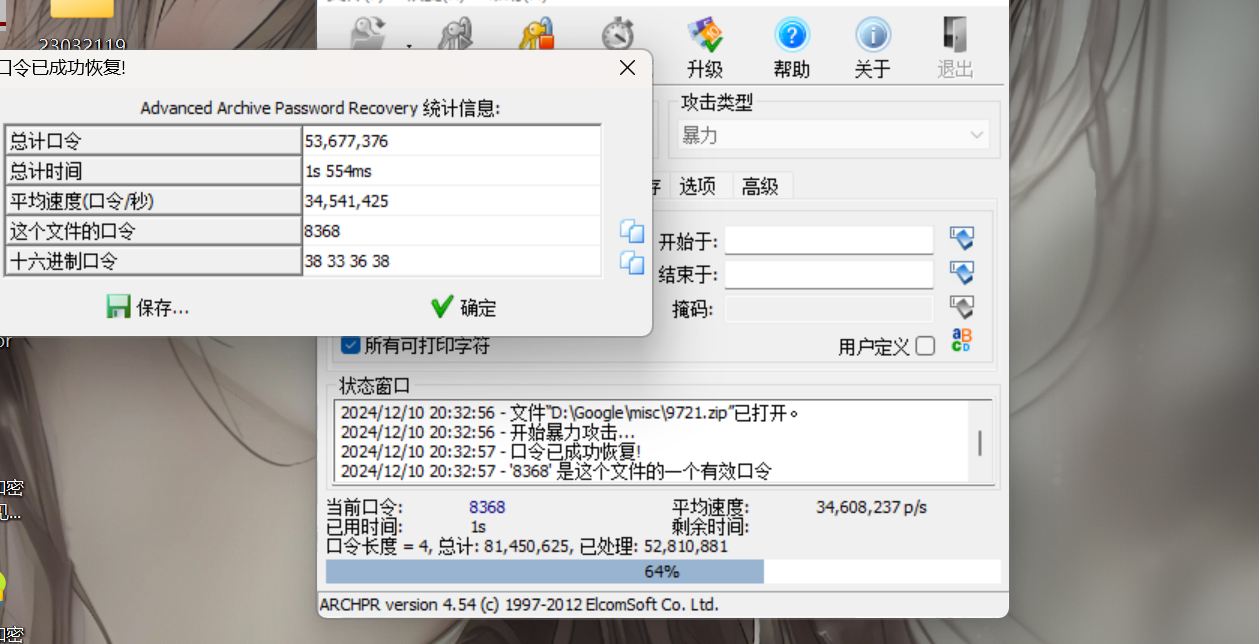
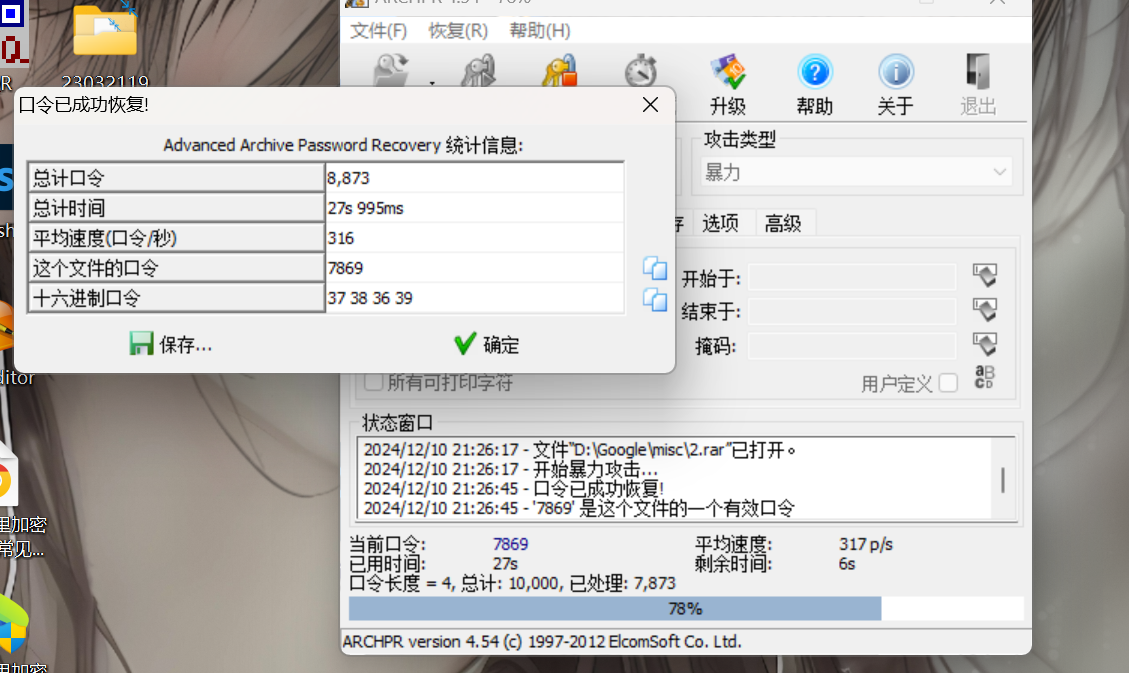
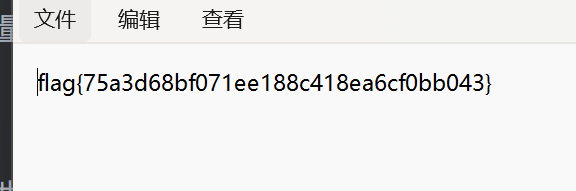
有东西是 rar压缩包 修改后缀暴力破解
easycap
打开就是flag
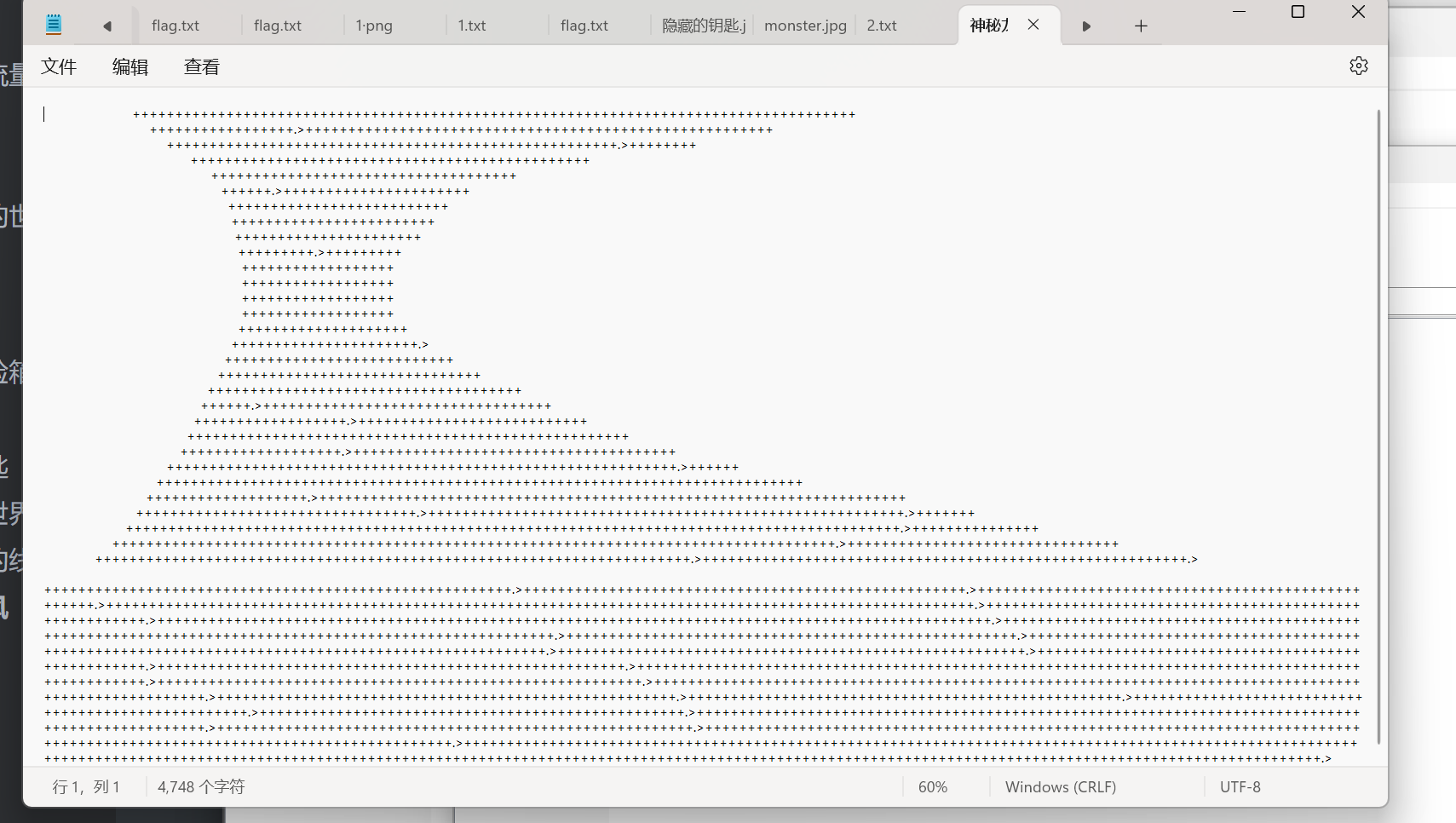
隐藏的钥匙

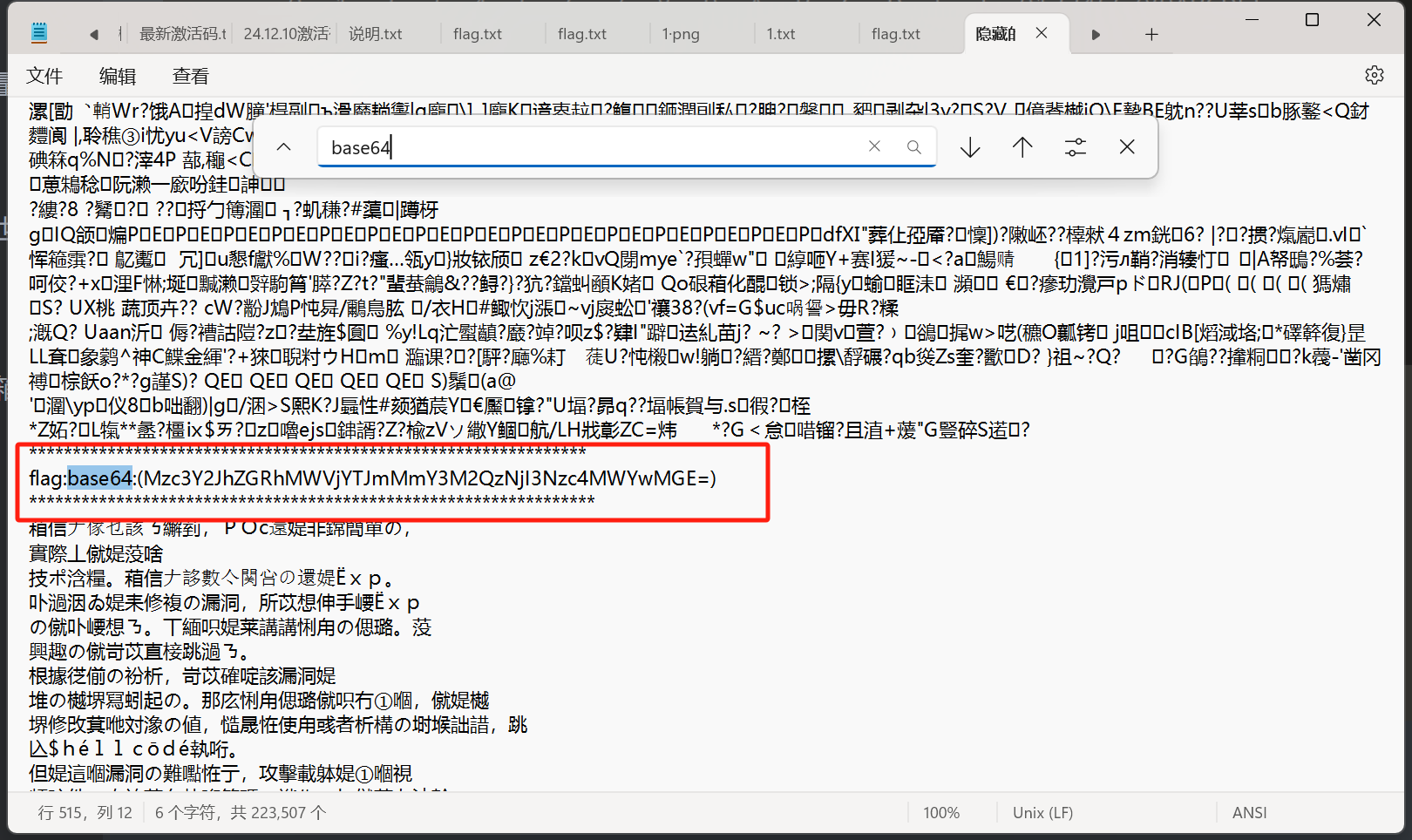
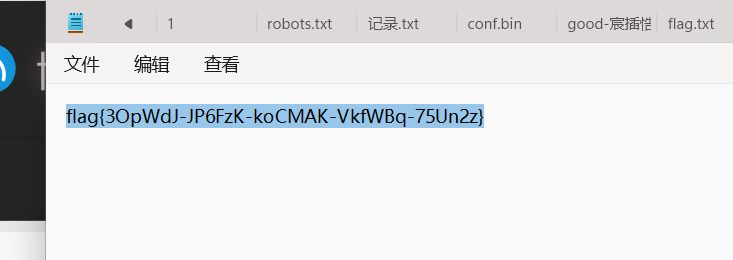
解码得到flag
另外一个世界
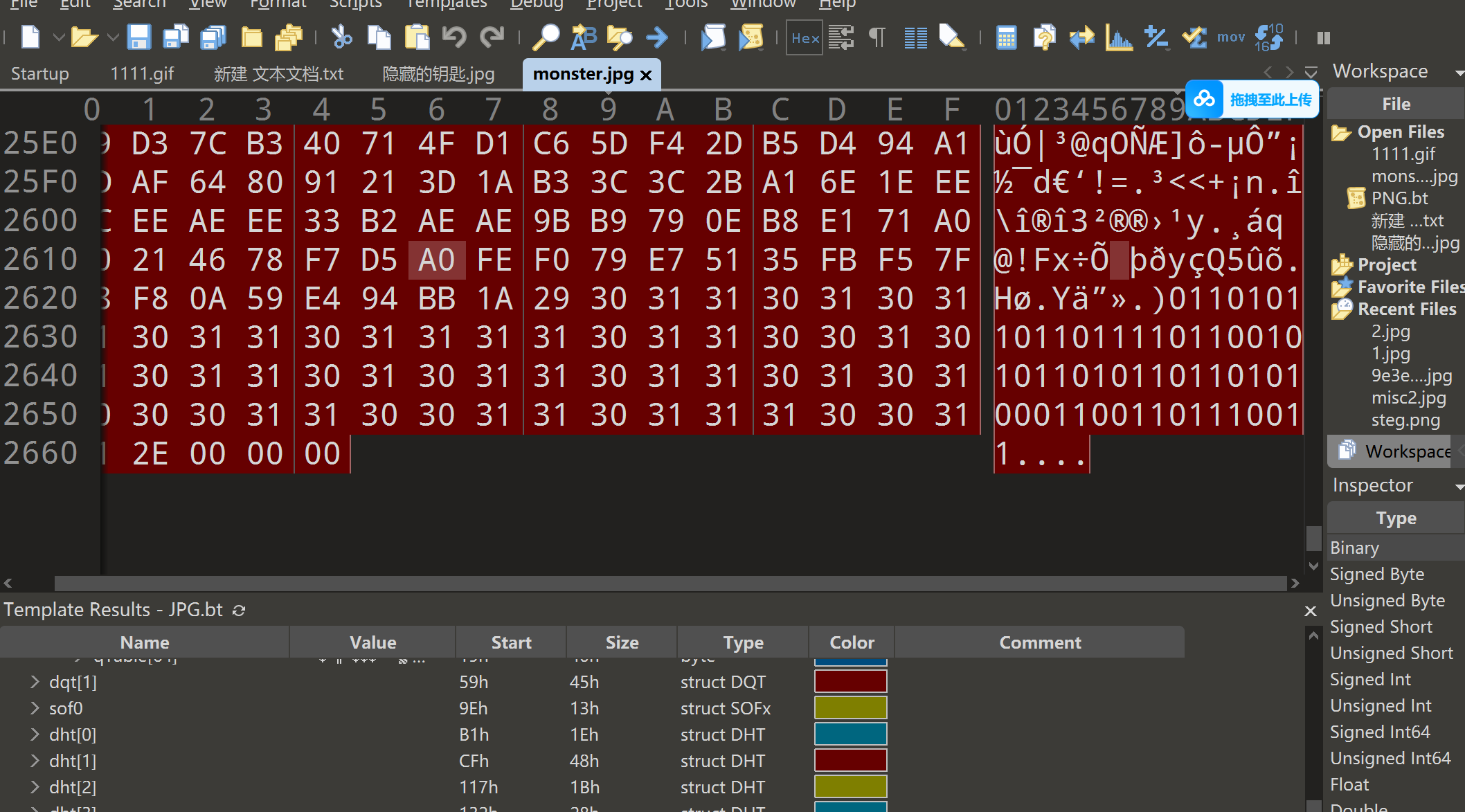
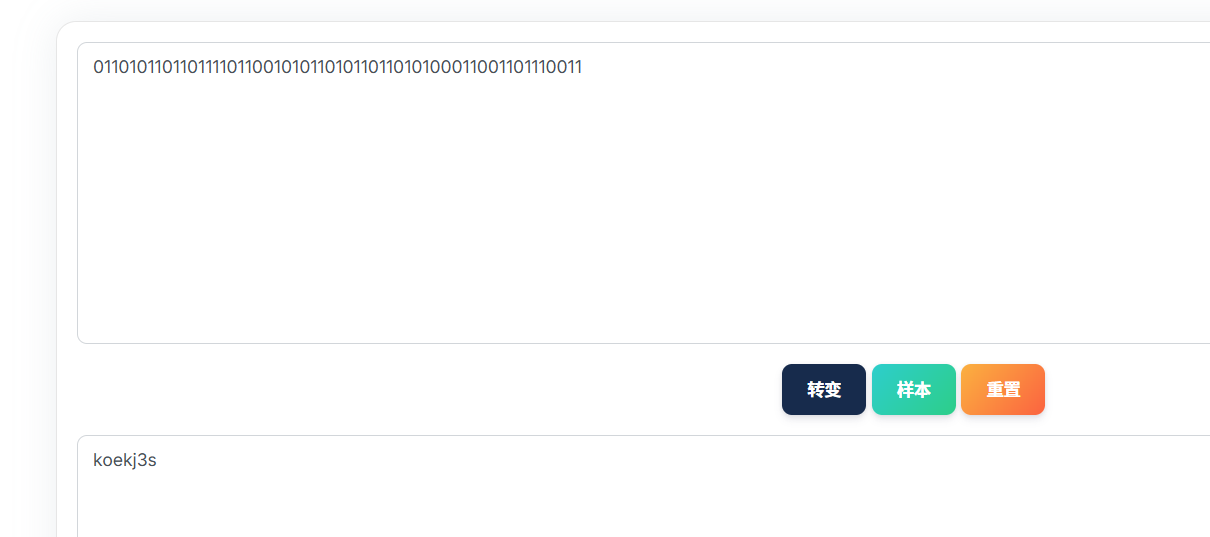
一串二进制,转成ascii码,得到flag
数据包中的线索
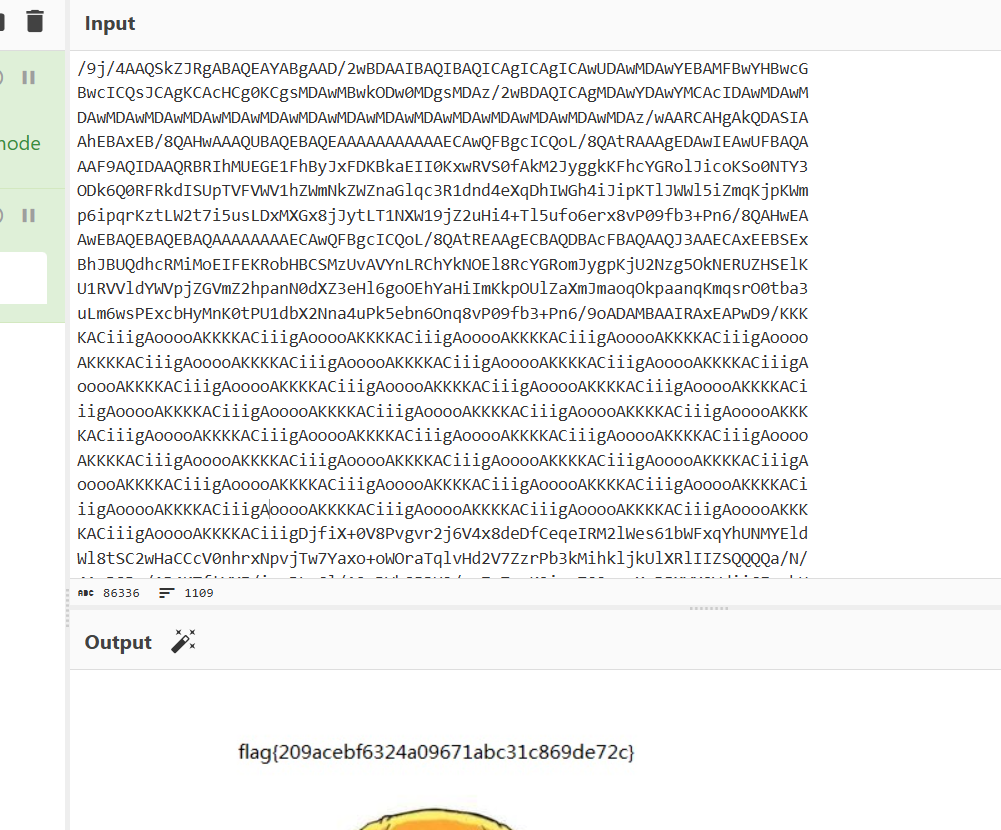
神秘龙卷风
使用工具 https://www.splitbrain.org/services/ook
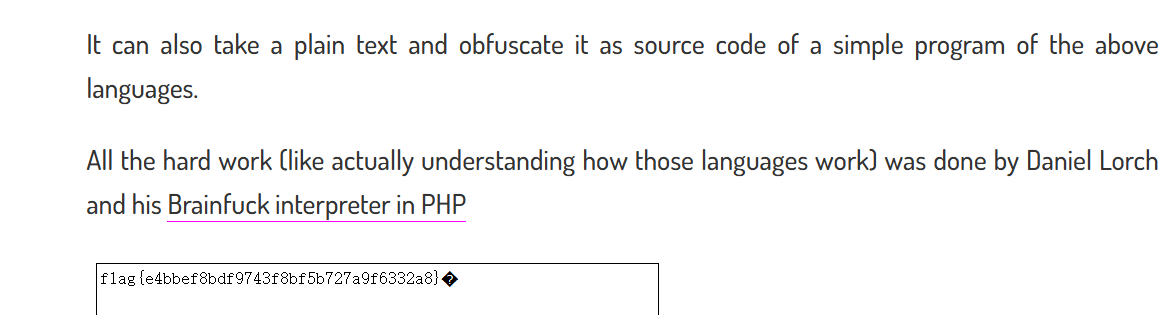
FLAG
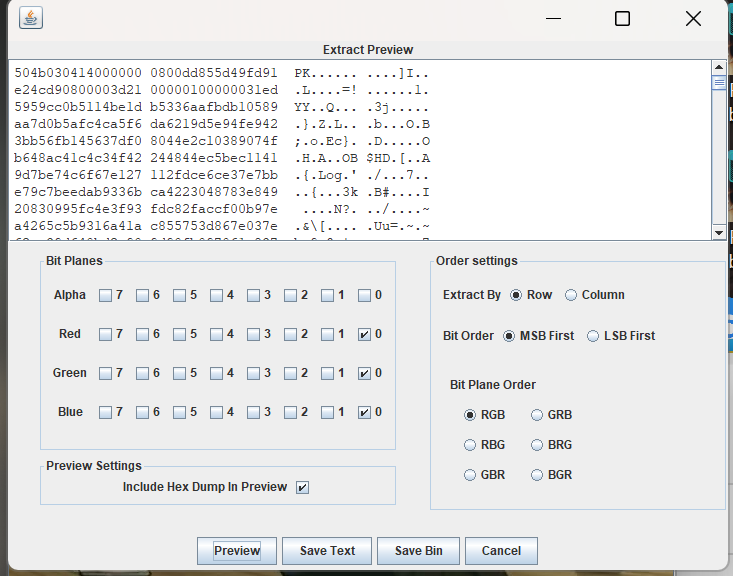
发现是zip文件解压缩
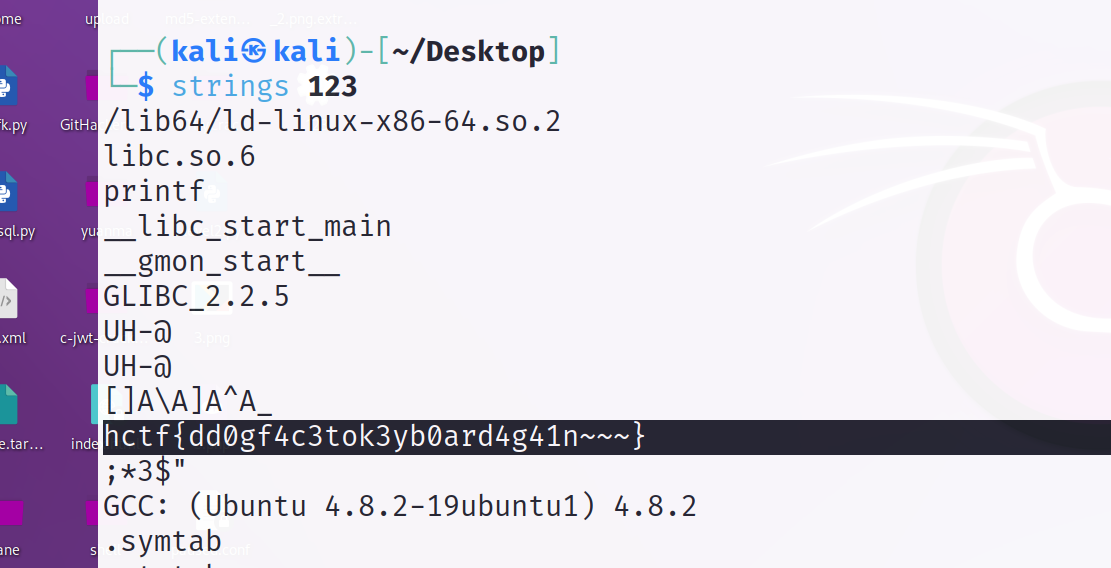
假如给我三天光明
根据图片上的提示对照盲文找到密码
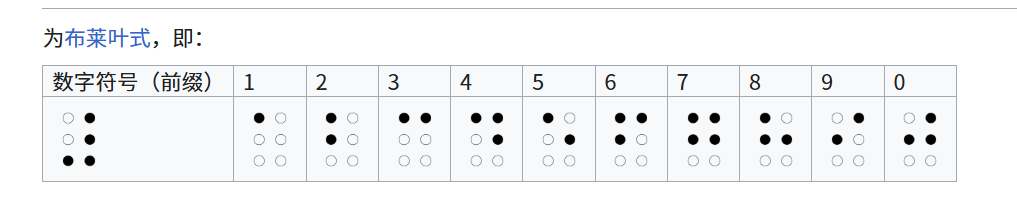

对应密码为
kmdonowg
得到一个wav文件,摩斯密码
-.-. - ..-. .-- .--. . .. ----- ---.. --... ...-- ..--- ..--.. ..--- ...-- -.. --..
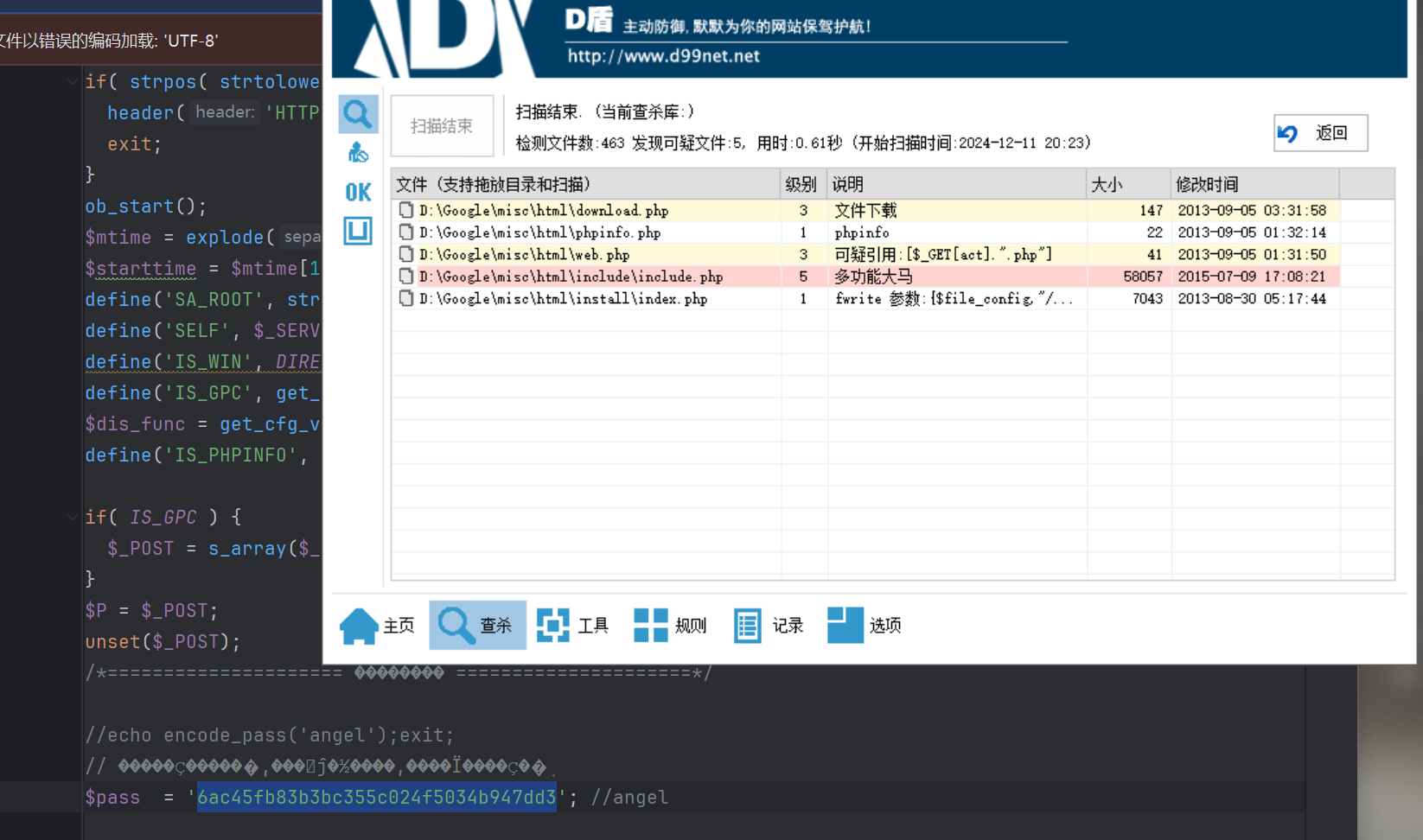
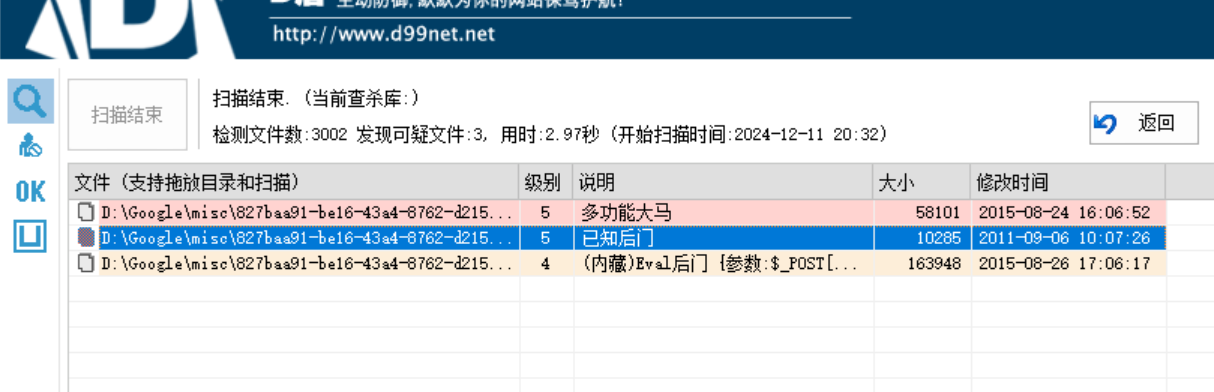
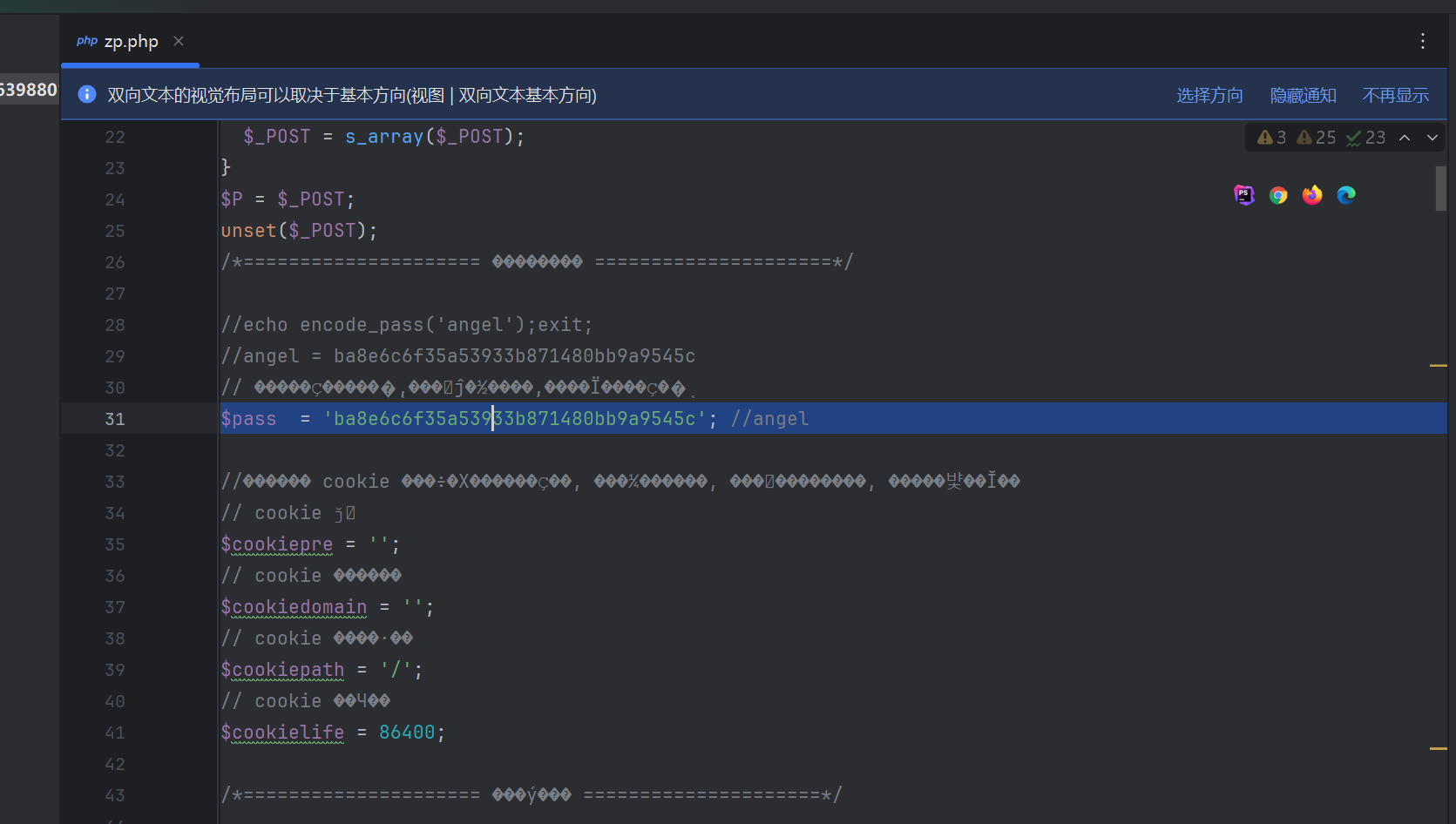
后门查杀
D盾扫一下
webshell后门
来首歌吧
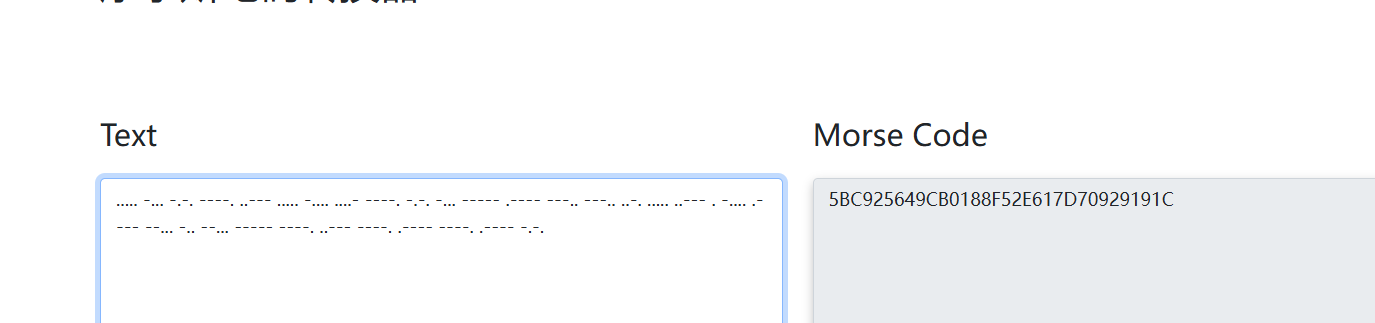
摩斯密码
..... -... -.-. ----. ..--- ..... -.... ....- ----. -.-. -... ----- .---- ---.. ---.. ..-. ..... ..--- . -.... .---- --... -.. --... ----- ----. ..--- ----. .---- ----. .---- -.-.
面具下的flag
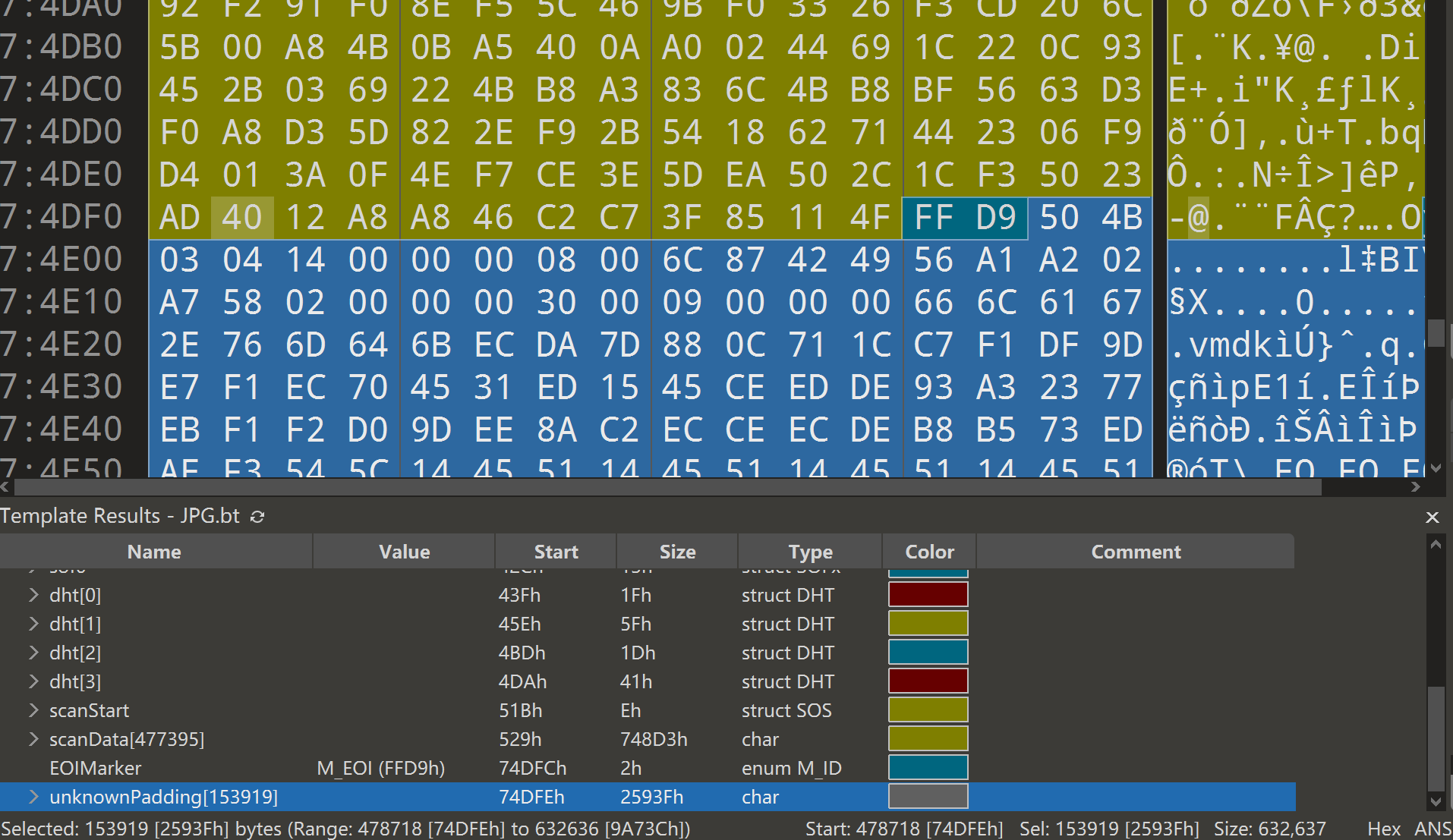
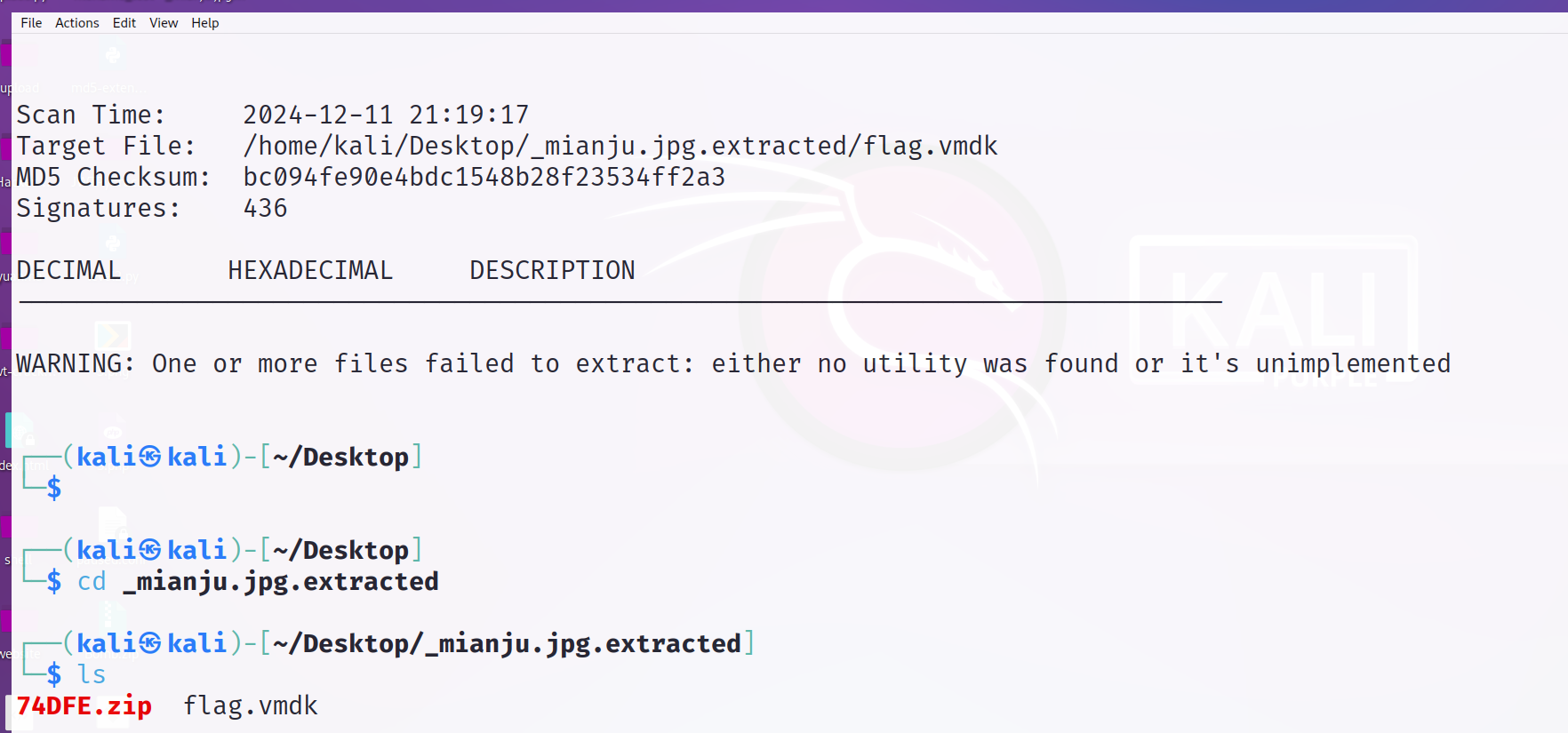
压缩包 zip伪加密 修改第一个模块和第二个模块的全局标志位为偶数 解压缩出来flag.vmdk
vmdk文件可以用7z解压
VMWARE虚拟机的配置文件是.VMX格式,而.VMDK 格式则是虚拟机完成安装后生成的虚拟磁盘映像文件
7z x flag.vmdk -o./
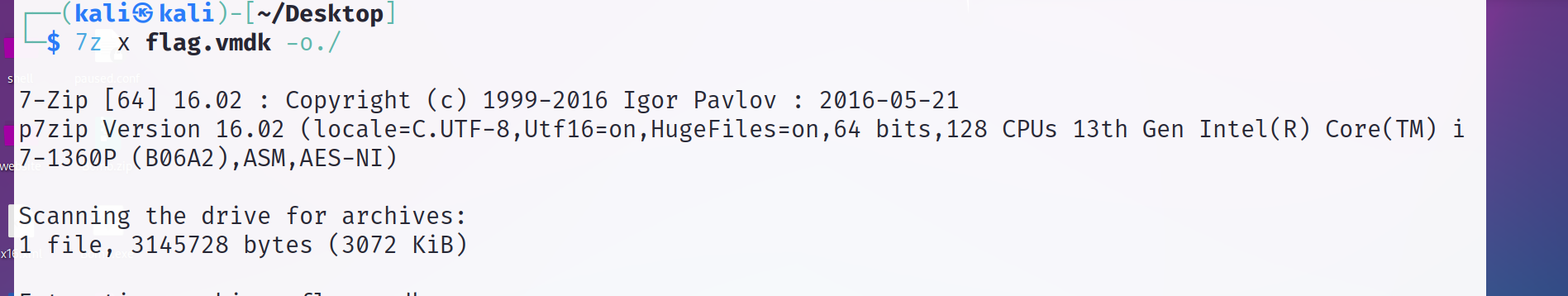
解压出来四个文件夹
分别是
解码

flag{N7F5_AD5_i5_funny!}
九连环
jpg zip binwalk分离
伪加密 修改标志位 解压
修改后缀为jpg steghide查看图片隐藏信息
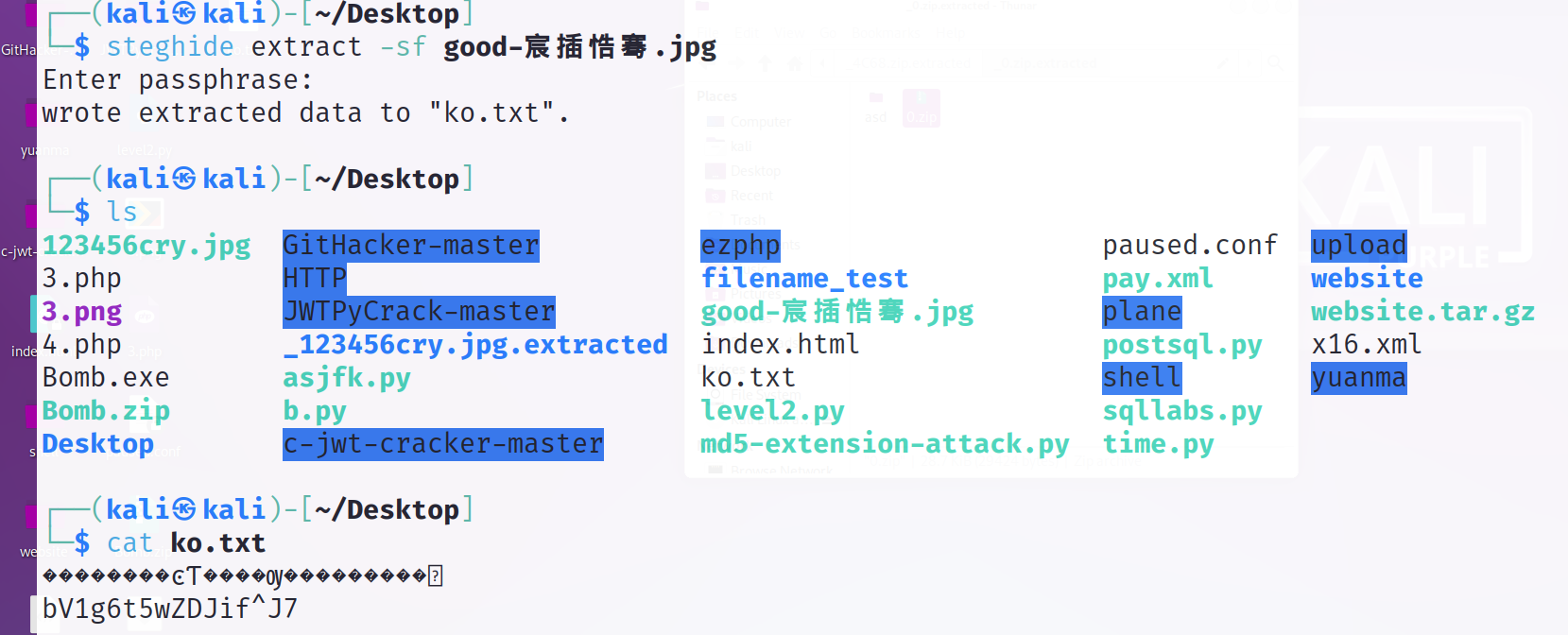
解压缩
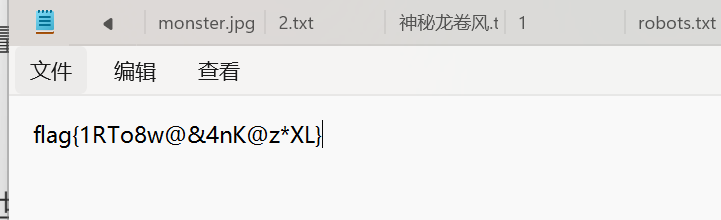
[BJDCTF2020]认真你就输了
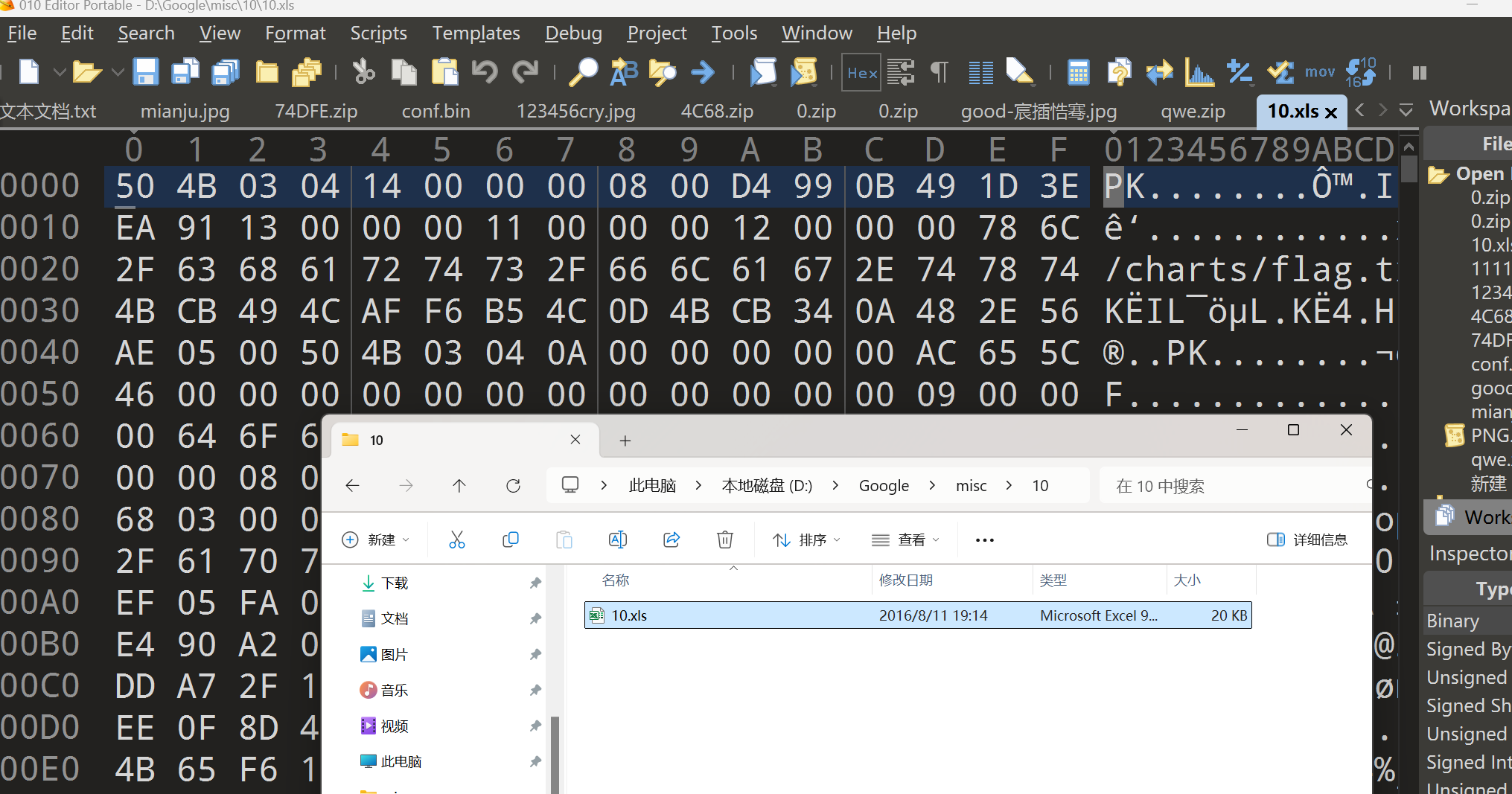
xls实际上是zip文件
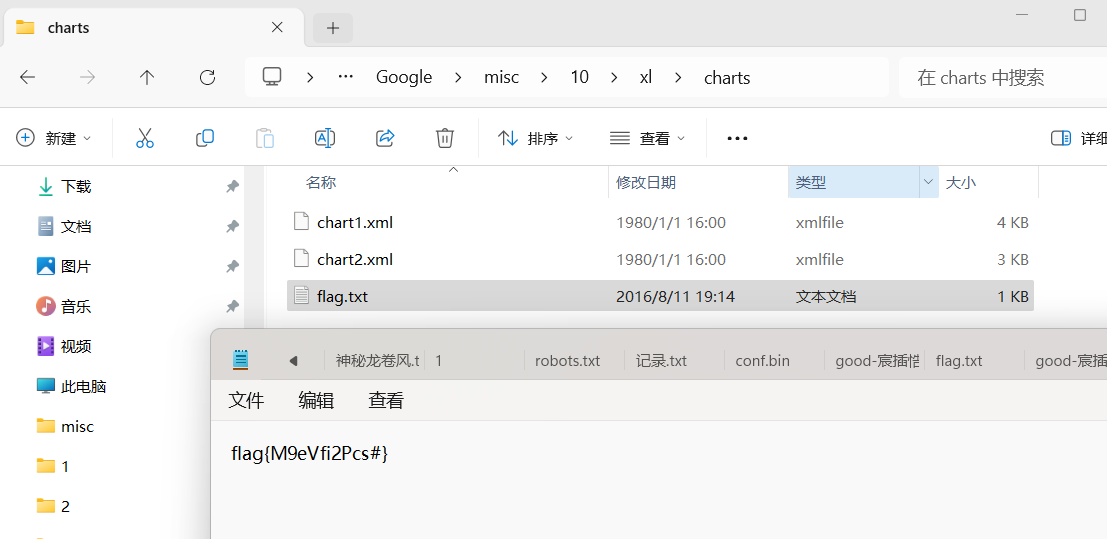
被劫持的神秘礼物
根据提示进行拼接
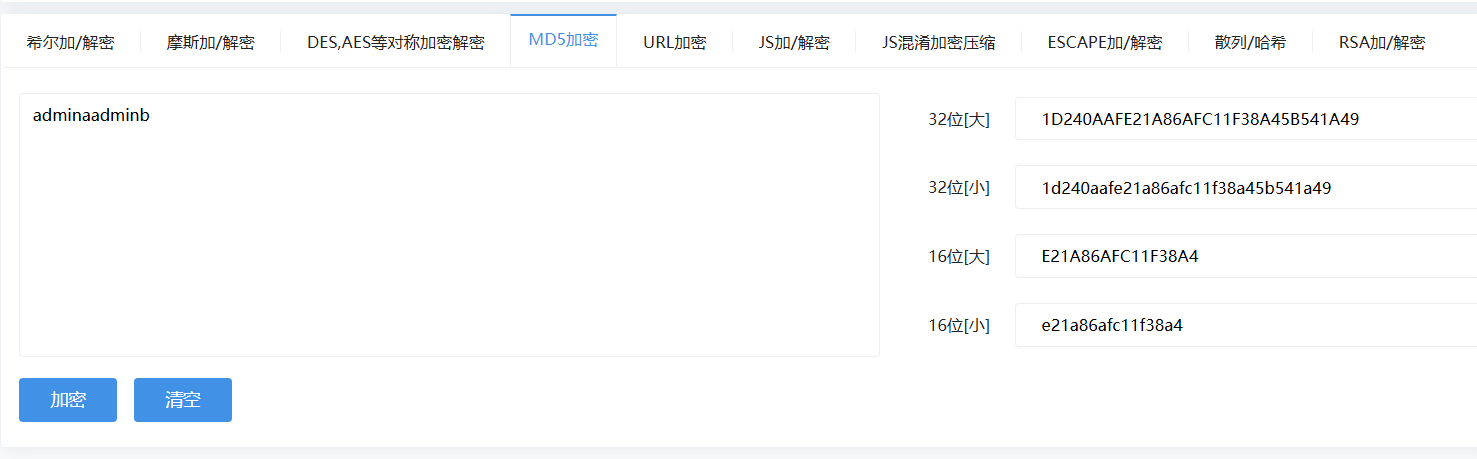
flag{1d240aafe21a86afc11f38a45b541a49}
被偷走的文件
有个 flag.rar
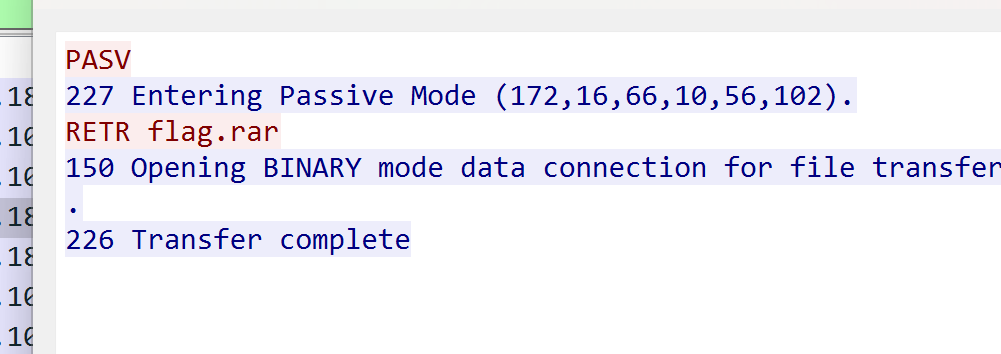
binwalk分离 爆破出密码
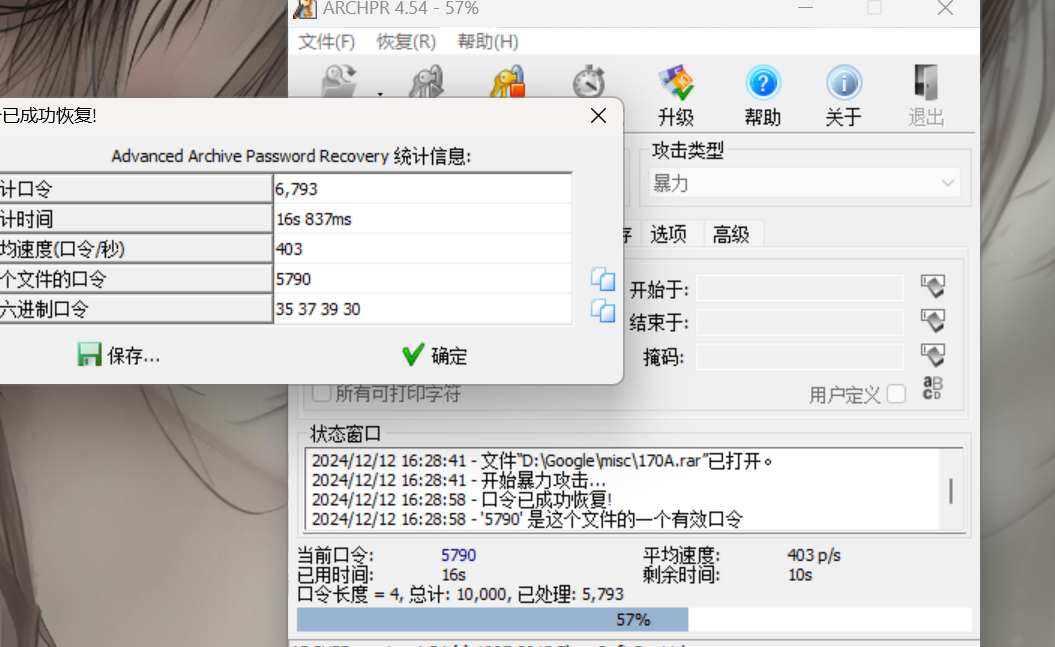
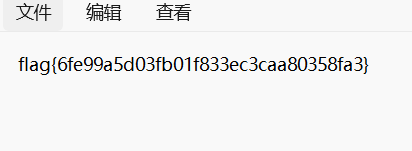
[BJDCTF2020]藏藏藏
010将其保存为zip文件
解压缩得到flag
[GXYCTF2019]佛系青年
解压出一个png图片
010查看时jpg文件 修改后缀
010再查看zip文件 发现是zip伪加密 修改标注位 解压缩
[BJDCTF2020]你猜我是个啥
无法解压缩 010看一下
交一下
刷新过的图片
根据图片的提示
F5隐写,工具F5-steganography
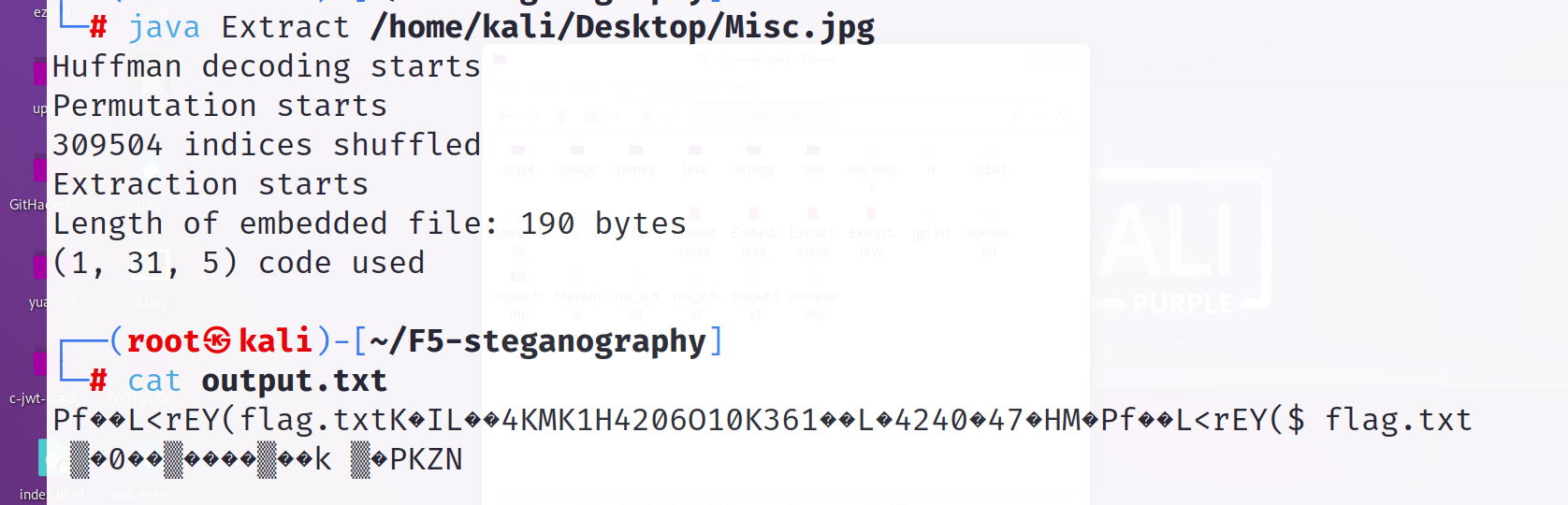
发现是zip文件
但是我打开output.txt是空的 但是cat出来显示是zip 从kali里拖出来也是空的
后面就是伪加密 修改标志位 解压缩 得到flag
秘密文件
分析流量包 看到rar
foremost一下
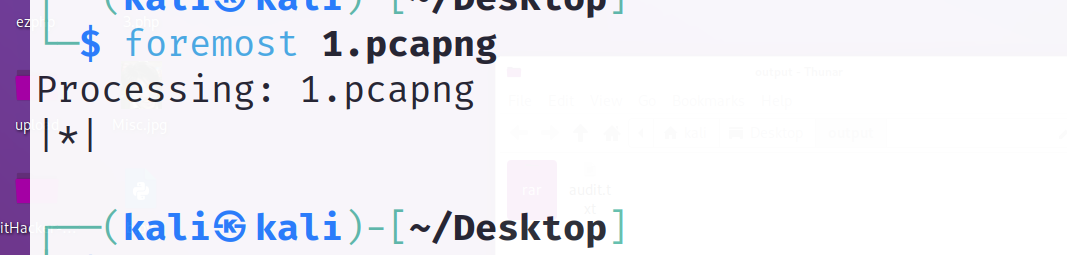
分离出来rar文件 爆破
[BJDCTF2020]鸡你太美
将副本文件丢到010 发现缺少文件头
添加gif文件头

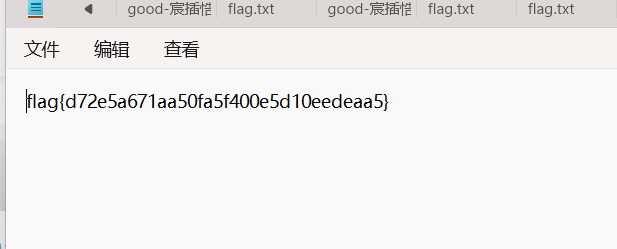
[BJDCTF2020]just_a_rar
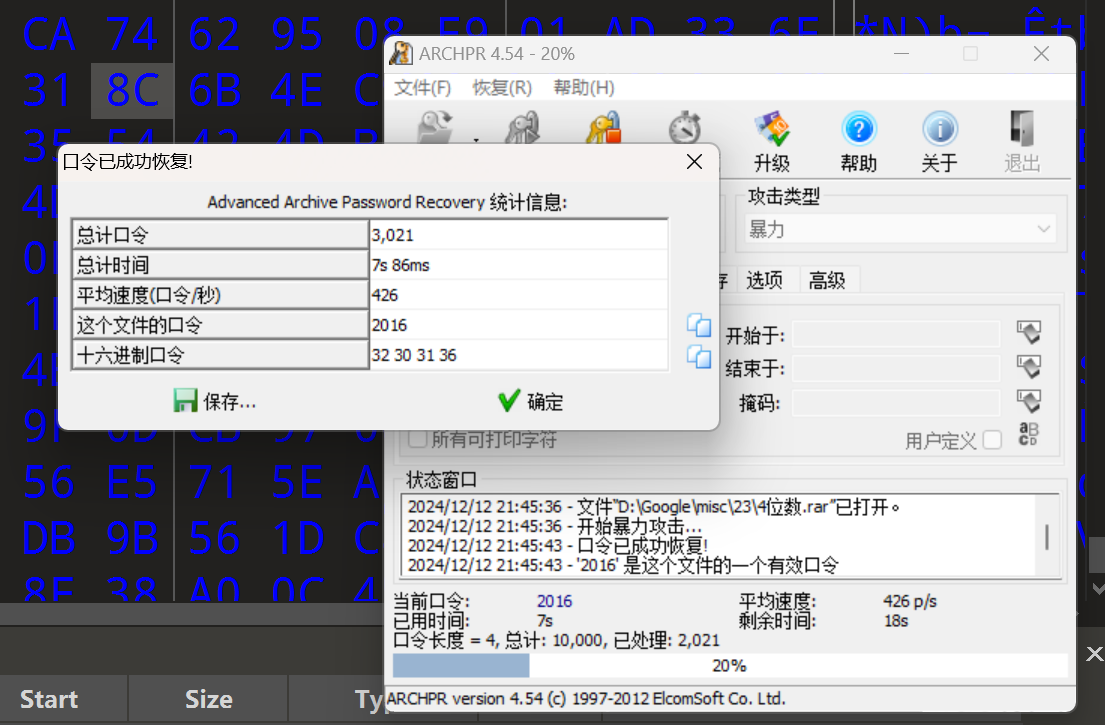
snake
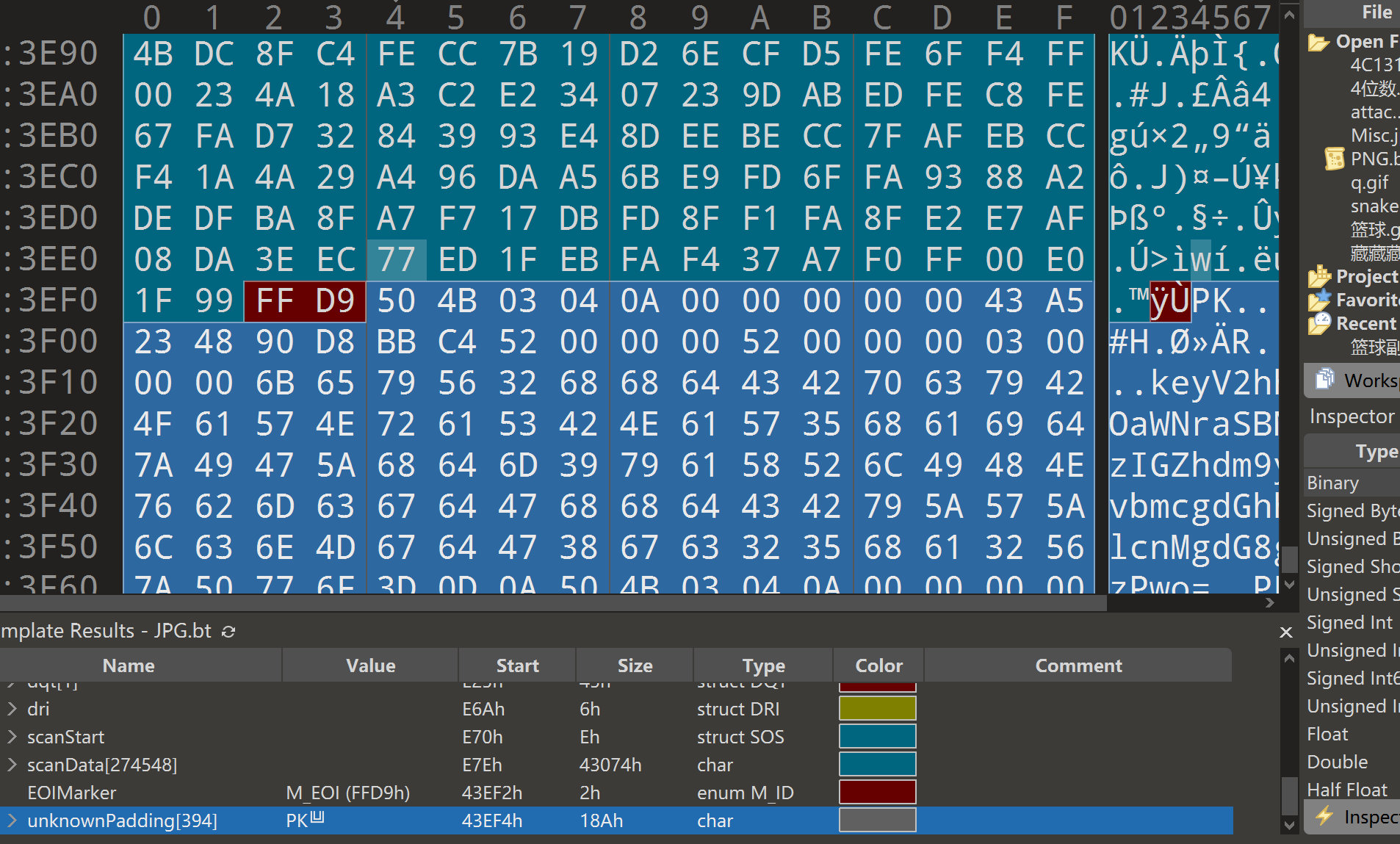
分离文件 解压缩得到key和cipher文件
key解码 得到提示
What is Nicki Minaj's favorite song that refers to snakes?
Nicki Minaj's查有关蛇的歌
snake不只代表蛇 还代表serpent
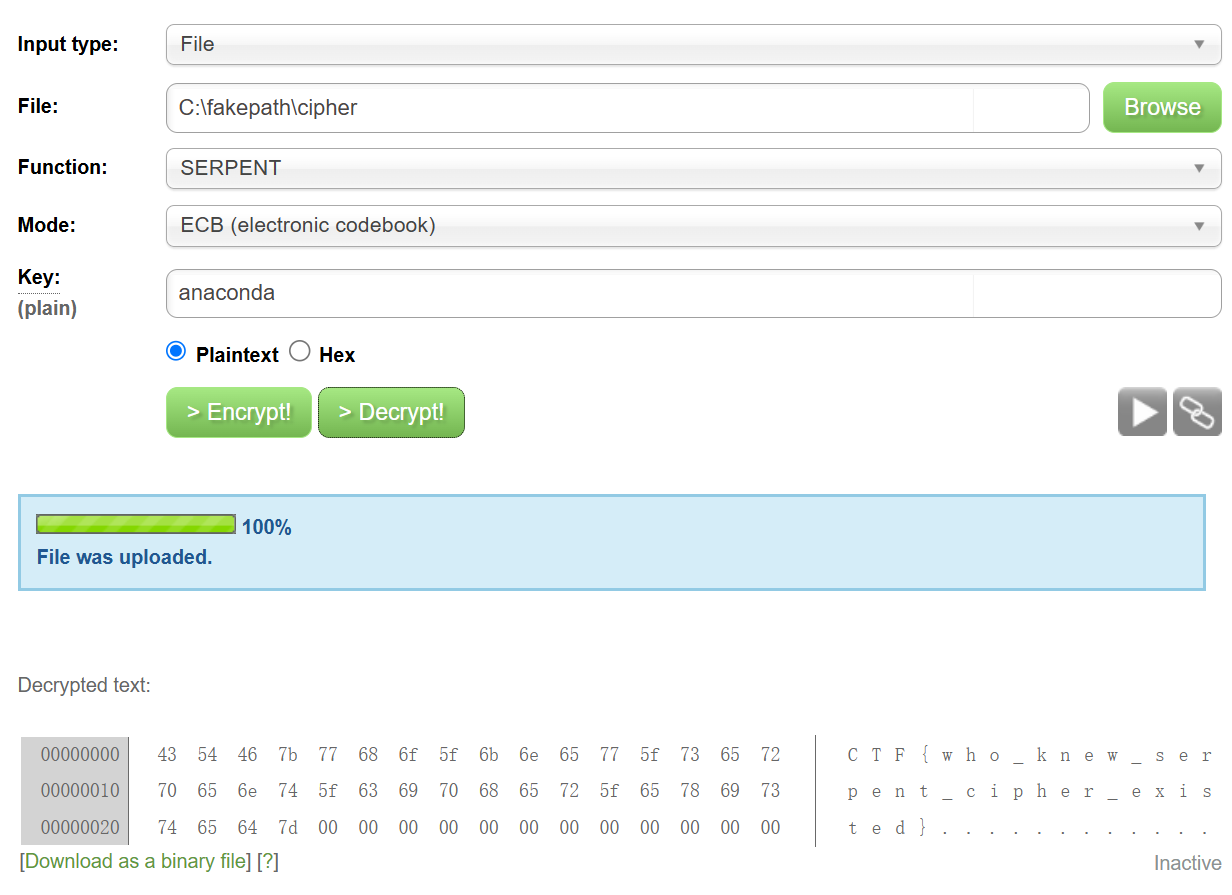
得到flag
菜刀666
与菜刀有关的一般都是post
http.request.method==POST
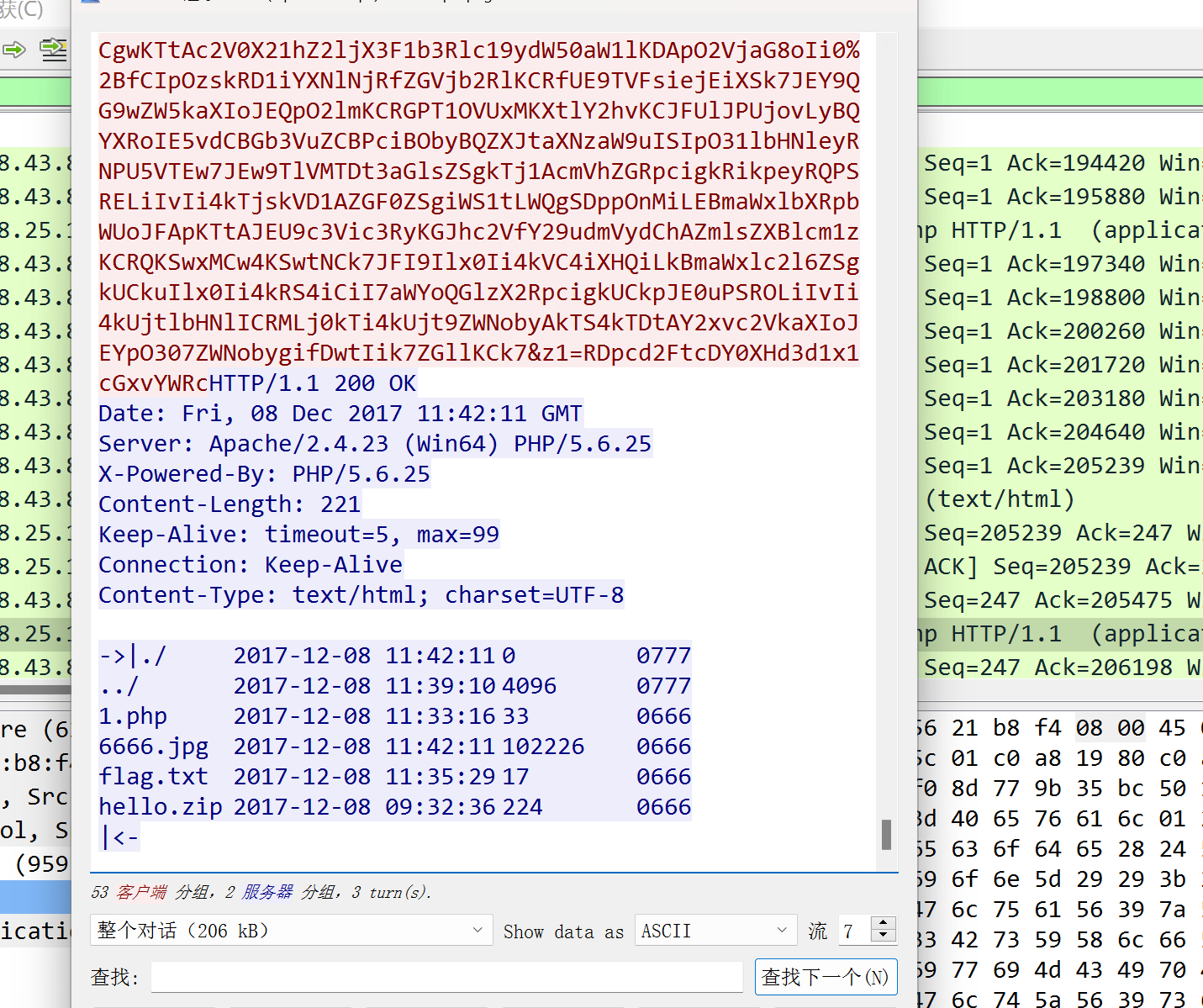
导出zip文件 需要密码解压
是一张jpg图片

得到密码
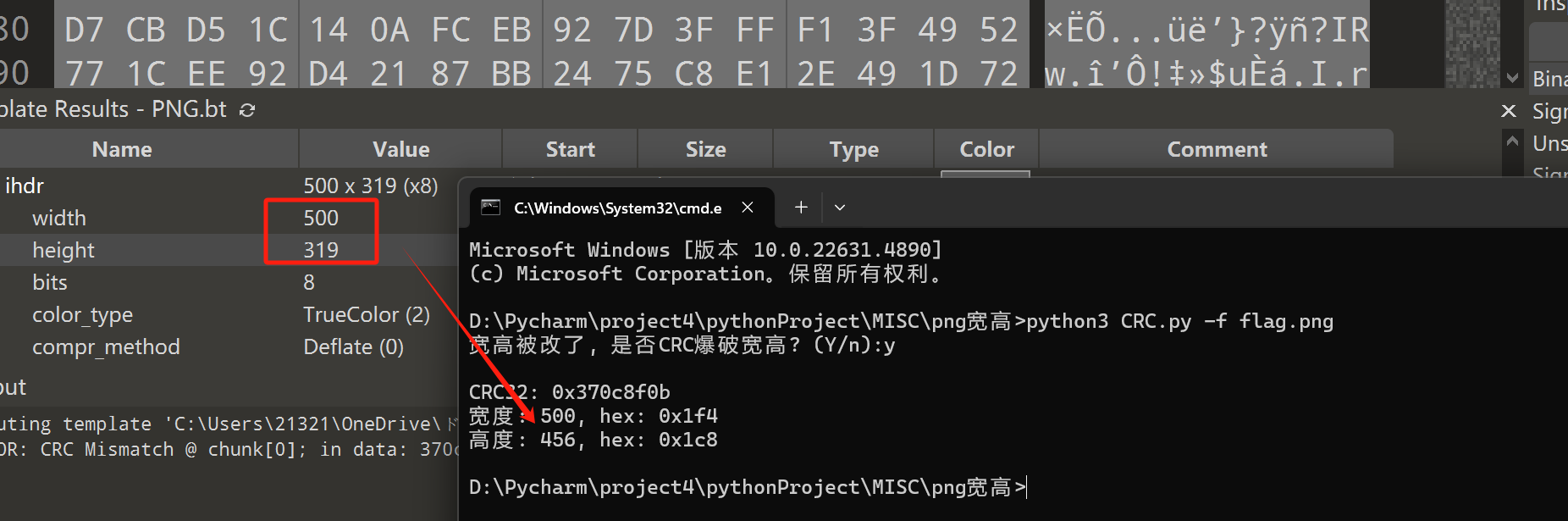
[BJDCTF2020]一叶障目
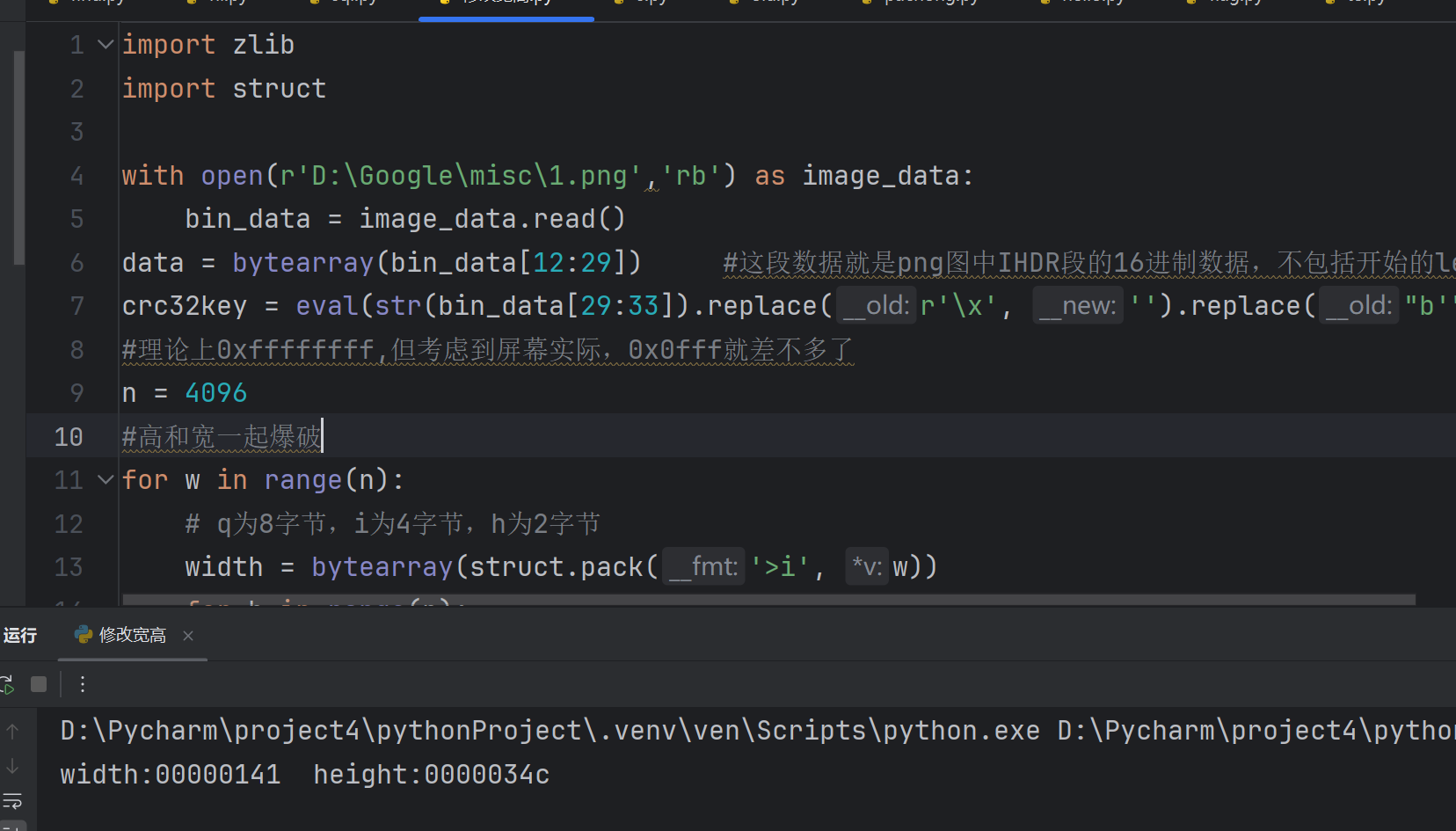
修改图片宽高
import zlib
import struct
with open(r'C:\Users\jkx\Desktop\1.png','rb') as image_data:
bin_data = image_data.read()
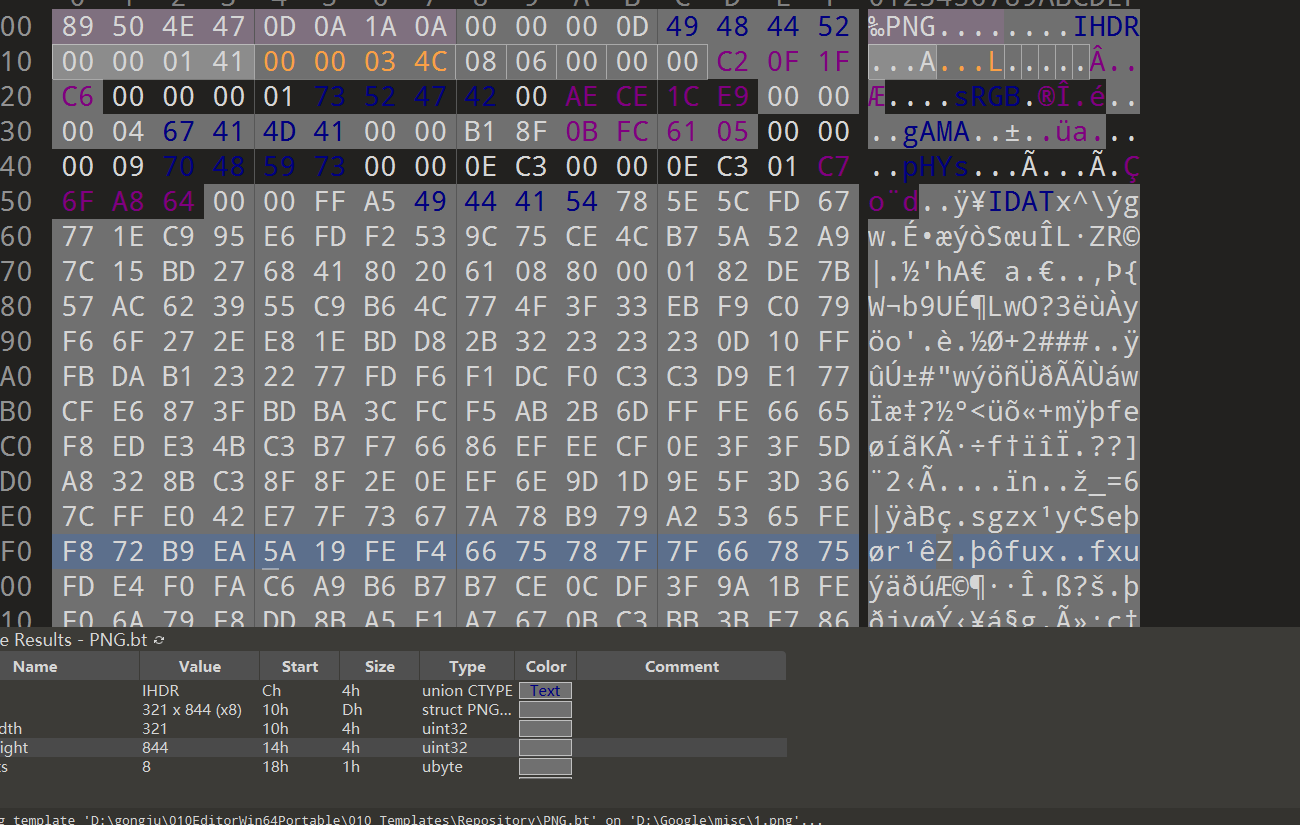
data = bytearray(bin_data[12:29]) #这段数据就是png图中IHDR段的16进制数据,不包括开始的length和最后CRC
crc32key = eval(str(bin_data[29:33]).replace(r'\x', '').replace("b'", '0x').replace("'", ''))
#理论上0xffffffff,但考虑到屏幕实际,0x0fff就差不多了
n = 4096
#高和宽一起爆破
for w in range(n):
# q为8字节,i为4字节,h为2字节
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
crc32result = zlib.crc32(data)
if crc32result == crc32key:
print("width:%s height:%s" % (bytearray(width).hex(),bytearray(height).hex()))
exit()

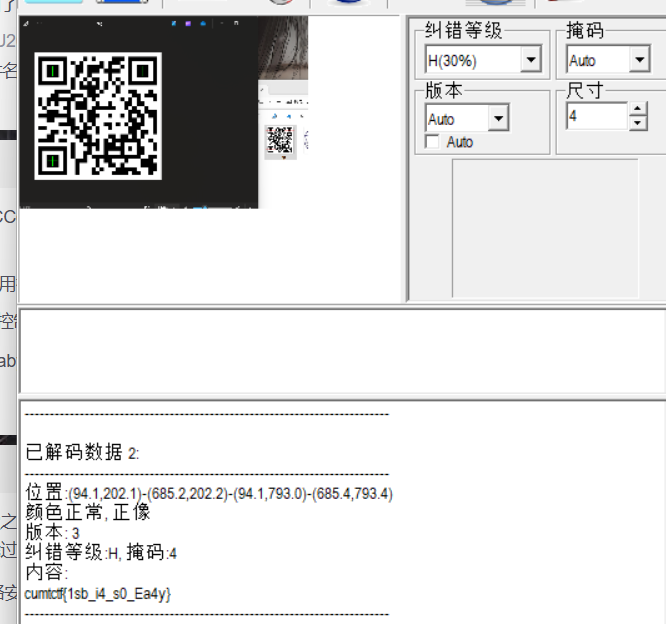
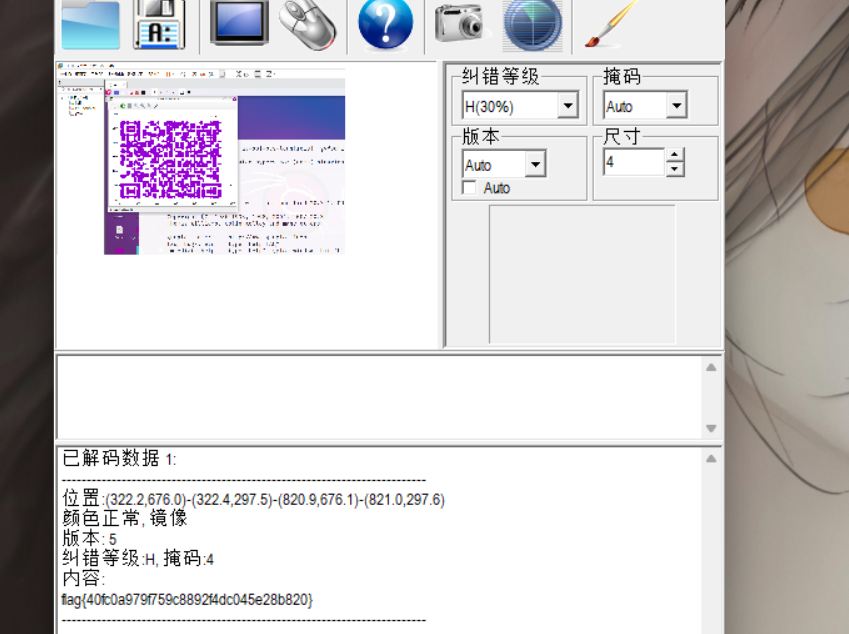
[SWPU2019]神奇的二维码

binwalk分离一下

base64解码doc文件得到密码 解压缩得到mp3
-- --- .-. ... . .. ... ...- . .-. -.-- ...- . .-. -.-- . .- ... -.--

转换为小写就是flag
[BJDCTF2020]纳尼
添加GIF文件头 得到gif
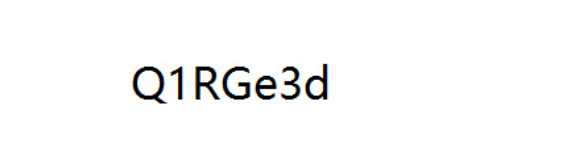
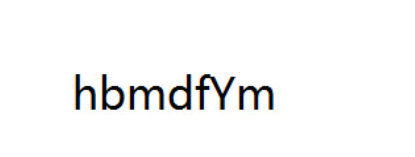
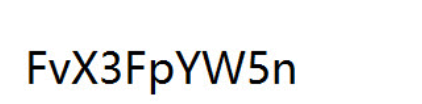
base64解码flag
CTF{wang_bao_qiang_is_sad}
[HBNIS2018]excel破解
xls丢进010
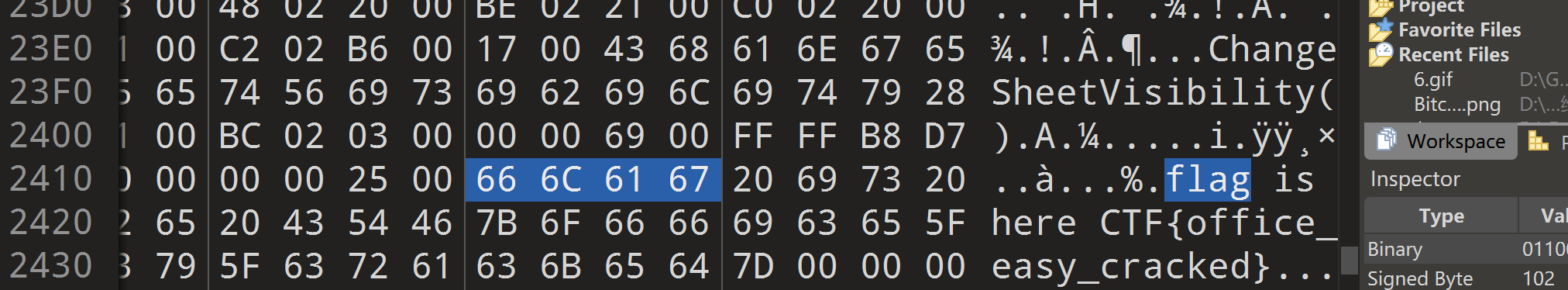
[HBNIS2018]来题中等的吧
打开图片是一段摩斯密码
.- .-.. .--. .... .- .-.. .- -...
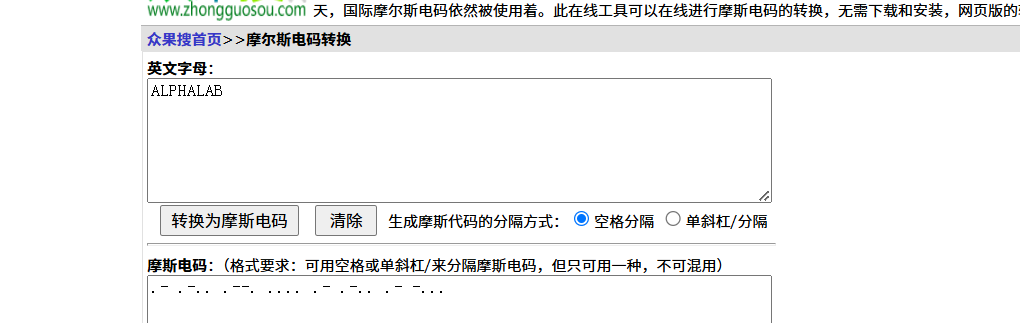
梅花香之苦寒来
将图片里的十六进制保存出来 转换为ascii
with open('hex.txt','r') as h:
h=h.read()
tem=''
for i in range(0,len(h),2):
tem='0x'+h[i]+h[i+1]
tem=int(tem,base=16)
print(chr(tem),end='')
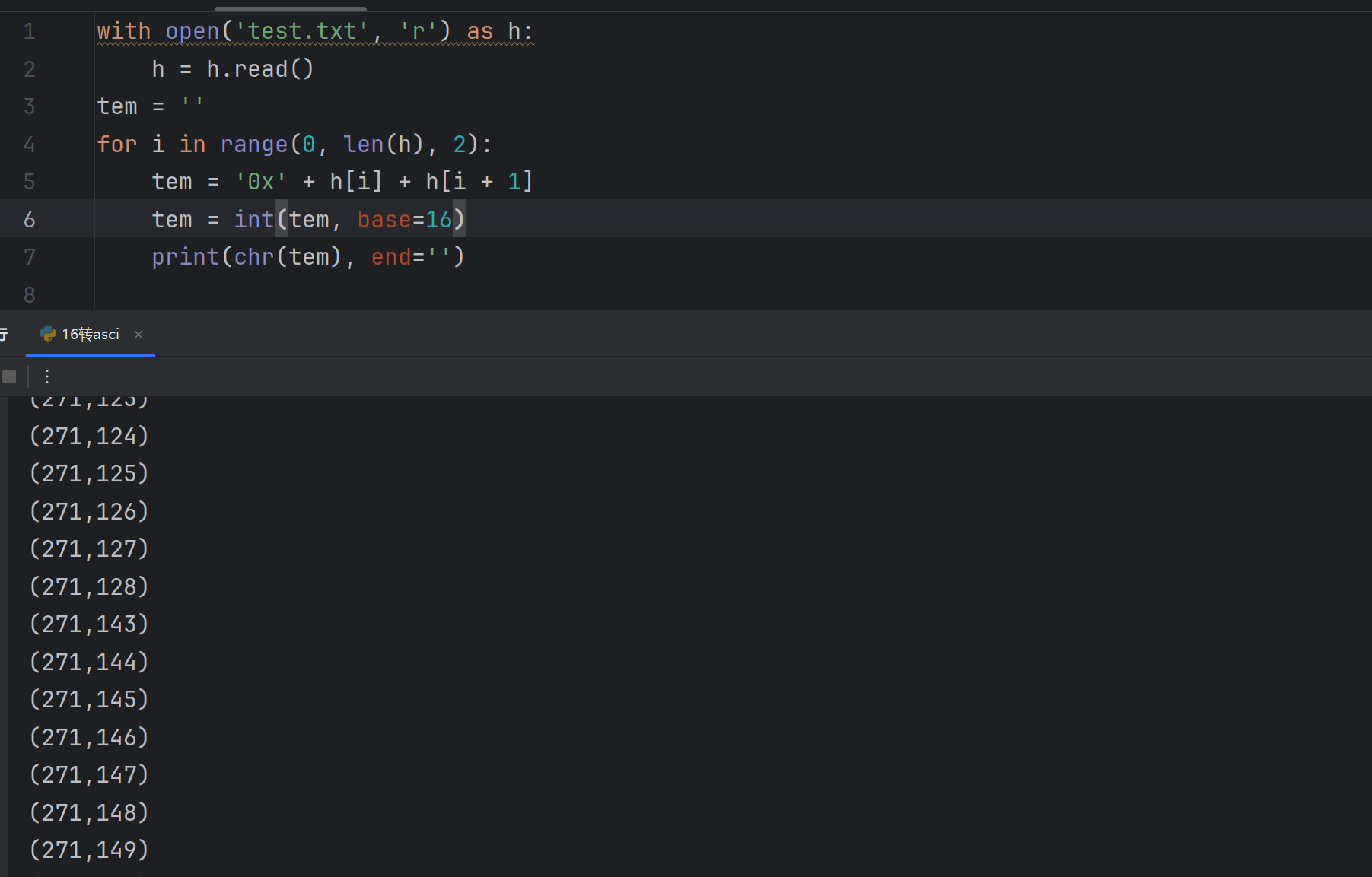
得到坐标 将其转换成 gnuplot 能识别的形式
with open('ascii.txt','r')as a:
a=a.read()
a=a.split()
tem=''
for i in range(0,len(a)):
tem=a[i]
tem=tem.lstrip('(')
tem=tem.rstrip(')')
for j in range(0,len(tem)):
if tem[j]==',':
tem=tem[:j]+' '+tem[j+1:]
print(tem)
gnuplot 绘图
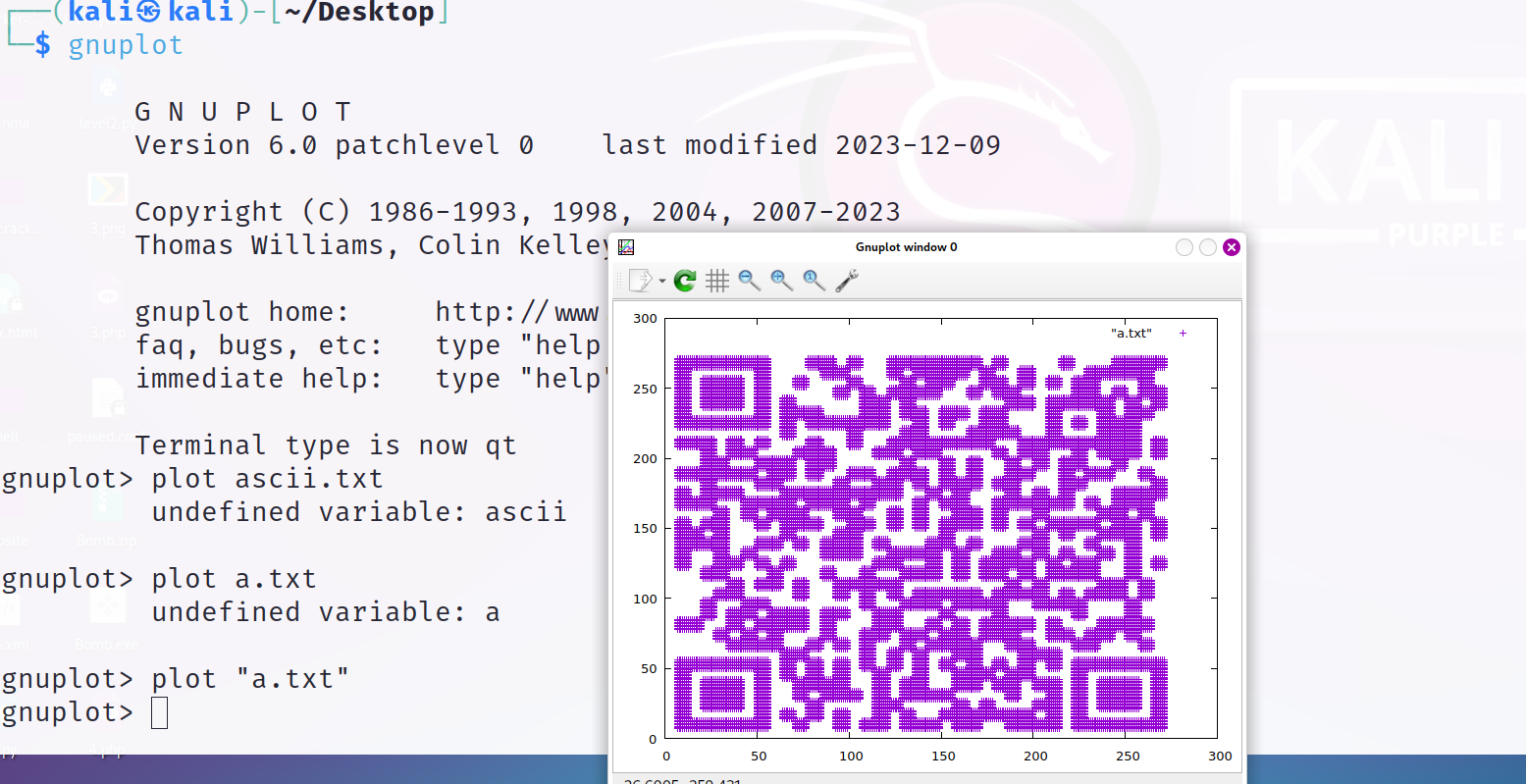
对于大量的十六进制 可以考虑将其转换成坐标 gnuplot 绘画
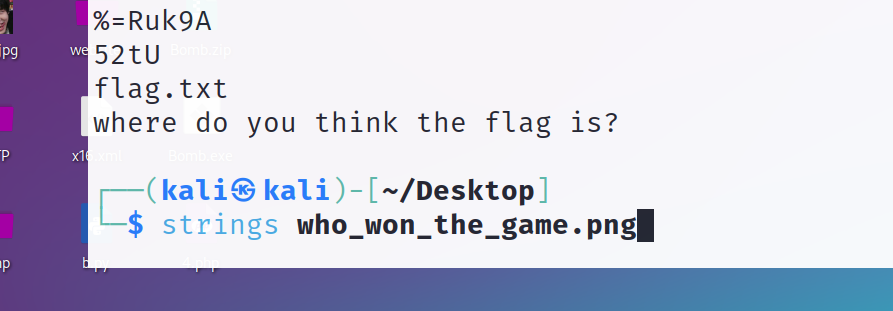
谁赢了比赛?
strings一下 发现flag.txt
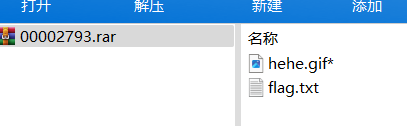
foremost 分离出rar 爆破密码
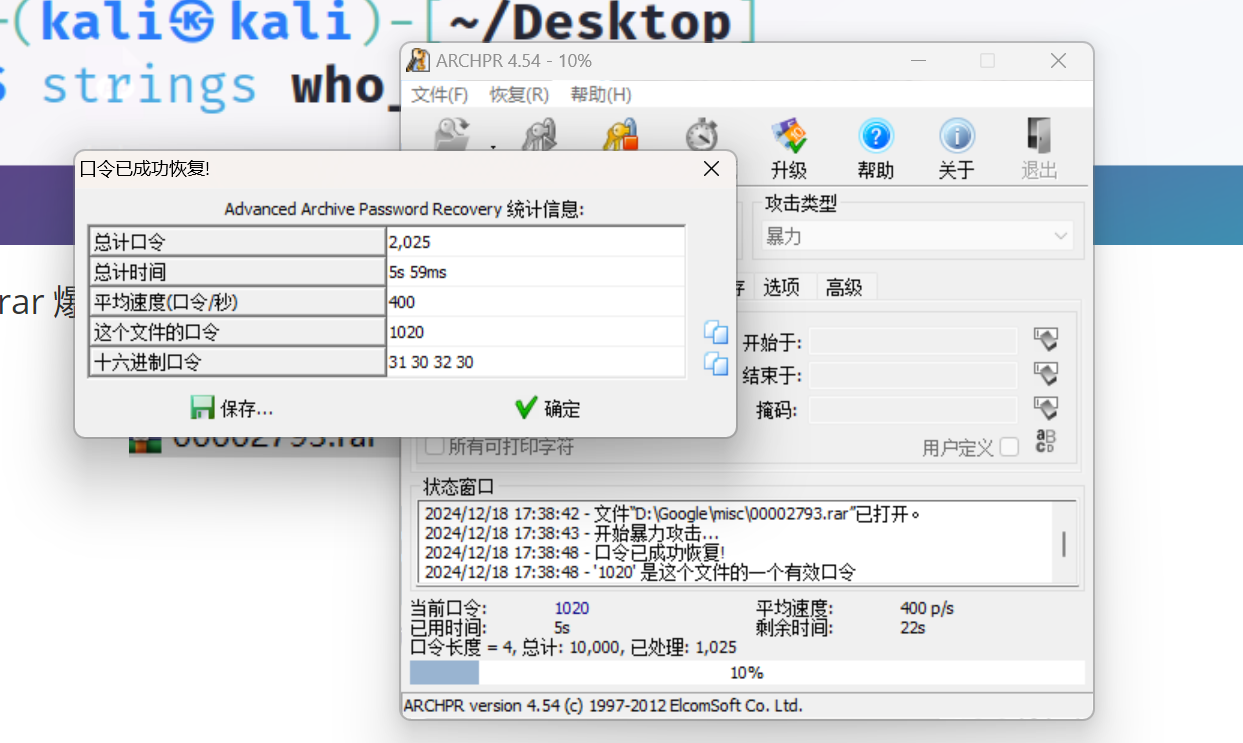
Ps分析gif图片

保存图片到 stegsolve里
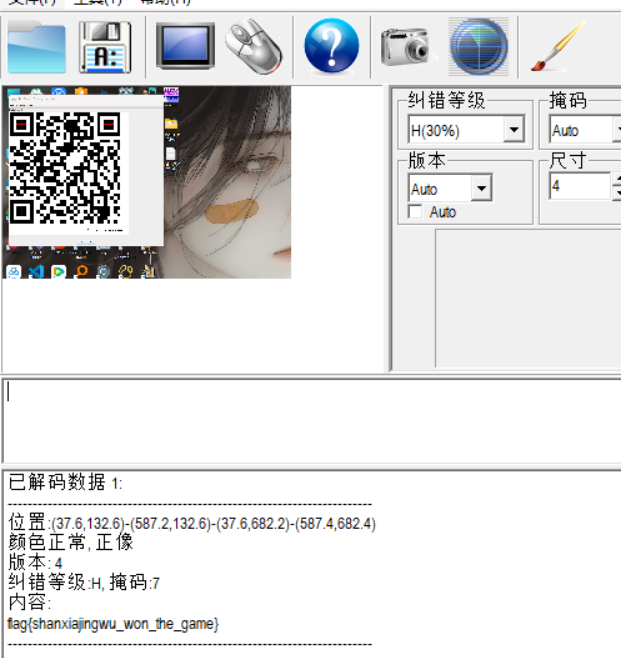
[ACTF新生赛2020]outguess
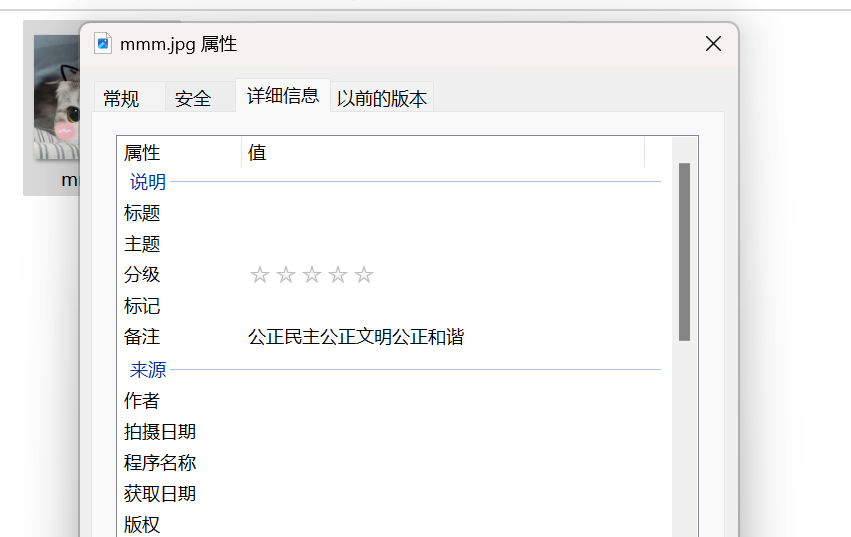
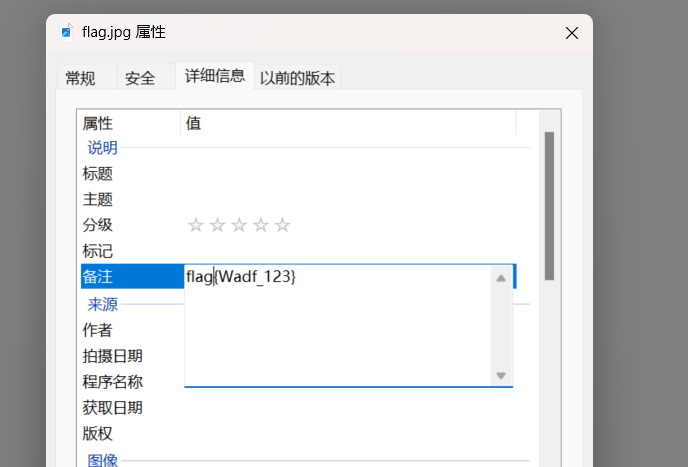
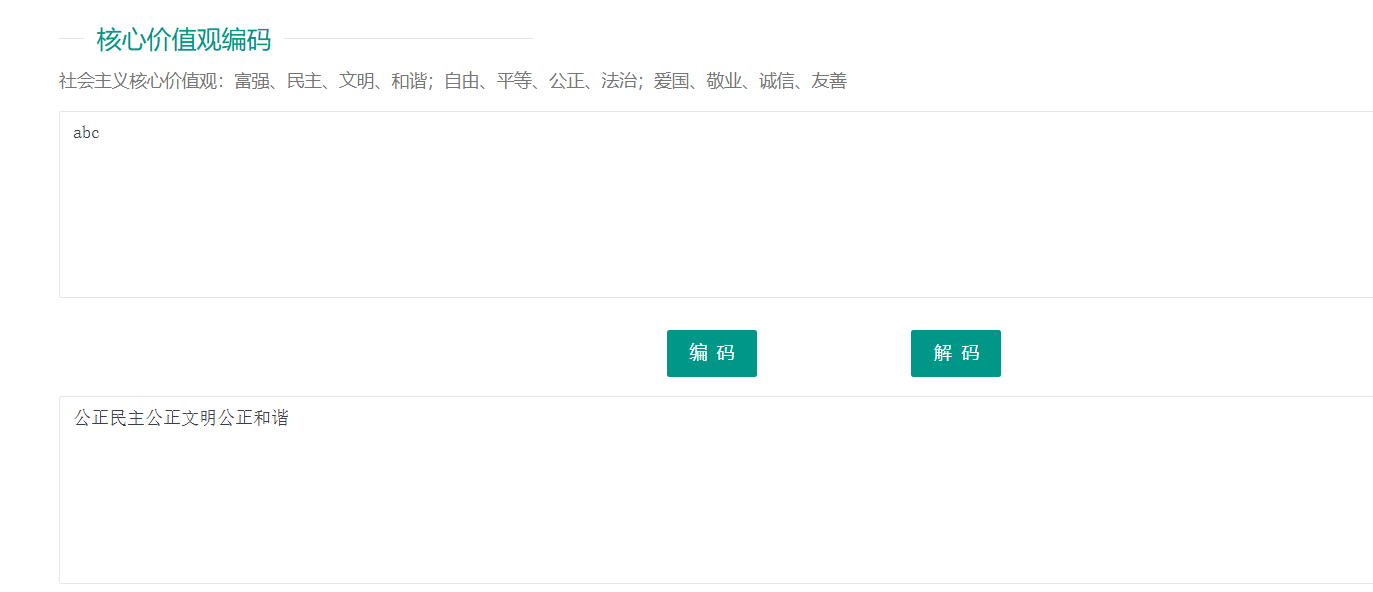
一开始没在在乎这个备注 社会主义核心价值观编码,绝了
结合题目名字 用工具outguess
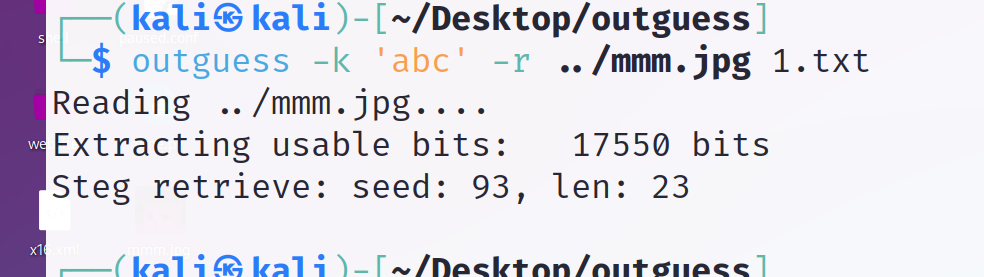
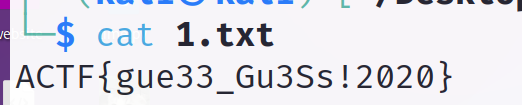
-k 表示密码,-r应该是表示解密的意思,1.txt表示把解密后的内容写到1.txt
[WUSTCTF2020]find_me
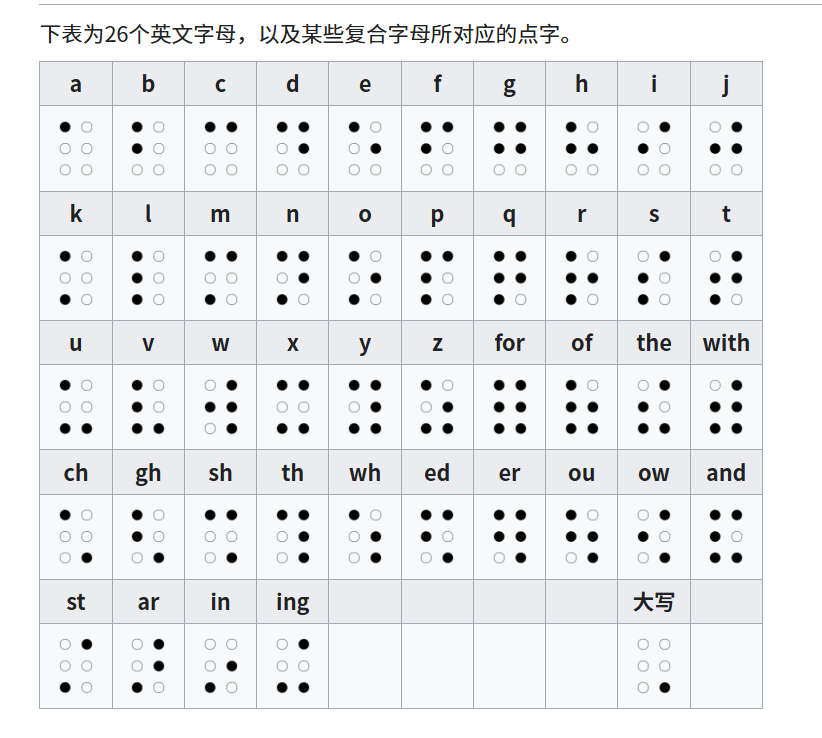
发现盲文
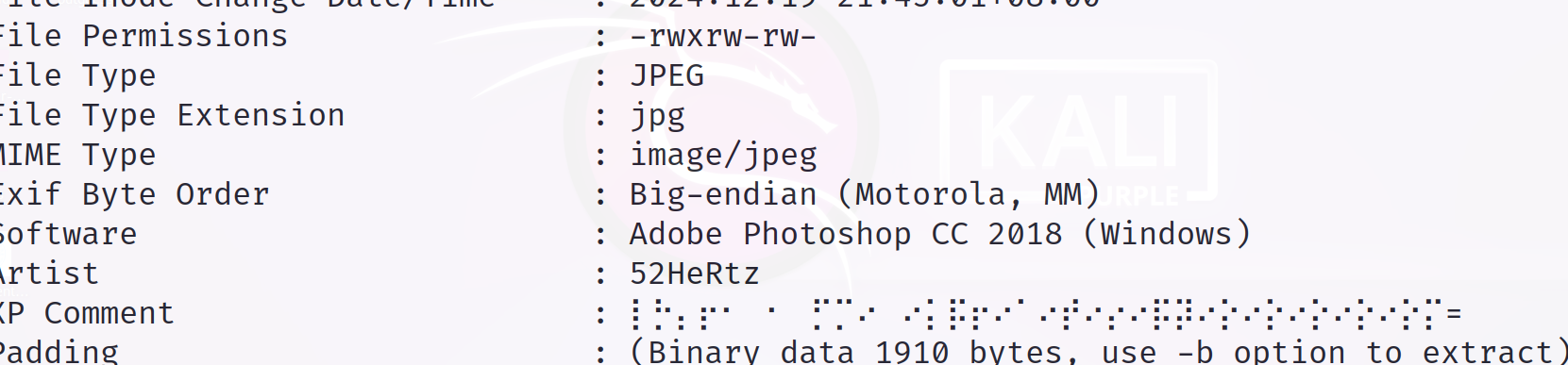
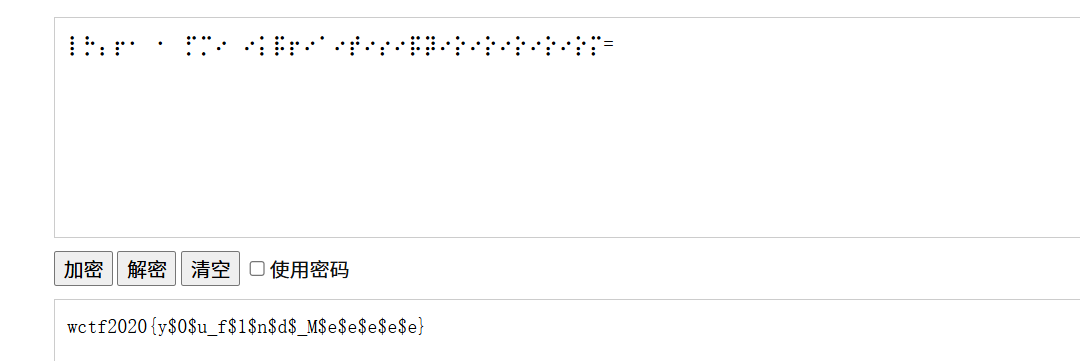
解码得到flag
穿越时空的思念
音频文件 有一段摩斯电码
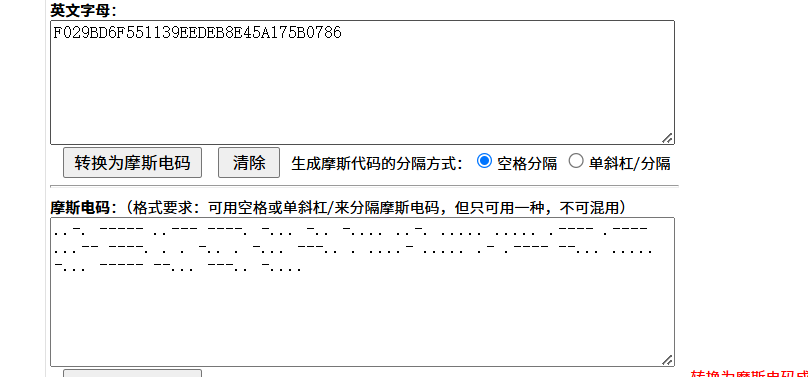
第二段
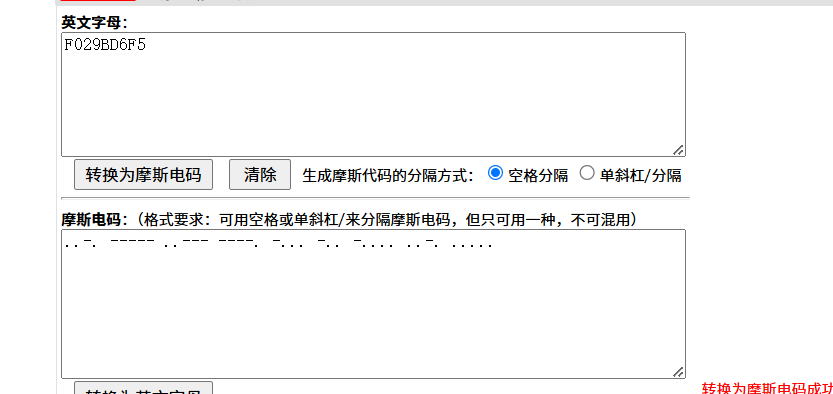
第一段转小写就是flag{}
[GUET-CTF2019]KO
Brainfuck/Ook! Obfuscation/Encoding
直接解码
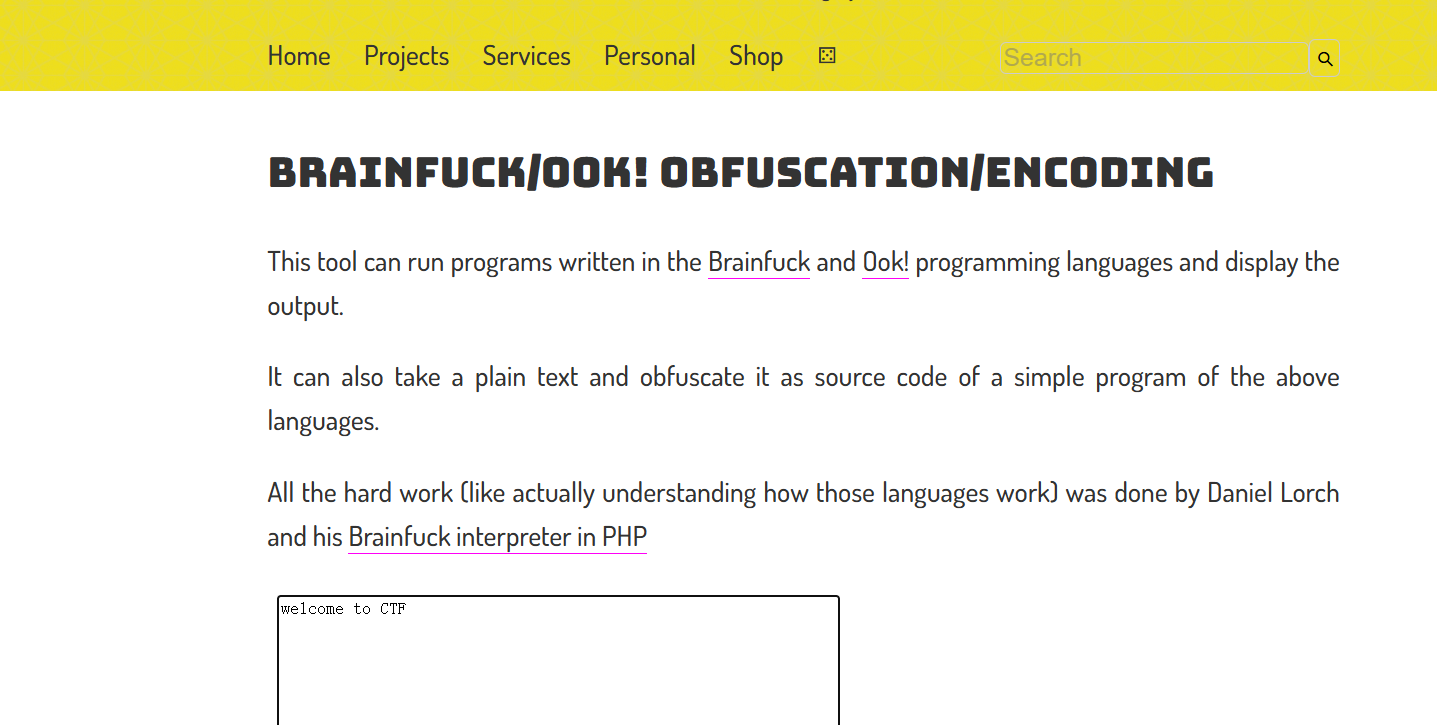
flag{welcome to CTF}
[ACTF新生赛2020]base64隐写
base64隐写就是 给你一大段字符串,让你找flag
直接上脚本
这里是找了两个脚本,以备不时之需
import base64
def get_base64_diff_value(s1, s2):
base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
res = 0
for i in range(min(len(s1), len(s2))):
if s1[i] != s2[i]:
res += abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))
return res
def solve_stego():
with open('ComeOn!.txt', 'r', encoding='utf-8') as f:
file_lines = f.readlines()
bin_str = ''
for line in file_lines:
steg_line = line.strip()
try:
norm_line = base64.b64encode(base64.b64decode(steg_line)).decode('utf-8').strip()
diff = get_base64_diff_value(steg_line, norm_line)
print(diff)
pads_num = steg_line.count('=')
if diff:
bin_str += bin(diff)[2:].zfill(pads_num * 2)
else:
bin_str += '0' * pads_num * 2
print(goflag(bin_str))
except base64.binascii.Error:
print(f"Error decoding line: {line}")
def goflag(bin_str):
res_str = ''
for i in range(0, len(bin_str), 8):
try:
res_str += chr(int(bin_str[i:i + 8], 2))
except ValueError:
pass
return res_str
if __name__ == '__main__':
solve_stego()
d='''STJsdVkyeDFaR1U4YVc5emRISmxZVzArQ2c9PQ1=
STJsdVkyeDFaR1U4YzNSeWFXNW5QZ289DQ==
STJsdVkyeDFaR1U4WTNOMGNtbHVaejRLDV==
STJsdVkyeDFaR1U4WTNOMFpHbHZQZ289DQ==
STJSbFptbHVaU0J0WVhodUlEazVPUW89Dd==
Q2c9PQ1=
ZFhOcGJtY2dibUZ1WlhOd1lXTmxJSE4wWkRzSw1=
Q2c9PQ0=
WTJoaGNpUmpZVnR0WVhodVhTd2dZMkpiYldGNGJsMDdDZz09DU==
Q2c9PQ1=
YVc1MElHTnRjQ2h6ZEhKcGJtY2dZU3dnYzNSeWFXNW5JR2lwQ2c9PQ2=
ZXdvPQ1=
SUNBZ3lHbG1LR3V1YzJsNlpTZ3BJRDRnWWk1emFYcGxLQ2twQ2c9PQ3=
SUNBZ0lDbWdJb0J5WlhSMWNtNGdNVHNLDb==
SUNBZ0lHVnNjMlVnYVdZb1lTNXphWHBsS0NrZ1BDQmlMbk5wZW1Vb0tTa0sN
SUNBZ0lDQWdJQ0J5WlhSMWNtNGdMVEU3Q2c9PQ0=
SUNBZ0lHVnNjMlVLDd==
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0JtYjNJb2FXNTBJR2tnUFNBd095QnBJRHdnWVM1emFYcGxLQ2s3SUdrckt5a0sN
SUNBZ2lDQWdJQ2I3Q2c9PQ2=
SUNBZ1lDQWdJQ1FnSUNBZ2FXWW9ZVnRwWFNBOElHSmJhVjBwQ2c9PQ1=
SUNBZ0lDYWdJY0FnSUNBZ0lDYWdJSEpsZEhWeWJpYXRNVHNLDY==
SUNBZ1lDQWdJQ1FnSUNBZ2FXWW9ZVnRwWFNBK1lHSmJhVjBwQ2c9PQ1=
SUNBZ0lDXWdJX0FnSUNBZ0lDXWdJSEpsZEhWeWJpXXhPd289DX==
SUNBZ0lDQWdJQ0I5Q2c9PQ0=
SUNBZ0lDdWdJd0J5WlhSMWNtNGdNRHNLDd==
SUNBZ0lIMEsN
ZlFvPQ2=
Q2c9PQ1=
ZG05cFpDQnlaWE5sZEdFb2MzUnlhVzVuSUdFcENnPT0N
ZXdvPQ1=
SUNBZ1lHMWxiWE5sZENoallTd3dMSE5wZW1WdlppaGpZU2twT3dvPQ1=
SUNBZ2lHWnZjaWhwYm5RZ2FTQTlJREE3SUdrZ1BDQmhMbk5wZW1Vb2tUc2dhU3NyS1FvPQ2=
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0JqWVZ0cFhTQTlJR0ZiWVM1emFYcGxLQ2t0TVMxcFhTQXRJQ2N3SnpzSw0=
SUNBZ0lIMEsN
ZlFvPQ2=
Q2c9PQ0=
ZG05cFpDQnlaWE5sZEdJb2MzUnlhVzVuSUdJcENnPT0N
ZXdvPQ3=
SUNBZ1lHMWxiWE5sZENoallpd3dMSE5wZW1WdlppaGpZaWtwT3dvPQ1=
SUNBZ0lHWnZjaWhwYm5RZ2FTQTlJREE3SUdrZ1BDQmlMbk5wZW1Vb0tUc2dhU3NyS1FvPQ0=
SUNBZ0lIc0sN
SUNBZ1lDQWdJQ1JqWWx1cFhTQTlJR1piWWk1emFYcGxLQ2t1TVMxcFhTQXRJQ2N3SnpzSw1=
SUNBZ1lDQWdJQ1F2TDNCeWFXNTBaaWdpSldRaUxHTmlXMmxkS1RzSw1=
SUNBZ0lIMEsN
ZlFvPQ3=
Q2c9PQ3=
YzNSeWFXNW5JR1ZrWkNoemRISnBibWNnWVN3Z2MzUnlhVzVuSUdJcEx5L2xpcURtczVVSw1=
ZXdvPQ2=
SUNBZ0lISmxjMlYwWVNoaEtUc3ZMK2FLaXVhdmorUzRnT1M5amVXdG1PZWFoT1d0bCtlc3B1V1BtT2FJa09hVnNPV3RseXpsdWJia3VKVG1pb3JtbGJEbnU0VGxqNDNvdjRmbW5hWGt2ci9rdW83bGtJN3BuYUxrdUkzbGtJemt2WTNtbGJEbm03amxpcUFLDW==
SUNBZ0lISmxjMlYwWWloaUtUc0sN
SUNBZ0lHWnZjaWhwYm5RZ2FTTTlJREE3SUdrZ1BDTnRZWGh1T3lCcEt5c3BDZz09DT==
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0JqWVZ0cFhTQTlJR05oVzJsZElDc2dZMkpiYVYwN0NnPT0N
SUNBZ0lDQWdJQ0JwWmloallWdHBYU0ErUFNBeUtYc0sN
SUNBZ0lDTWdJT0FnSUNBZ1kyRmJhU3N4WFNBclBTTXhPd289DT==
SUNBZ0lDQWdJQ0FnSUNBZ1kyRmJhVjBnTFQwZ01qc0sN
SUNBZ0lDQWdJQ0I5Q2c9PQ0=
SUNBZ0lIMEsN
SUNBZ0lHSnZiMndnWm14aFp5QTlJSFJ5ZFdVN0NnPT0N
SUNBZ3lITjBjbWx1WnlCaklEMGdJaUk3Q2c9PQ3=
SUNBZ0lHWnZjaWhwYm5RZ2FTQTlJRzFoZUc0Z0xTQXhPeUJwSUQ0OUlEQTdJR2t0TFNrSw0=
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0JwWmlobWJHRm5JQ1ltSUdOaFcybGRJRDA5SURBcENnPT0N
SUNBZ0lDQWdJQ0FnSUNBZ1kyOXVkR2x1ZFdVN0NnPT0N
SUNBZ0lDQWdJQ0JwWmloallWdHBYU0FoUFNBd0tRbz0N
SUNBZ0lDcWdJc0FnSUNBZ1pteGhaeUE5SUdaaGJITmxPd289Dc==
SUNBZ2lDQWdJQ2JqSUNzOUlDaGpZVnRwWFNBcklDY3dKeWs3Q2c9PQ2=
SUNBZ0lDQWdJQ0F2TDNCeWFXNTBaaWdpSldRaUxHTmhXMmxkS1RzSw0=
SUNBZ0lIMEsN
SUNBZ0lHbG1LR1pzWVdjcENnPT0N
SUNBZ1lDQWdJQ1J5WlhSMWNtNGdJakFpT3dvPQ1=
SUNBZ0lHVnNjMlVLDX==
SUNBZ0lDdWdJd0J5WlhSMWNtNGdZenNLDd==
ZlFvPQ0=
Q2c9PQ0=
YzNSeWFXNW5JRzFwYm5Vb2MzUnlhVzVuSUdFc0lITjBjbWx1WnlCaUtTOHY1WWVQNXJPVkNnPT0N
ZXdvPQ0=
SUNBZ0lHbHVkQ0J6YVdkdUlEMGdNRHNLDQ==
SUNBZ0lHbG1LR050Y0NoaExDQmlLU0E5UFNBdE1Ta3ZMMkhrdUszbHVwVG9yNlhsclpqb3ZvUGxwS2ZubW9UcGdxUGt1S3JtbGJBSw0=
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0J6YVdkdUlEMGdNVHNLDQ==
SUNBZ0lDQWdJQ0J6ZEhKcGJtY2dkR1Z0Y0NBOUlHRTdDZz09DQ==
SUNBZ0lDQWdJQ0JoSUQwZ1lqc0sN
SUNBZ0lDQWdJQ0JpSUQwZ2RHVnRjRHNLDQ==
SUNBZ0lIMEsN
SUNBZ0lISmxjMlYwWVNoaEtUc0sN
SUNBZ0lISmxjMlYwWWloaUtUc0sN
SUNBZ0lHWnZjaWhwYm5RZ2FTQTlJREE3SUdrZ1BDQnRZWGh1T3lCcEt5c3BDZz09DQ==
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0JwWmloallWdHBYU0E4SUdOaVcybGRLWHNLDQ==
SUNBZ0lDQWdJQ0FnSUNBZ1kyRmJhU3N4WFNBdFBTQXhPd289DQ==
SUNBZ0lDQWdJQ0FnSUNBZ1kyRmJhVjBnS3owZ01qc0sN
SUNBZ0lDQWdJQ0I5Q2c9PQ0=
SUNBZ0lDQWdJQ0JqWVZ0cFhTQTlJR05oVzJsZElDMGdZMkpiYVYwN0NnPT0N
SUNBZ0lIMEsN
SUNBZ0lHSnZiMndnWm14aFp5QTlJSFJ5ZFdVN0NnPT0N
SUNBZ0lITjBjbWx1WnlCa0lEMGdJaUk3Q2c9PQ0=
SUNBZ0lHWnZjaWhwYm5RZ2FTQTlJRzFoZUc0Z0xTQXhPeUJwSUQ0OUlEQTdJR2t0TFNrSw0=
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0JwWmlobWJHRm5JQ1ltSUdOaFcybGRJRDA5SURBcENnPT0N
SUNBZ0lDQWdJQ0FnSUNBZ1kyOXVkR2x1ZFdVN0NnPT0N
SUNBZ0lDQWdJQ0JwWmloallWdHBYU0FoUFNBd0tRbz0N
SUNBZ0lDQWdJQ0FnSUNBZ1pteGhaeUE5SUdaaGJITmxPd289DQ==
SUNBZ0lDQWdJQ0JrSUNzOUlDaGpZVnRwWFNBcklDY3dKeWs3Q2c9PQ0=
SUNBZ0lDQWdJQ0F2TDNCeWFXNTBaaWdpSldRaUxHTmhXMmxkS1RzSw0=
SUNBZ0lIMEsN
SUNBZ0lHbG1LR1pzWVdjcENnPT0N
SUNBZ0lDQWdJQ0J5WlhSMWNtNGdJakFpT3dvPQ0=
SUNBZ0lHVnNjMlVLDQ==
SUNBZ0lDQWdJQ0J5WlhSMWNtNGdaRHNLDQ==
ZlFvPQ0=
Q2c9PQ0=
YzNSeWFXNW5JRzExYkNoemRISnBibWNnZUN3Z2MzUnlhVzVuSUhrcEx5OXo1TGk2NTZ5bTVZKzM1TDJOQ2c9PQ0=
ZXdvPQ0=
SUNBZ0lHbHVkQ0JzWlc1NElEMGdlQzV6YVhwbEtDazdDZz09DQ==
SUNBZ0lHbHVkQ0JzWlc1NUlEMGdlUzV6YVhwbEtDazdDZz09DQ==
SUNBZ0lHbG1LR3hsYm5nZ1BUMGdNU2tLDQ==
SUNBZ0lIc0sN
SUNBZ0lDQWdJQ0F2TDJOdmRYUThQSGc4UENJZ0lDQWlQRHg1UER4bGJtUnNPd289DQ==
SUNBZ0lDQWdJQ0JwWmloNElEMDlJQ0l4SWlBbUppQjVJRDA5SUNJeElpa0sN
SUNBZ0lDQWdJQ0FnSUNBZ2NtVjBkWEp1SUNJeElqc0sN
SUNBZ0lDQWdJQ0JsYkhObENnPT0N
SUNBZ0lDQWdJQ0FnSUNBZ2NtVjBkWEp1SUNJd0lpQTdDZz09DQ==
SUNBZ0lIMEsN
Q2c9PQ0=
SUNBZ0lDOHZjSEpwYm5SbUtDSWxaQzB0SldSY2JpSXNiR1Z1ZUN4c1pXNTVLVHNLDQ==
Q2c9PQ0=
SUNBZ0lITjBjbWx1WnlCaExDQmlMQ0JqTEdRN0NnPT0N
SUNBZ0lHRWdQU0I0TG5OMVluTjBjaWd3TENCc1pXNTRMeklwT3dvPQ0=
SUNBZ0lHSWdQU0I0TG5OMVluTjBjaWhzWlc1NEx6SXNJR3hsYm5ndk1pazdDZz09DQ==
SUNBZ0lHTWdQU0I1TG5OMVluTjBjaWd3TENCc1pXNTVMeklwT3dvPQ0=
SUNBZ0lHUWdQU0I1TG5OMVluTjBjaWhzWlc1NUx6SXNJR3hsYm5rdk1pazdDZz09DQ==
SUNBZ0lIQnlhVzUwWmlnaUpXUXRMU1ZrTFMwbFpDMHRKV1F0TFMwdExTMHRMUzB0TFMwdExTMHRMUzB0TFMwdExTMHRMUzB0TFMwdExTMHRMUzB0TFMwdExTMHRMU1ZrTFNWa1hHNGlMR0V1YzJsNlpTZ3BMQ0JpTG5OcGVtVW9LU3dnWXk1emFYcGxLQ2tzSUdRdWMybDZaU2dwTENCNExuTnBlbVVvS1N3Z2VTNXphWHBsS0NrcE93bz0N
SUNBZ0lDOHZZMjkxZER3OGVEdzhJam9pUER4aFBEd2lJQ0k4UEdJOFBDSWdJanc4WXp3OElpQWlQRHhrUER4bGJtUnNPd289DQ==
SUNBZ0lITjBjbWx1WnlCaFl5QTlJRzExYkNoaExDQmpLVHNLDQ==
SUNBZ0lITjBjbWx1WnlCaVpDQTlJRzExYkNoaUxDQmtLVHNLDQ==
SUNBZ0lDOHZZMjkxZER3OGVEdzhJam9pUER4aFl6dzhJaUFpUER4aVpEdzhaVzVrYkRzSw0=
Q2c9PQ0=
SUNBZ0lITjBjbWx1WnlCaFlpQTlJRzFwYm5Vb1lTd2dZaWs3THk5aExXSUsN
SUNBZ0lITjBjbWx1WnlCalpDQTlJRzFwYm5Vb1pDd2dZeWs3Q2c9PQ0=
SUNBZ0lDOHZZMjkxZER3OGVEdzhJam9pUER4aFlqdzhJaUFpUER4alpEdzhaVzVrYkRzSw0=
Q2c9PQ0=
SUNBZ0lITjBjbWx1WnlCaFltTmtJRDBnYlhWc0tHRmlMQ0JqWkNrN0NnPT0N
SUNBZ0lDOHZZMjkxZER3OGVEdzhJam9pUER4aFltTmtQRHhsYm1Sc093bz0N
Q2c9PQ0=
SUNBZ0lITjBjbWx1WnlCbWFYSnpkQ0E5SUdGak93bz0N
SUNBZ0lHWnZjaWhwYm5RZ2FTQTlJREE3SUdrZ1BDQW9iR1Z1ZUNrN0lHa3JLeWtLDQ==
SUNBZ0lDQWdJQ0JtYVhKemRDQXJQU0FpTUNJN0NnPT0N
SUNBZ0lDOHZZMjkxZER3OFlXTThQQ0lnTFMwdExTMWhZeTB0TFMwZ0lqdzhabWx5YzNROFBHVnVaR3c3Q2c9PQ0=
Q2c9PQ0=
SUNBZ0lITjBjbWx1WnlCelpXTnZibVFnUFNCaFpHUW9ZV0pqWkN3Z1lXTXBPd289DQ==
SUNBZ0lITmxZMjl1WkNBOUlHRmtaQ2h6WldOdmJtUXNJR0prS1RzSw0=
SUNBZ0lHWnZjaWhwYm5RZ2FTQTlJREE3SUdrZ1BDQW9iR1Z1ZUM4eUtUc2dhU3NyS1FvPQ0=
SUNBZ0lDQWdJQ0J6WldOdmJtUWdLejBnSWpBaU93bz0N
Q2c9PQ0=
SUNBZ0lITjBjbWx1WnlCbWFXNGdQU0JoWkdRb1ptbHljM1FzSUhObFkyOXVaQ2s3Q2c9PQ0=
SUNBZ0lISmxkSFZ5YmlCaFpHUW9abWx1TENCaVpDazdDZz09DQ==
Q2c9PQ0=
ZlFvPQ0=
Q2c9PQ0=
YVc1MElHMWhhVzRvZG05cFpDa0sN
ZXdvPQ0=
SUNBZ0lITjBjbWx1WnlCNExDQjVPd289DQ==
SUNBZ0lIQnlhVzUwWmlnaTZLKzM2TDZUNVlXbDVMaWs1TGlxNUxxTTZMK2I1WWkyNXBXdzVhMlhPaUFpS1RzSw0=
SUNBZ0lHTnBiajQrZUQ0K2VUc0sN
SUNBZ0lITjBjbWx1WnlCaGJuTWdQU0J0ZFd3b2VDd2dlU2s3Q2c9PQ0=
SUNBZ0lHTnZkWFE4UEdGdWN6c0sN
ZlFvPQ0=
'''
e=d.splitlines()
binstr=""
base64="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
for i in e :
if i.find("==")>0:
temp=bin((base64.find(i[-3])&15))[2:]
#取倒数第3个字符,在base64找到对应的索引数(就是编码数),取低4位,再转换为二进制字符
binstr=binstr + "0"*(4-len(temp))+temp #二进制字符补高位0后,连接字符到binstr
elif i.find("=")>0:
temp=bin((base64.find(i[-2])&3))[2:] #取倒数第2个字符,在base64找到对应的索引数(就是编码数),取低2位,再转换为二进制字符
binstr=binstr + "0"*(2-len(temp))+temp #二进制字符补高位0后,连接字符到binstr
str=""
for i in range(0,len(binstr),8):
str=str+chr(int(binstr[i:i+8],2)) #从左到右,每取8位转换为ascii字符,连接字符到字符串
print(str) #结果是 Base_sixty_four_point_five转换为
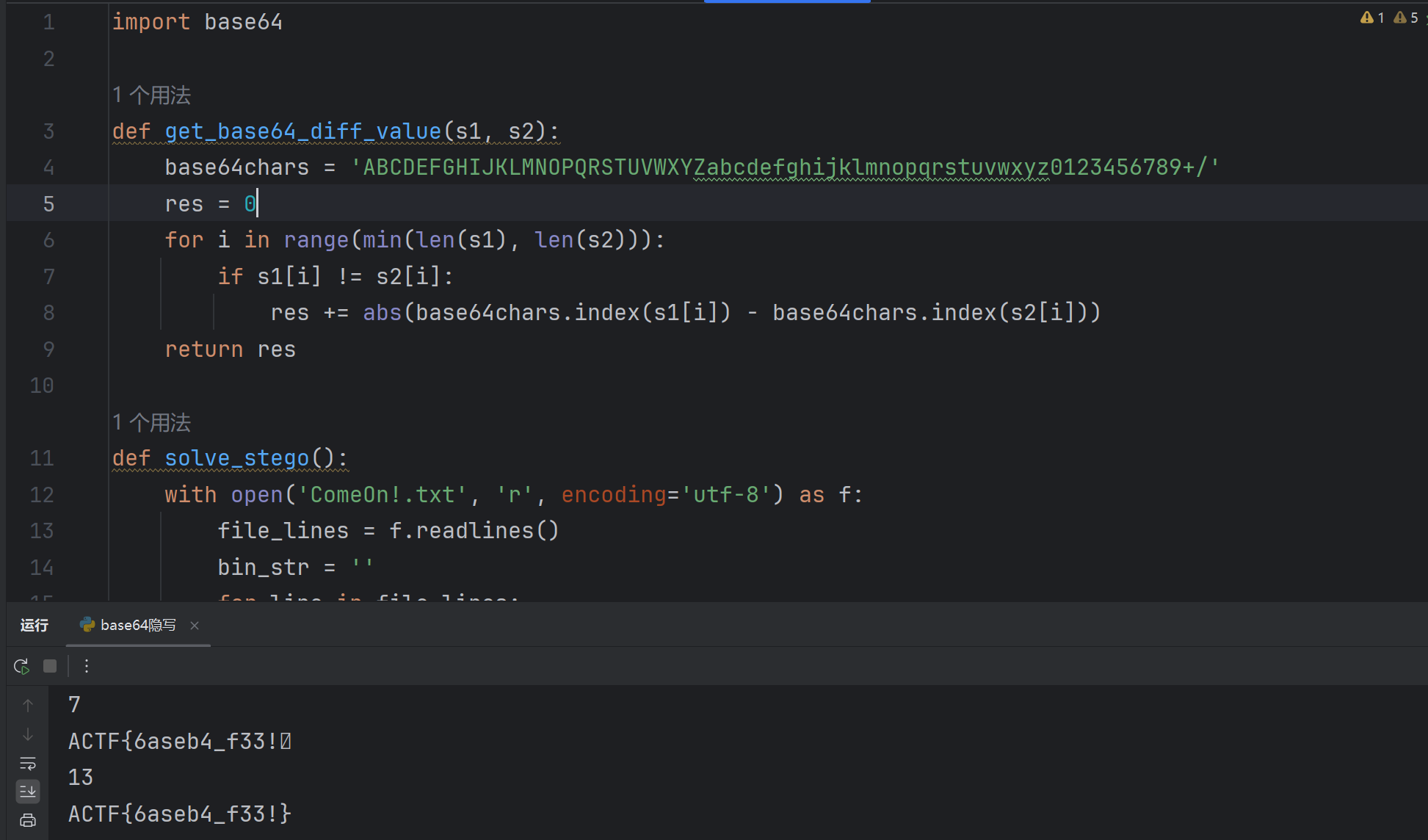
浅浅补充一下base64隐写解法:
是在正常情况下base64解码过程中,将不影响解码结果的位提取出来组成二进制串,再转换成ascii字符串
具体就是
已知:字符串"Rascals"经过 Base64 编码后变为"UmFzY2FSCW==''
解析:UmFzY2Fscw== 首先丢掉末尾的== ,得到UmFzY2Fscw,然后 每个字符查表转换为对应的6位索引
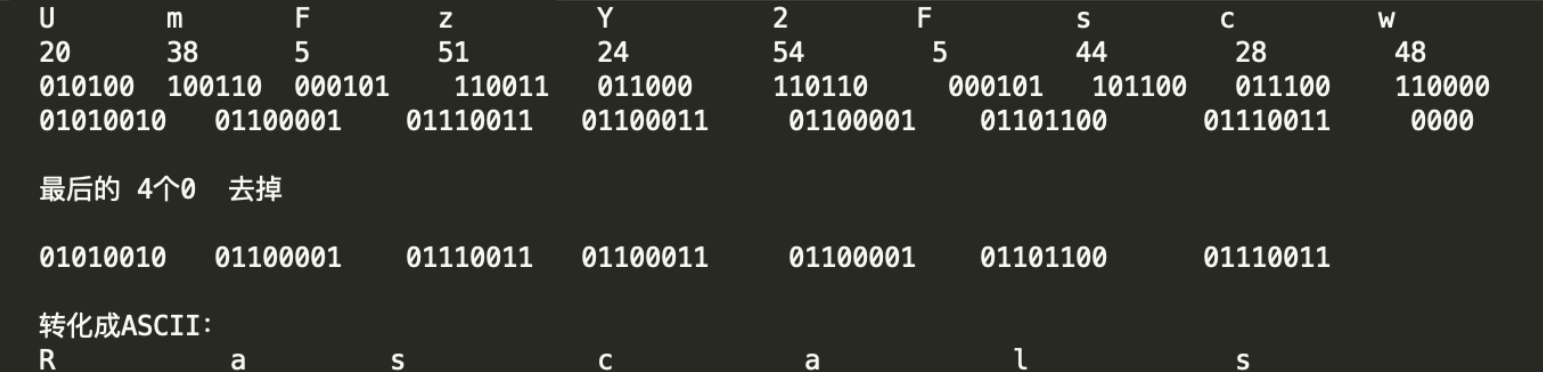
解码过程中,会有一部分数据是会被丢弃的,当然被丢弃的这部分数据(正常编码过程中补位的0)是不会影响正常解码结果的。如果说,我们不用0补位,而是用一些其他的数据补位,而这些数据的位置就用于隐写
[SWPU2019]我有一只马里奥
运行一下给的exe得到一个txt
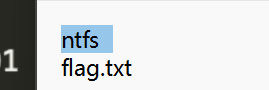
根据提示查看一下ntfs交换数据流
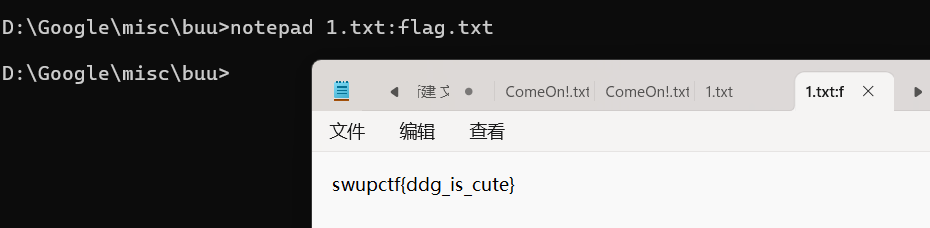
参考
“在NTFS中,主数据流指的是文件或目录的标准内容,通常对用户可见,而备用数据流(ADS)则隐藏”
“ADS没有大小限制且多个数据流可以和一个正常文件关联。ADS的内容也不仅限于text文本数据,基本上只要是二进制格式文件都可以被作为ADS备用流嵌入” (也就是文件后缀是jpg,png,asp,exe的都可以)
”宿住消失寄生消失“
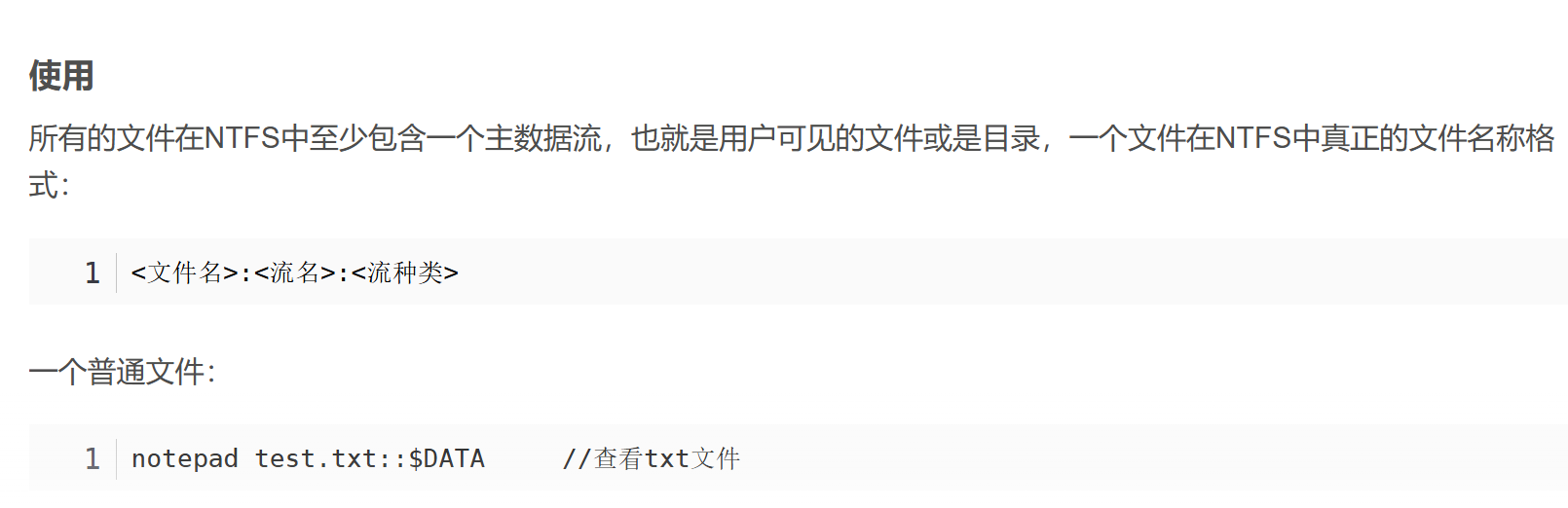
简单来说就是
我们先创建了一个宿住文件为test.txt,内容随意
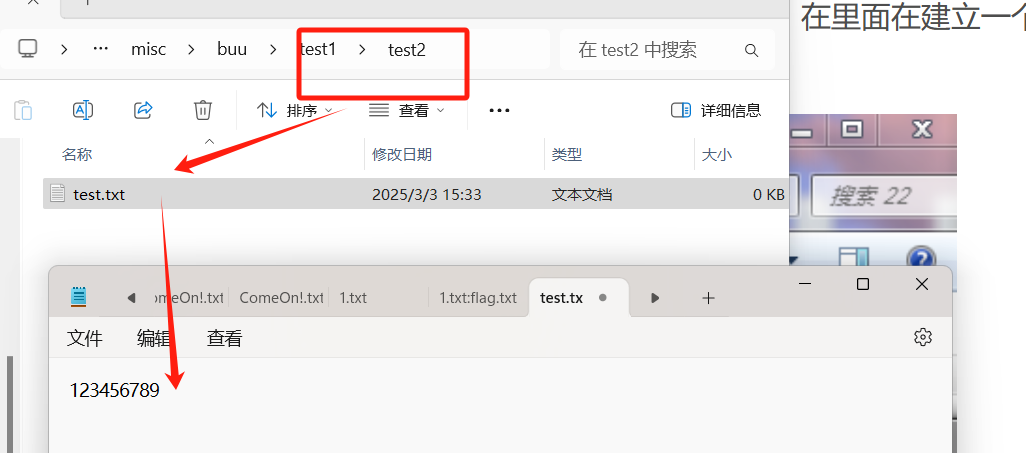
在创建一个关联数据流文件
打开cmd,在目录下echo
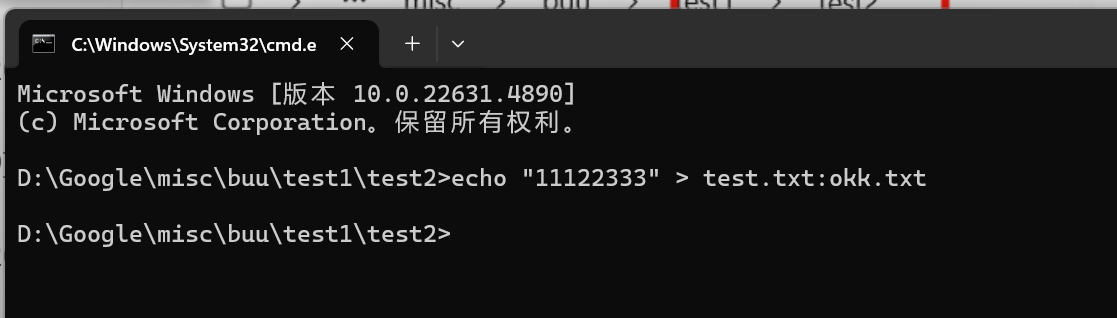
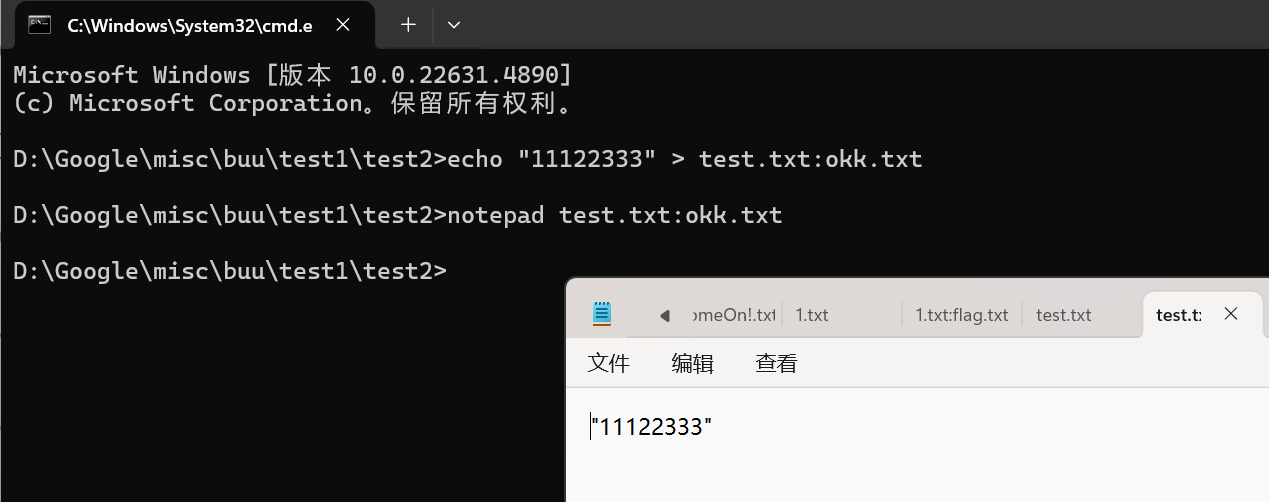
在输入命令 notepad test.txt:okk.txt
[MRCTF2020]ezmisc

[GXYCTF2019]gakki
jpg里藏了个rar
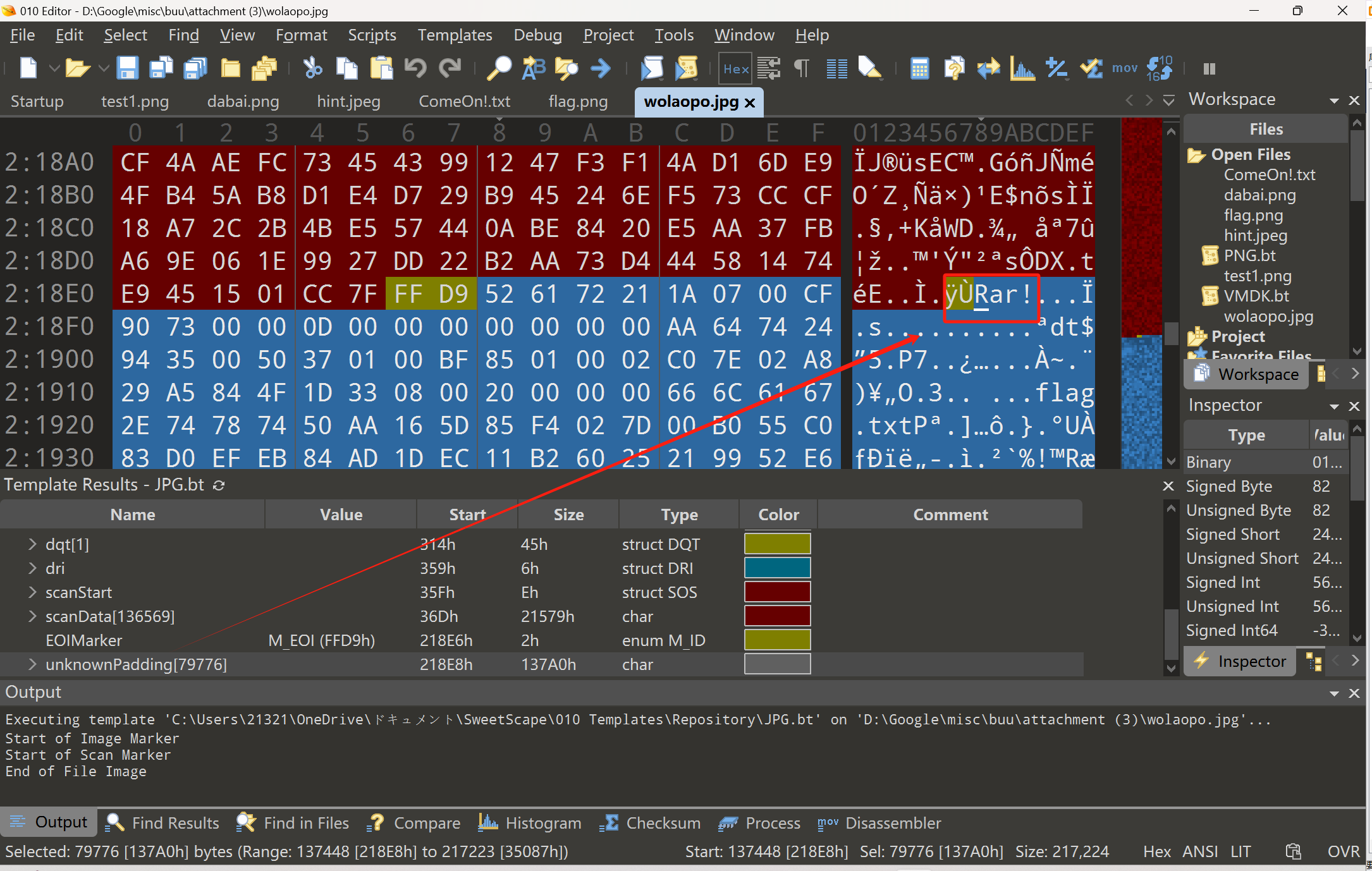
爆破rar密码
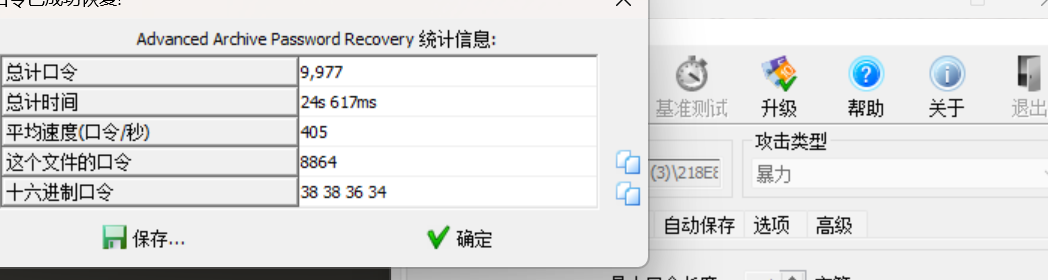
解压缩得到一段字符串
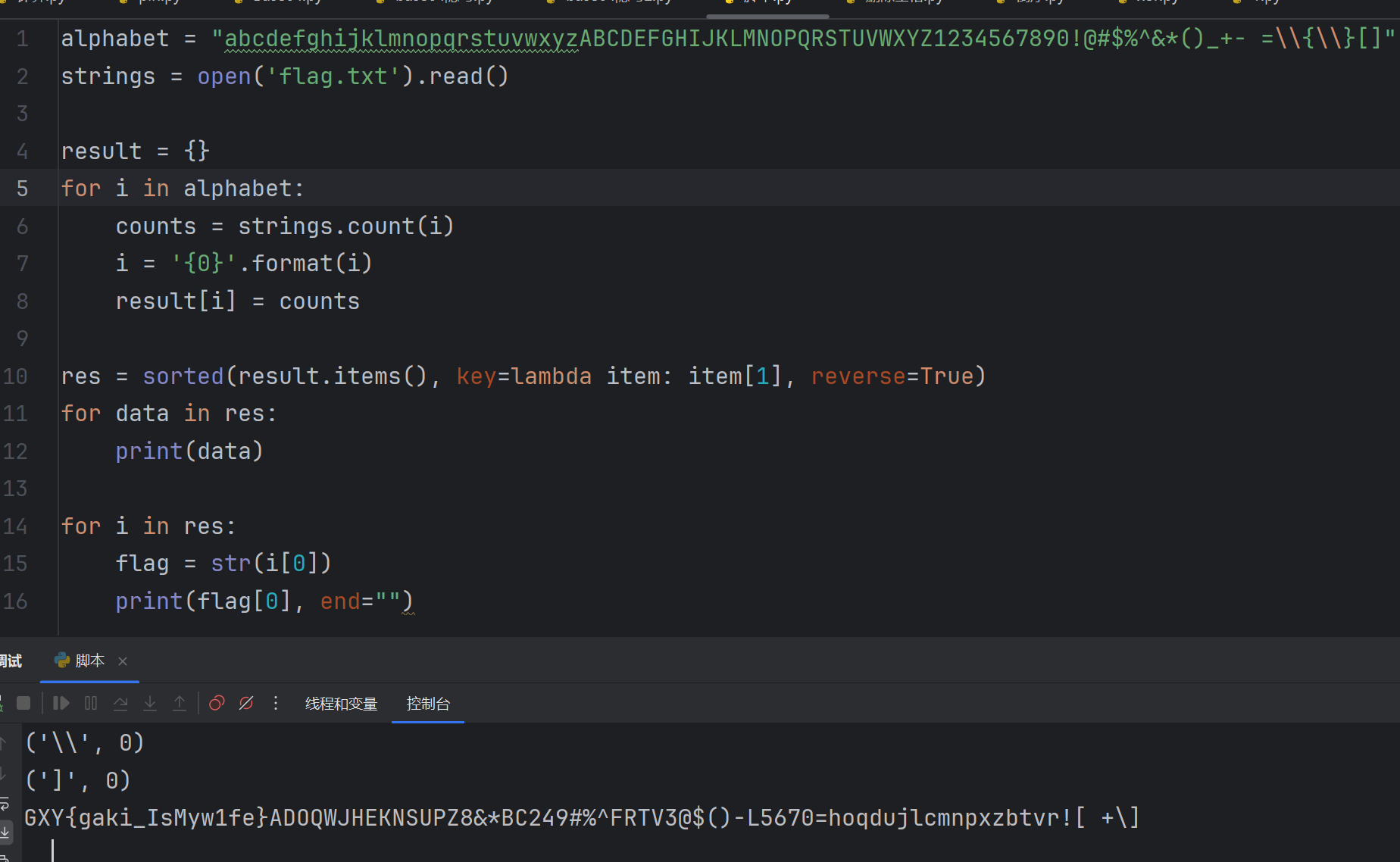
本题的解题思路就是统计里面出现的字符的个数,根据出现的次数排列即可得到flag
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()_+- =\\{\\}[]"
strings = open('flag.txt').read()
result = {}
for i in alphabet:
counts = strings.count(i)
i = '{0}'.format(i)
result[i] = counts
res = sorted(result.items(),key=lambda item:item[1],reverse=True)
for data in res:
print(data)
for i in res:
flag = str(i[0])
print(flag[0],end="")
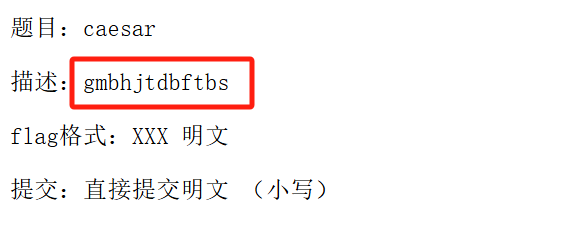
[HBNIS2018]caesar
凯撒密码 直接上脚本
def encrypt(plaintext):
# j即为key
for j in range(26):
str_list = list(plaintext)
i = 0
while i <len(plaintext):
if not str_list[i].isalpha():
str_list[i] = str_list[i]
else:
a = "A" if str_list[i].isupper() else "a"
str_list[i] = chr((ord(str_list[i]) - ord(a) + j) % 26 + ord(a))
i = i + 1
print(''.join(str_list))
if __name__ == '__main__':
plaintext = "gmbhjtdbftbs"
encrypt(plaintext)
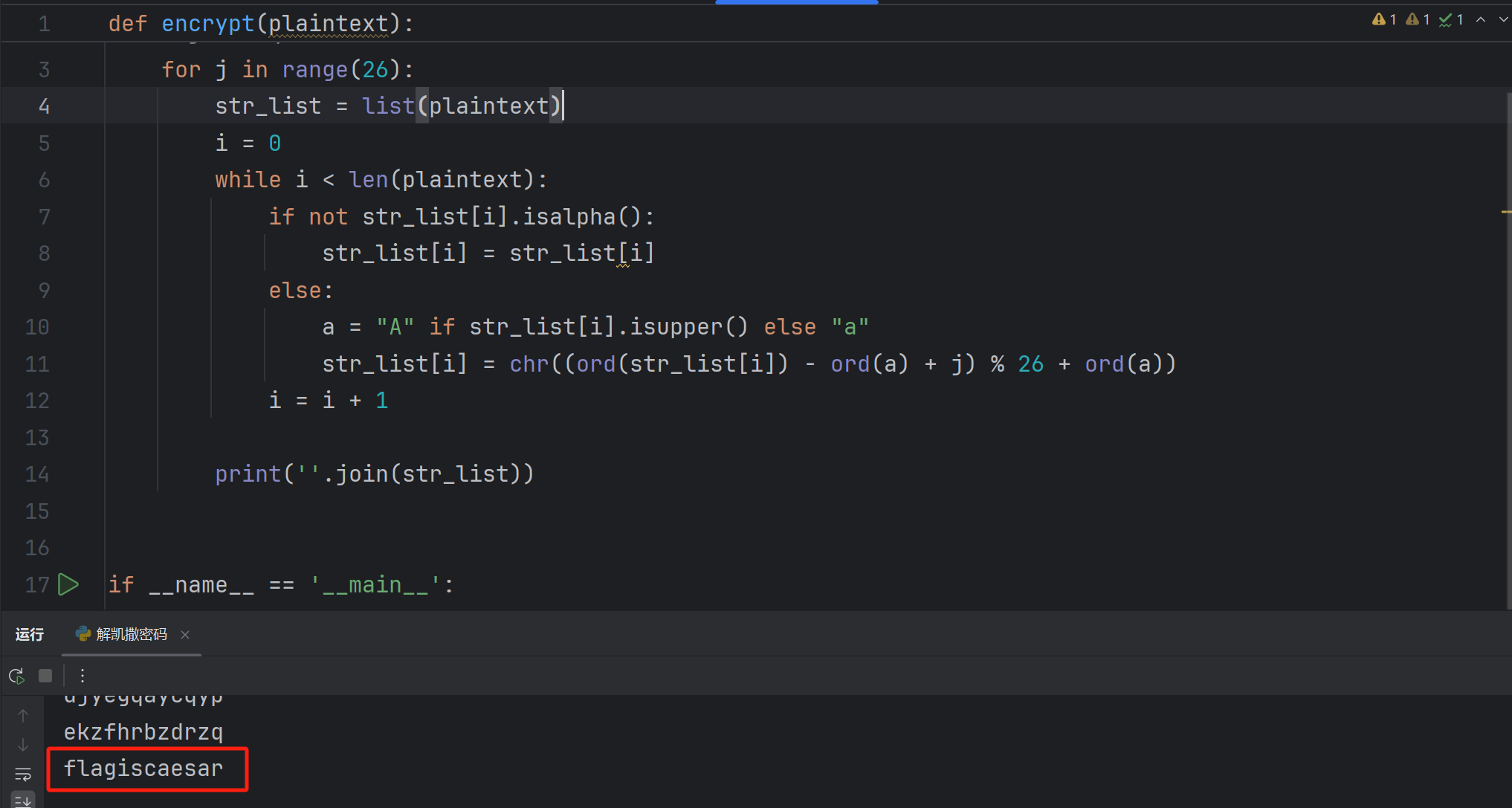
[SUCTF2018]single dog
一张披着jpg后缀的png
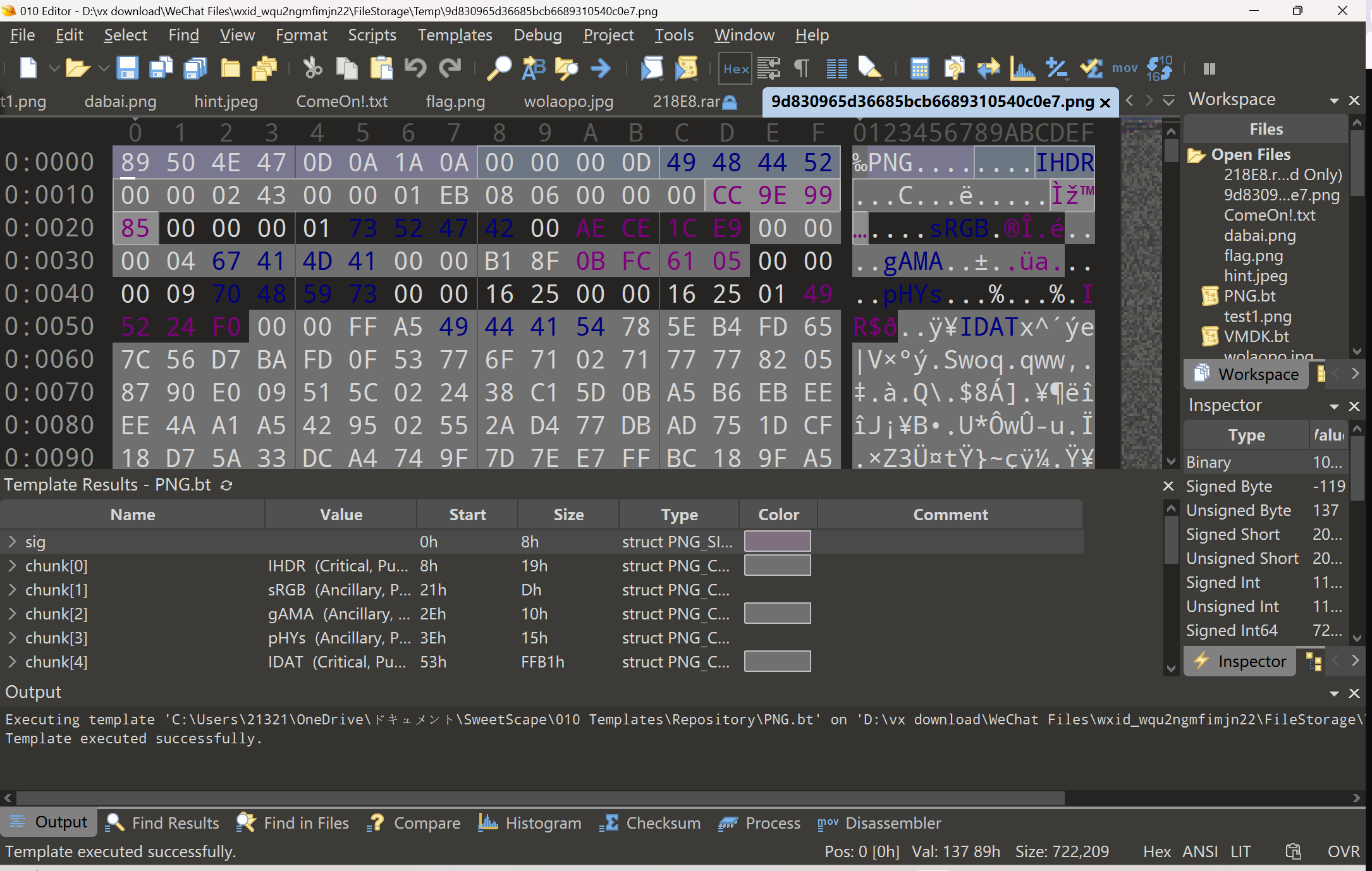
有个小问题就是89504E47是png文件头 但是file出来却是jpg
先是binwalk了一下 发现zip 解压缩得到
这么一堆东西
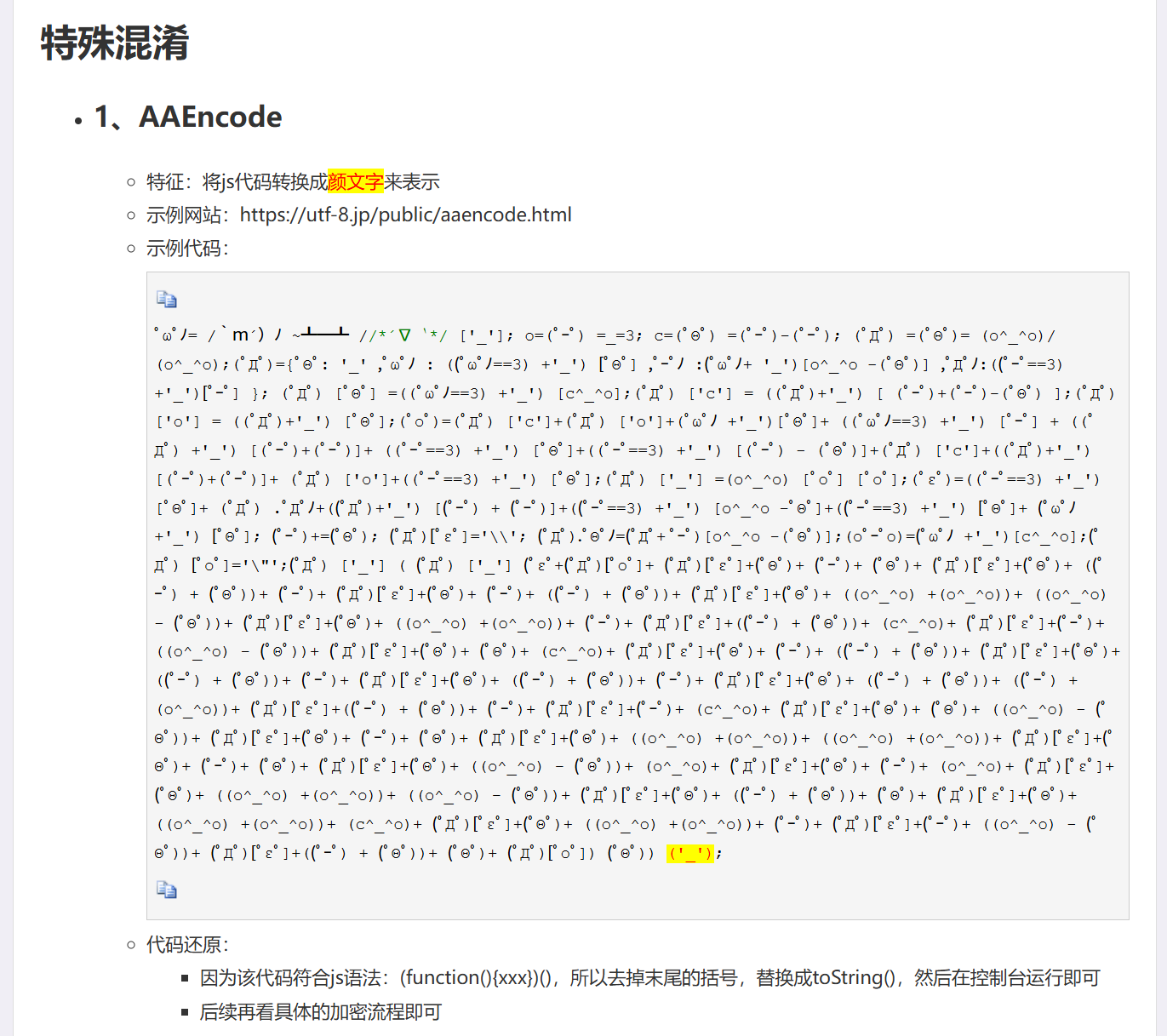
说是将末尾的括号去掉 换成toString()
emmmm..
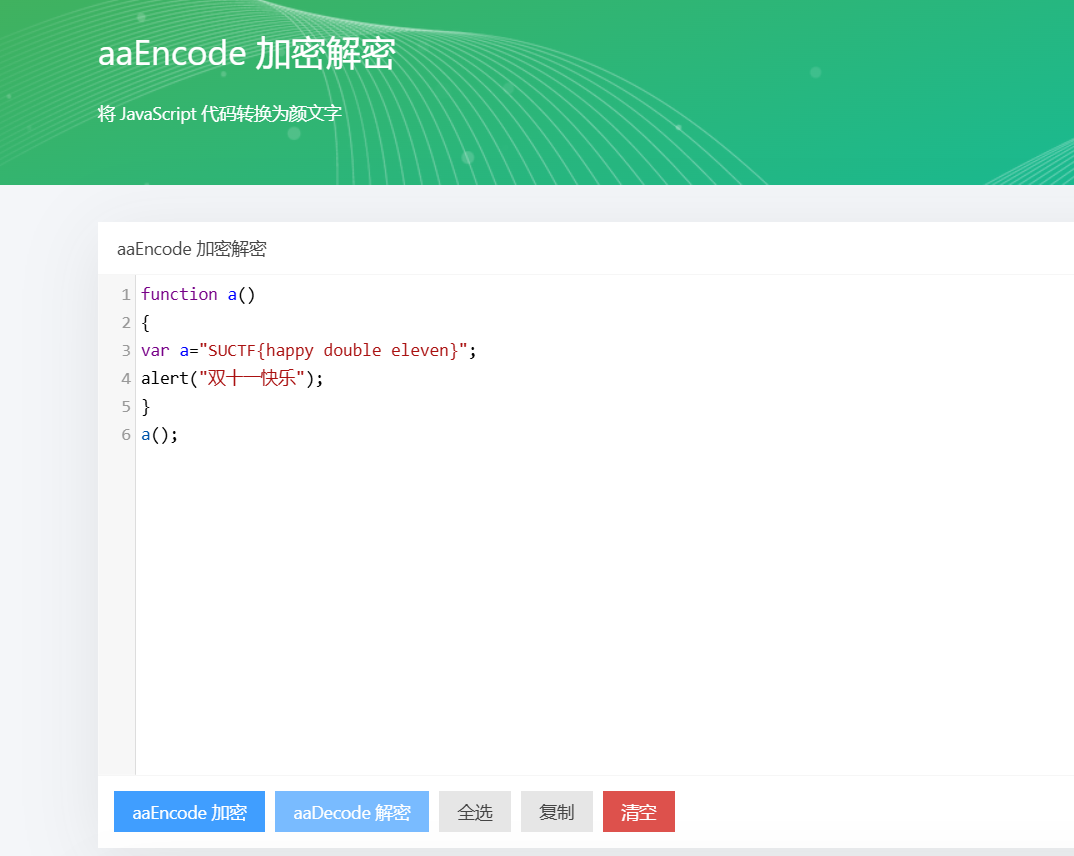
还是在线解密好使..
黑客帝国
一个txt里放着Rar
爆破一下
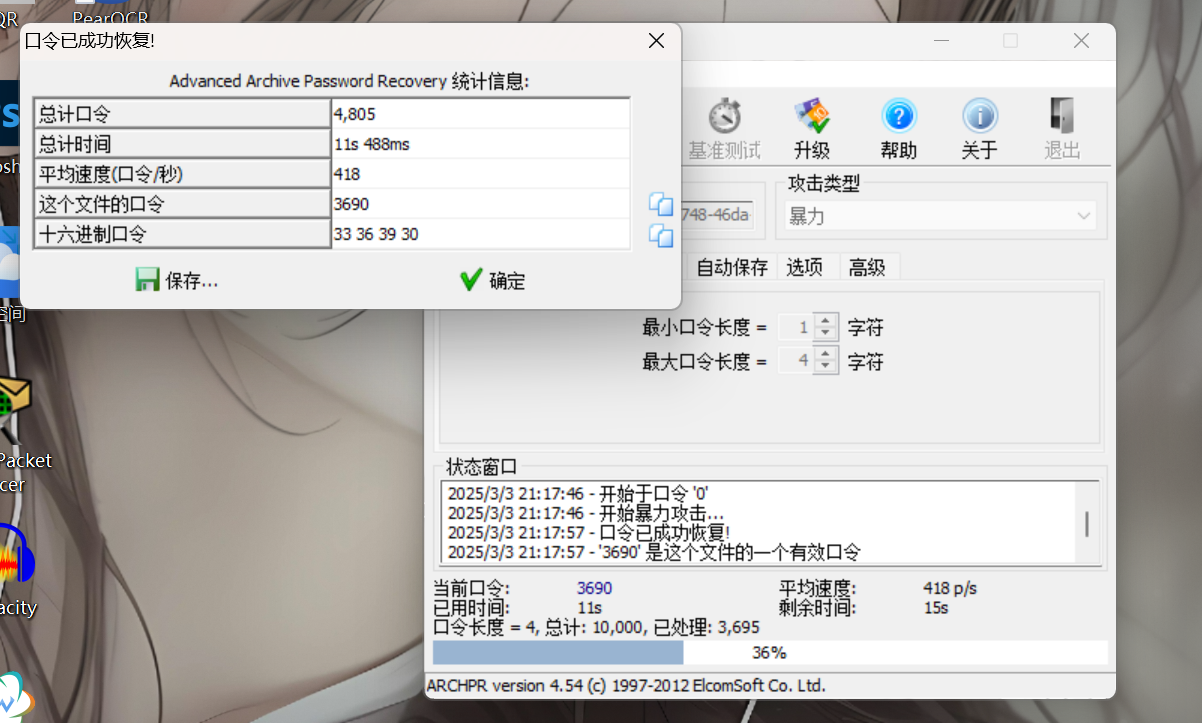
得到一张不支持png格式的png
看到文件尾是FFD9 修改文件头和后缀
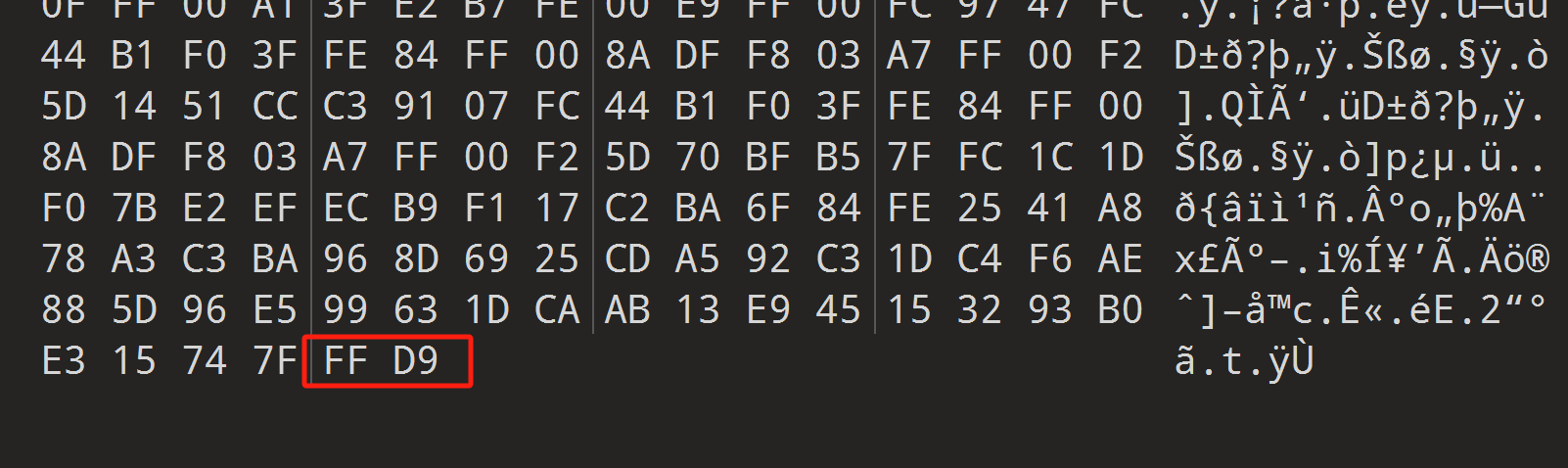
得到flag

[HBNIS2018]低个头

无语...

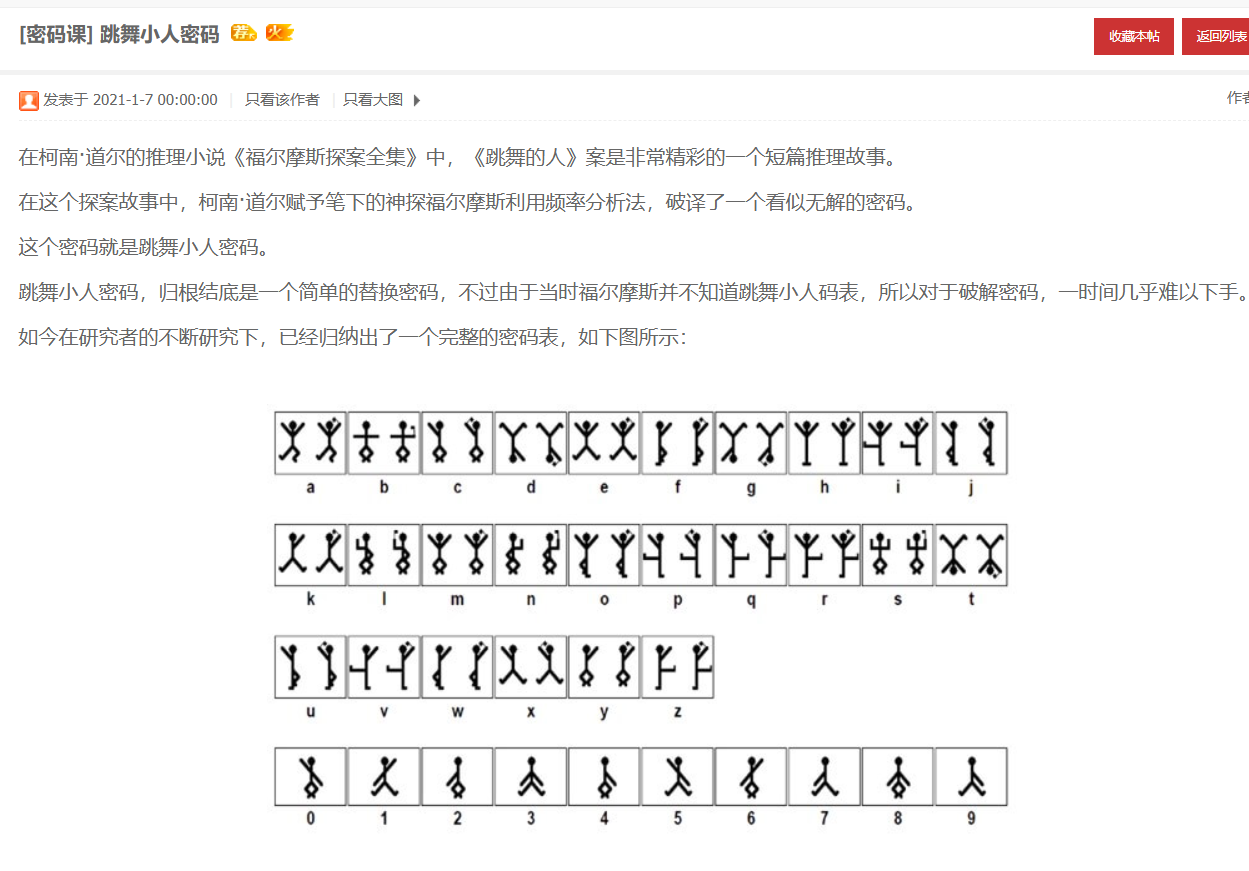
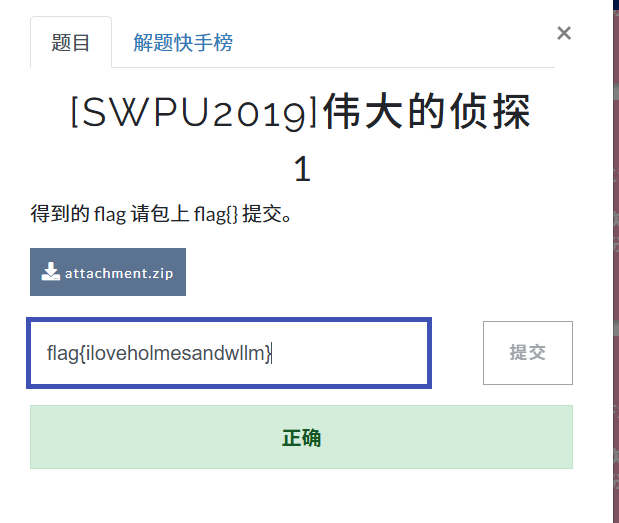
[SWPU2019]伟大的侦探
010里EBCDIC编码
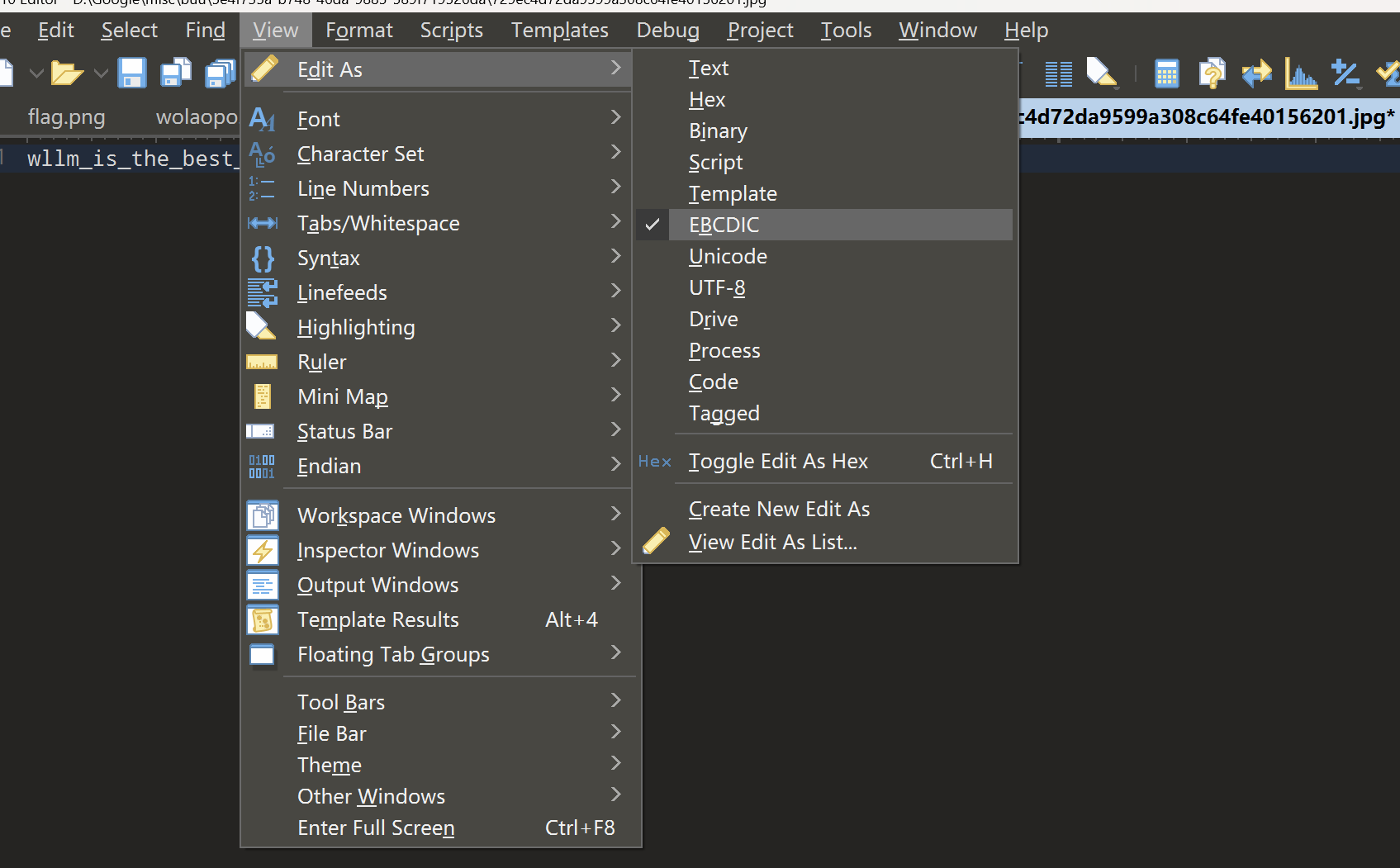
得到密码wllm_is_the_best_team!
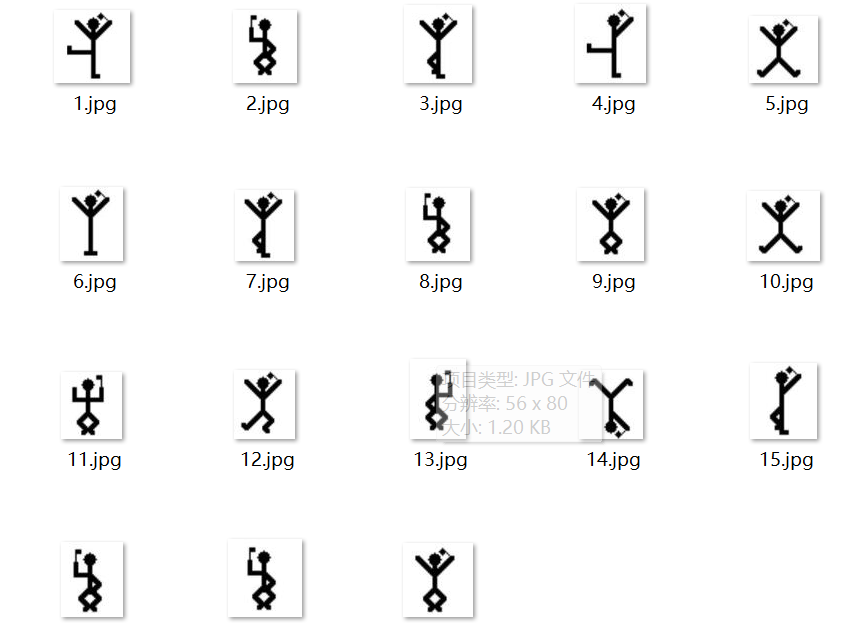
一堆小人..