Crypto( 11 )
yxx
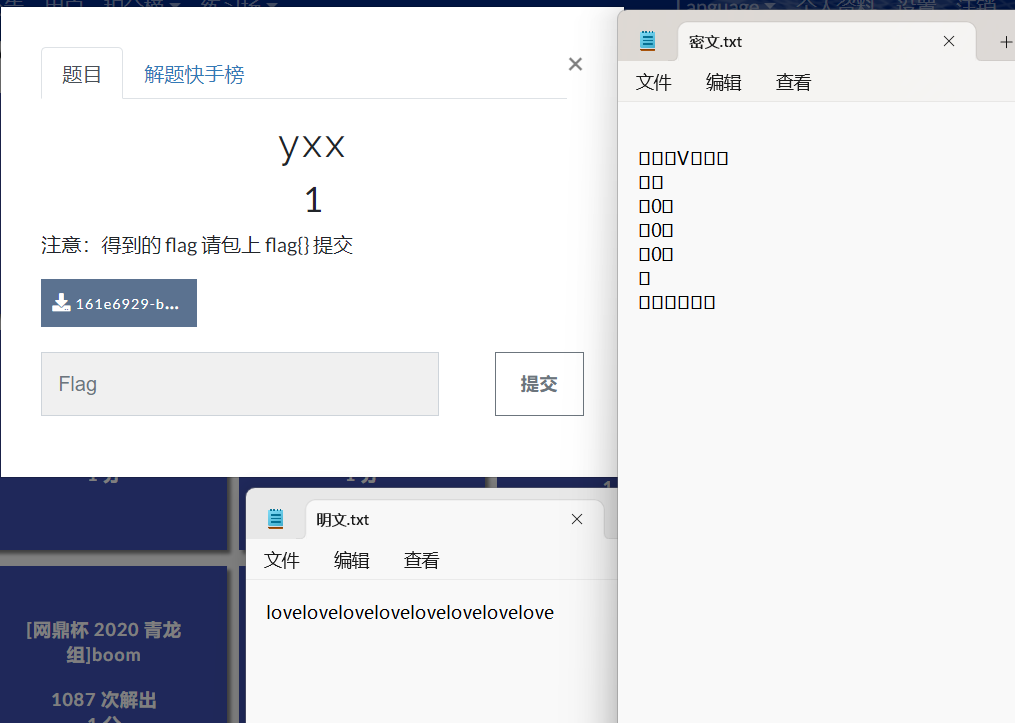
将两个文件都用010打开,转为二进制
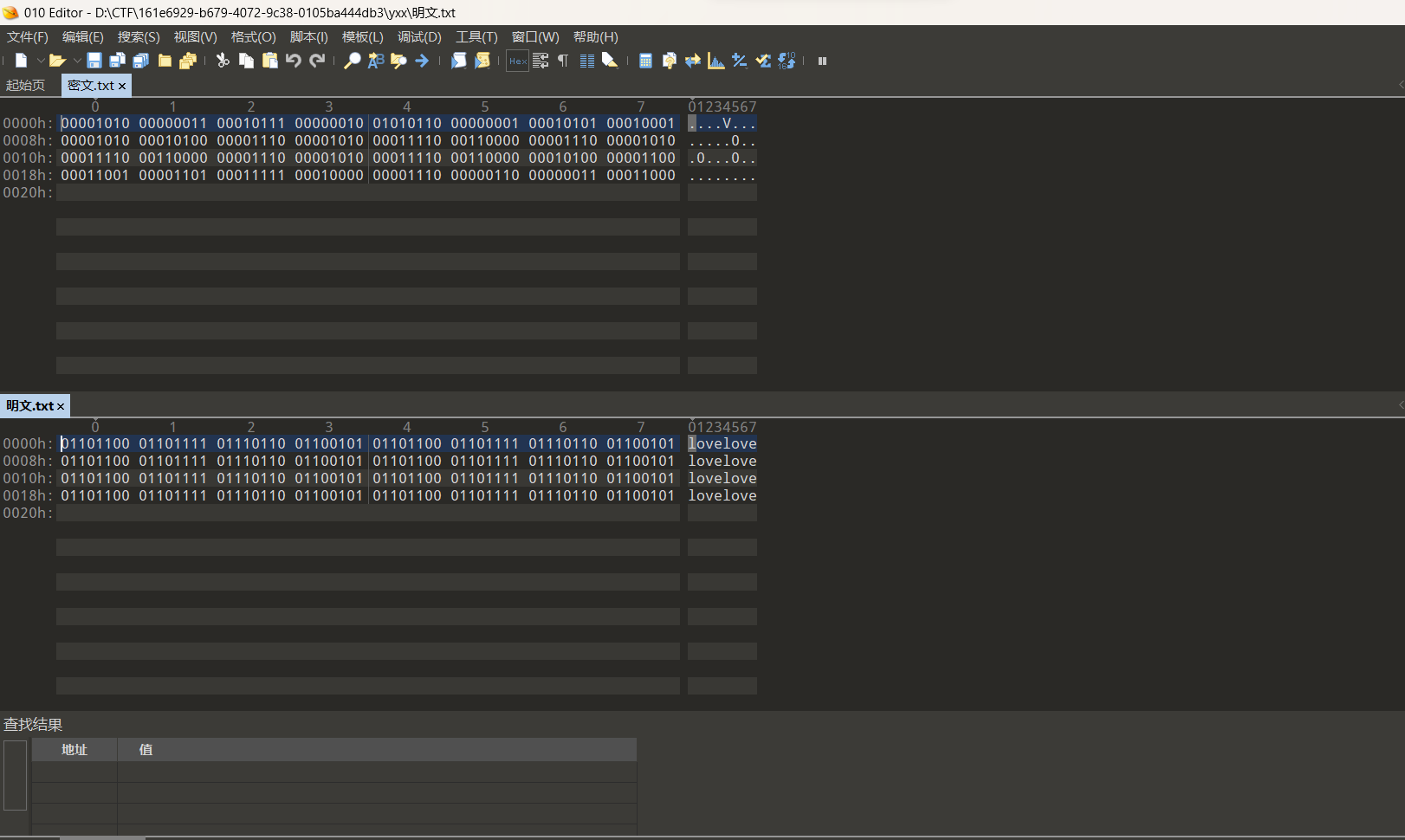
下面是异或脚本
点击查看代码
a='0110110001101111011101100110010101101100011011110111011001100101011011000110111101110110011001010110110001101111011101100110010101101100011011110111011001100101011011000110111101110110011001010110110001101111011101100110010101101100011011110111011001100101'
b='0000101000000011000101110000001001010110000000010001010100010001000010100001010000001110000010100001111000110000000011100000101000011110001100000000111000001010000111100011000000010100000011000001100100001101000111110001000000001110000001100000001100011000'
c=''
for i in range(len(a)):
if(a[i]==b[i]):
c+='0'
else:
c+='1'
print(c)
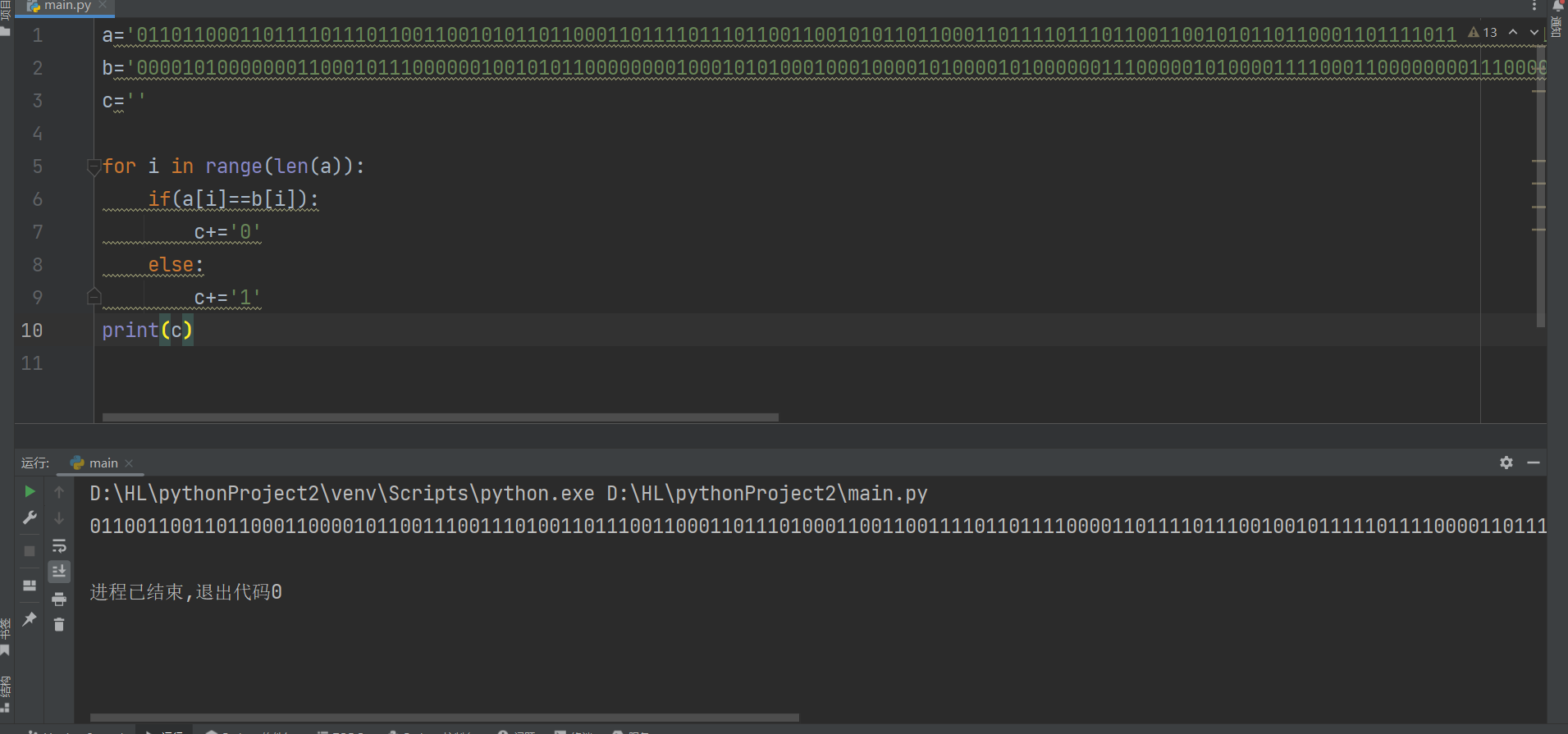
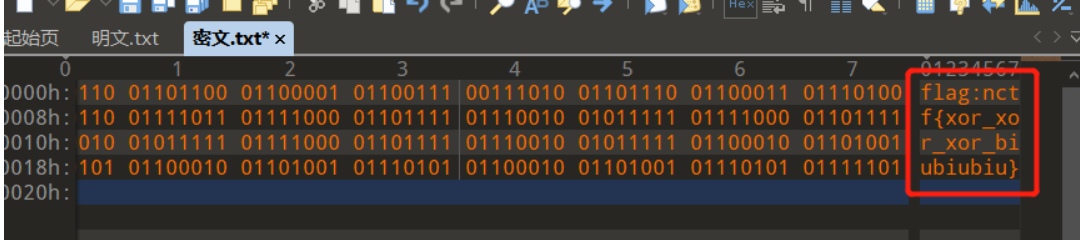
flag{xor_xor_xor_biubiubiu}
[AFCTF2018]你能看出这是什么加密么
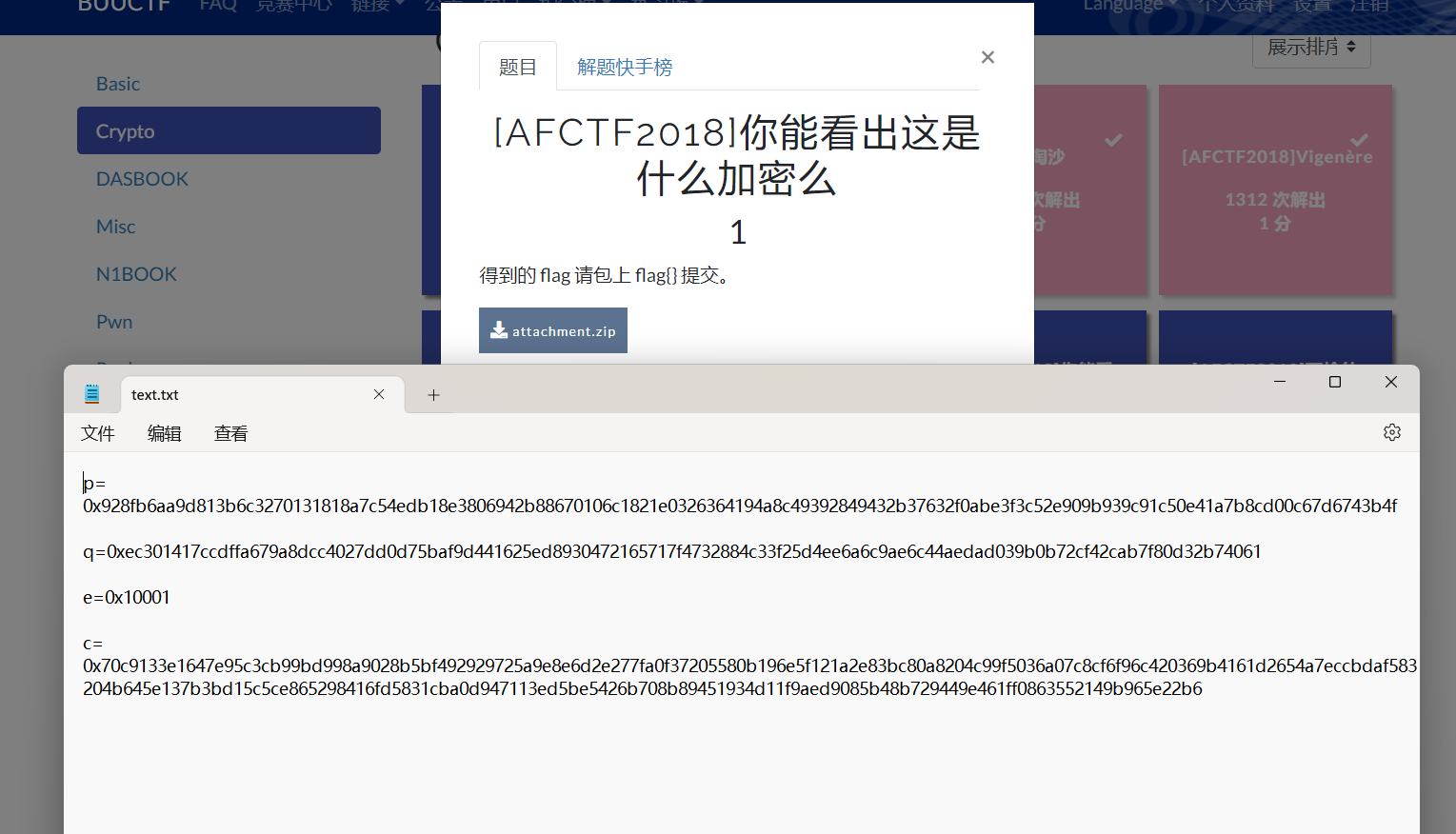
是rsa加密,脚本如下
点击查看代码
import binascii
import gmpy2
import binascii
p = 32968350940699980657930803613151404473574304024691423777313774889908862596593974505408563479347203657944730457083838853799946370868164530123853574071511042506373967
q = 2880152120462299039547844713611759800616693058487756771628124899159366904931022178508385592572818981251437302744086103000323987445642079008931937
c = 79200636304478271014515653428599205348546363880946576416664212880828226632721700716018261410389126930860598324371523316772928996360356422063555113754727289043115498759013305194277072343492062380609722125010442330717505742205680602598802403784826674446752282126860193320062982428054987016007285150027446362806
e = 65537
n = p * q
phi_n = (q - 1) * (p - 1)
d = gmpy2.invert(e, phi_n)
m = gmpy2.powmod(c, d, n)
print(binascii.unhexlify(hex(m)[10:]))
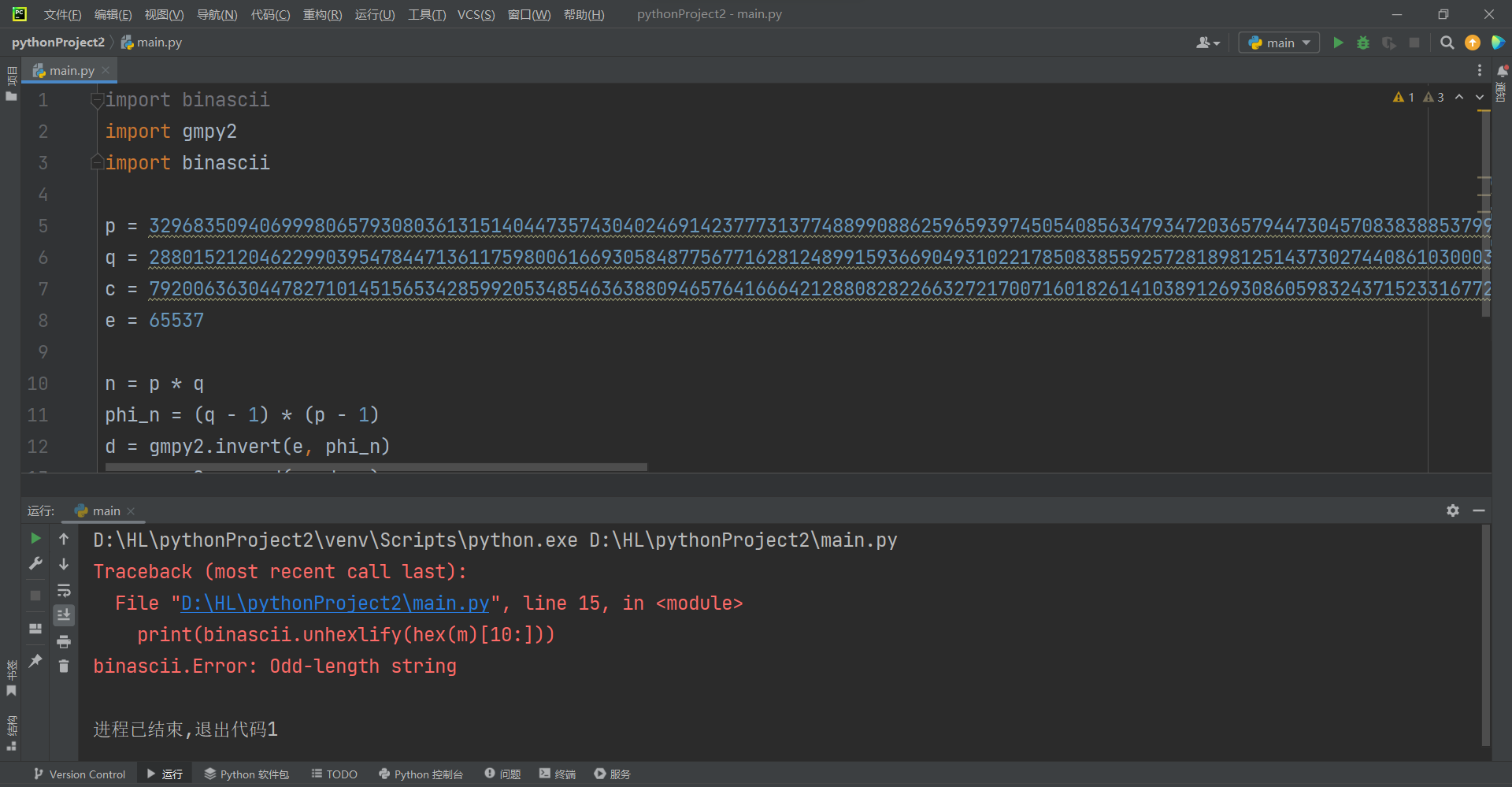
报错了,大佬说将最后的10改为9即可
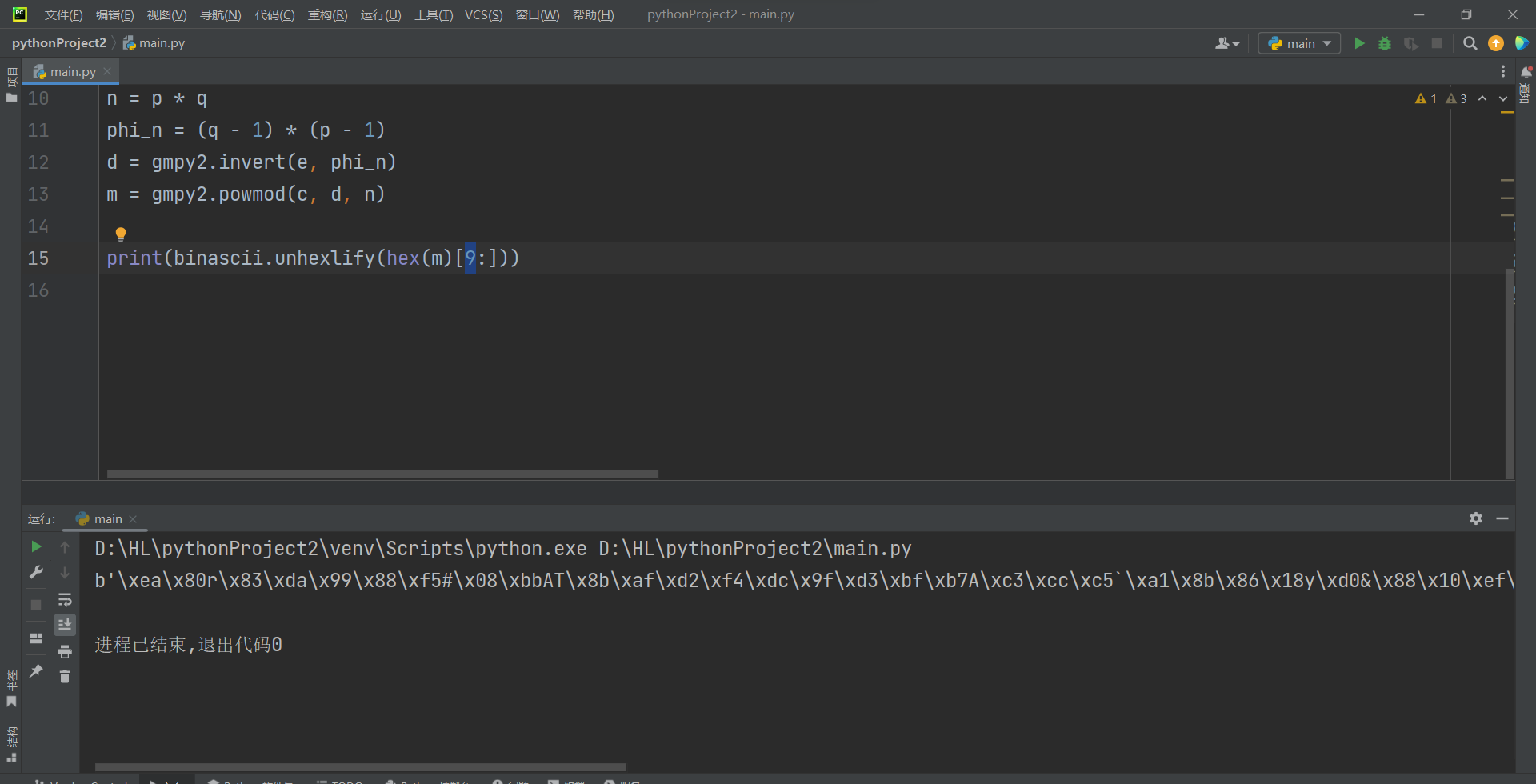
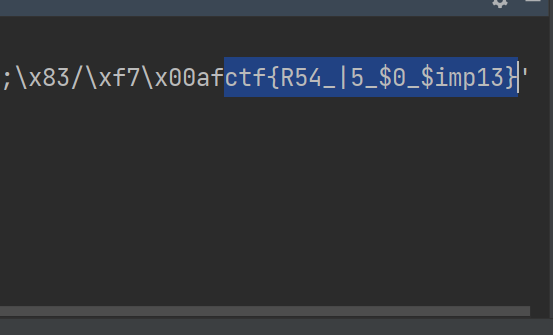
flag{R54_|5_$0_$imp13}
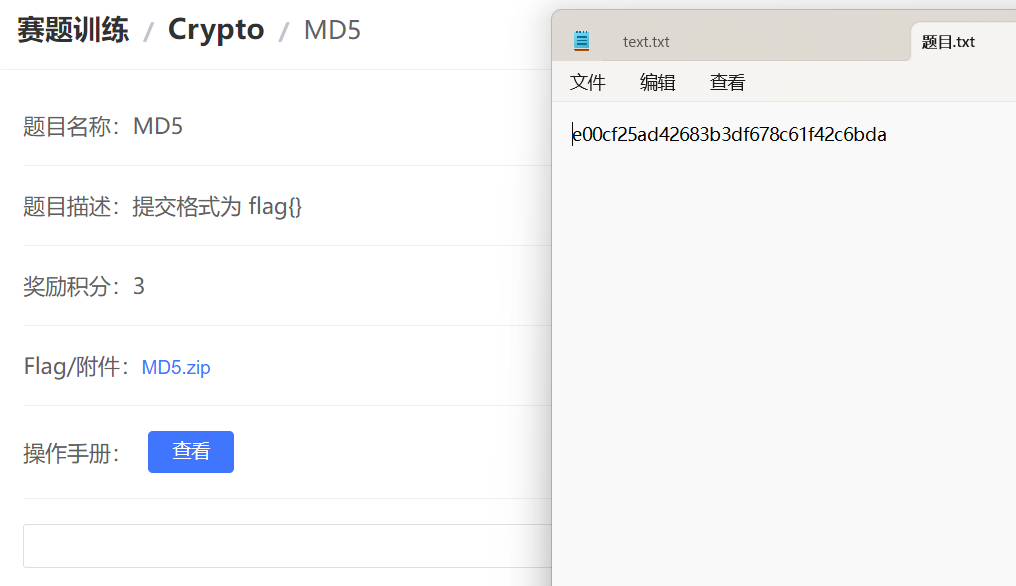
MD5
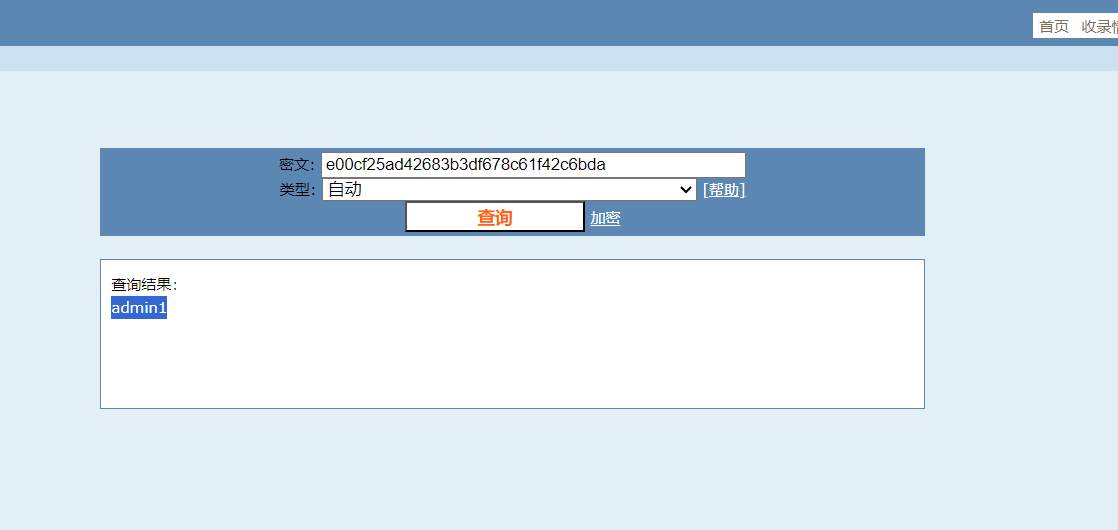
flag{admin1}
摩丝
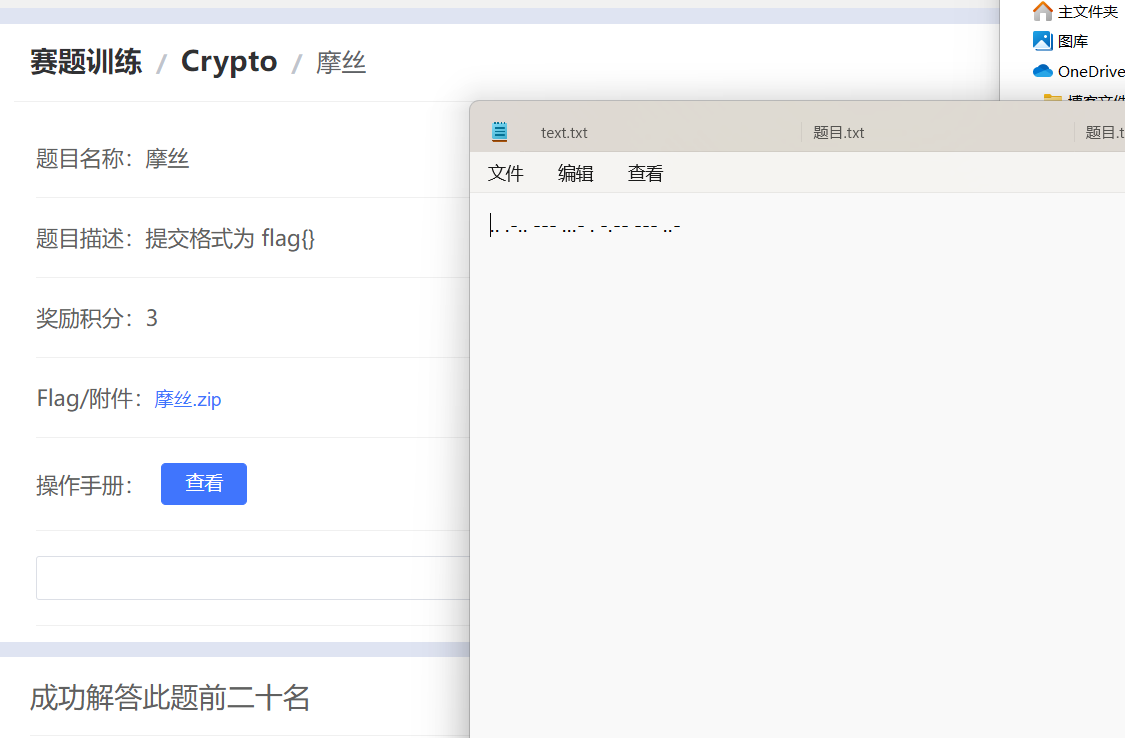
flag{ILOVEYOU}
低头
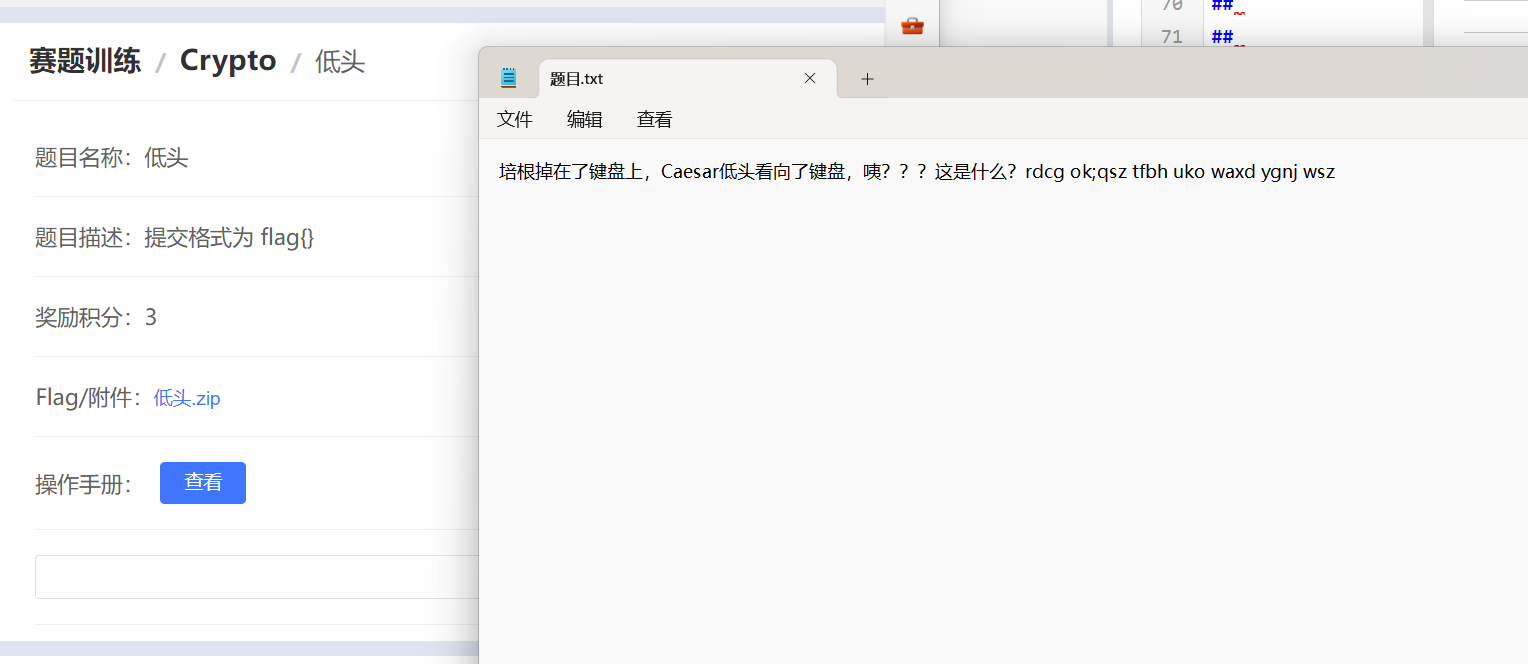
看见题目名称,就觉得跟键盘有关
敲出来是flagisha
flag{flagisha}
AAencode
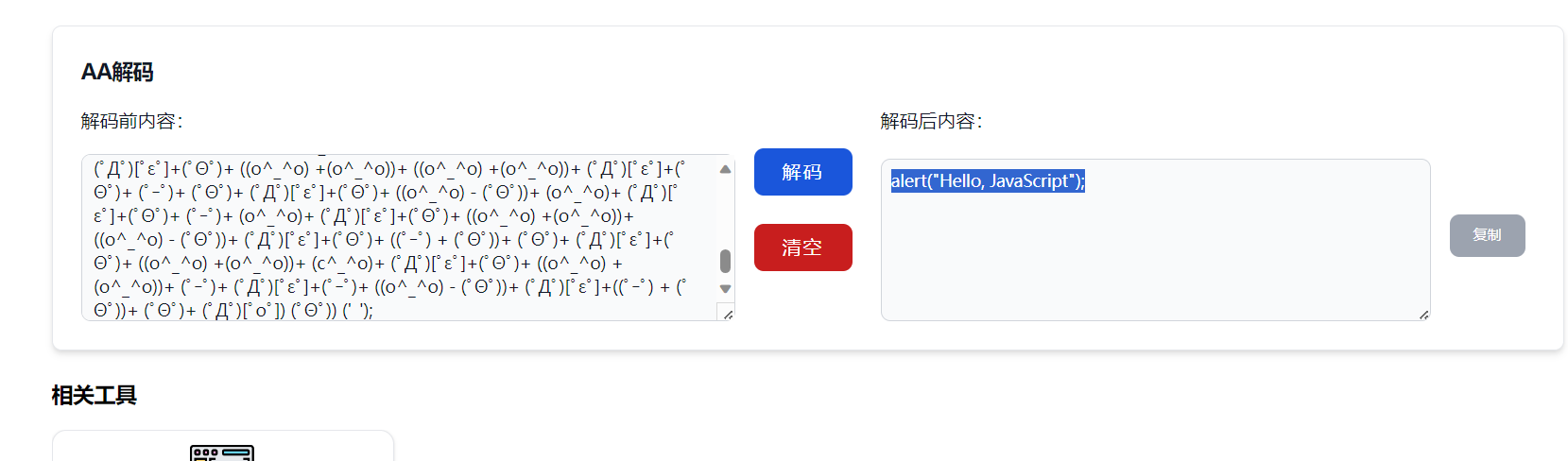
flag{Hello,JavaScript}
I like music
搜搜音符解密,有这么一个在线工具
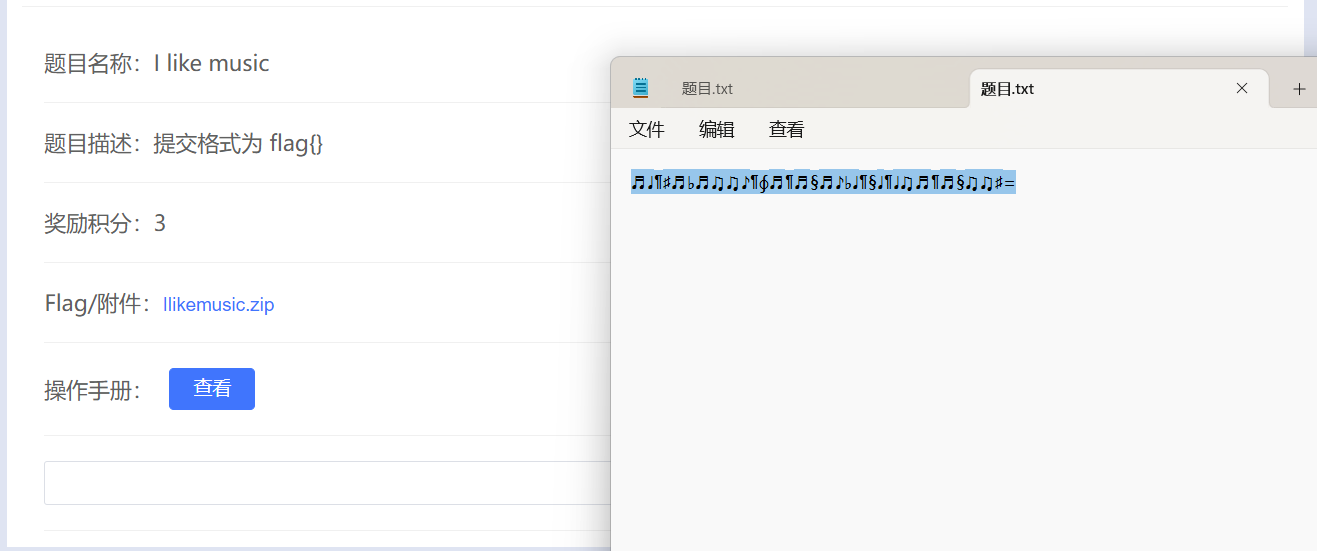
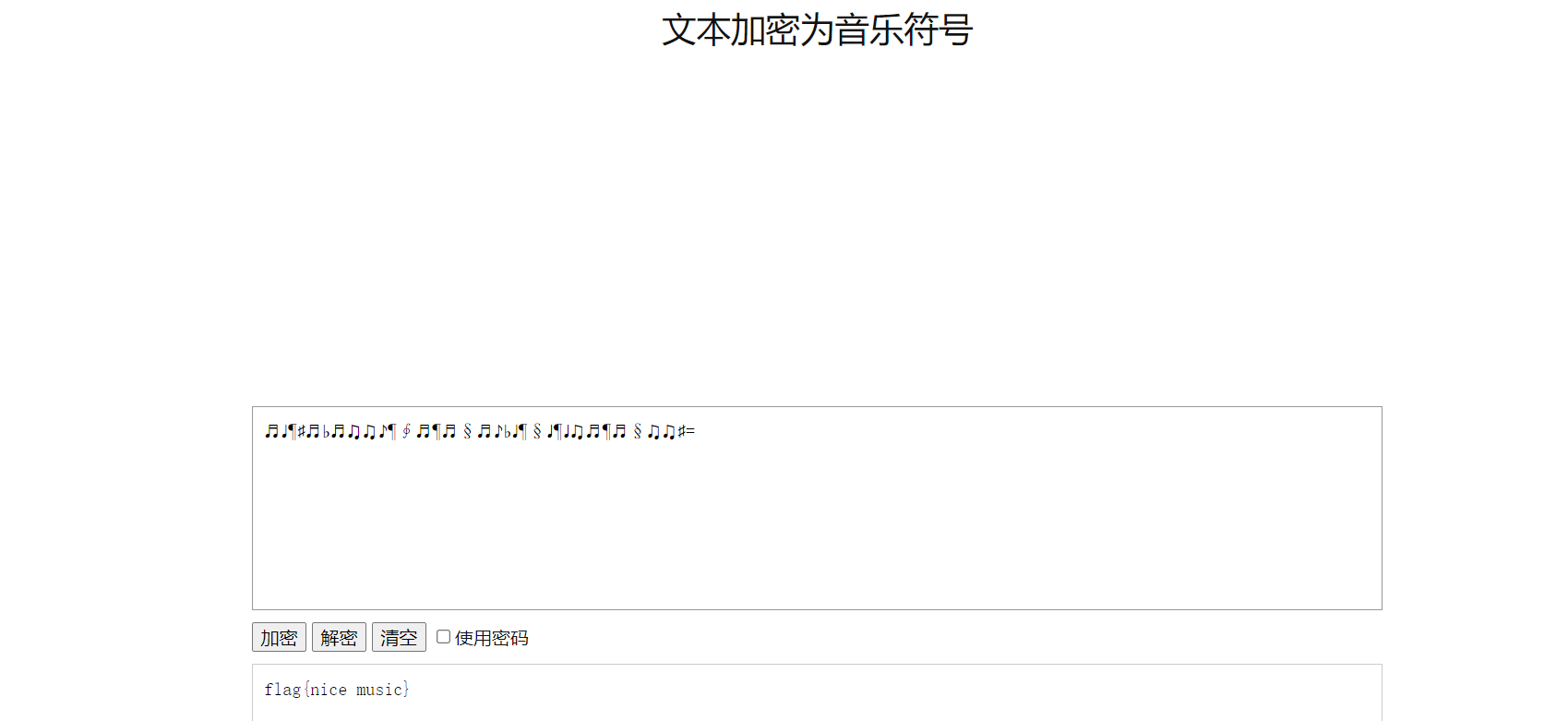
flag{nice music}
文本加密
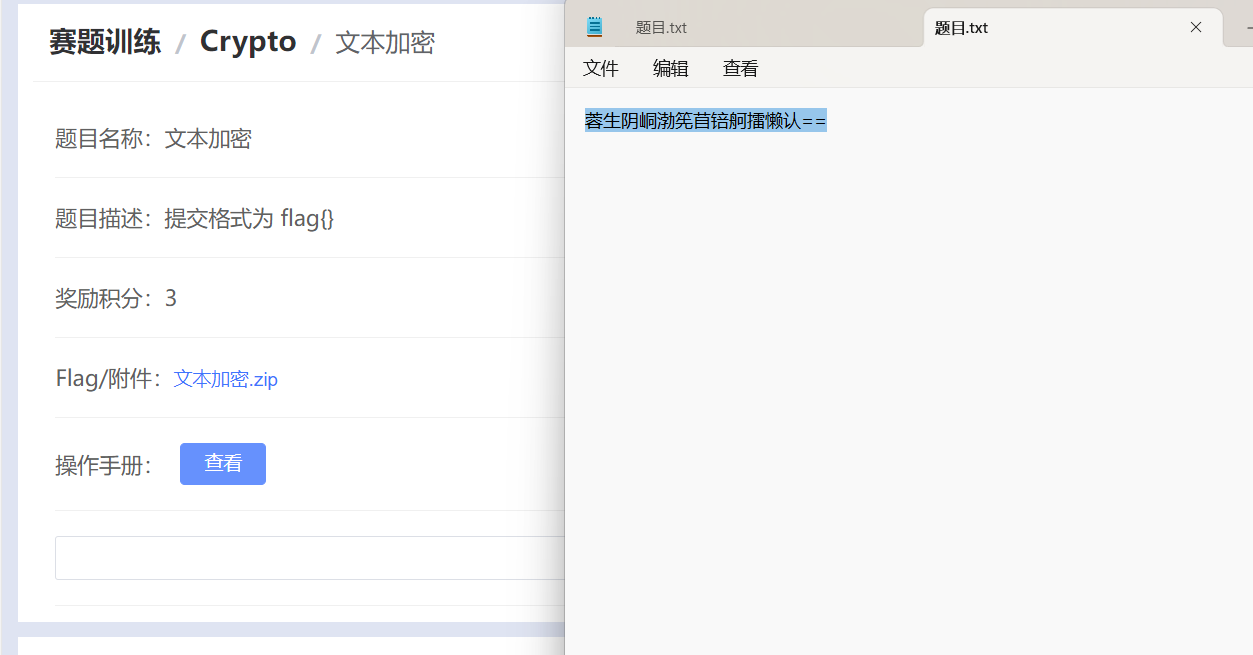
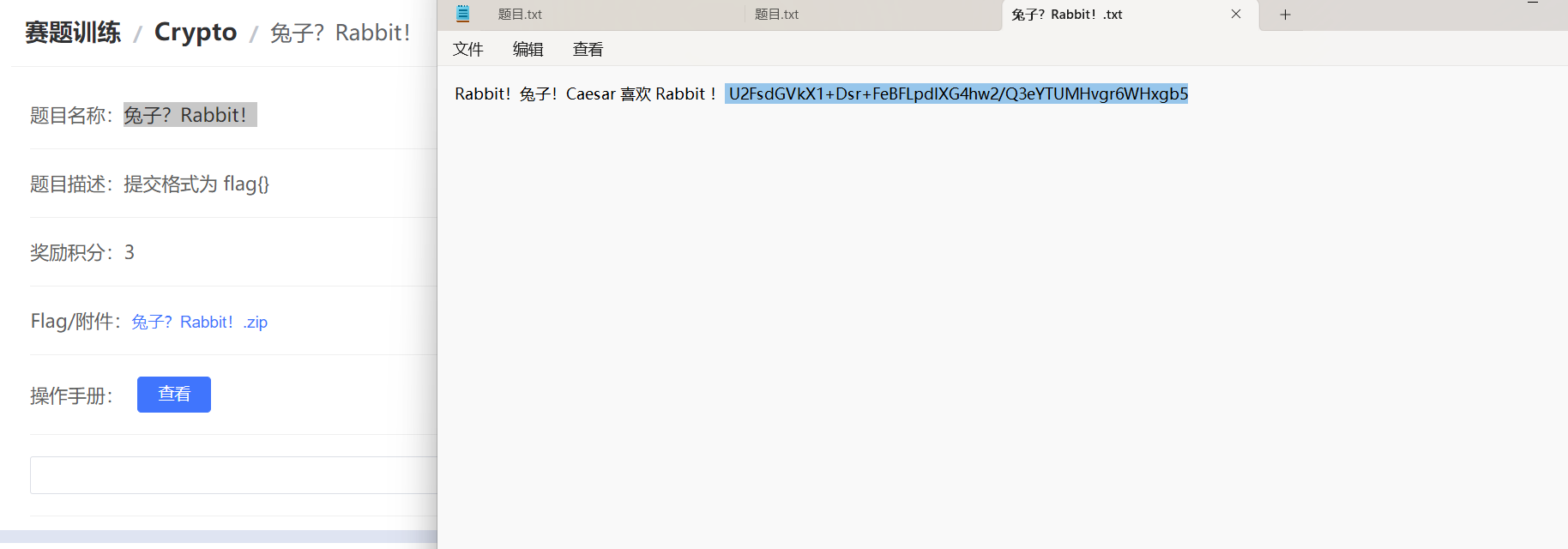
兔子?Rabbit!
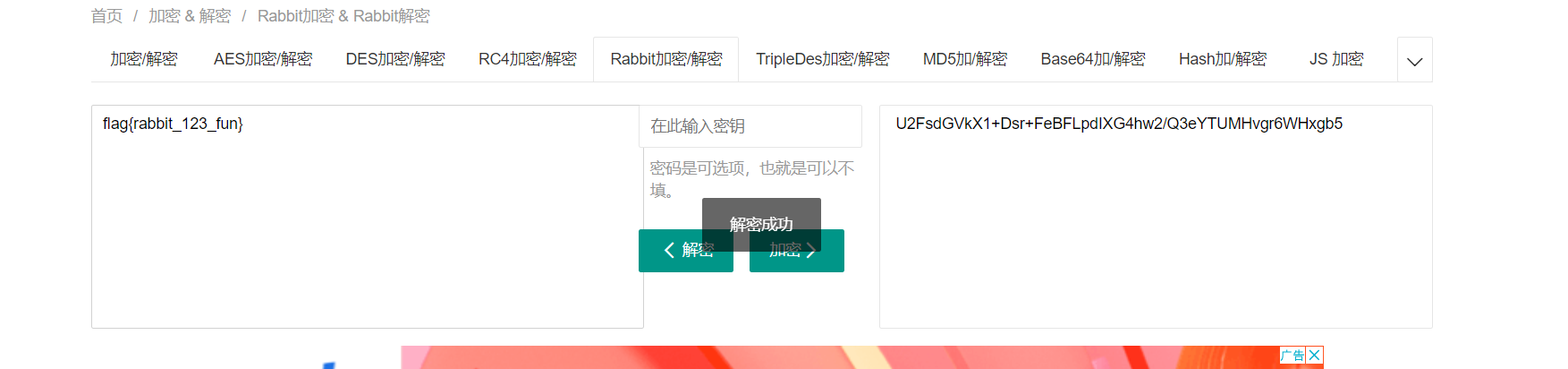
flag{rabbit_123_fun}
看我回旋踢
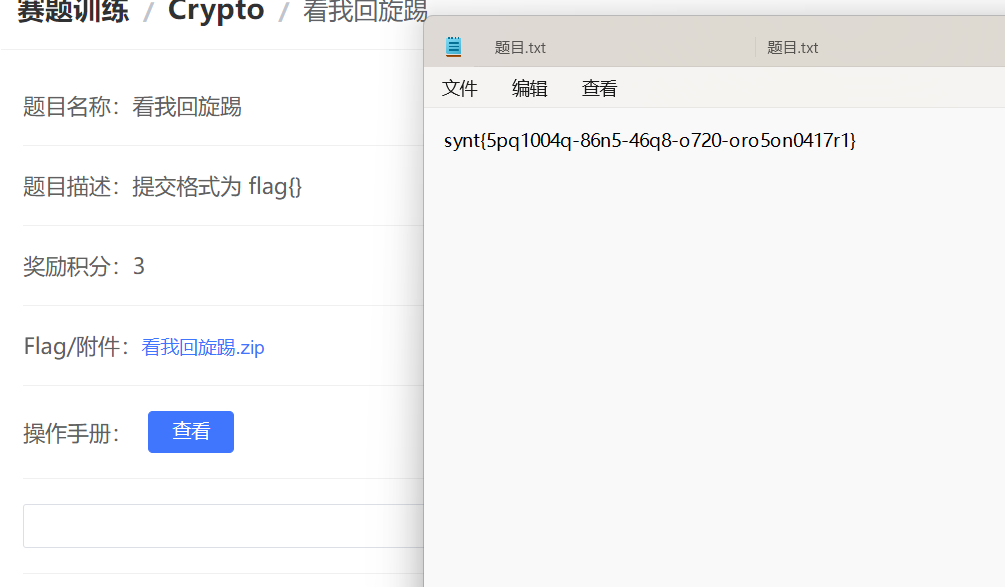
一看见跟flag形式差不多,就猜想是凯撒密码,然后利用枚举就ok了
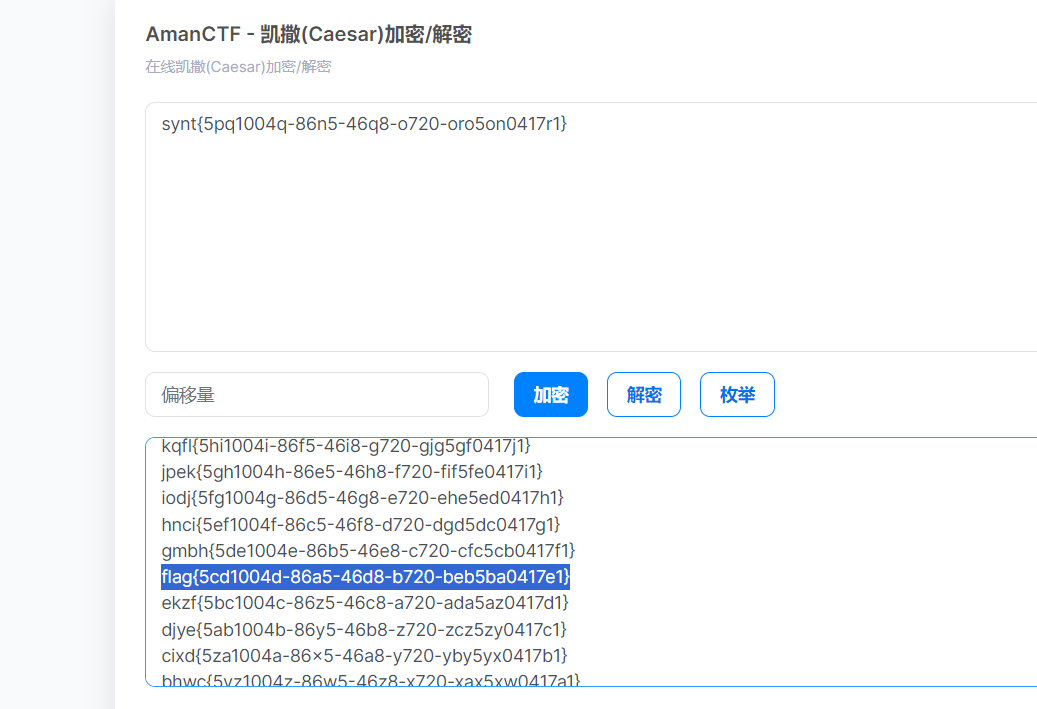
flag{5cd1004d-86a5-46d8-b720-beb5ba0417e1}



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理