XCTF IgniteMe
一.查壳

结论:
1.用vc++编译的。
2.无壳,毕竟是一分的题
二.点击运行,发现不是爆破,而是找出注册机,汇编功力还在提升中,只能拖入ida来静态调试了
具体的见注释:

二.1点击进入关键函数
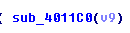
注意!这里有个坑,
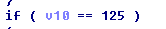
将125转换成字符,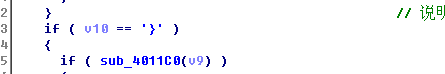
说明最后一个字符是}这点,可能会被很多人给忽视了,三分逆向,七分猜2333
三.见注释

四.脚本上:
v7="GONDPHyGjPEKruv{{pj]X@rF"
byte=[0xD,0x13,0x17,0x11,0x2,0x1,0x20,0x1D,0x0C,0x2,0x19,0x2F,0x17,0x2B,0x24,0x1F,0x1E,0x16,0x9,0xF,0x15,0x27,0x13,0x26,0xA,0x2F,
0x1E,0x1A,0x2D,0xC,0x22,0x4]
v5=""
str=""
for i in range(24):
v5+=chr(ord(v7[i])^byte[i])
for j in v5:
str+=chr((ord(j)-72)^0x55)
res=""
for a in str:
if a>='A' and a<='Z':
res+=chr(ord(a)+32)
elif a>='a' and a<='z':
res+=chr(ord(a)-32)
else:
res+=a
print(res)
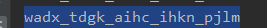
五.FLAG:
flag=EIS{wadx_tdgk_aihc_ihkn_pjlm}


